In this walk through, we will be going through the Cross Site Scripting Reflected (AJAX-JSON) vulnerability section from bWAPP Labs. We will be exploring and exploiting Reflected Cross Scripting vulnerability in AJAX-JSON implementations and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
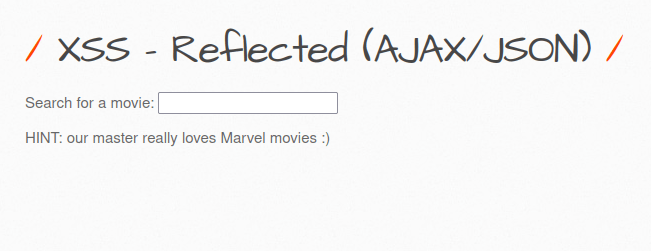
- The application has a search functionality where we can search for movies in the DB. It uses ajax to dynamically search the input.
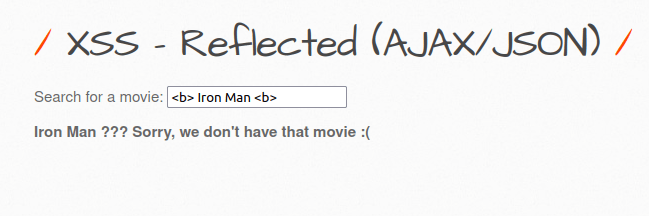
- Let’s check if we can contaminate the input and get our data stored in the DOM. I used the below payload where i have specified the bold HTML tag and the application parses it reflect on the page in real time which makes it vulnerable.
<b> Iron Man <b>
- I used the below payload to generate a pop-up alert.
<img src=x onerror=alert('Hacked')>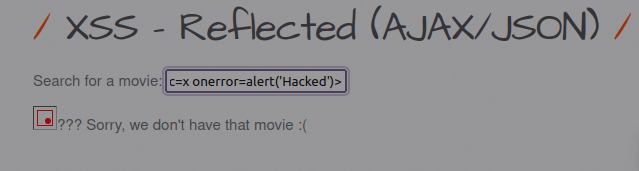

Security: Medium
- Setting the security level to Medium
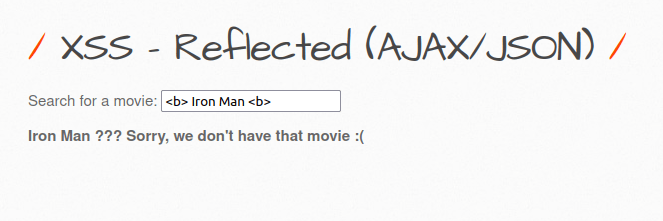
- I used the below payload to check if the application is till vulnerable and it worked.
<b> Iron Man <b>
- I used the below payload to generate a pop-up alert and exploited the application successfully.
<img src=x onerror=alert('Hacked')>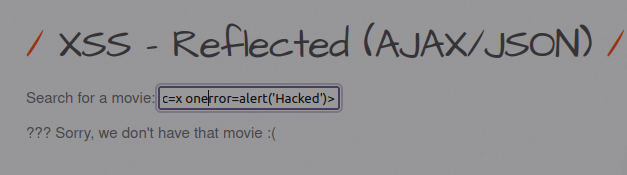

Also Read: bWAPP – Cross Site Scripting Reflected (Back-button)
Conclusion:

So, we finally completed all the security levels for the bWAPP Cross Site Scripting Reflected (AJAX-JSON) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Reflected-XSS attacks can be mitigated by performing input sanitization on endpoints, whitelist the allowed characters in the input and using a WAF. Along with that, we can prevent data from any untrusted source to be dynamically written to the HTML document. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




