In this walk through, we will be going through the Text Files (Accounts) vulnerability section from bWAPP Labs. We will be exploring and exploiting Text Account Files and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
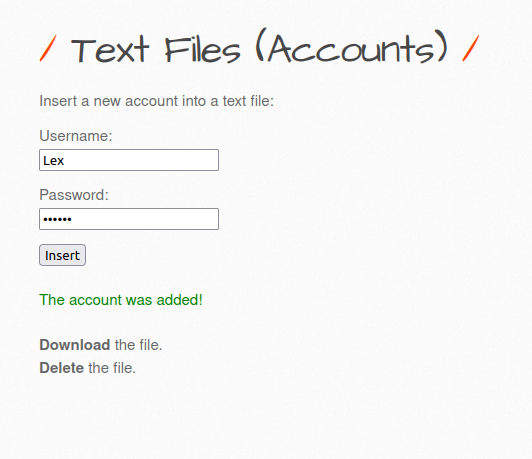
- The application has a functionality to add a new account. It issues a POST request to insecure_crypt_storage_2.php file with our username and password parameter. Once account is created, it displays a download and delete file button.
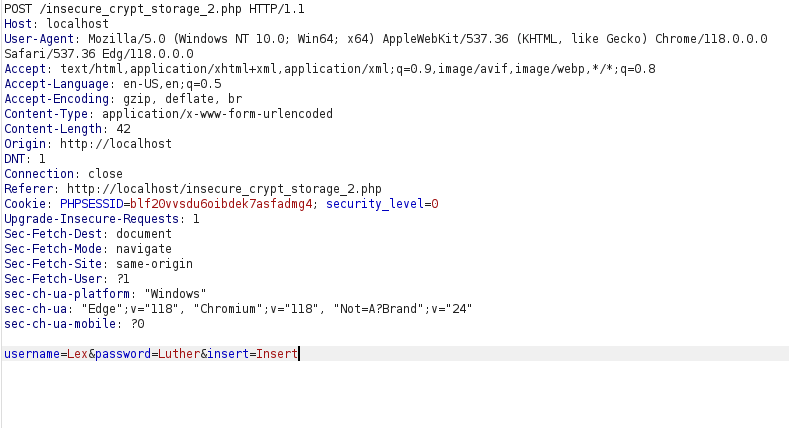
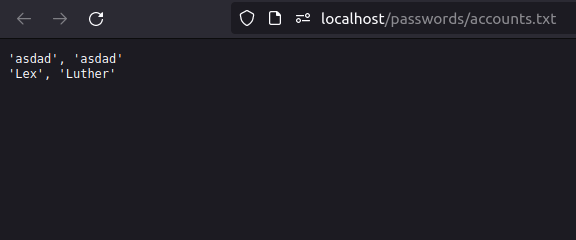
- Upon clicking the download file button, we are able to see the added username and password in plain text.
Security: Medium
- Setting the security level to Medium.
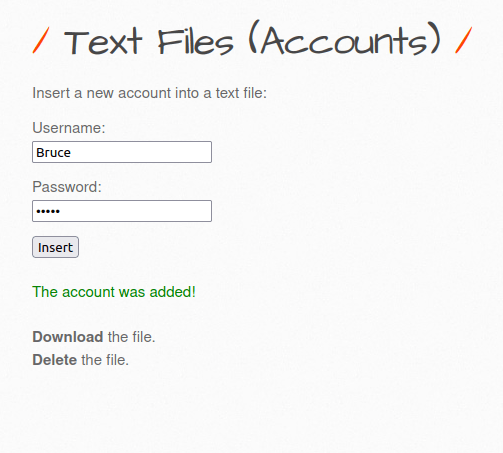
- I added another user again and had a look in the accounts.txt file. This time we got an encrypted password value.
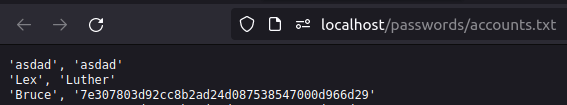
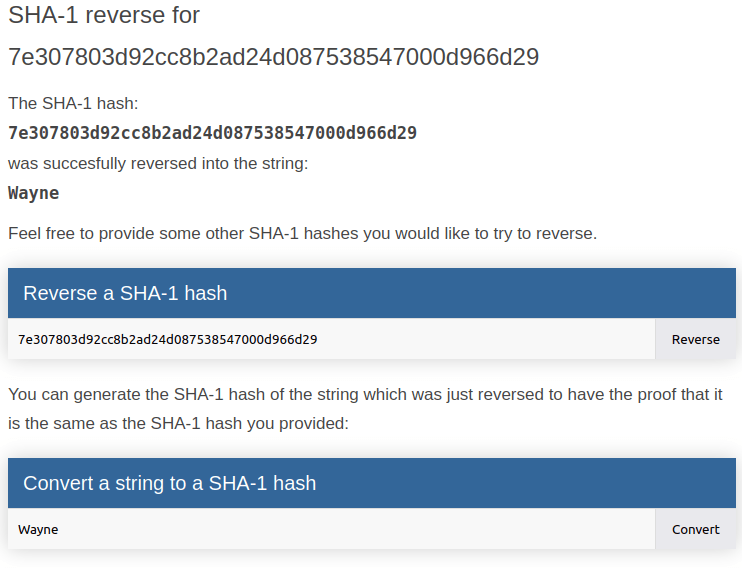
- It was a SHA1 hash and on decrypting it we got our password value.
Security: High
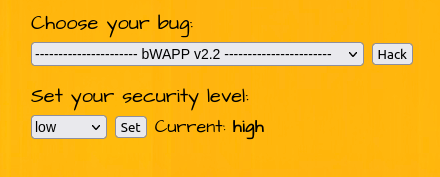
- Setting the security level to High.
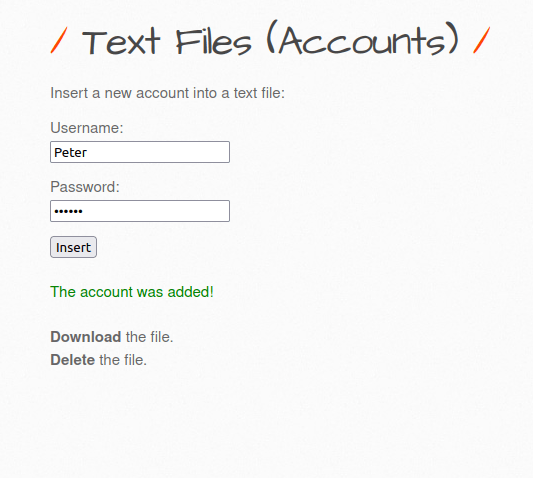
- Adding another account.
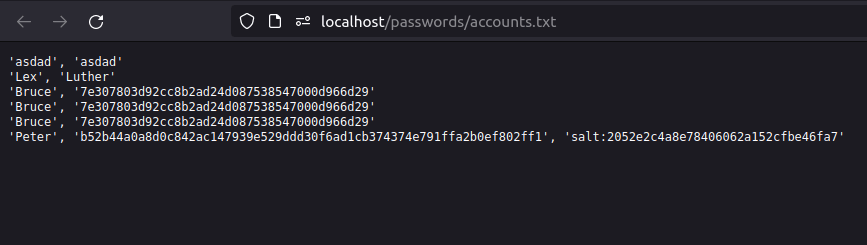
- This time it is more difficult to crack the password as it is using a salt with it but it is still possible.
Also Read: bWAPP – SQL Injection Stored (User-Agent)
Conclusion:

So, we finally completed all the security levels for the bWAPP Text Files (Accounts) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate this by storing sensitive file properly and avoiding leakage issues. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




