In this walk through, we will be going through the User-Agent Impersonation vulnerability section from Mutillidae Labs. We will be exploring and performing User-Agent Impersonation with User Agent Switcher and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.
Table of Contents
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

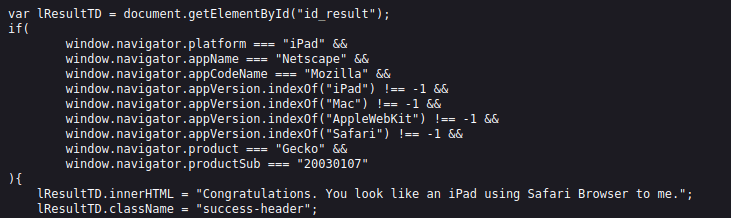
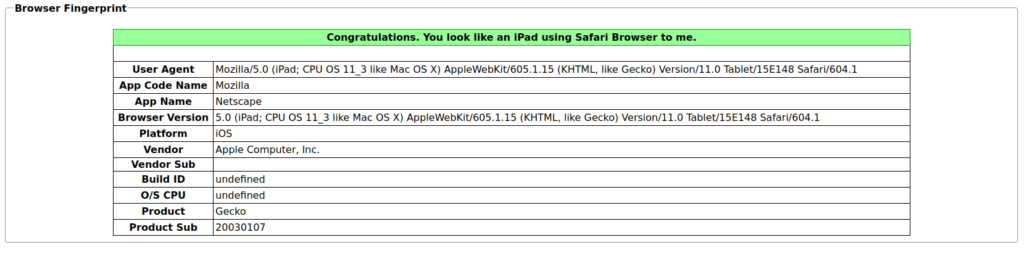
- In this challenge, the application is authorizing the user on the basis of his browser information with the help of User-Agent. It expects a user with iPad on Safari Browser.
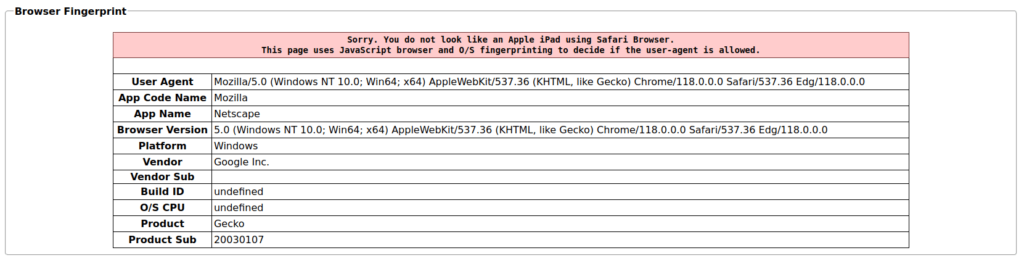
- I used User-Agent switcher on mozilla and changed the user-agent to that of iPad.
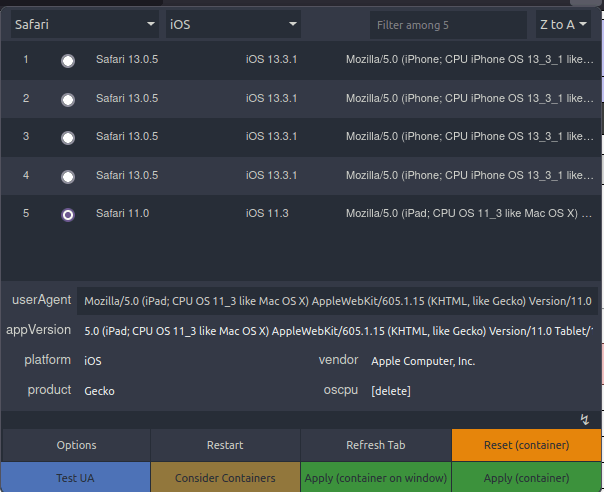
- However it didn’t worked even now.
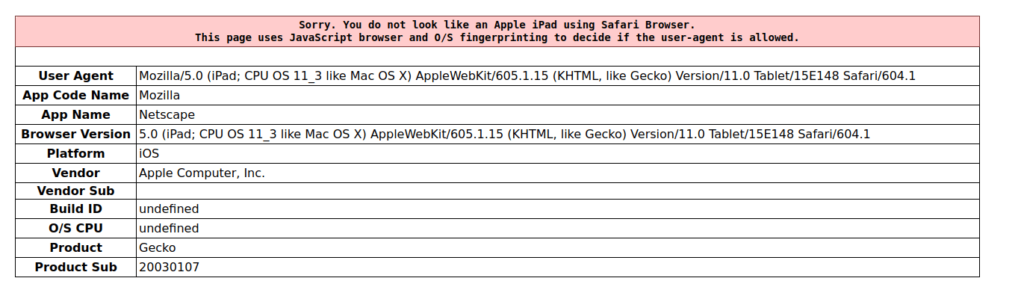
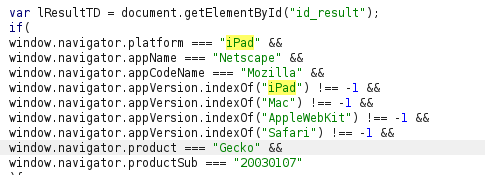
- Upon checking the source code found out that the application is checking the platform field for “iPad”. Dig something on this however was unable to come up any way to edit it.
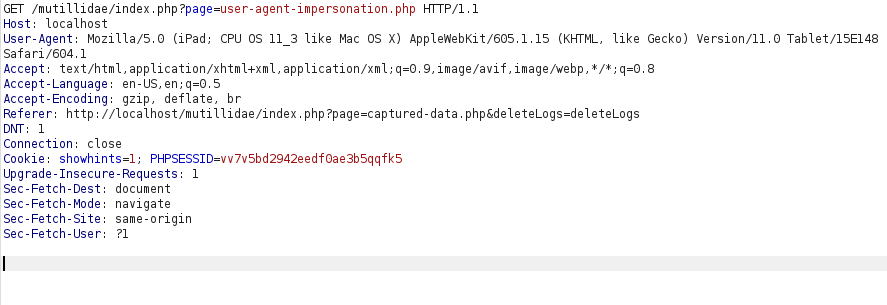
- Next, i intercepted the request and Then intercept the response by right clicking -> Do intercept – Response of this request.
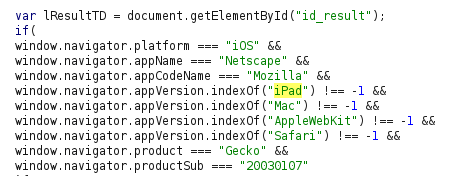
- Changed the iPad value to iOS in the response and forward the request. We are not authorized to view the page.
Also Read: Mutillidae – Sqlmap Practice (View Blogs)
Conclusion:

So, we finally completed all the security levels for the Mutillidae User-Agent Impersonation Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential User-Agent Impersonation attacks by solely not relying on client side controls like User Agent for allowing access to the resource on the web server. Developers can create required server side checks and proper authentication mechanisms in order to prevent these types of attacks. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




