In this walk through, we will be going through the Content Discovery room from Tryhackme. This room will teach you the various ways of discovering hidden or private content on a webserver that could lead to new vulnerabilities. So on that note, let’s get started.

Task 1 – What is Content Discovery?
Question 1 – What is the Content Discovery method that begins with M?
Manually
Question 2 – What is the Content Discovery method that begins with A?
Automated
Question 3 – What is the Content Discovery method that begins with O?
OSINT
Task 2 – Manual Discovery: Robots.txt
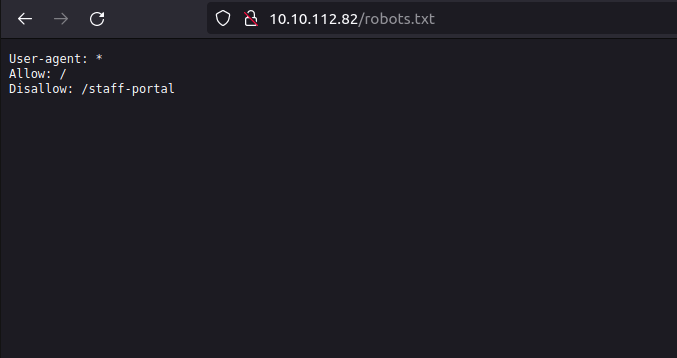
Question 1 – What is the directory in the robots.txt that isn’t allowed to be viewed by web crawlers?
staff-portal
Task 3 – Manual Discovery: Favicon
Use favicon to get information about the framework that target application is using.
OWASP – https://wiki.owasp.org/index.php/OWASP_favicon_database
- Find the favicon area of the website by viewing source. Here: view-source:https://static-labs.tryhackme.cloud/sites/favicon/images/favicon.ico
- use the curl command to download the favicon and get his MD5 hash.
curl https://static-labs.tryhackme.cloud/sites/favicon/images/favicon.ico | md5sum
- Compare it with OWASP favicon database to get the framework used in the website.
- if hash ends with 427e, then curl failed.
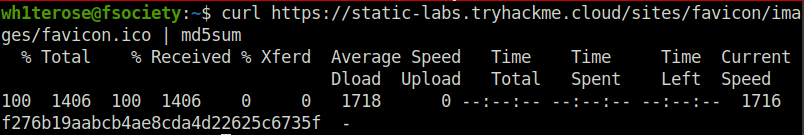
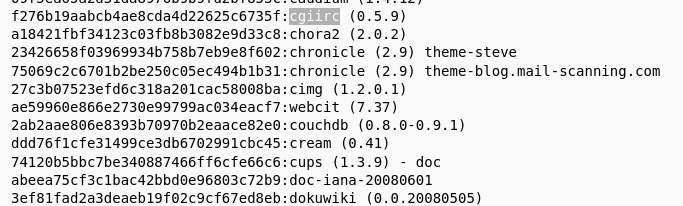
Hash captured – f276b19aabcb4ae8cda4d22625c6735f
Question 1 – What framework did the favicon belong to?
cgiirc
Task 4 – Manual Discovery: Sitemap.xml
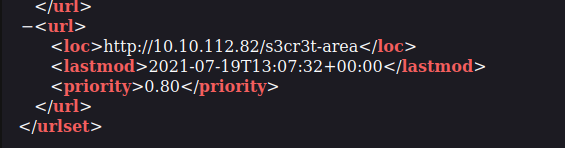
Question 1 – What is the path of the secret area that can be found in the sitemap.xml file?
/s3cr3t-area
Task 5 – Manual Discovery: HTTP Headers
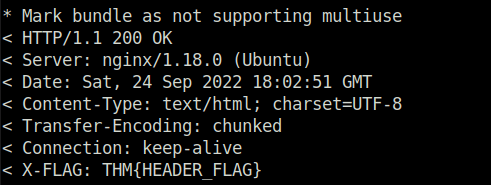
Question 1 – What is the flag value from the X-FLAG header?
THM{HEADER_FLAG}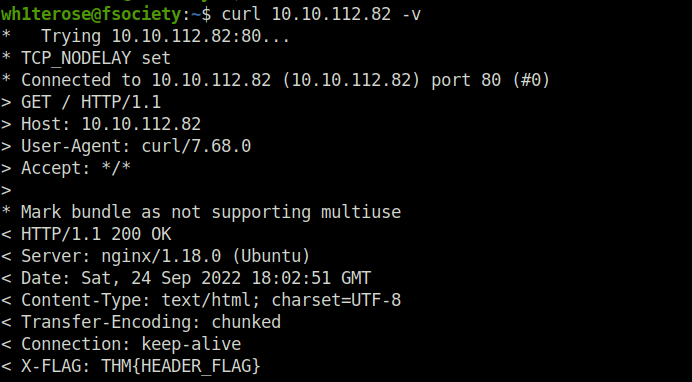
Task 6 – Manual Discovery: Framework Stack
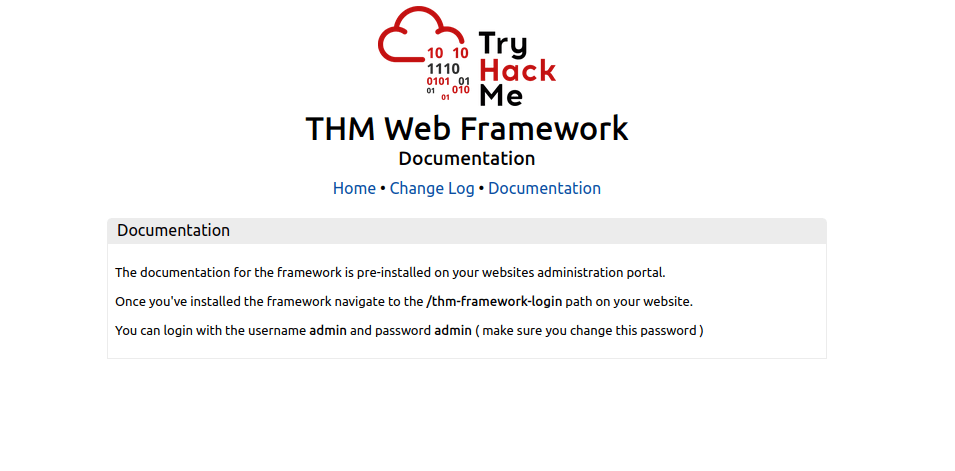
THM Framework default credentials –
- Username – admin
- Password – admin
Question 1 – What is the flag from the framework’s administration portal?
THM{CHANGE_DEFAULT_CREDENTIALS}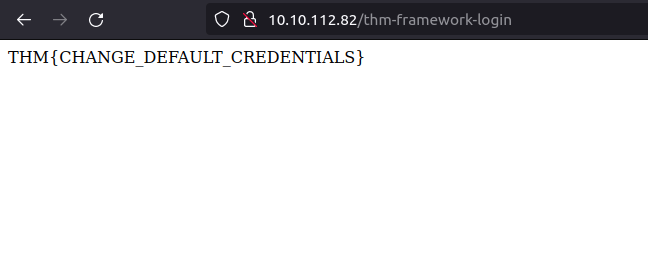
Task 7 – OSINT: Google Hacking / Dorking
Question 1 – What Google dork operator can be used to only show results from a particular site?
site:
Task 8 – OSINT: Wappalyzer
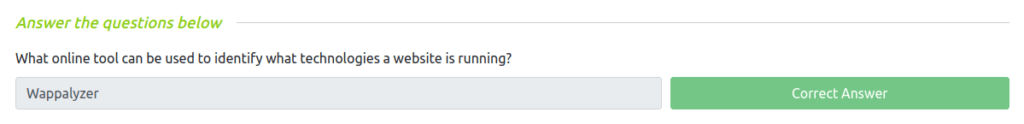
Question 1 – What online tool can be used to identify what technologies a website is running?
Wappalyzer
Task 9 – OSINT: Wayback Machine
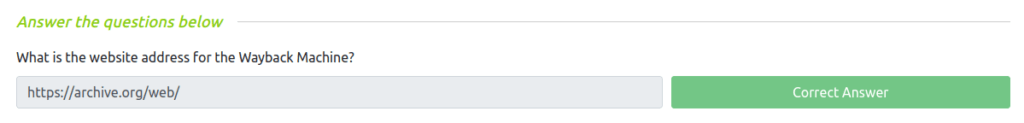
Question 1 – What is the website address for the Wayback Machine?
https://archive.org/web/
Task 10 – OSINT: GitHub
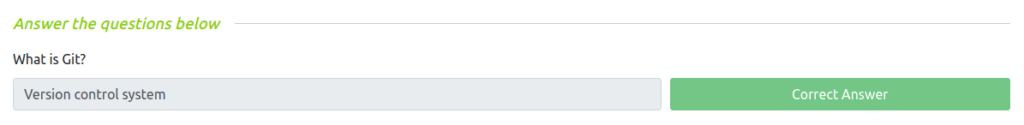
Question 1 – What is Git?
Version control system
Task 11 – OSINT: S3 Buckets
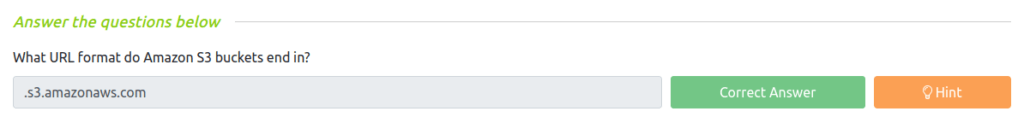
Question 1 – What URL format do Amazon S3 buckets end in?
.s3.amazonaws.com
Task 12 – Automated Discovery
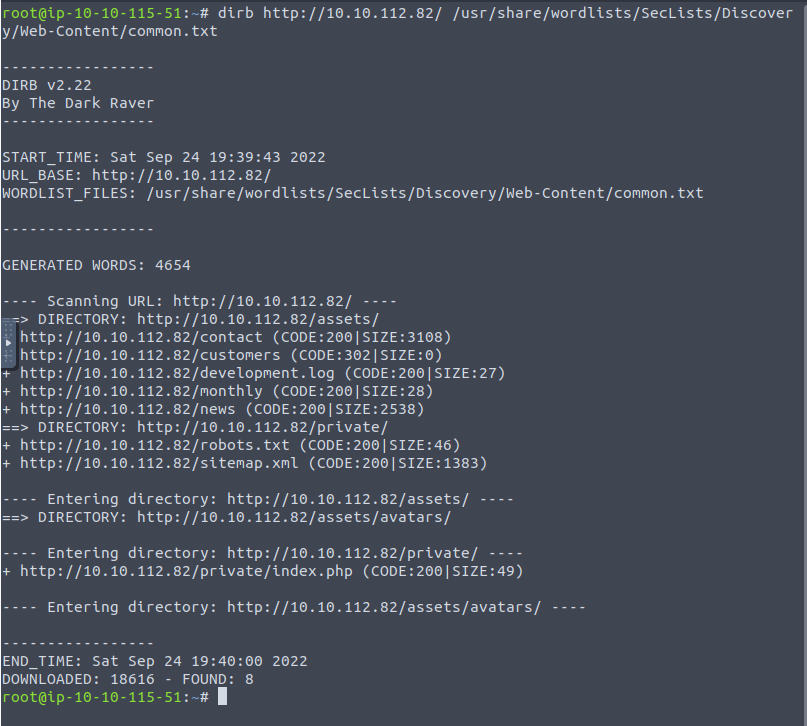
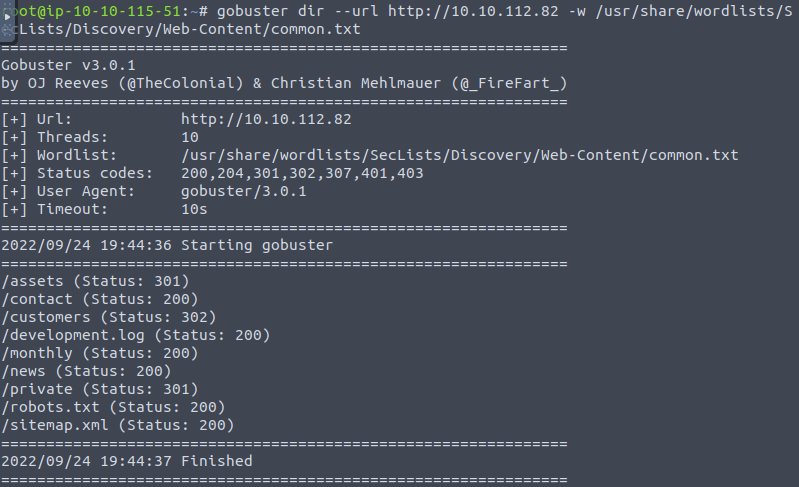
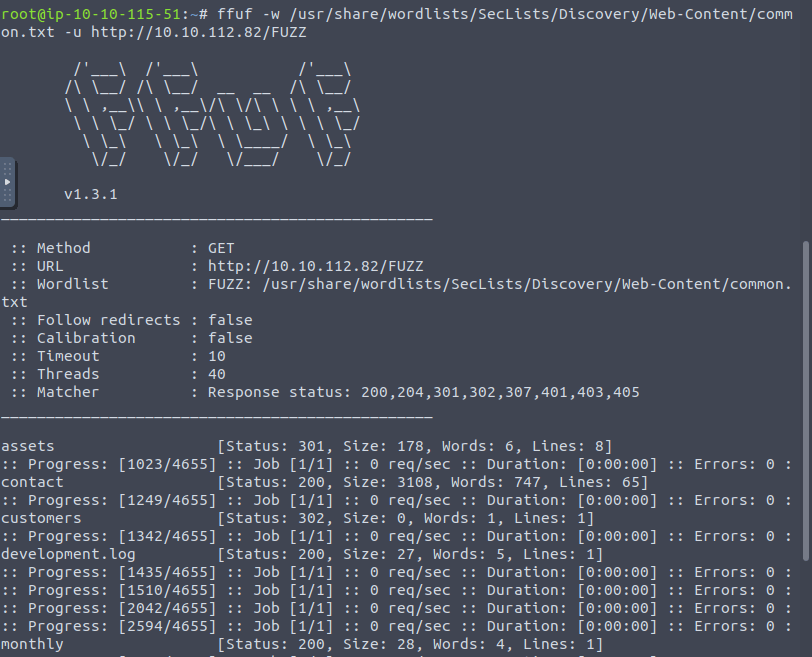
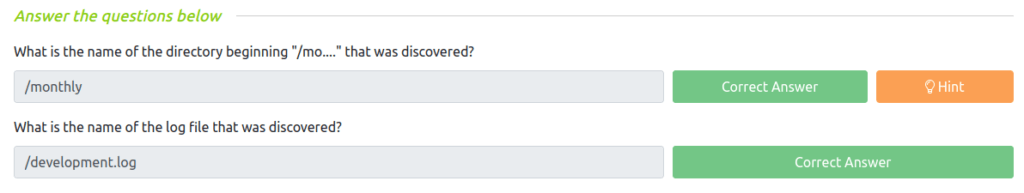
Question 1 – What is the name of the directory beginning “/mo….” that was discovered?
/monthly
Question 2 – What is the name of the log file that was discovered?
/development.log
Also Read: Tryhackme – Chill Hack
Conclusion:

So this was “Content Discovery” room for you. We covers the basics of content discovery from robots.txt to directory bruteforcing with different tools. Getting familiar with these techniques and tools will definitely help you in your bug bounty journey. So on that note, i will take your leave for the day but remember to “Hack the planet” for the meanwhile.




