In this walk through, we will be going through the Introduction to Cryptography room from Tryhackme. This room is rated as Medium on the platform and we will learn about encryption algorithms such as AES, Diffie-Hellman key exchange, hashing, PKI, and TLS. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction
Question 1 – You can guess that it is a quote. Who said it?
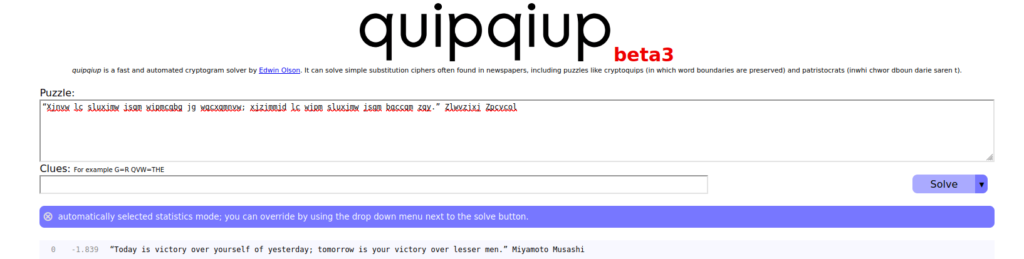
Miyamoto Musashi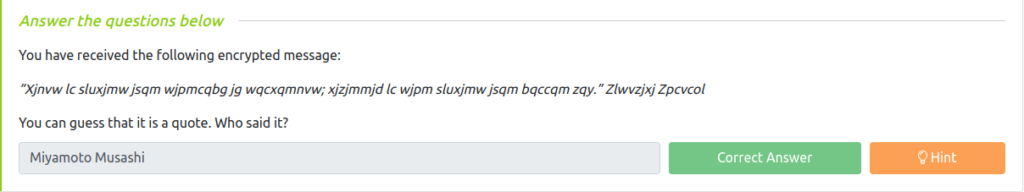
Task 2 – Symmetric Encryption
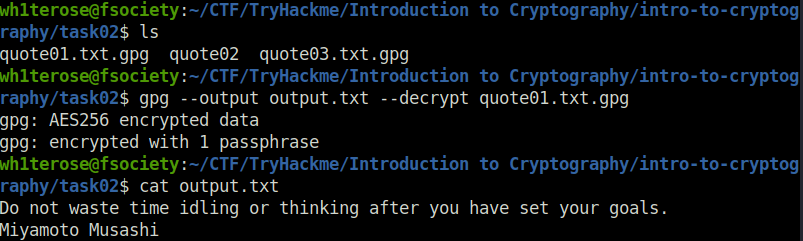
Question 1 – Decrypt the file quote01 encrypted (using AES256) with the key s!kR3T55 using gpg. What is the third word in the file?
wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task02$ ls quote01.txt.gpg quote02 quote03.txt.gpg wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task02$ gpg --output output.txt --decrypt quote01.txt.gpg gpg: AES256 encrypted data gpg: encrypted with 1 passphrase wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task02$ cat output.txt Do not waste time idling or thinking after you have set your goals. Miyamoto Musashi
wasteQuestion 2 – Decrypt the file quote02 encrypted (using AES256-CBC) with the key s!kR3T55 using openssl. What is the third word in the file?
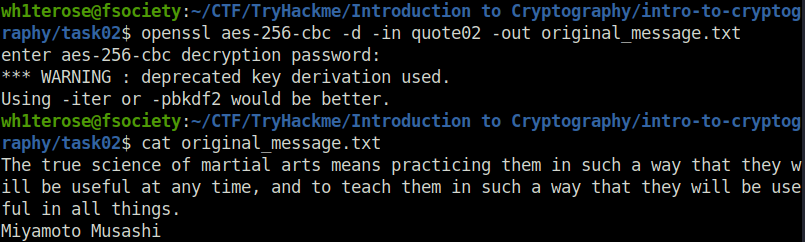
wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task02$ openssl aes-256-cbc -d -in quote02 -out original_message.txt enter aes-256-cbc decryption password: *** WARNING : deprecated key derivation used. Using -iter or -pbkdf2 would be better. wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task02$ cat original_message.txt The true science of martial arts means practicing them in such a way that they will be useful at any time, and to teach them in such a way that they will be useful in all things. Miyamoto Musashi
scienceQuestion 3 – Decrypt the file quote03 encrypted (using CAMELLIA256) with the key s!kR3T55 using gpg. What is the third word in the file?
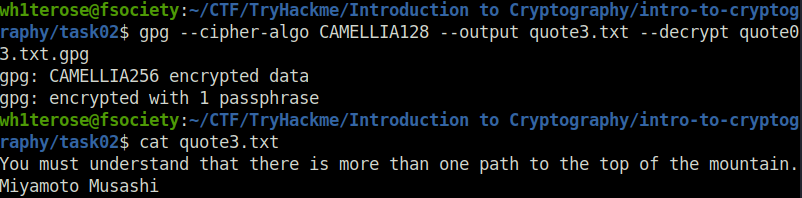
raphy/task02$ gpg --cipher-algo CAMELLIA128 --output quote3.txt --decrypt quote03.txt.gpg gpg: CAMELLIA256 encrypted data gpg: encrypted with 1 passphrase wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task02$ cat quote3.txt You must understand that there is more than one path to the top of the mountain. Miyamoto Musashi
understand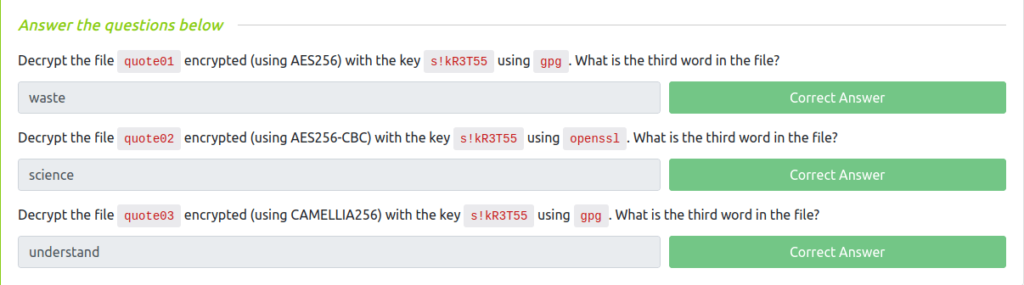
Task 3 – Asymmetric Encryption
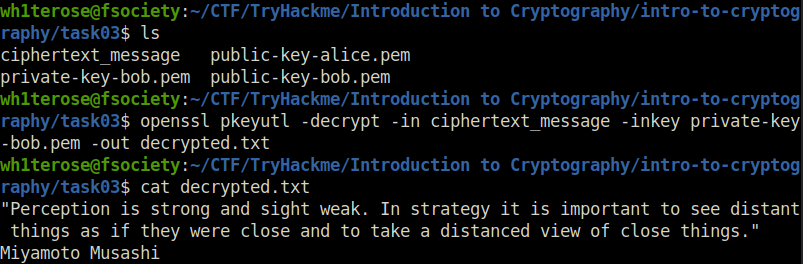
Question 1 – Bob has received the file ciphertext_message sent to him from Alice. You can find the key you need in the same folder. What is the first word of the original plaintext?
wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task03$ openssl pkeyutl -decrypt -in ciphertext_message -inkey private-key-bob.pem -out decrypted.txt wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task03$ cat decrypted.txt "Perception is strong and sight weak. In strategy it is important to see distant things as if they were close and to take a distanced view of close things." Miyamoto Musashi
Question 2 – Take a look at Bob’s private RSA key. What is the last byte of p?
openssl rsa -in private-key-bob.pem -text -noout
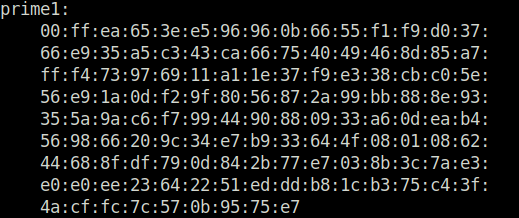
e7Question 3 – Take a look at Bob’s private RSA key. What is the last byte of q?
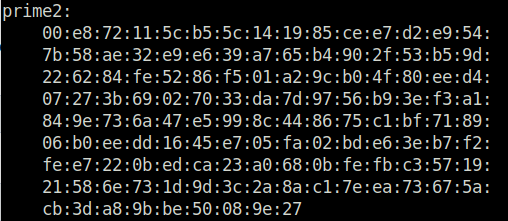
27
Task 4 – Diffie-Hellman Key Exchange
Question 1 – A set of Diffie-Hellman parameters can be found in the file dhparam.pem. What is the size of the prime number in bits?
openssl dhparam -in dhparams.pem -text -noout
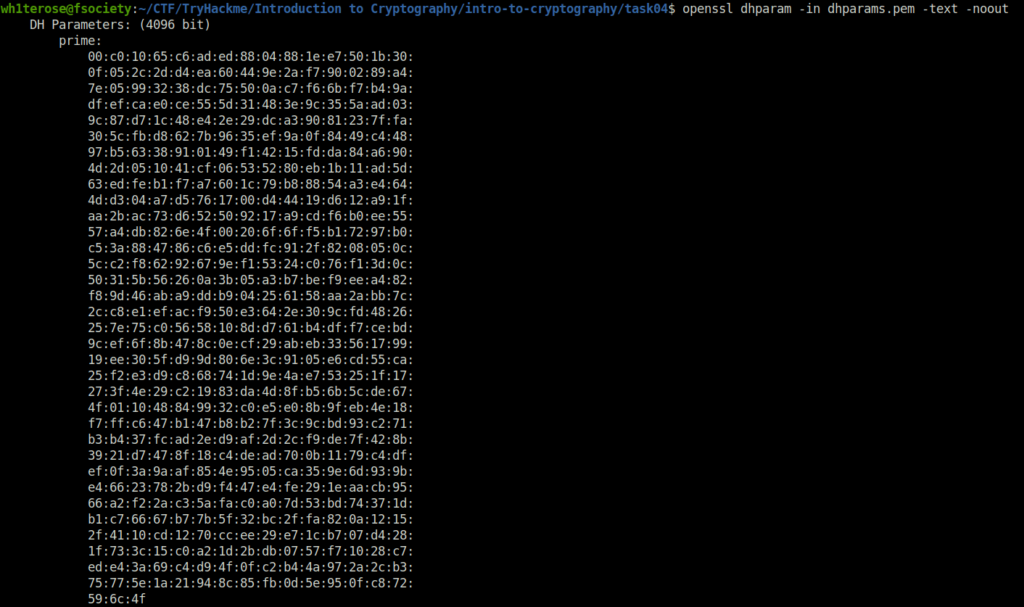
4096Question 2 – What is the prime number’s last byte (least significant byte)?
4f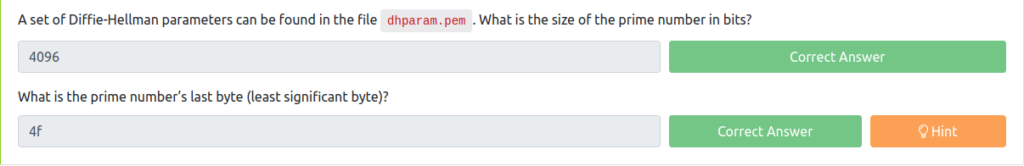
Task 5 – Hashing
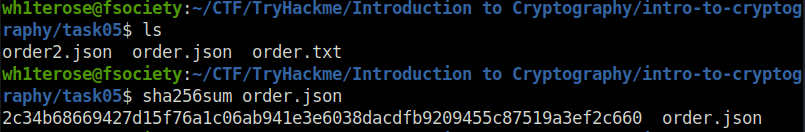
Question 1 – What is the SHA256 checksum of the file order.json?
wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task05$ sha256sum order.json 2c34b68669427d15f76a1c06ab941e3e6038dacdfb9209455c87519a3ef2c660 order.json
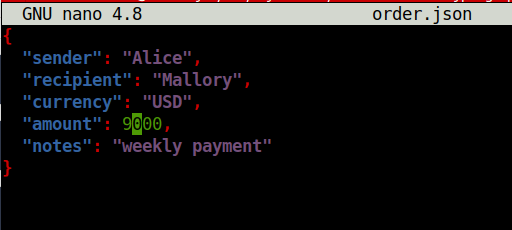
2c34b68669427d15f76a1c06ab941e3e6038dacdfb9209455c87519a3ef2c660Question 2 – Open the file order.json and change the amount from 1000 to 9000. What is the new SHA256 checksum?
wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task05$ nano order.json wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task05$ sha256sum order.json 11faeec5edc2a2bad82ab116bbe4df0f4bc6edd96adac7150bb4e6364a238466 order.jso
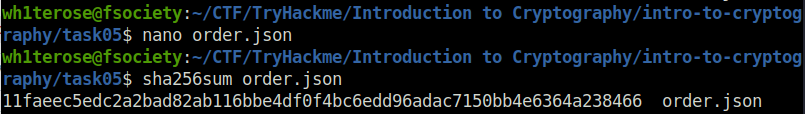
11faeec5edc2a2bad82ab116bbe4df0f4bc6edd96adac7150bb4e6364a238466Question 3 – Using SHA256 and the key 3RfDFz82, what is the HMAC of order.txt?
wh1terose@fsociety:~/CTF/TryHackme/Introduction to Cryptography/intro-to-cryptography/task05$ hmac256 3RfDFz82 order.txt c7e4de386a09ef970300243a70a444ee2a4ca62413aeaeb7097d43d2c5fac89f order.txt
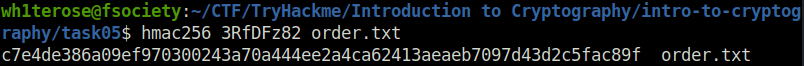
c7e4de386a09ef970300243a70a444ee2a4ca62413aeaeb7097d43d2c5fac89f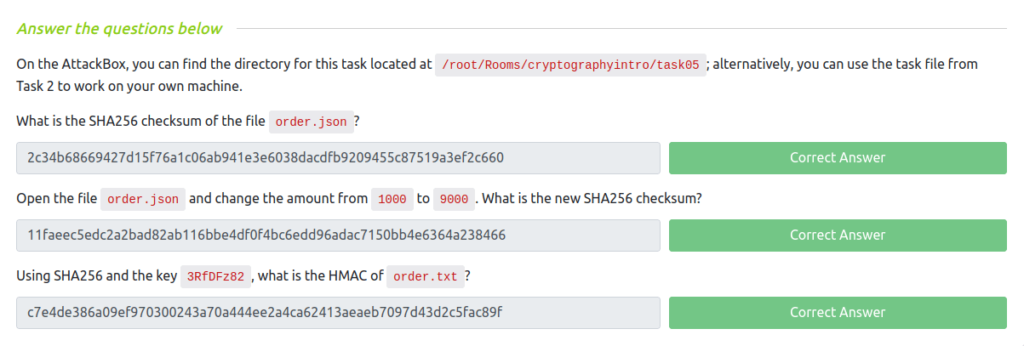
Task 6 – PKI and SSL/TLS
Question 1 – What is the size of the public key in bits?
openssl x509 -in cert.pem -text
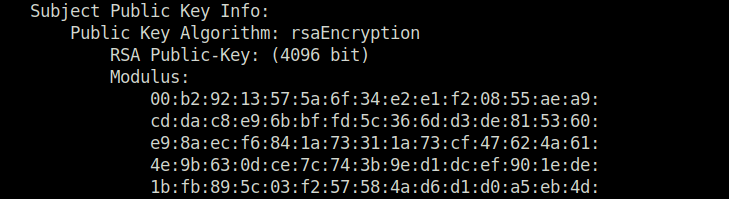
4096Question 2 – Till which year is this certificate valid?
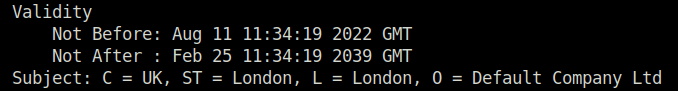
2039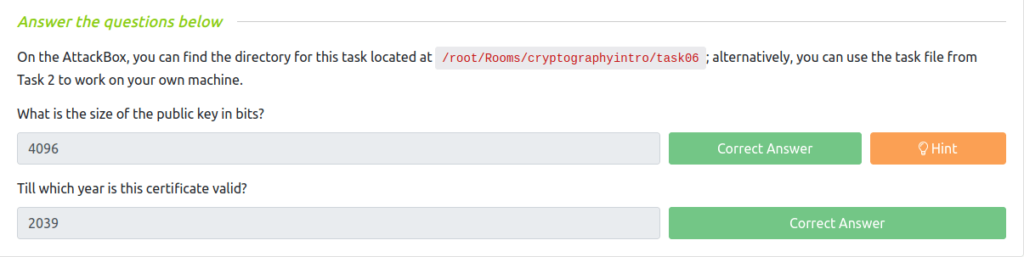
Task 7 – Authenticating with Passwords
Question 1 – You were auditing a system when you discovered that the MD5 hash of the admin password is 3fc0a7acf087f549ac2b266baf94b8b1. What is the original password?
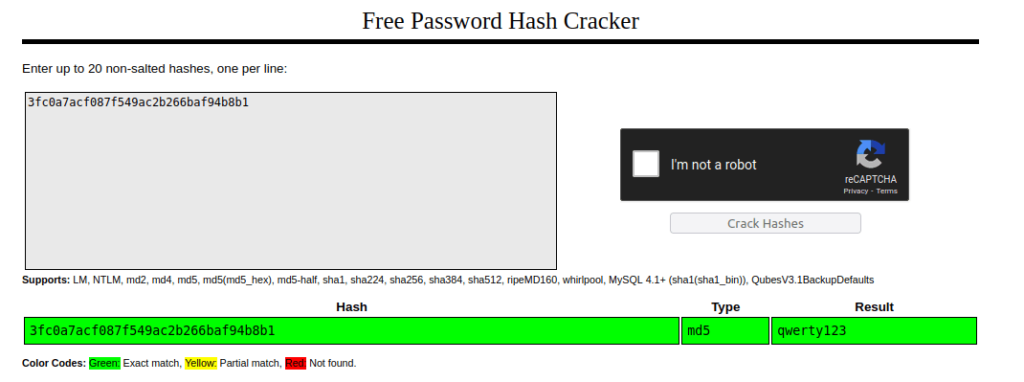
qwerty123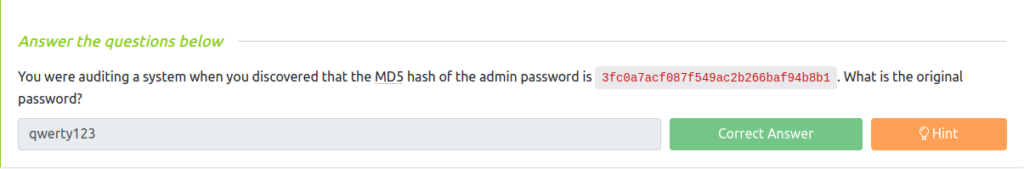
Task 8 – Cryptography and Data – Example
Task 9 – Conclusion
Also Read: Tryhackme – Fowsniff CTF
So that was “Introduction to Cryptography” for you. We learned about the basics of Cryptography. Then we took a deep dive into Symmetric and Asymmetric encryption. Along with that, looked into Diffie-Hellman Key Exchange and Hashing. Moving on, learned about PKI and SSL/TLS. At last, looked into some cryptography usage and completed the room. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




