In this walk through, we will be going through the Metasploit Introduction room from Tryhackme. This room will cover the fundamentals of one of the most popular exploitation framework out there, namely Metasploit. We will cover the components of the framework and how we can use it in exploitation part of our hacking methodology. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction to Metasploit
Metasploit is the most widely used exploitation framework. Metasploit is a powerful tool that can support all phases of a penetration testing engagement, from information gathering to post-exploitation.
Metasploit has two main versions:
- Metasploit Pro: The commercial version that facilitates the automation and management of tasks. This version has a graphical user interface (GUI).
- Metasploit Framework: The open-source version that works from the command line. This room will focus on this version, installed on the AttackBox and most commonly used penetration testing Linux distributions.
The Metasploit Framework is a set of tools that allow information gathering, scanning, exploitation, exploit development, post-exploitation, and more. While the primary usage of the Metasploit Framework focuses on the penetration testing domain, it is also useful for vulnerability research and exploit development.
The main components of the Metasploit Framework can be summarized as follows:
- msfconsole: The main command-line interface.
- Modules: supporting modules such as exploits, scanners, payloads, etc.
- Tools: Stand-alone tools that will help vulnerability research, vulnerability assessment, or penetration testing. Some of these tools are msfvenom, pattern_create and pattern_offset. We will cover msfvenom within this module, but pattern_create and pattern_offset are tools useful in exploit development which is beyond the scope of this module.
Task 2 – Main Components of Metasploit
Question 1 – What is the name of the code taking advantage of a flaw on the target system?
exploitQuestion 2 – What is the name of the code that runs on the target system to achieve the attacker’s goal?
payloadQuestion 3 – What are self-contained payloads called?
singlesQuestion 4 – Is “windows/x64/pingback_reverse_tcp” among singles or staged payload?
singles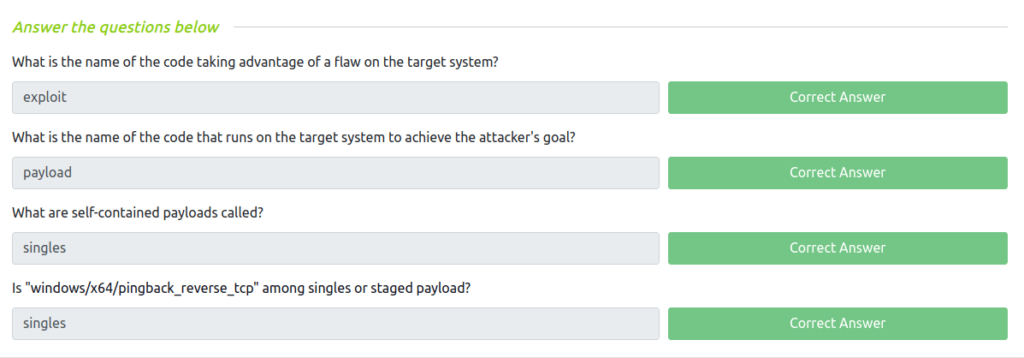
Task 3 – Msfconsole
Question 1 – How would you search for a module related to Apache?
search ApacheQuestion 2 – Who provided the auxiliary/scanner/ssh/ssh_login module?
info auxiliary/scanner/ssh/ssh_login module
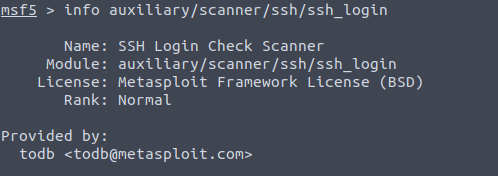
todb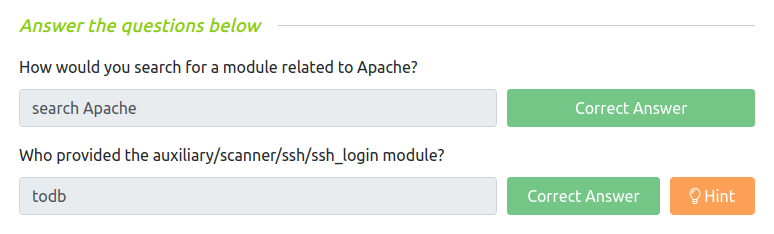
Task 4 – Working with modules
Question 1 – How would you set the LPORT value to 6666?
set LPORT 6666Question 2 – How would you set the global value for RHOSTS to 10.10.19.23 ?
setg RHOSTS 10.10.19.23Question 3 – What command would you use to clear a set payload?
unset PAYLOADQuestion 4 – What command do you use to proceed with the exploitation phase?
exploit
Task 5 – Summary
Also Read: Tryhackme – Linux PrivEsc Arena
So that was “Metasploit: Introduction” for you. In this room, we have covered about the fundamentals of the exploitation framework, Metasploit. We looked into the main components of the framework, modules and its basic usage which can help us in the exploitation phase of our hacking methodology. Metasploit had hundreds of exploits, payloads and auxiliary modules for number of software, service and protocols. So, play it with to understand it more. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




