In this walk through, we will be going through the Principles of Security room from Tryhackme. This room will teach us about the principles of information security that secures data and protects systems from abuse. On that note, let’s get started.
Table of Contents
Task 1 – Introduction
Task 2 – The CIA Triad
Question 1 – What element of the CIA triad ensures that data cannot be altered by unauthorised people?
IntegrityQuestion 2 – What element of the CIA triad ensures that data is available?
AvailabilityQuestion 3 – What element of the CIA triad ensures that data is only accessed by authorised people?
Confidentiality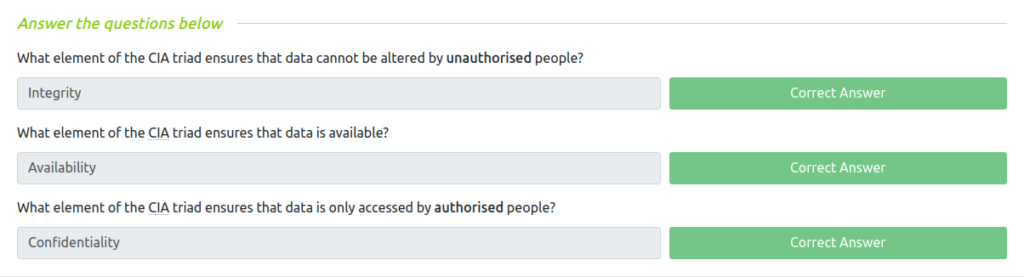
Task 3 – Principles of Privileges
Question 1 – What does the acronym “PIM” stand for?
Privileged Identity ManagementQuestion 2 – What does the acronym “PAM” stand for?
Privileged Access ManagementQuestion 3 – If you wanted to manage the privileges a system access role had, what methodology would you use?
PAMQuestion 4 – If you wanted to create a system role that is based on a users role/responsibilities with an organisation, what methodology is this?
PIM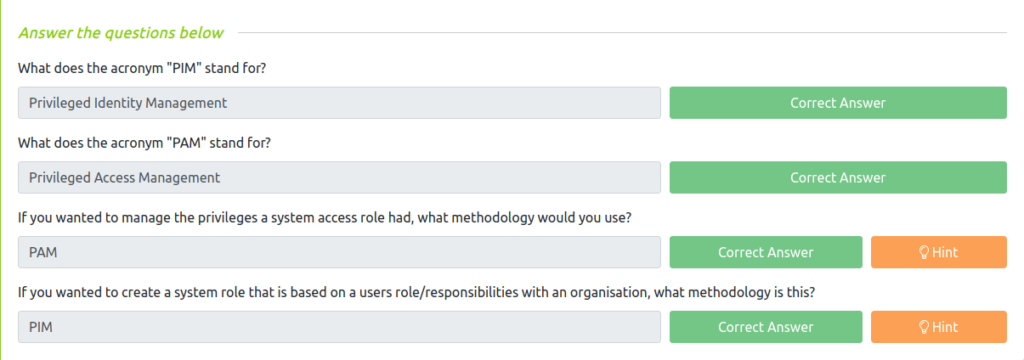
Task 4 – Security Models Continued
Question 1 – What is the name of the model that uses the rule “can’t read up, can read down”?
The Bell-LaPadula ModelQuestion 2 – What is the name of the model that uses the rule “can read up, can’t read down”?
The Biba modelQuestion 3 – If you were a military, what security model would you use?
The Bell-LaPadula ModelQuestion 4 – If you were a software developer, what security model would the company perhaps use?
The Biba model
Task 5 – Threat Modelling & Incident Response
Question 1 – What model outlines “Spoofing”?
STRIDEQuestion 2 – What does the acronym “IR” stand for?
Incident ResponseQuestion 3 – You are tasked with adding some measures to an application to improve the integrity of data, what STRIDE principle is this?
TamperingQuestion 4 – An attacker has penetrated your organisation’s security and stolen data. It is your task to return the organisation to business as usual. What incident response stage is this?
Recovery
Also Read: Tryhackme – Pickle Rick
So that was “Principles of Security” for you. In this room, we have learned the principles of information security that secures data and protects systems from abuse. We have covered topics like the CIA triad, Principles of privileges, Security Models, Threat Intelligence and Incident Response and more. On that note, i will take your leave and meet you in next one. So stay tuned and till then, “Hack the planet”.




