In this walk through, we will be going through the Sakura Room from Tryhackme. This room will take us through a sample OSINT investigation in which we will be asked to identify a number of identifiers and other pieces of information in order to help catch a cybercriminal by using a wide variety of OSINT techniques. So, let’s get started without any delay.
Table of Contents
Task 1 – INTRODUCTION
Question 1 – Are you ready to begin?
Let's Go!
Task 2 – TIP-OFF
Question 1 – What username does the attacker go by?

- I used the below online exifdata viewer and found the location of the home directory of the attacker in SVG:Export-filename attribute which reveals the username.
- Exif Data Viewer – https://exifmeta.com/
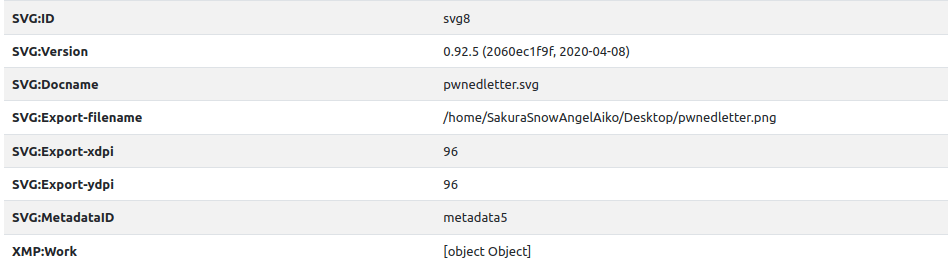
SakuraSnowAngelAiko
Task 3 – RECONNAISSANCE
Question 1 – What is the full email address used by the attacker?
- I used sherlock to hunt down any social media accounts with the previously found username. Got a valid hit for Github.
python3 sherlock.py SakuraSnowAngelAiko
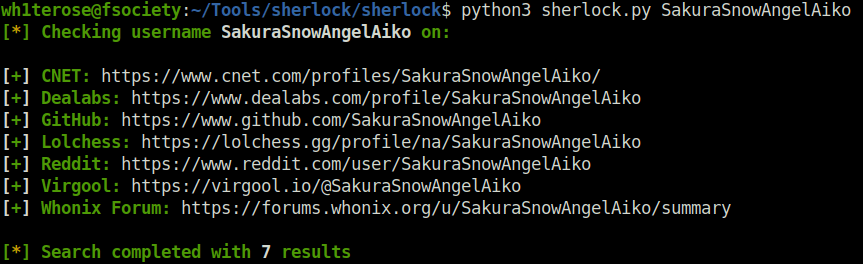
- In the github account, one of the repo has a public key in it.
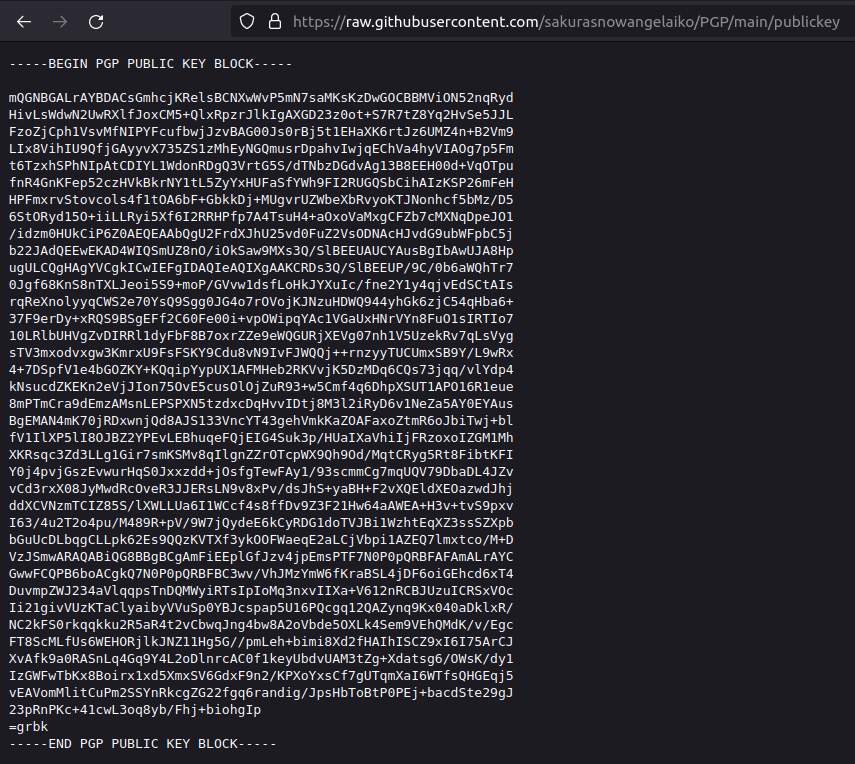
- Decoded the public key using gpg which reveals the email address of the attacker.
gpg -v publickey.asc
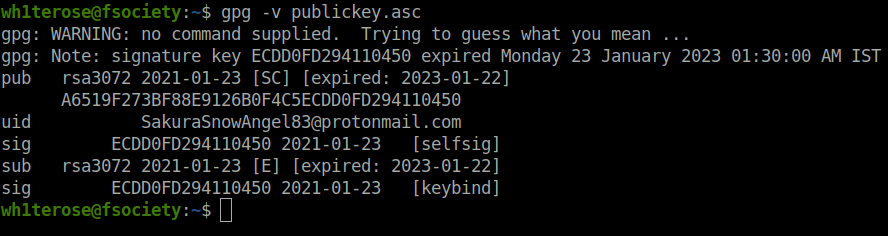
[email protected]Question 2 – What is the attacker’s full real name?
- I searched the username on the Google also and got a result of a twitter account which seems like it belongs to our attacker.
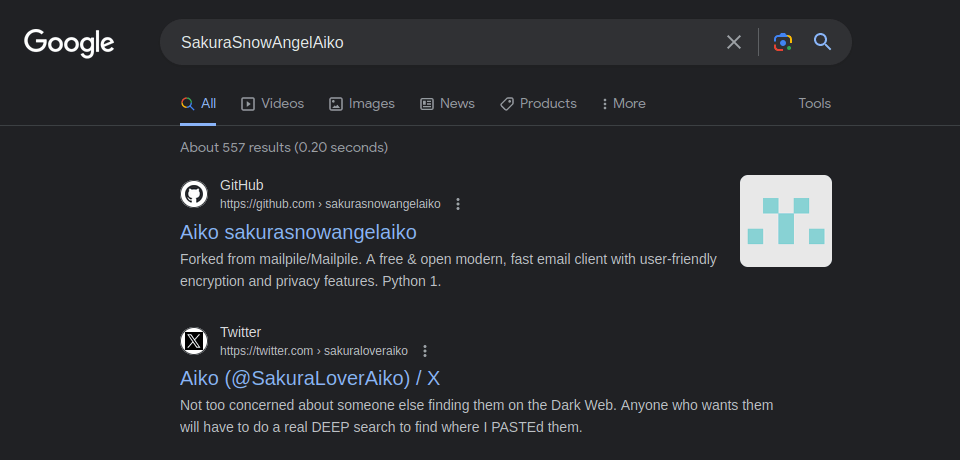
- Got a post from the attacker’s account which links his another account that reveals his real name.
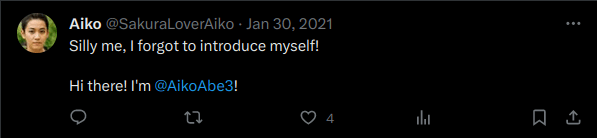
Aiko Abe
Task 4 – UNVEIL
Question 1 – What cryptocurrency does the attacker own a cryptocurrency wallet for?
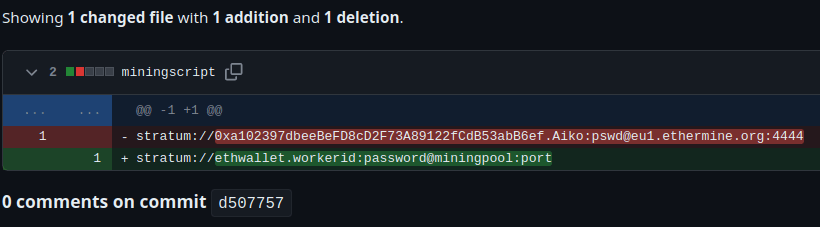
- As per the github repo the attacker has a mining script for the ETH or Ethereum coin.
ethereumQuestion 2 – What is the attacker’s cryptocurrency wallet address?
- I found the attacker’s crypto wallet address in the very first commit of the mining script.
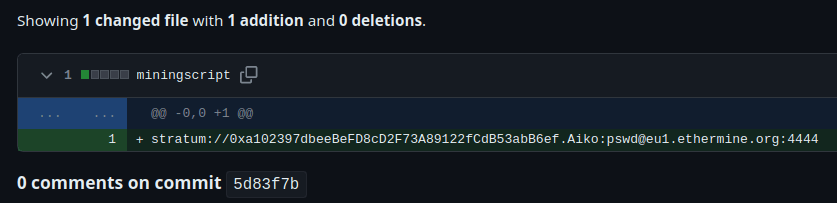
0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6efQuestion 3 – What mining pool did the attacker receive payments from on January 23, 2021 UTC?
ethermineQuestion 4 – What other cryptocurrency did the attacker exchange with using their cryptocurrency wallet?
- I used blockchain viewer and got a transaction hit for Tether coin from the attacker’s wallet address.
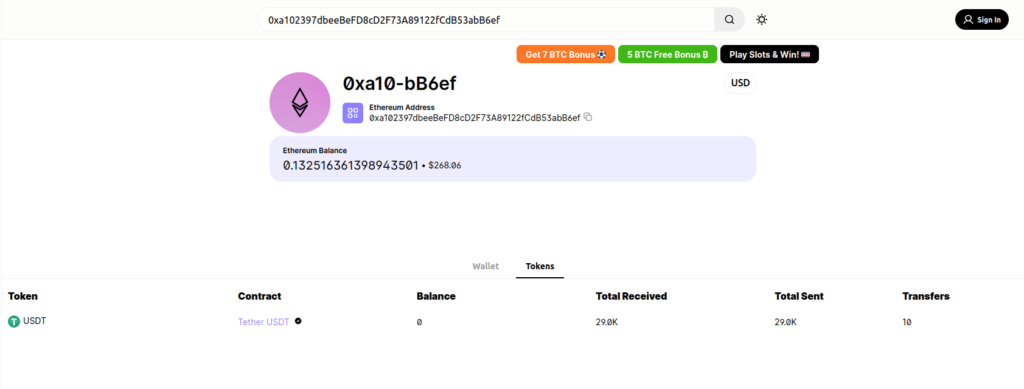
Tether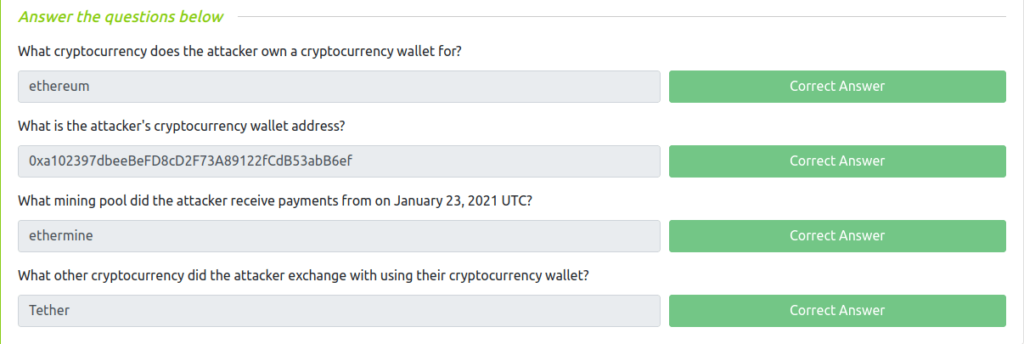
Task 5 – TAUNT
Question 1 – What is the attacker’s current Twitter handle?
- As we have already found the attacker’s twitter account. This was easy.
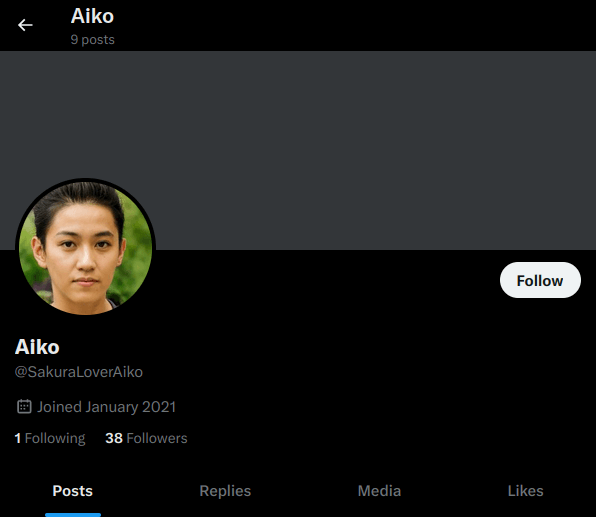
SakuraLoverAikoQuestion 2 – What is the URL for the location where the attacker saved their WiFi SSIDs and passwords?
- I was not able to resolve the Darkweb address as there was no post where i can see that mentioned. Moreover, it did not get resolve as per the hint too.
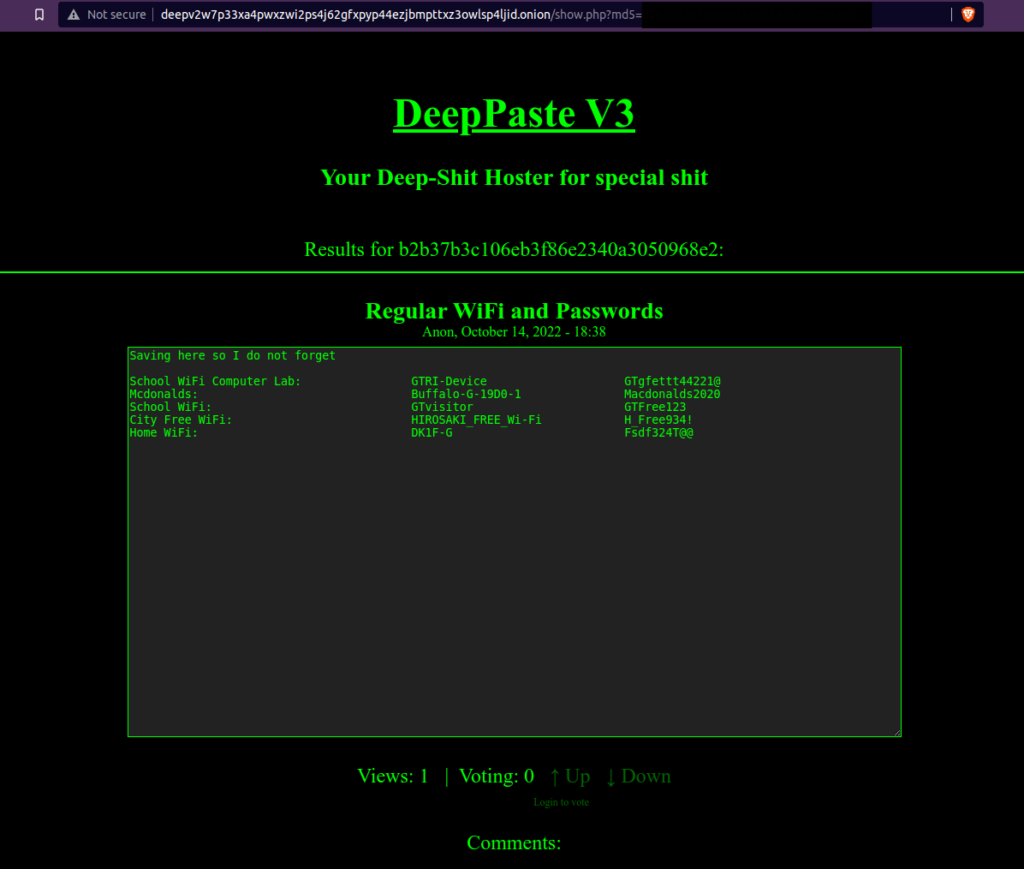
deepv2w7p33xa4pwxzwi2ps4j62gfxpyp44ezjbmpttxz3owlsp4ljid.onion/show.php?md5=b2b37b3c106eb3f86e2340a3050968e2Question 3 – What is the BSSID for the attacker’s Home WiFi?
- Used Wigle’s Advance search and got a hit for the attacker’s SSID name.
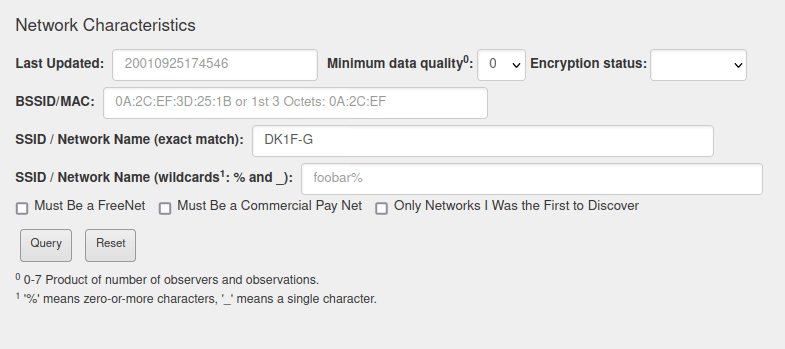
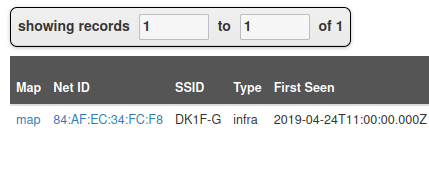
84:AF:EC:34:FC:F8
Task 6 – HOMEBOUND
Question 1 – What airport is closest to the location the attacker shared a photo from prior to getting on their flight?
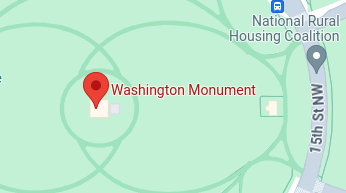
- As per the latest picture, we can see the Washington monument in the background.

- I looked up the monument in Google maps and search for the nearby airports. The “Ronald Reagan Washington National Airport” stood up in the results.
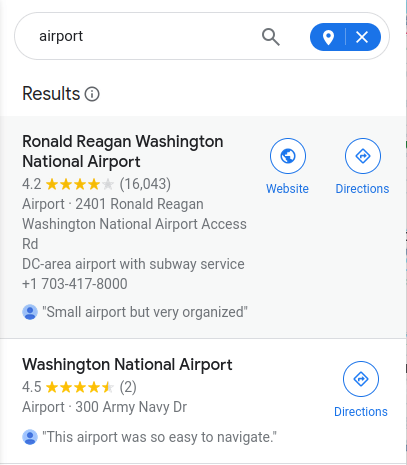
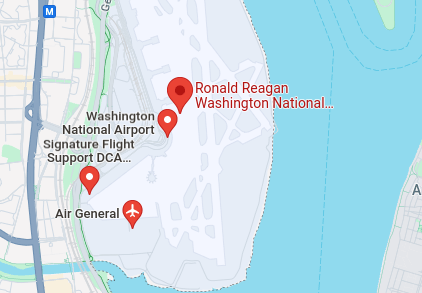
- Looked the 3 digit code for it and got our answer.
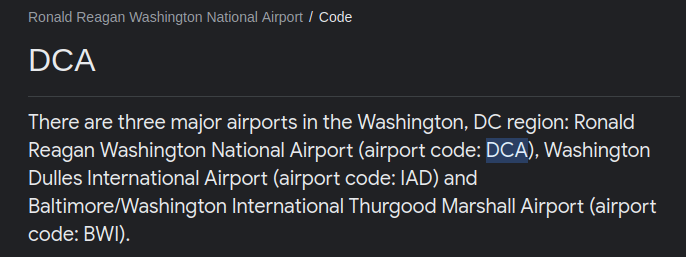
DCAQuestion 2 – What airport did the attacker have their last layover in?
- The next picture was where the attacker has his last layover. I looked up for “Jal Sakura Lounge Skytrax” on google and got result for Haneda Airport.

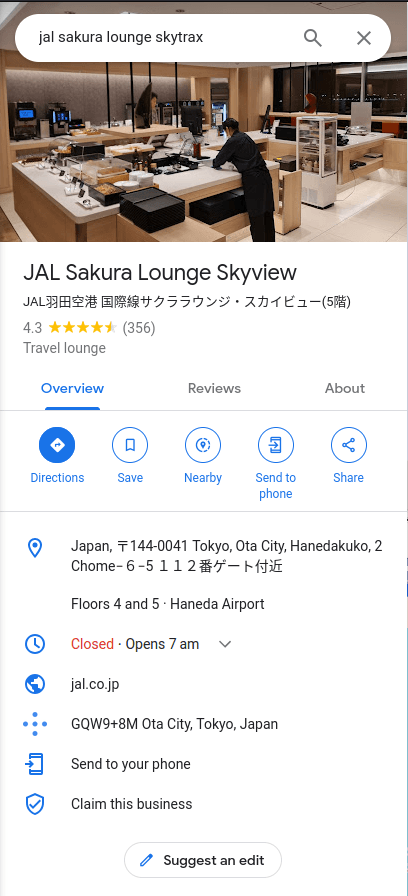
- Looked up the code for it and turns out to be “HND”.
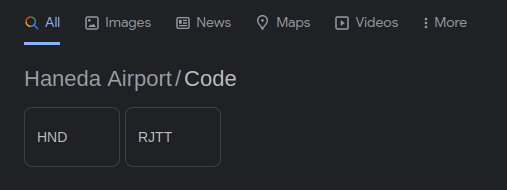
HNDQuestion 3 – What lake can be seen in the map shared by the attacker as they were on their final flight home?
- The next picture has a map which has a small water body (lake) in the center of it. I performed a reverse image search on this and then looked it up on the map. Found out that the lake in the center is “Lake Inawashiro”.
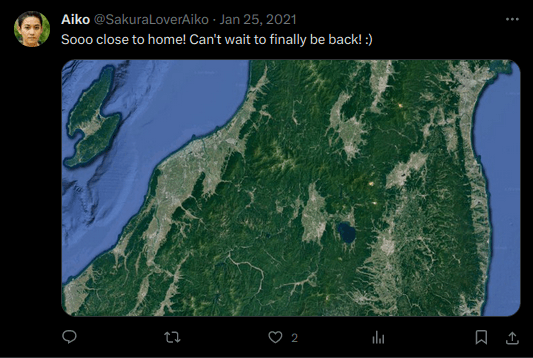
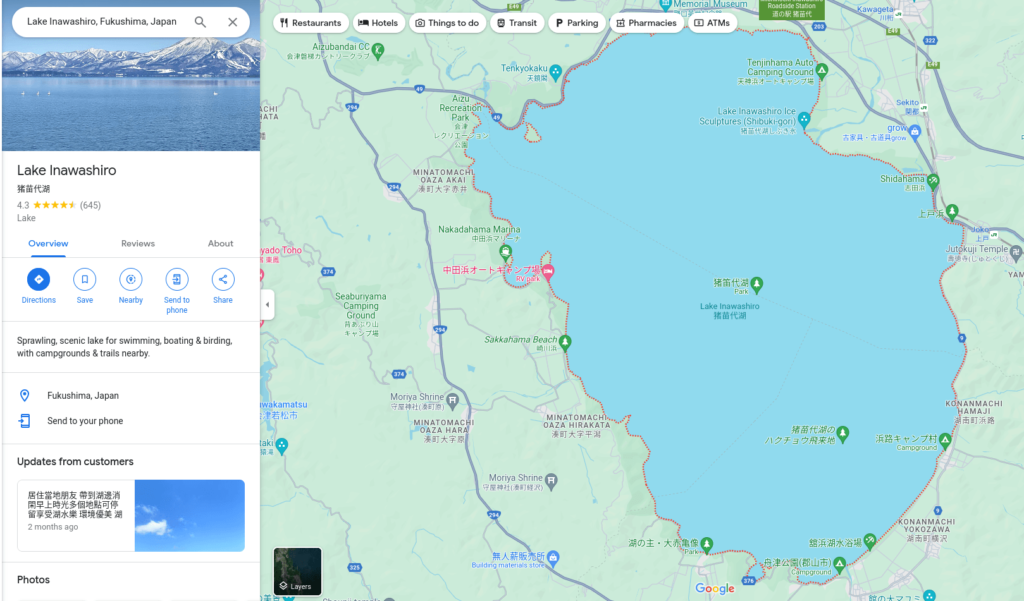
Lake InawashiroQuestion 4 – What city does the attacker likely consider “home”?
- For the attacker’s home address, i looked into the Wigel BSSID result again. Opened up the inbuilt map on it and clicked on attacker’s SSID which reveals an address in Japan. Translated it using google translate that gave me the home address of the attacker.
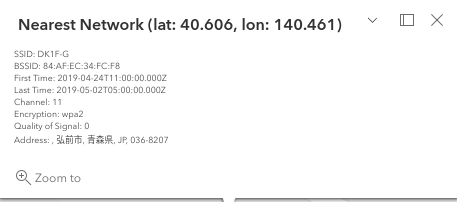
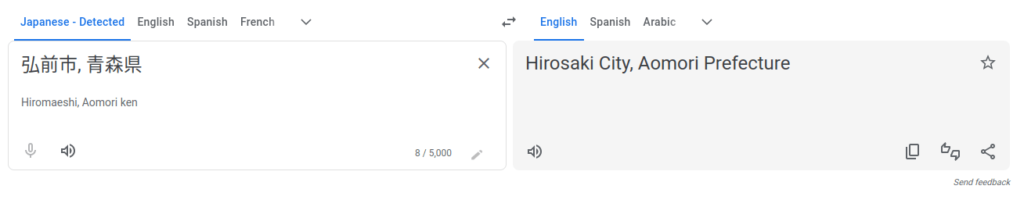
Hirosaki
Also Read: Tryhackme – Phishing Emails in Action
So that was “Sakura Room” for you. We started off with an image and checked its exif data. There we found the potential username of the attacker. Performing recon using sherlock and google search on the username reveals a github and twitter account. The github has a gpg key stored in it. Decoding it reveals the email address of the attacker. Moving on, from the twitter account we also found the attacker’s real name. Next, we looked into the github account thoroughly and found the crypto wallet address and mining pool the attacker was using. With the help of the wallet address, we came to know that attacker has used Tether crypto as an exchange current using his wallet. Further, from his twitter account, we got a hint that he had stored his MAC address in a paste website on deep web. Found the ESSID of the attacker’s home Wifi and got his router’s MAC address. Next, we trailed the attacker’s journey from Ronald Reagan Airport to Haneda Airport indicating Lake Inawashiro and finally to his home. At last, the BSSID reveals the attacker’s city and address when looked into the Wigle map and that’s how we completed the room. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




