In this walk through, we will be going through the Wazuh room from Tryhackme. In this room we will learn about Wazuh, which is a free, open source and enterprise-ready security monitoring solution for threat detection and integrity monitoring. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction
Question 1 – When was Wazuh released?
2015Question 2 – What is the term that Wazuh calls a device that is being monitored for suspicious activity and potential security threats?
AgentQuestion 3 – Lastly, what is the term for a device that is responsible for managing these devices?
Manager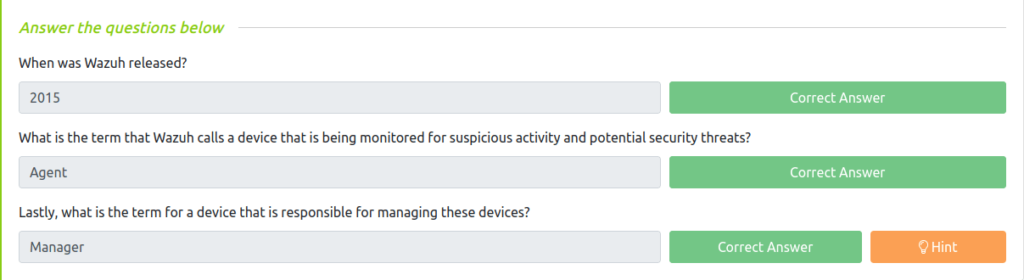
Task 2 – Required: Deploy Wazuh Server
Question 1 – Login to the Wazuh management server on HTTPS://10.10.183.190 before proceeding with this room’s tasks.
Done
Task 3 – Wazuh Agents
Question 1 – Ensure that you are logged in to the Wazuh management server on HTTPS://10.10.183.190
DoneQuestion 2 – Navigate to the “Agents” tab by pressing Wazuh -> Agents
Done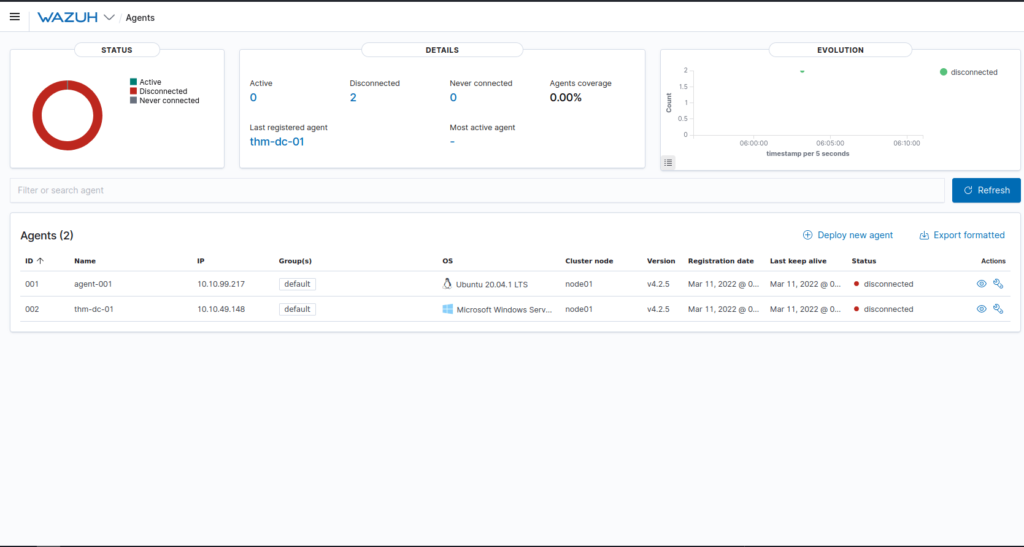
Question 3 – How many agents does this Wazuh management server manage?
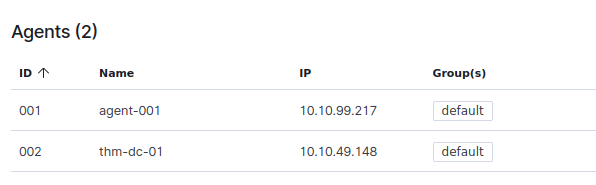
2Question 4 – What are the status of the agents managed by this Wazuh management server?
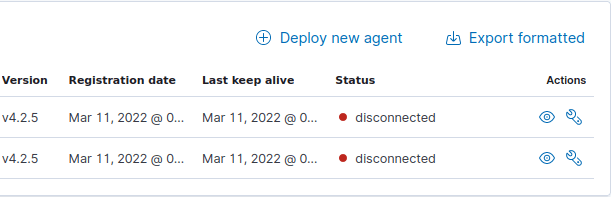
Disconnected
Task 4 – Wazuh Vulnerability Assessment & Security Events
Question 1 – Ensure that you are logged in to the Wazuh management server on HTTPS://10.10.183.190
DoneQuestion 2 – Navigate to the Agents tab by pressing Wazuh -> Agents like so
Done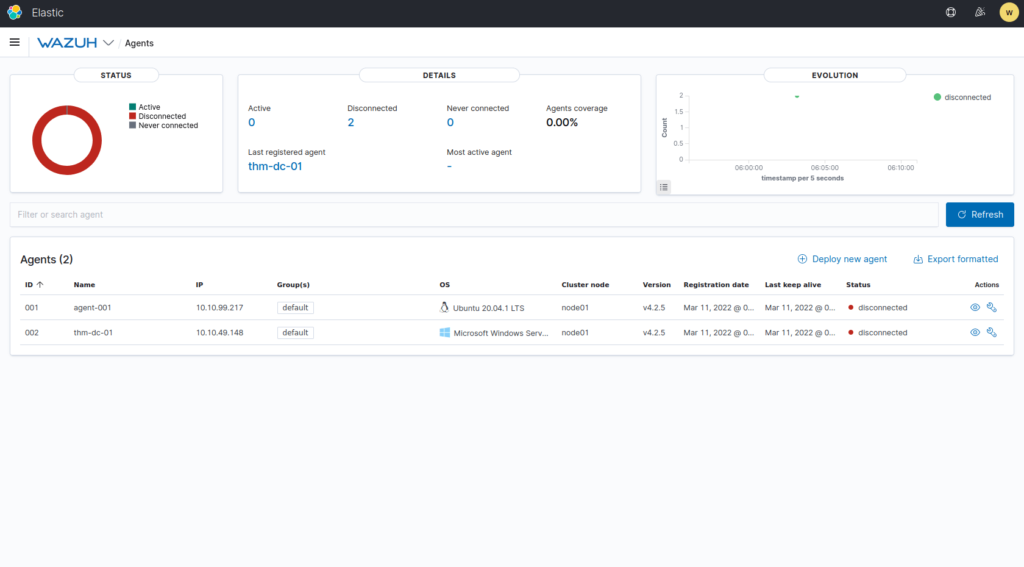
Question 3 – Select the agent named “AGENT-001“
Done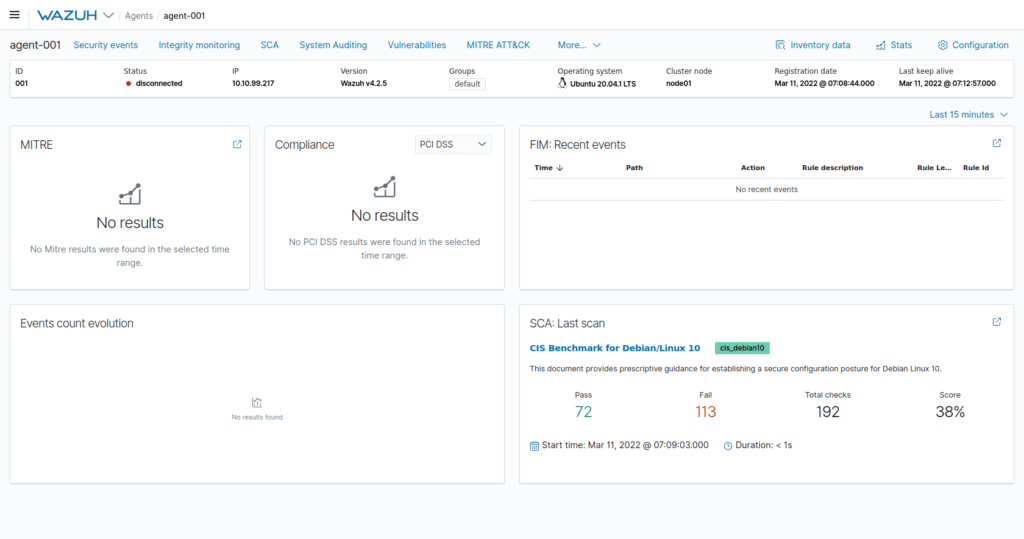
Question 4 – How many “Security Event” alerts have been generated by the agent “AGENT-001”?
Note: You will need to make sure that your time range includes the 11th of March 2022
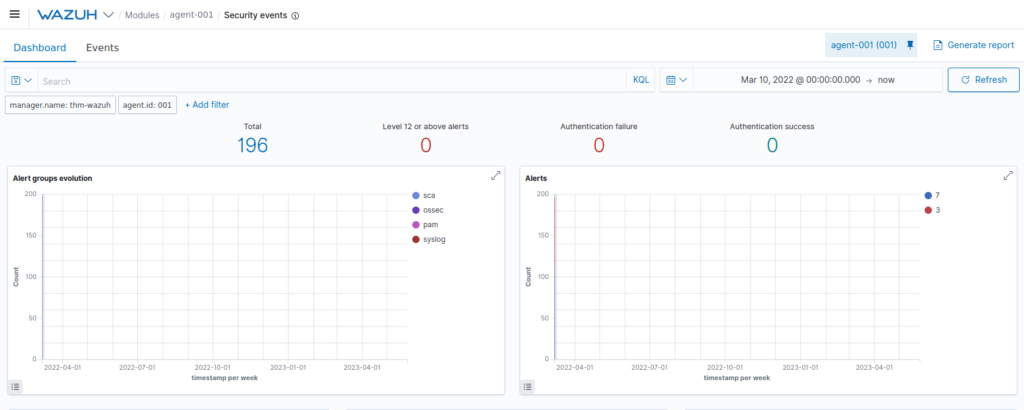
196
Task 5 – Wazuh Policy Auditing
Question 1 – Ensure that you are logged in to the Wazuh management server on [10.10.183.190](https://tryhackme.com/room/MACHINE_IP target=)
DoneQuestion 2 – Navigate to the “Modules” tab by pressing Wazuh -> Modules and open the “Policy Management” module like so:
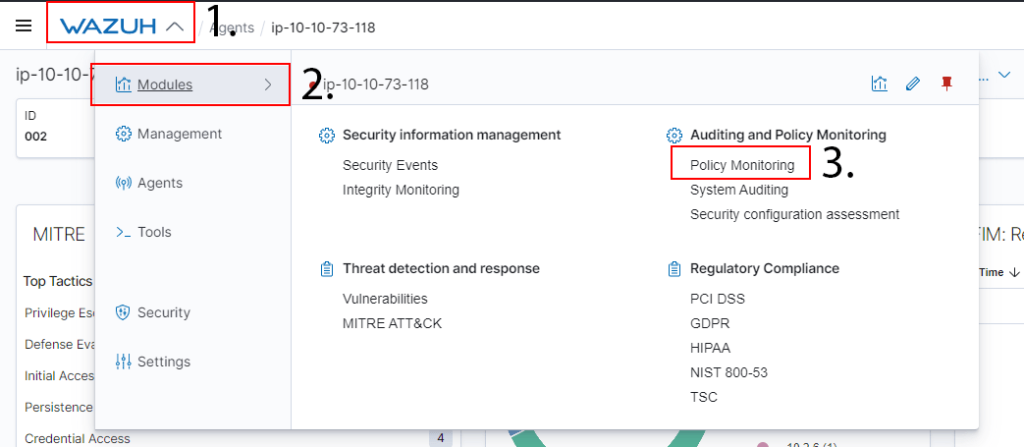
DoneTask 6 – Monitoring Logons with Wazuh
Question 1 – Ensure that you are logged in to the Wazuh management server on [10.10.229.53](https://tryhackme.com/room/10.10.229.53 target=)
DoneQuestion 2 – Navigate to the “Management” tab by pressing Wazuh -> Management and open the “Rules” module like so:
Done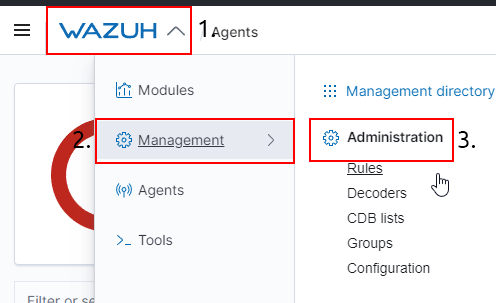
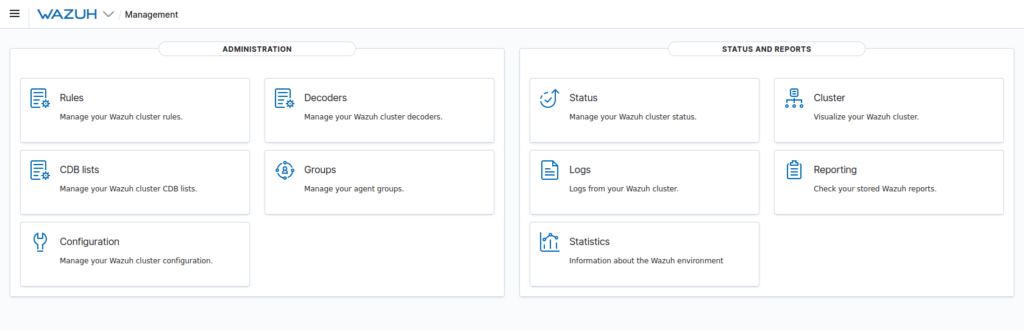
Task 7 – Collecting Windows Logs with Wazuh
Question 1 – What is the name of the tool that we can use to monitor system events?
SysmonQuestion 2 – What standard application on Windows do these system events get recorded to?
Event Viewer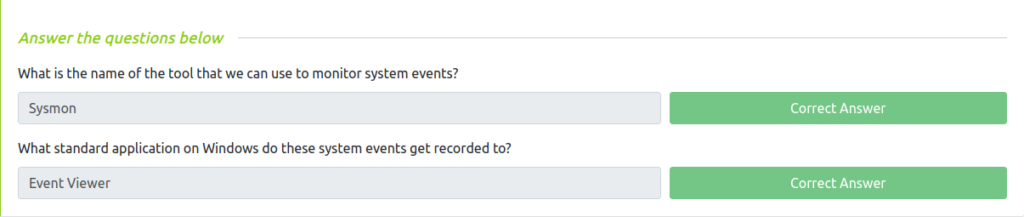
Task 8 – Collecting Linux Logs with Wazuh
Question 1 – What is the full file path to the rules located on a Wazuh management server?
/var/ossec/ruleset/rules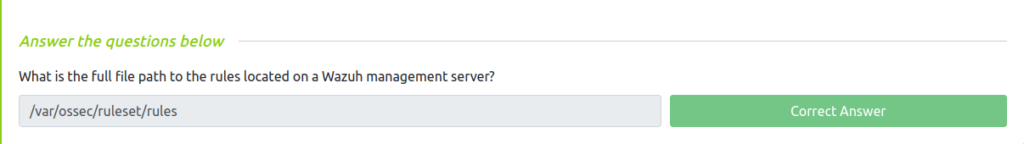
Task 9 – Auditing Commands on Linux with Wazuh
Question 1 – What application do we use on Linux to monitor events such as command execution?
auditdQuestion 2 – What is the full path & filename for where the aforementioned application stores rules?
/etc/audit/rules.d/audit.rules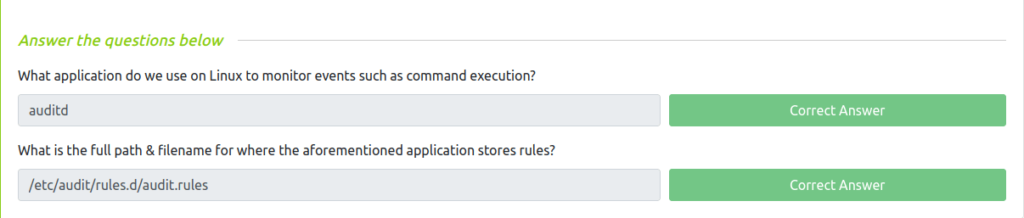
Task 10 – Wazuh API
Question 1 – What is the name of the standard Linux tool that we can use to make requests to the Wazuh management server?
curlQuestion 2 – What HTTP method would we use to retrieve information for a Wazuh management server API?
GETQuestion 3 – What HTTP method would we use to perform an action on a Wazuh management server API?
PUTQuestion 4 – Navigate to Wazuh’s API console.
DoneQuestion 5 – Use the API console to find the Wazuh server’s version.
Note: You will need to add the “v” prefix to the number for this answer. For example v1.2.3
v4..2.5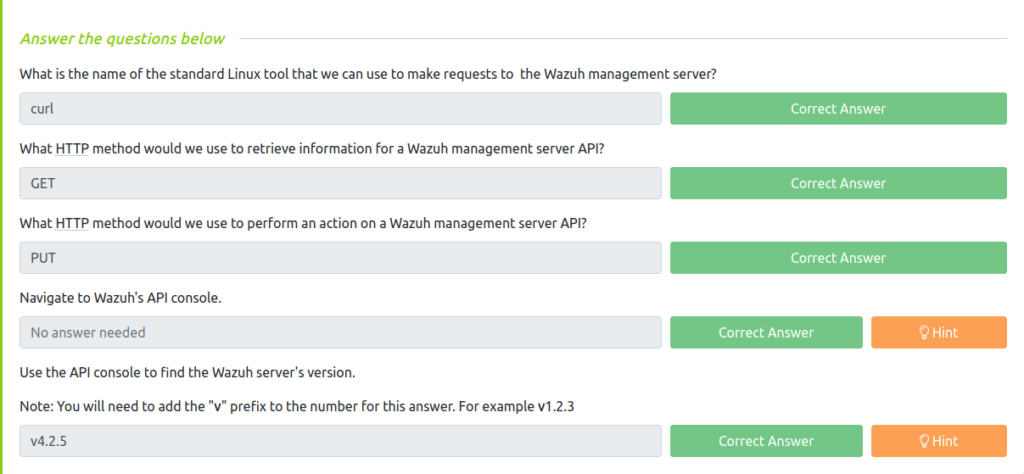
Task 11 – Generating Reports with Wazuh
Question 1 – Use Wazuh’s “Report” feature to generate a report of an agent.
Done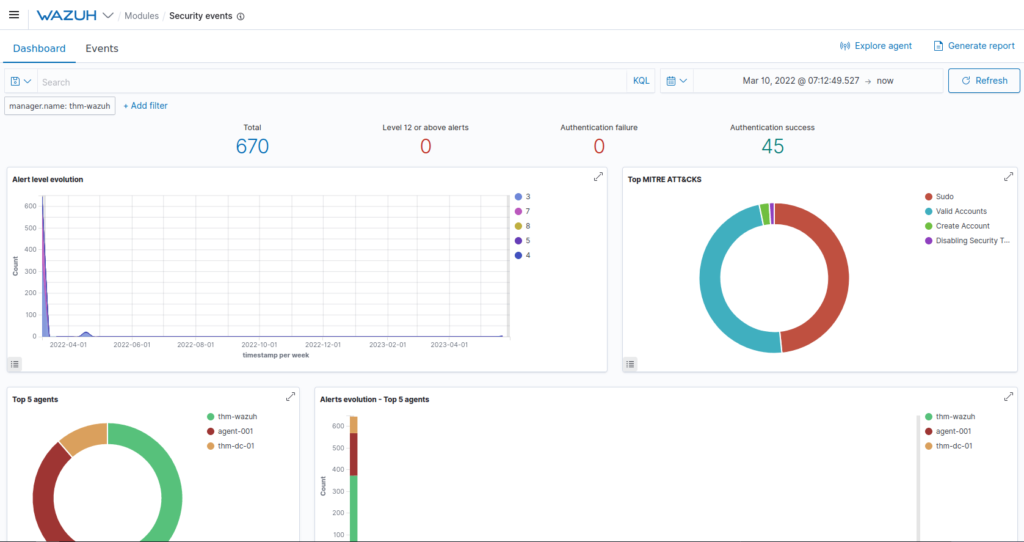
Question 2 – Navigate to the Wazuh “Report” dashboard
Done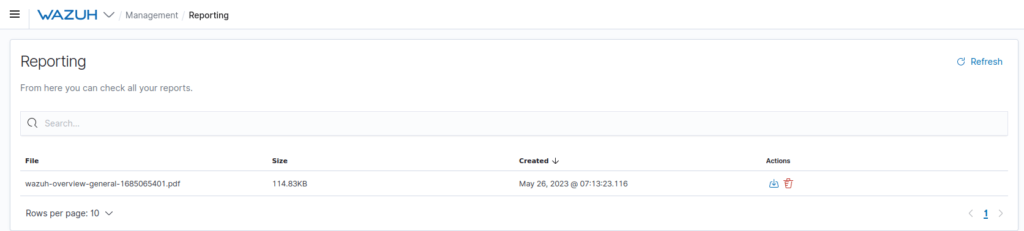
Question 3 – Analyse the report. What is the name of the agent that has generated the most alerts?
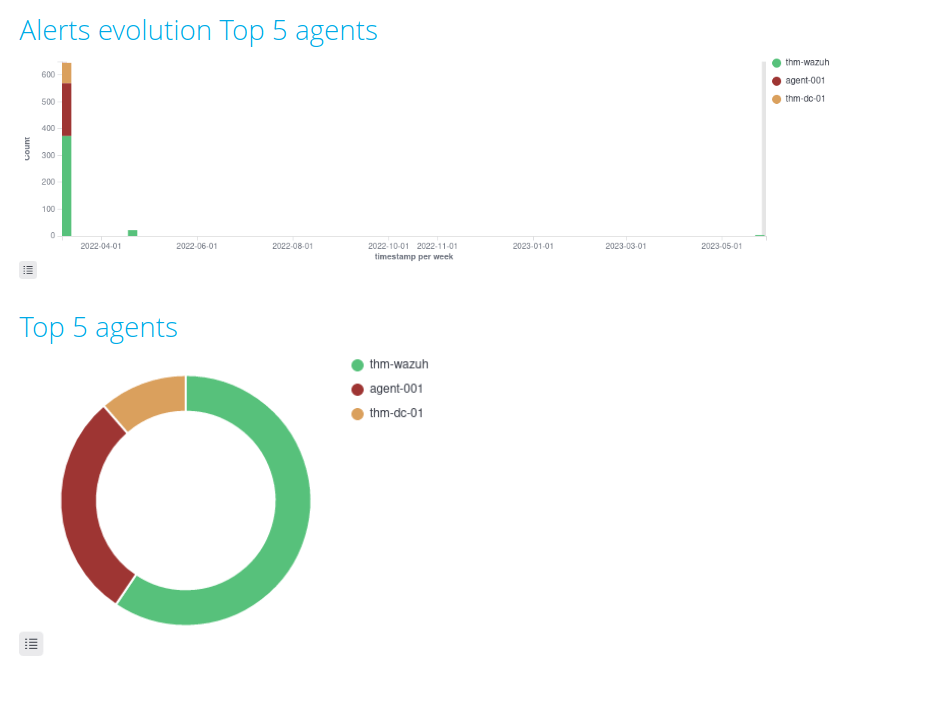
agent-001
Task 12 – Loading Sample Data
Question 1 – I’ve imported the sample data!
Done
Question 2 – I have played around with the sample data.
Done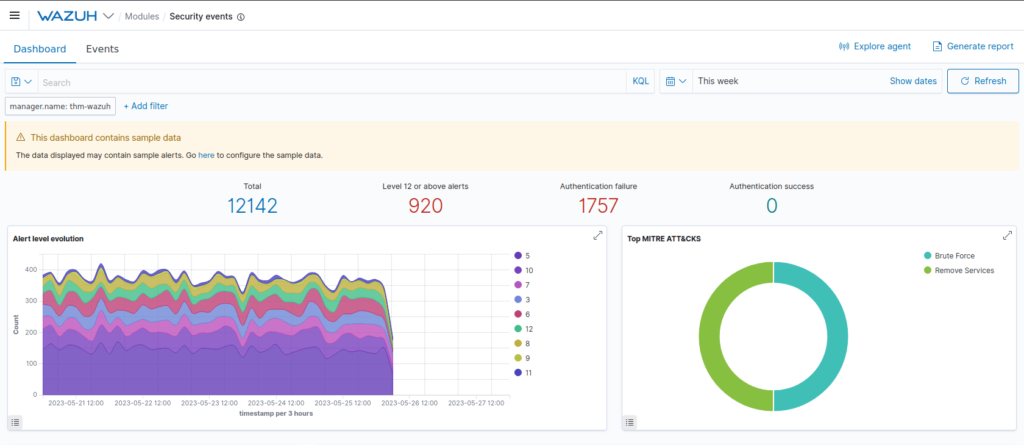
Also Read: Tryhackme – Vulnversity
So that was “Wazuh” for you. In this room, we have learned about the fundamentals of EDR solutions, where an EDR liked Wazuh can be used and then we took a dive into how to access Wazuh. Moving on, we learned how to navigate around Wazuh and create rules and alerts for it. At last, we looked into log digestion in both Windows and Linux environment with Wazuh and had a peek on Wazuh API for further extending its capabilities. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




