In this walk through, we will be going through the Windows Forensics 1 room from Tryhackme. This room is rated as Medium on the platform and is developed to introduce us with Windows Registry Forensics. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction to Windows Forensics
Question 1 – What is the most used Desktop Operating System right now?
Microsoft Windows
Task 2 – Windows Registry and Forensics
Question 1 – What is the short form for HKEY_LOCAL_MACHINE?
HKLM
Task 3 – Accessing registry hives offline
Question 1 – What is the path for the five main registry hives, DEFAULT, SAM, SECURITY, SOFTWARE, and SYSTEM?
C:\Windows\System32\Config
Question 2 – What is the path for the AmCache hive?
C:\Windows\AppCompat\Programs\Amcache.hve
Task 4 – Data Acquisition
Question 1 – Try collecting data on your own system or the attached VM using one of the above mentioned tools
Done
Task 5 – Exploring Windows Registry
Question 1 – Study the above material to understand the difference between the different tools
Done
Task 6 – System Information and System Accounts
Question 1 – What is the Current Build Number of the machine whose data is being investigated?
19044Question 2 – Which ControlSet contains the last known good configuration?
1Question 3 – What is the Computer Name of the computer?
THM-4N6Question 4 – What is the value of the TimeZoneKeyName?
Pakistan Standard TimeQuestion 5 – What is the DHCP IP address
192.168.100.58Question 6 – What is the RID of the Guest User account?
501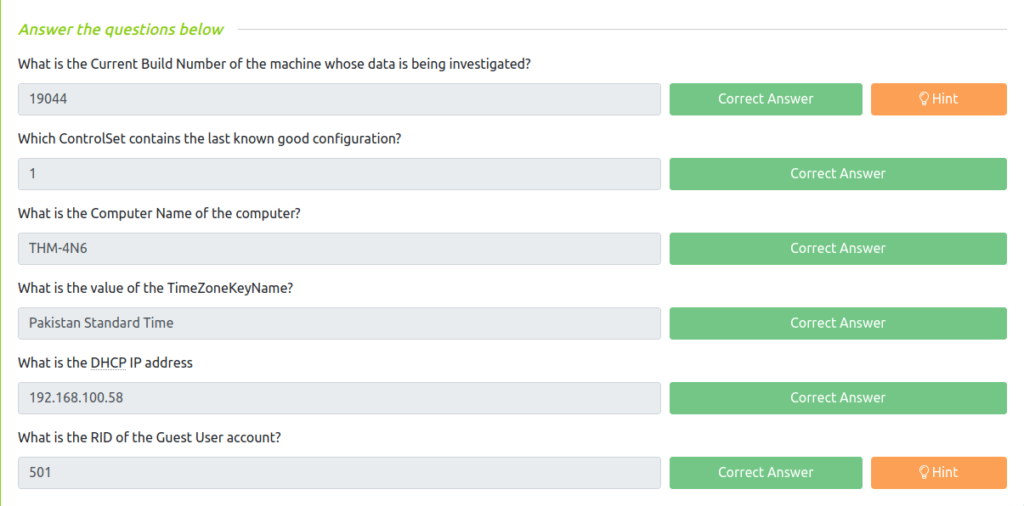
Task 7 – Usage or knowledge of files/folders
Question 1 – When was EZtools opened?
2021-12-01 13:00:34Question 2 – At what time was My Computer last interacted with?
2021-12-01 13:06:47Question 3 – What is the Absolute Path of the file opened using notepad.exe?
C:\Program Files\Amazon\EC2ConfigService\SettingsQuestion 4 – When was this file opened?
2021-11-30 10:56:19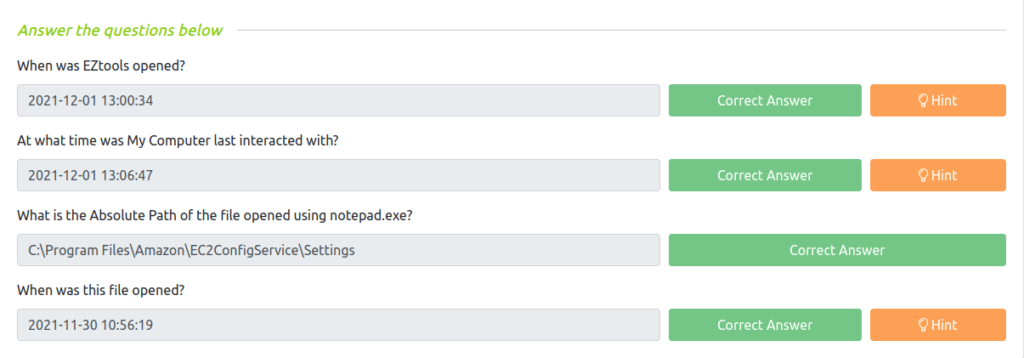
Task 8 – Evidence of Execution
Question 1 – How many times was the File Explorer launched?
26Question 2 – What is another name for ShimCache?
AppCompatCacheQuestion 3 – Which of the artifacts also saves SHA1 hashes of the executed programs?
AmCacheQuestion 4 – Which of the artifacts saves the full path of the executed programs?
BAM/DAM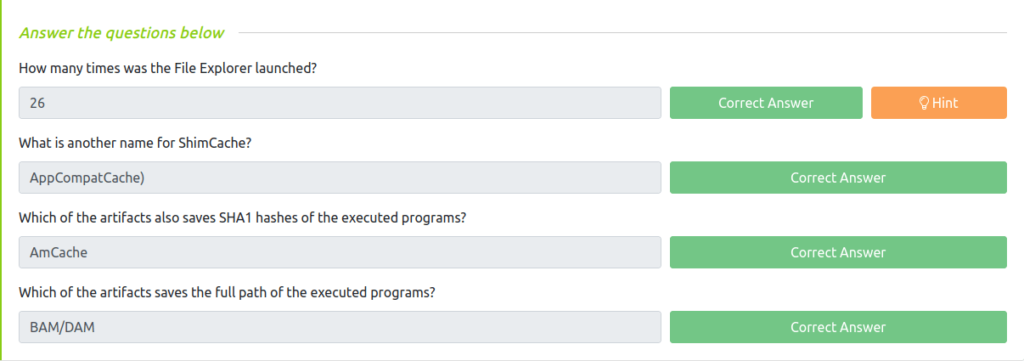
Task 9 – External Devices/USB device forensics
Question 1 – What is the serial number of the device from the manufacturer ‘Kingston’?
1C6F654E59A3B0C179D366AE&0Question 2 – What is the name of this device?
Kingston DataTraveler 2.0 USB DeviceQuestion 3 – What is the friendly name of the device from the manufacturer ‘Kingston’?
USB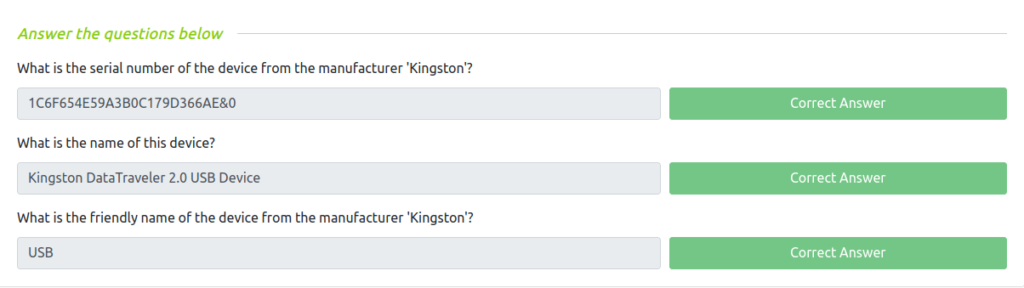
Task 10 – Hands-on Challenge
Question 1 – How many user created accounts are present on the system?
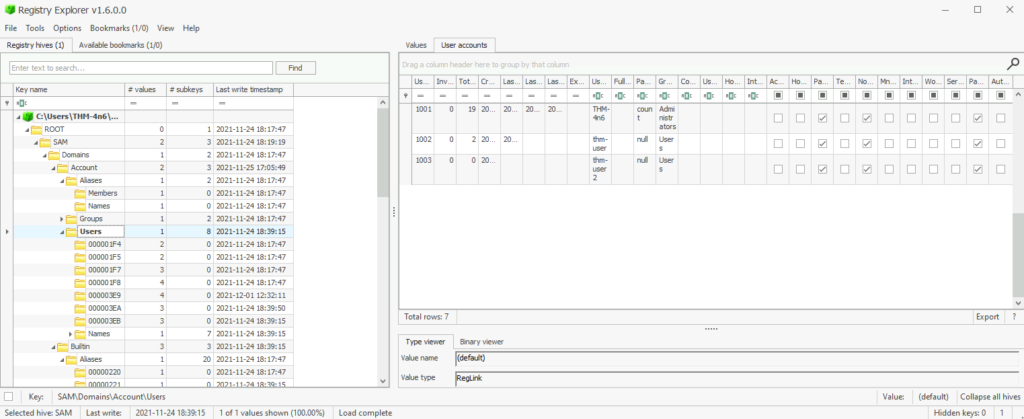
3Question 2 – How many user created accounts are present on the system?
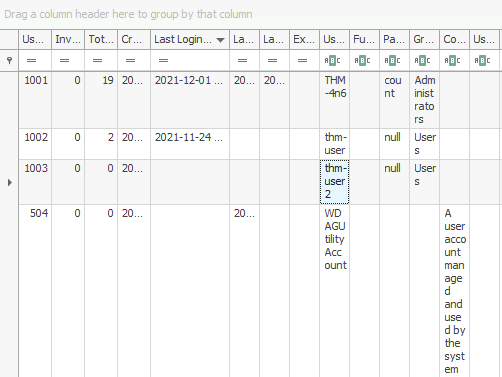
thm-user2Question 3 – What’s the password hint for the user THM-4n6?
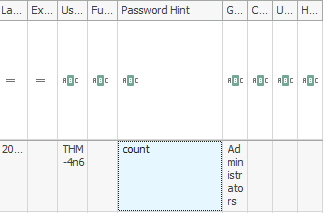
countQuestion 4 – When was the file ‘Changelog.txt’ accessed?
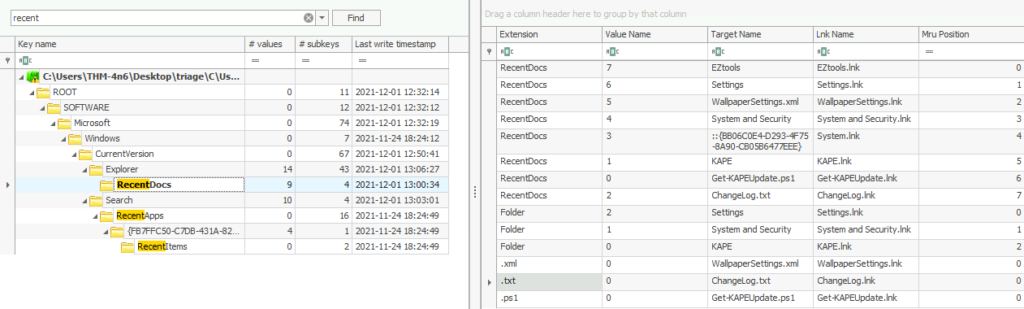
2021-11-24 18:18:48Question 5 – What is the complete path from where the python 3.8.2 installer was run?
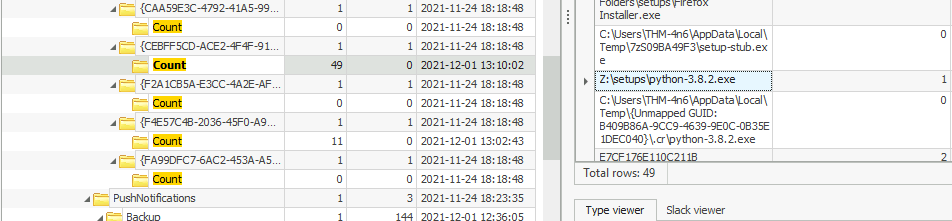
Z:\setups\python-3.8.2.exeQuestion 6 – When was the USB device with the friendly name ‘USB’ last connected?
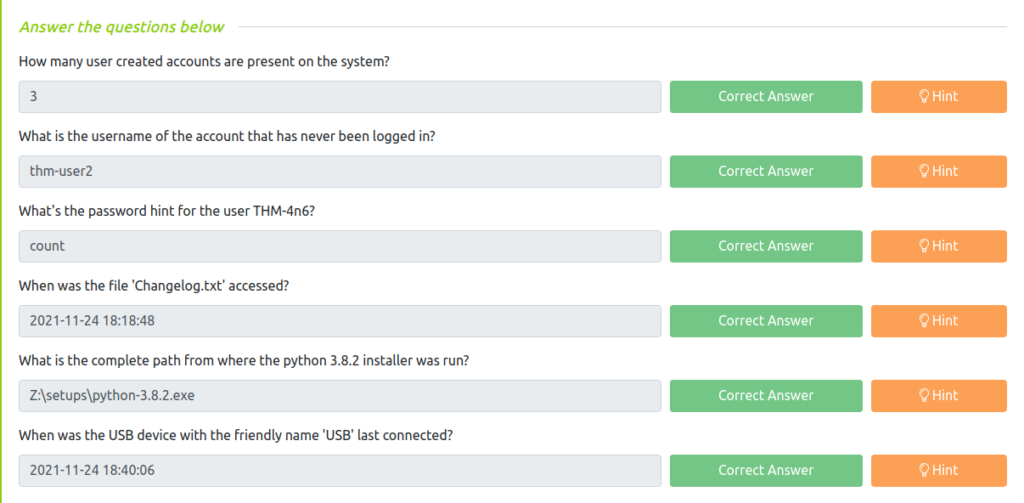
2021-11-24 18:40:06Task 11 – Conclusion
Also Read: Tryhackme – Wgel CTF
So that was “Windows Forensics 1” for you. We have learned about the fundamentals of the Windows Registry Forensics. We started with the basics of Windows Registry and Forensics. Then we access registry hives offline. Post that we perform Data acquisition, and explored Windows registry. Further, we looked into system information/accounts and explored files, folders and some attached devices. At last, we solved an hands-on challenge and completed the room. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




